Introduction
As organizations generate and store more sensitive information than ever, securing that data across on-premise systems, cloud platforms, and modern distributed architectures has become a business priority. For years, the Vormetric Data Security Platform (now under Thales) has been recognized as one of the most comprehensive frameworks for protecting data at rest (data stored on disks, databases, or backups and not actively moving across networks), enforcing access controls, and centralizing key management across diverse environments. Its capabilities have supported large enterprises across banking, healthcare, government, manufacturing, and other highly regulated sectors.
But as technology landscapes shift toward hybrid architectures, cloud-native applications, microservices, and automation-driven development, organizations increasingly need encryption solutions that are both powerful and adaptable. While Vormetric remains a strong and trusted platform, modern businesses often require additional flexibility, simplified integration, cloud-native workflows, and advisory support to design encryption programs that keep pace with evolving threats and operational demands.
In this blog, we explore what the Vormetric Data Security Platform offers, why it became an industry standard, and how modern encryption service providers like Encryption Consulting can help organizations strengthen, modernize, and extend their data-protection strategy in ways that align with today’s architectures and tomorrow’s requirements.
Understanding The Vormetric Data Security Platform
The Vormetric platform is built around a core component, Data Security Manager (DSM), which serves as the central authority for encryption keys, policies, and access control. Surrounding the DSM is an ecosystem of modules designed to handle different types of data and different protection needs. At the heart of this ecosystem is Vormetric Transparent Encryption (VTE), an agent-based solution that operates at the kernel level to encrypt data at the file or volume layer without requiring application changes.
Because the encryption and access controls are enforced within the operating system kernel, VTE remains completely transparent to applications, allowing them to function normally while still ensuring that only authorized users and processes can access decrypted data. This enables enterprises to maintain granular control over who can access sensitive information, under what conditions, and through which processes.
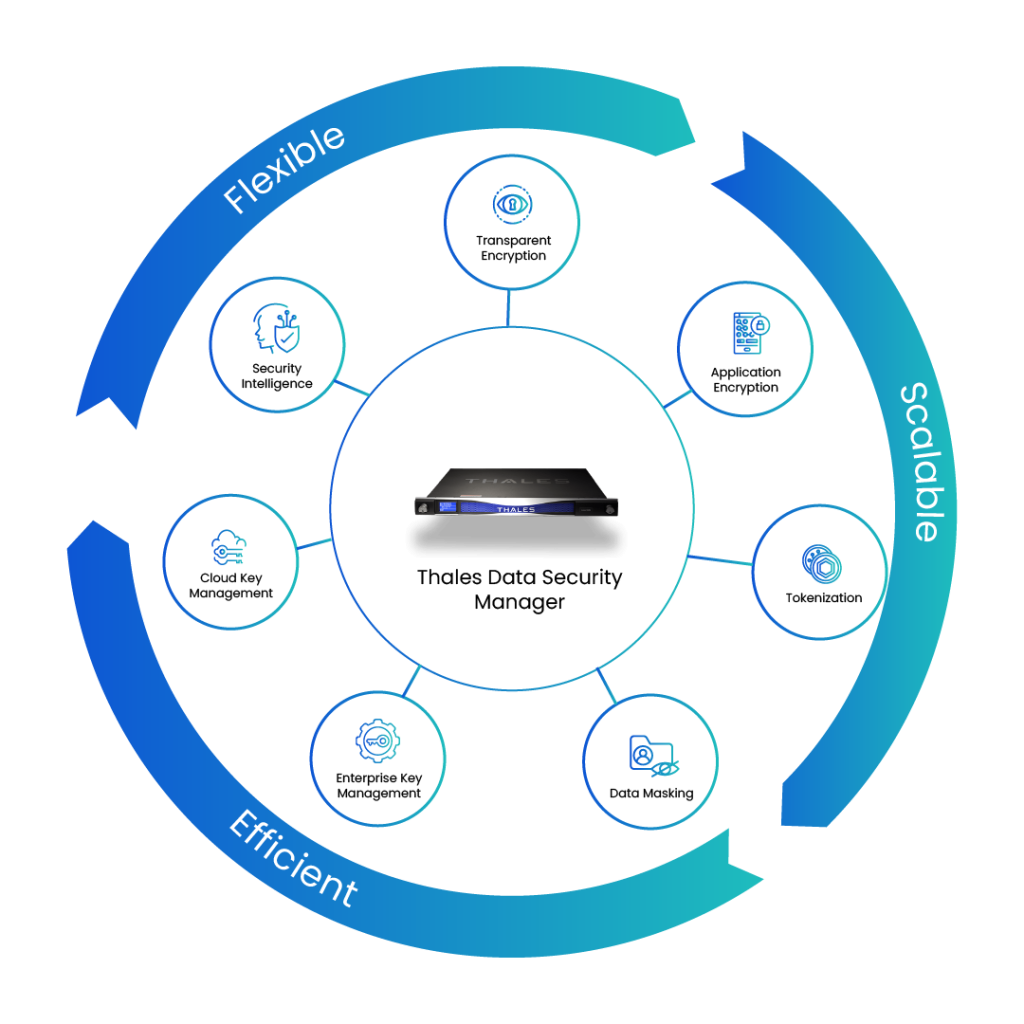
As seen in the above diagram, beyond Transparent Encryption, Vormetric expands into several additional data-protection capabilities, including:
- Application Encryption: Encrypting specific sensitive fields, such as credit card numbers or Social Security numbers, directly within applications.
- Tokenization: Replacing sensitive values (e.g., PANs in payment systems) with tokens that have no exploitable meaning.
- Data Masking: Obscuring sensitive data like customer PII when viewed by non-privileged users or support teams.
- Encryption Gateways: Encrypting data before it is stored in cloud services such as AWS S3 or Salesforce.
