Education Center, Public Key Infrastructure (PKI)
What is Public Key Cryptography?

Education Center, Public Key Infrastructure (PKI)

Asymmetric cryptography or public key cryptography is where 2 keys are used to establish a secure connection between 2 entities in a network. Public key cryptography utilizes asymmetric encryption. The private key is kept only with the owner of the website, the server, or with whom you want to communicate. The public key is distributed among the clients and the userbase. The private key can only decrypt the data encrypted using the public key. Asymmetric cryptography thus protects against Man in the Middle attacks and attacks where the data-in-transit might be compromised or modified.
The major functions of public-key cryptography are encryption, decryption, digital signatures, and key exchange.
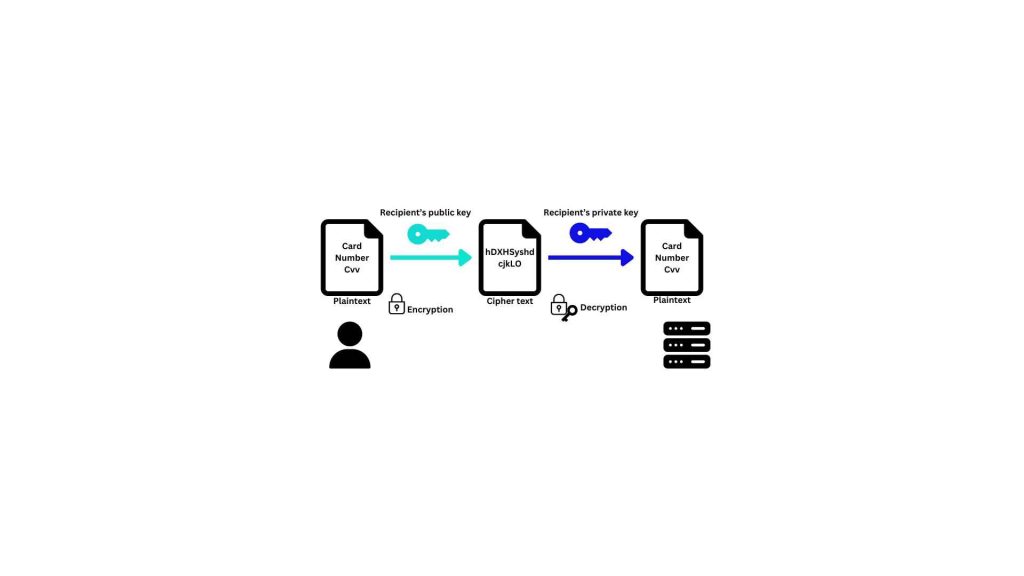
Public-key cryptography facilitates the encryption of messages or data to ensure secure communication over untrusted networks. The recipient’s public key is used for encryption, and only the corresponding private key can decrypt the message. This process ensures that only the intended recipient can decipher the information.
Decryption is the process of reverting encrypted data back to its original form, and public-key cryptography allows this process securely. The recipient uses their private key to decrypt messages that were encrypted with their corresponding public key. This ensures that only the authorized recipient can access the original information.
Public-key cryptography enables the creation and verification of digital signatures to authenticate the origin and integrity of messages or documents. The sender signs the message with their private key, and the recipient can verify the signature using the sender’s public key. This process ensures that the message has not been tampered with and was indeed sent by the claimed sender.
Public-key cryptography facilitates secure exchange between parties to establish shared secret keys for symmetric encryption. Parties can exchange public keys and derive a shared secret key without exposing their private keys. This shared key is then used for symmetric encryption, enhancing the security of subsequent communication.
A high-level real-world example of public-key cryptography is the secure transmission of information over the internet, particularly during online transactions, like shopping or banking.
Imagine you are making an online purchase:
Encryption (Sender – User’s Browser):
The user’s browser (sender) has the public key of the website. Before transmitting sensitive information (e.g., credit card details), the browser uses the website’s public key to encrypt the data.
Transmission:
The encrypted data (cipher text) is sent over the internet to the website.
Decryption (Recipient – Website):
The website (recipient), which possesses the corresponding private key, decrypts the received information. Only the website, with the private key, can successfully decrypt and access the transmitted data.
Authentication Assurance
Public key cryptography strengthens authentication by enabling the verification of message authenticity through digital signatures. This ensures that recipients can confidently validate the origin of messages, enhancing the overall security of communication channels.
Simplified Key Distribution
Public key cryptography addresses the complexities of key distribution by encouraging users to openly share their public keys. This eliminates the need for secure pre-shared key channels, offering a more convenient and scalable approach to managing encryption keys.
Non-Repudiation via Digital Signatures
Public key cryptography introduces non-repudiation features comparable to physical signatures. Messages digitally signed serve as unequivocal acknowledgments, preventing senders from disowning their communications. This strengthens the accountability and trustworthiness of digital interactions.
Security Risks of Private Key Exposure
If an attacker gains access to your private key, there is a significant security risk as they can decrypt and read all your messages. The confidentiality of your communication becomes compromised, emphasizing the importance of safeguarding private keys.
Impact of Private Key Loss
The loss of a private key poses a critical challenge, as it renders you unable to decrypt received messages. This loss of access can result in the permanent inability to retrieve or understand sensitive information, underscoring the need for secure key management practices.
Performance Considerations
Public key cryptography tends to operate at a slower pace compared to symmetric cryptography. This method may not be suitable for decrypting bulk messages efficiently, highlighting a potential drawback in terms of speed and performance, particularly in scenarios where large volumes of data need decryption.
In conclusion, public key cryptography is the generational basis for enforcing the security of digital language transactions in our connected world. Its ability to provide secure encryption, digital signatures, and key exchange mechanisms has made it imperative to secure on-line transactions, authenticate users, and ensure that the information is accurate As cyber threats evolve, public-key cryptographic trust in the virtual realm in protecting touch information And it remains a powerful tool to nurture.
Choose Encryption Consulting for unmatched expertise, reliable answers, and comprehensive support to protect your digital infrastructure and secure consent for your virtual transactions.