- What is SSL?
- What is TLS?
- What is HTTPS?
- How Do SSL, TLS, and HTTPS Work Together?
- "SSL Certificate" vs. "TLS Certificate"
- The TLS Handshake Explained
- Types of TLS Handshakes
- Comparison between SSL and TLS
- Comparison between HTTP and HTTPS
- Examining a Certificate Example
- How to Set Up SSL/TLS on Your Website?
- Additional Tips for Securing Your Website
- Why Is HTTPS Important?
- How can Encryption Consulting Help?
- Conclusion
Encryption is crucial to web security, as it protects sensitive data from unauthorized access and cyber threats. It ensures secure communication, prevents data breaches, and builds trust between users and websites. Public Key Infrastructure (PKI) plays a crucial role in this by enabling authentication, encryption, and data integrity through SSL/TLS. TLS is the successor to SSL and is now the standard for securing online interactions, as SSL has been deprecated due to known vulnerabilities. HTTPS is not a separate protocol but rather HTTP running over TLS, which ensures encrypted data transmission between browsers and servers for secure web browsing.
What is SSL?
SSL (Secure Sockets Layer) was the original security protocol developed by Netscape in the mid-1990s. It provided a way to encrypt the data that was transmitted between your browser and a web server. Before its vulnerabilities were exposed, SSL was a widely adopted protocol for securing online communications, relying on a simple verification process. The process is:
- Your browser requests the website to prove its identity.
- The website sends an SSL certificate similar to a digital ID card.
- Your browser verifies the certificate.
- If the certificate is valid, then the encrypted communication begins.
All versions of SSL (1.0, 2.0, and 3.0) are now considered obsolete due to discovered vulnerabilities with SSL 3.0, which was officially deprecated in 2015 as per RFC 7568.
What is TLS?
TLS, or Transport Layer Security, is the current protocol used to safeguard web traffic, with several versions available: TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3. TLS is an improvement over SSL and is widely adopted today. Although the term “SSL” is still commonly used, most modern websites rely on TLS for encryption. Notably, as of March 2020, both TLS 1.0 and TLS 1.1 have been deprecated due to their vulnerabilities and outdated cryptographic methods.
- Stronger Security: TLS addresses vulnerabilities found in SSL and older TLS versions, making it more resilient against attacks such as BEAST and POODLE.
- Faster Performance: The handshake process in TLS is quicker, particularly in TLS 1.3, which requires only one round trip to establish a secure connection, compared to two in TLS 1.2.
- Modern Encryption: It utilizes advanced cryptographic methods such as authenticated encryption with associated data (AEAD) ciphers and mandates perfect forward secrecy (PFS), ensuring that session keys are unique and discarded after use to prevent the decryption of past sessions.
What is HTTPS?
HTTPS stands for Hypertext Transfer Protocol Secure. It’s the secure version of HTTP, which loads web pages. HTTPS uses encryption to protect data exchanged between your browser and a website. While it is commonly stated that HTTPS uses “SSL/TLS encryption,” this terminology can be misleading. HTTPS no longer uses SSL; it exclusively relies on TLS, the modern successor to SSL. All versions of SSL have been deprecated due to security vulnerabilities, and TLS has replaced SSL as the standard protocol for securing web communications.
When you see “https://” in a URL or a padlock icon in your browser, this means that your website uses SSL/TLS encryption. Your data is protected from interception by any attackers seeking to exploit data breaches. However, it’s important to understand how HTTPS affects performance, particularly due to the TLS handshake and session management.
Performance Implications of HTTPS
- TLS Handshake Overhead: The initial TLS handshake requires additional round-trips before a secure connection is established. This typically involves two additional round-trips compared to HTTP, which can introduce latency. However, modern hardware and optimized protocols have significantly mitigated this overhead.
- Session Resumption: To improve performance, TLS supports session resumption techniques that enable clients and servers to skip the full handshake process for subsequent connections. This reduces latency and enhances loading speeds, especially for users who frequently revisit the same site.
- Impact of HTTP/2: The adoption of HTTP/2 has further enhanced HTTPS performance by reducing latency through the multiplexing of multiple requests over a single connection. This minimizes the need for multiple TLS handshakes, making HTTPS sites faster than ever before.