- Centralized Key Management: Managing encryption keys for databases, KMIP-compliant devices, and cloud-native KMS platforms from a unified console.
- Security Intelligence: Capturing detailed logs related to data access attempts, policy violations, and privileged-user activity.
This breadth enables organizations to deploy a cohesive, unified data-at-rest protection strategy across multiple operating systems, cloud providers, big data platforms, container environments, and virtualization technologies.
The platform also emphasizes strong compliance alignment. With support for FIPS 140-2 Level 2 and Level 3, Common Criteria certifications, and integrations with Oracle and Microsoft SQL TDE, Vormetric aligns well with regulatory requirements across PCI DSS, GDPR, HIPAA, SOX, and other data protection mandates. These certifications and regulatory mappings are critical because they help organizations demonstrate that their data-security controls meet internationally recognized standards, reduce audit complexity, and minimize the risk of non-compliance penalties. By providing validated, standards-based security controls, Vormetric enables businesses to confidently secure sensitive data while streamlining the path to regulatory compliance.
Why Vormetric Became A Market Standard?
Vormetric’s popularity stems from its ability to protect data in a wide variety of environments while maintaining strict control over access. Its policy-based approach ensures that even privileged users, such as system administrators or DBAs, cannot view decrypted data unless explicitly authorized. This “separation of duties” model reduces the risk of insider threats and supports a zero-trust approach to data access long before “zero trust” became a mainstream security concept.
It also reinforces Vormetric’s Root User Impersonation Prevention capability, which ensures that even highly privileged accounts such as root or system administrators, cannot impersonate authorized users to access decrypted data. By preventing misuse of elevated credentials, the platform further strengthens protection against insider attacks and unauthorized access.
The platform’s versatility also contributed to its widespread adoption. Whether data is stored on-premise, in virtualized infrastructure, in big data clusters, or in cloud workloads, Vormetric offers consistent controls. Its security intelligence capabilities provide detailed visibility into data access and attempted access, making it easier for organizations to detect anomalies, identify malicious behavior, and respond to advanced threats.
In addition, Vormetric enables organizations to explicitly whitelist trusted applications and block unauthorized or suspicious processes from accessing sensitive data. By enforcing application-level access controls at the kernel layer, the platform ensures that even if malware, exploited services, or rogue scripts run on the system, they are unable to read or decrypt protected information, significantly reducing the risk of data theft or compromise.
For large enterprises with complex systems, regulatory pressure, and traditional infrastructure, Vormetric has long offered a dependable, high-assurance way to secure data at scale.
