Issue
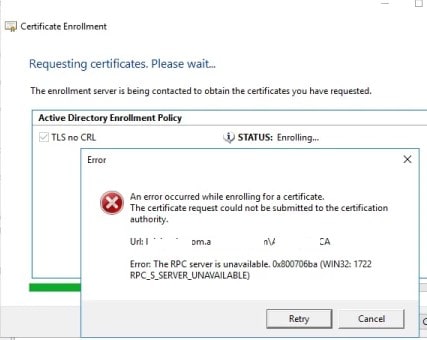
Every time the user tries to enroll a certificate, an RPC Server Unavailable error appears. In this instance, the domain controller or another client neglects to sign up for certificates from the CA.
Error Code
0x800706ba (WIN32: 1722 RPC_S_SERVER_UNAVAILABLE)
Description
When a user requests a certificate from ADCS Certification Authority, the requested certificate is not supported by this CA or request cannot be submitted to the certification authority due to a rpc error:
Win32 error 1722: “The RPC server is unavailable”
Now what does “The RPC server is unavailable” error mean? It typically indicates a communication breakdown between two devices or systems. This error occurs when a Windows device has trouble communicating with another remote device.
Cause
This RPC Server unavailable error occurs only due to two reasons:
- It is not feasible to connect to the CA’s RPC interface.
- Although it is possible to connect to the CA’s RPC interface, the remote computer could not be authenticated due to problems with its security certificate or firewall restrictions.
Steps done
- Checked from network trace to find that it denies the access (status: nca_s_fault_access_denied)
- Checked GP Result to see which GPO are being populated.
Solution
This solution has been divided into five parts, covering the details of what we need to do:
-
Checking Network Connection
The client and the CA must be able to communicate via the network.
- Check whether the hostname for CA Server is correct or not.
- If the hostname is correct, then look for whether the name resolution is working fine and resolving the server’s name (i.e., the DNS entry registered on the old computer object).
- Check whether the correct ports are opened on all firewalls (if any) to verify that no rpc connection failed.
- Basic, but it should also be taken care that the CA server and service are available and running successfully.
-
Fixing the RPC Interface
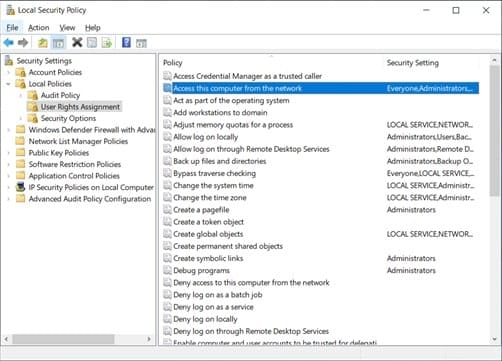
Coming to CA, the first hurdle is that the RPC interface must be cleared, and the connection should be established. To do this, the account should have “Access this computer from the network” permissions granted.
To do this
-
Open Local Security Policy -> Expand Local policies -> Double click User rights assignment.
-
By default, the following accounts should be enrolled here. Everyone, Administrators, Backup operators, Users
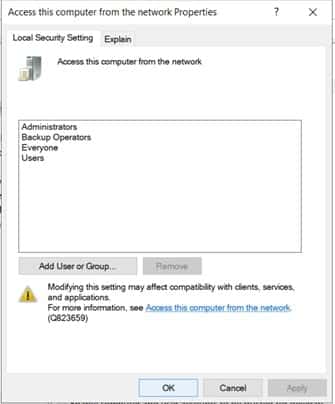
Note: There is also an option to “Deny access to this computer from Network”, which should strictly be avoided.
-
-
DCOM Permissions
After RPC is properly configured, DCOM will handle the authentication. To open this configuration,
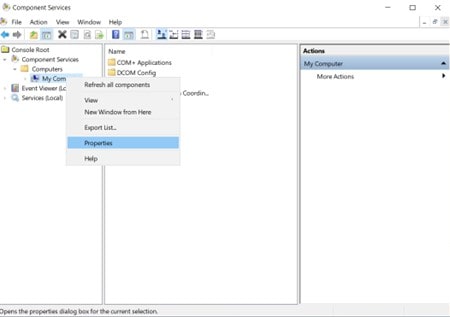
- Open Component Services; to do so, type dccomcnfg.
-
Browse to My computers and right-click. Enter properties.