- Resource Consumption: While HTTPS may initially seem more resource-intensive, studies show that the CPU load from TLS accounts for less than 1%, with minimal memory usage per connection. Therefore, the performance impact is often negligible for modern servers.
While HTTPS introduces some overhead due to the TLS handshake, advancements in technology and protocols, such as HTTP/2, have significantly mitigated these effects, ensuring that the security benefits of using HTTPS far outweigh any minor performance impacts.
How Do SSL, TLS, and HTTPS Work Together?
- SSL/TLS are protocols that encrypt data during transmission.
- HTTPS uses these protocols to secure web traffic. HTTPS is HTTP running over TLS, and the handshake is part of the TLS process that establishes a secure connection between the browser and the server.
- When you visit an HTTPS website, your browser and the server perform an “SSL/TLS handshake” to establish a secure connection.
The adoption of HTTPS has surged due to browser initiatives, particularly Google Chrome’s decision to label HTTP sites as “Not Secure.” This warning, initially applied to sites that collect sensitive information, has been expanded to all HTTP pages, prompting website owners to prioritize security. As a result, HTTPS usage among top websites has increased significantly, with over 75% of Chrome traffic now protected by HTTPS.
Common Misconceptions
What many people refer to as “SSL certificates” or “TLS certificates” are actually X.509 digital certificates that authenticate a website’s identity and enable encrypted connections.
X.509 certificates play a crucial role in the operation of TLS. When you visit a website using HTTPS, the server provides its X.509 certificate during the TLS handshake. This certificate contains information about the website and a public key, which is used to encrypt data. Your browser verifies the certificate against trusted organizations known as Certificate Authorities (CAs) to ensure it’s valid and belongs to the correct website. Once verified, the connection becomes secure, protecting your data from being intercepted and ensuring you’re communicating with the intended site.
“SSL Certificate” vs. “TLS Certificate”
Despite TLS having replaced SSL, the term “SSL certificate” remains widely used in the industry for marketing purposes. This is largely because the term has been ingrained in public consciousness, and many people are more familiar with it than with “TLS certificate.” As a result, companies continue to use “SSL certificate” to appeal to a broader audience, even though it is technically inaccurate since all modern certificates now support TLS.
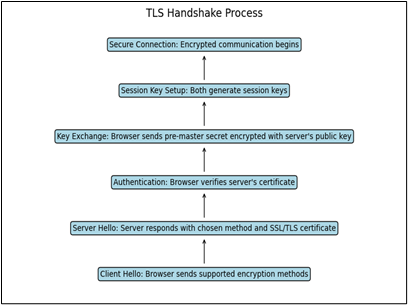
The TLS Handshake Explained
A TLS handshake is the process by which a client and server establish a secure connection by agreeing on encryption settings, authenticating each other, and exchanging cryptographic keys before transmitting encrypted data. During this process, the browser and server negotiate encryption methods, verify the server’s identity using its certificate, and generate session keys for encrypting data. In TLS 1.3, the handshake is faster and more secure, as messages are encrypted immediately, reducing connection time and protecting sensitive information from attackers.
Steps of the TLS Handshake
- Client Hello: The client (your browser) sends supported encryption methods (cipher suites) and a random value to the server.
- Server Hello: The server responds with its chosen encryption method, random value, and SSL/TLS certificate.
- Authentication: The client verifies the server’s certificate to ensure it’s legitimate.
- Key Exchange: The client generates a pre-master secret (random string) and encrypts it using the server’s public key from its certificate. However, in TLS 1.3, the RSA key exchange is no longer supported; instead, it uses ephemeral Diffie-Hellman for key exchange, ensuring perfect forward secrecy. This means that even if a session key is compromised, past communications remain secure.
- Session Key Generation: Both client and server use the pre-master secret to create session keys for symmetric encryption.
- Secure Connection Established: After exchanging final messages encrypted with the session key, all further communication becomes encrypted.
By using ephemeral Diffie-Hellman, TLS 1.3 enhances security by generating unique keys for each session that do not rely on long-term keys, making it more resistant to potential future attacks.
TLS Handshake Process
Types of TLS Handshakes
- TLS 1.2 Handshake
In TLS 1.2, the handshake requires two round-trips communications between the client and server before encryption begins.. It supports older encryption methods, such as RSA, which is now considered less secure due to its vulnerabilities. While still widely used, TLS 1.2 is slower compared to newer versions. For example, a common cipher suite used in TLS 1.2 is TLS_RSA_WITH_AES_128_CBC_SHA, which relies on RSA for key exchange and AES for encryption but lacks features such as forward secrecy.
- TLS 1.3 Handshake
TLS 1.3 enhances performance by reducing the handshake to a single round trip, thereby cutting latency and speeding up connections. It enhances security by replacing outdated algorithms like RSA with modern methods, such as Elliptic Curve Diffie-Hellman (ECDH), for key exchange, thereby ensuring perfect forward secrecy. Additionally, it encrypts more of the handshake process and supports efficient cipher suites, such as TLS_AES_128_GCM_SHA256, which enhance both speed and security.
- 0-RTT Handshake (TLS 1.3 Feature)
A notable feature of TLS 1.3 is the 0-RTT (Zero Round Trip Time) Handshake, which allows a client previously connected to a server to resume the session immediately without waiting for a response. This eliminates round-trips and significantly reduces latency. However, 0-RTT does not provide full forward secrecy because it relies on pre-shared keys from previous sessions, which can be compromised.
Additionally, 0-RTT is vulnerable to replay attacks, where attackers resend intercepted early data to trick the server into processing duplicate requests. To mitigate this risk, servers implement anti-replay mechanisms, such as requiring unique identifiers for each request, using time limits for data validity, and applying stricter checks for sensitive actions. While 0-RTT enhances performance, it should be used cautiously to ensure security.
Comparison between SSL and TLS
| Feature | SSL | TLS |
|---|---|---|
| Security | Older and less secure | Newer and more secure |
| Speed | Slower handshake process | Faster Handshake Process |
| Encryption Methods | Uses outdated algorithms | Uses advanced encryption |
| Usage Today | Deprecated | Actively used (TLS 1.2 & 1.3) |
Comparison between HTTP and HTTPS
| Feature | HTTP | HTTPS |
|---|---|---|
| Security | No encryption | Encrypted using SSL/TLS |
| Trust Indicators | Marked as “Not Secure” | Displays a padlock icon |
| Data Protection | Vulnerable to attacks | Protects sensitive data |
| SEO Benefits | No ranking boost | Higher search engine ranking |
Examining a Certificate Example
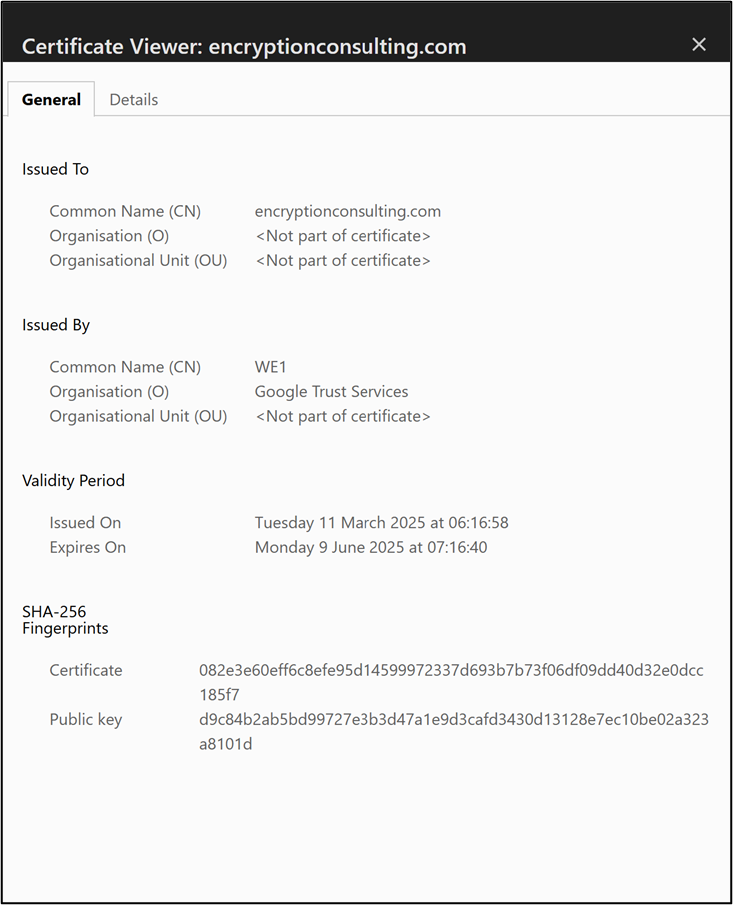
To better understand how SSL/TLS certificates work, look at the certificate details for encryptionconsulting.com, as provided in the image.