-
Browse to COM Security under “EDIT LIMITS”.
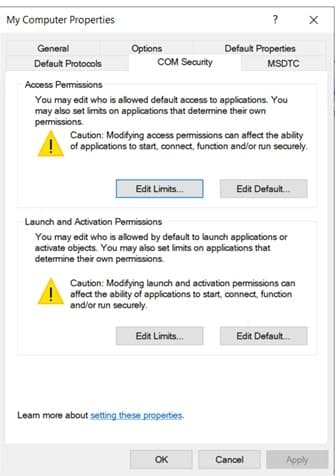
-
Check whether these permissions are there in the security group:
- Access permissions: Local Access and “Remote Access”
-
Launch and activation permissions: “Local Launch” and “Remote Launch.”
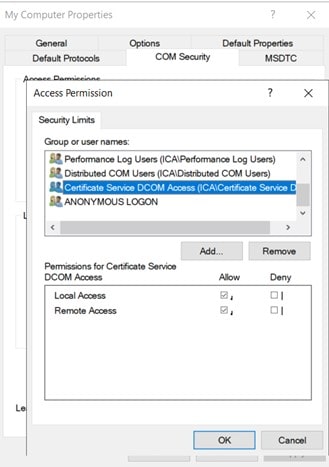
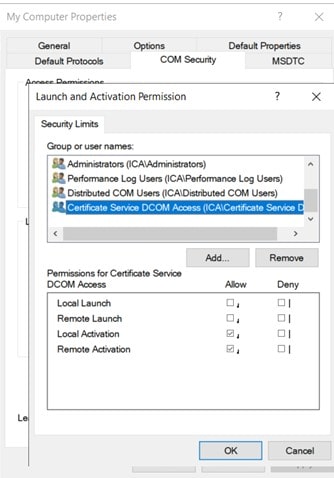
- By default, the “Authenticated Users” are in the local “Certificate Service DCOM Access” security group.
Note: To be aware that these settings can be controlled via Group Policy.
-
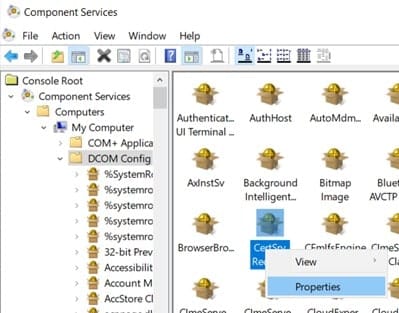
DCOM Config (CertSrv) Interface
- Go to “Component Services” -> “Computers” -> “My Computers” -> “DCOM Config”
-
Open DCOM Config and select CertSrv Request. Right click and open properties.
-
Go to security tab and click on edit.
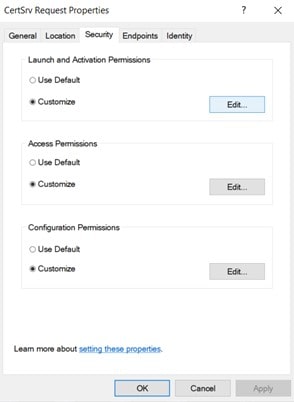
- For Launch and Activation Permissions: Check “Local Activation” and “Remote Activation” for Everyone
-
For Access Permissions: Check “Local Access” and “Remote Access” for Everyone
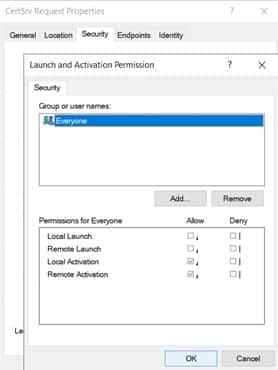
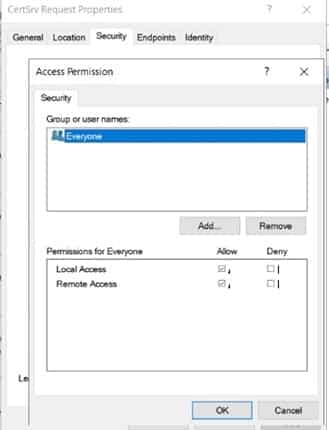
Set the following permissions:
-
CA Permissions
It is always a checklist to see that the proper permissions on the CA are given. Otherwise, it would return CERTSRV_E_ENROLL_DENIED error.