Certificate Details
- Issued To:
- Common Name (CN): encryptionconsulting.com
- Organisation (O): (Not part of the certificate)
- Organisational Unit (OU)
:(Not part of the certificate)
- Issued By:
- Common Name (CN): WE1
- Organisation (O): Google Trust Services
- Organisational Unit (OU): (Not part of the certificate)
- Validity Period:
- Issued On: Tuesday, March 11, 2025, at 06:16:58
- Expires On: Monday, June 9, 2025, at 07:16:40
- SHA-256 Fingerprints: There are also the SHA-256 fingerprints on this certificate, including the Certificate and the Public Key details.
What Do These Details Tell Us?
- Common Name (CN): This field specifies the domain name for which the certificate is issued. In this case, the certificate is issued for encryptionconsulting.com.
- Issued By (Google Trust Services): This indicates that the certificate was issued by a trusted CA. Browsers trust certificates issued by known CAs.
- Validity Period: The certificate is valid from March 11, 2025, to June 9, 2025. It is crucial to renew certificates before they expire to avoid security warnings. Expired certificates can compromise secure communication, triggering browser warnings such as “Not Secure,” which can erode user trust and hinder site accessibility.
- SHA-256 Fingerprints: These are unique certificates and public key identifiers. They can be used to verify the integrity of the certificate.
How Does This Relate to HTTPS?
When you visit encryptionconsulting.com using HTTPS, your browser will:
- Receive this certificate from the server.
- Verify that the certificate is valid (i.e., not expired and issued by a trusted CA, such as Google Trust Services).
- Certificate Chain Verification: Browsers verify the certificate chain by checking each certificate in the path from the server’s certificate to a trusted root CA. This involves ensuring that each certificate is signed by the private key of the next certificate in the chain, starting from the root certificate, which is stored in the browser’s trusted root store. If any certificate in this chain is invalid or untrusted, the connection will be marked as insecure.
- Use the public key within the certificate to establish a secure connection.
- Finally, all data exchanged between your browser and the server is encrypted, ensuring privacy and security during transmission.
How to Set Up SSL/TLS on Your Website?
Setting up SSL/TLS on your website might sound technical, but it’s easier than you think! Here’s how you can do it:
Step 1: Choose an SSL/TLS Certificate
There are three main types of certificates:
- DV (Domain Validation): A Basic security measure that verifies domain ownership.
- OV (Organization Validation): Enhances security by verifying domain ownership and organization identity.
- EV (Extended Validation): The highest level of trust; displays the company name in the browser bar.
- You can purchase certificates from trusted CAs, such as Microsoft or GlobalSign, or use free options like Let’s Encrypt.
Step 2: Generate a Certificate Signing Request (CSR)
- A CSR contains information about your domain and organization that will be included in your certificate.
- Log in to your hosting control panel or server terminal.
- Use tools like OpenSSL to generate a CSR file.
Step 3: Install the Certificate
There are two main ways to install an SSL/TLS certificate:
- Using Your Hosting Control Panel: Most hosting providers offer one-click installation for certificates purchased through them. Upload your certificate files if you are using a third-party CA.
- Using Plugins for WordPress: Install plugins like “Really Simple SSL” to automate installation.
Step 4: Configure HTTPS
- Update all internal links on your site from http:// to https://.
- Set up 301 redirects to ensure visitors are automatically directed to HTTPS versions of your pages.
Step 5: Test Your Configuration
- Use tools like SSL Labs to verify that your certificate is installed correctly.
- Ensure that you disable older protocols, such as TLS 1.0 and 1.1, and enable TLS 1.3 for improved security and performance.
- Additionally, consider implementing automated certificate renewal using the ACME protocol with services like Let’s Encrypt. This system simplifies the process of renewing SSL/TLS certificates, ensuring they remain valid without manual intervention. By automating renewals, you can avoid potential downtime or security warnings due to expired certificates, keeping your website secure and compliant effortlessly.
Additional Tips for Securing Your Website
Start by enabling HTTP Strict Transport Security (HSTS) to enhance your website’s security. This ensures that browsers connect to your site over HTTPS, preventing attackers from forcing insecure connections. HSTS protects against protocol downgrade attacks by forcing browsers to connect to a website exclusively over HTTPS. It automatically upgrades any HTTP requests to HTTPS, preventing attackers from intercepting and redirecting users to an insecure connection. Once enabled, the browser remembers the HSTS policy for future visits, ensuring all communication remains encrypted and secure.
You can implement HSTS by adding the following header to your web server configuration:
Header always set Strict-Transport-Security “max-age=31536000; includeSubDomains”
Another important step is ensuring Server Name Indication (SNI) support is enabled. SNI allows multiple SSL/TLS certificates to be hosted on the same IP address, making it essential for businesses to manage multiple domains or subdomains under a single server. With SNI, when a client initiates a connection, it includes the domain name it wants to access in the TLS handshake. This enables the server to identify which TLS certificate to present, ensuring that the correct certificate is used for each domain. Without SNI, only one certificate could be presented per IP address, leading to compatibility issues and potentially insecure connections.
By supporting multiple certificates on a single IP, SNI reduces costs and simplifies management for web hosting providers, allowing them to host various websites securely without needing dedicated IP addresses for each one. This flexibility is crucial for efficient resource use and maintaining durable security across multiple domains.
Finally, regularly monitor and update your SSL/TLS certificates to prevent security warnings or website downtime. Set up automated reminders or utilize certificate management tools to track expiration dates and renew certificates promptly. Keeping certificates up to date maintains security and ensures compliance with industry standards.
Why Is HTTPS Important?
Using HTTPS offers multiple benefits:
- Data Security: Encrypts sensitive information, such as passwords or payment details, during transmission.
- Trustworthiness: Browsers mark Websites with HTTPS as secure, while HTTP sites may show warnings like “Not Secure.”
- SEO Benefits: Google ranks HTTPS websites higher than HTTP ones.
- Compliance: Many regulations, such as the GDPR, require secure data handling through encryption.
- Modern Web Compatibility: HTTPS is essential for utilizing modern web technologies such as Service Workers and HTTP/2. Major browsers only support HTTP/2 over secure connections, meaning that without HTTPS, websites cannot take advantage of the performance improvements offered by this protocol.
How can Encryption Consulting Help?
Encryption Consulting enhances TLS and HTTPS security with services such as TLS hardening, certificate lifecycle management, and penetration testing. Our PKI Assessment and TLS Hardening Service ensures strong encryption by optimizing configurations, enforcing security best practices, and maintaining compliance with key regulations, including GDPR, HIPAA, PCI DSS, and NIST. With CertSecure Manager, we automate certificate issuance, renewal, and revocation to prevent expirations and security risks. Our Penetration Testing Service identifies vulnerabilities in TLS/HTTPS implementations, helping businesses maintain their security. We also provide custom encryption solutions for code signing, APIs, email security, and enterprise communications. Partner with us to enhance TLS security, ensure compliance, and protect sensitive data.
Conclusion
To summarize what we have learned until now.
- SSL was the original protocol for securing online communications, but it has been replaced by TLS due to better security features.
- TLS encrypts data more effectively and is used today for almost all secure connections.
- HTTPS ensures websites use SSL/TLS encryption to protect user data during browsing.
- Now that you know how these technologies work together, setting up SSL/TLS on your website will help protect users’ data while boosting trustworthiness and search rankings!
- What is SSL?
- What is TLS?
- What is HTTPS?
- How Do SSL, TLS, and HTTPS Work Together?
- "SSL Certificate" vs. "TLS Certificate"
- The TLS Handshake Explained
- Types of TLS Handshakes
- Comparison between SSL and TLS
- Comparison between HTTP and HTTPS
- Examining a Certificate Example
- How to Set Up SSL/TLS on Your Website?