Modernizing Traditional Data Security Platforms
Despite its strengths, organizations today often find themselves needing more agility and operational simplicity than traditional platforms like Vormetric were originally designed to provide. Deploying agents across thousands of servers, managing appliance clusters, configuring TDE integrations, and maintaining complex policy structures can be resource-intensive. Cloud migrations, container adoption, and microservices architectures further complicate deployments.
Organizations also increasingly seek encryption solutions that integrate seamlessly with DevOps pipelines, automatically rotate keys in cloud-native environments, and offer simple REST APIs that developers can consume without needing cryptographic expertise. These expectations, being driven by modern engineering culture, require a balance of robust security and streamlined, developer-friendly workflows.
This is where Encryption Consulting strengthens the journey. We don’t replace platforms like Vormetric but enhance them, helping organizations modernize data protection without losing their existing security foundations.
How Can Encryption Consulting Help?
At Encryption Consulting, we don’t just offer encryption technology, but also partner with you to build a sustainable, future-ready data protection strategy with our Encryption Advisory Services. Inspired by industry-best practices, our advisory services are deeply rooted in cryptographic expertise, governance, and real-world deployment. Here’s how we support organizations at every stage of their encryption journey.
Assessment & Gap Analysis
- Current State Audit: We begin by conducting a thorough assessment of your existing data-protection infrastructure. This includes mapping out where sensitive data lives (databases, file systems, cloud storage, applications), and how encryption is currently being used.
- Key Management Review: We analyse how you handle your cryptographic keys; how they are stored, rotated, and controlled. This helps uncover unnecessary risk, key sprawl, or weak processes.
- Compliance Mapping: Leveraging regulatory frameworks like GDPR, PCI DSS, NIST, etc, we evaluate whether your encryption posture meets both current and emerging compliance needs. Check out our Compliance Advisory Services!
Strategy & Roadmap Development
- Tailored Encryption Strategy: We develop a customized strategy that aligns encryption with your business goals, regulatory needs, and threat landscape. Whether you’re protecting PII, financial data, intellectual property, or mission-critical workloads, we build a strategy that makes sense for you.
- Governance Frameworks: We help you define policies, ownership models, and roles (who manages keys, who approves encryption change requests, and how to handle key rotation).
- Technology Architecture & Reference Designs: Using proven architectural patterns, we design reference models for how encryption should be integrated into your data infrastructure, whether it’s for on-prem systems, cloud workloads, containers, or data lakes.
Vendor Evaluation & Proof-of-Concept (POC)
- RFP/RFI Design: If you plan to evaluate third-party encryption or key-management vendors, we assist you in crafting RFPs and RFI documents tailored to your use cases.
- Vendor Comparison Framework: We assess potential vendors (or internal options) across critical metrics, performance, scalability, key management features, cost, compliance, and integration.
- Proof-of-Concept Execution: We help set up POC environments that test real-world use cases: encrypting databases, cloud buckets, or even container volumes. We document results, analyse costs (licensing, hardware, operational), and make go/no-go recommendations.
Implementation & Integration Support
- Program Setup & Governance: We don’t just deliver tools, we help you embed encryption into your governance model. This includes defining key-lifecycle procedures, designing change-management processes, and building encryption review boards if needed.
- Encryption Technology Roll-out: Whether you choose to deploy Transparent Encryption agents (in legacy systems), use application-level encryption, or go API-first with modern connectors, we guide you through architecture, configuration, and deployment.
- Key Management System (KMS) Design: We help architect a robust key-management plan, whether cloud-native, HSM-backed, or hybrid, tailored to your risk model and scale.
Monitoring & Continuous Advisory
- Risk Monitoring: We set up mechanisms to detect unusual key usage, anomalous decryption patterns, or policy violations, giving you visibility into potential misuse or security drift.
- Governance Reviews: Periodically, we revisit your encryption governance, rotate key policies, and ensure your cryptographic controls keep pace with evolving business needs.
- Future-Proofing: We work with you to plan for future challenges like post-quantum cryptography, cloud migration, zero-trust encryption, or regulatory changes. Encryption Consulting’s advisory model explicitly includes preparing for quantum-era risks.
Conclusion
Vormetric has long provided a strong foundation for securing sensitive data across complex enterprise environments. But as organizations shift toward cloud-native, distributed, and fast-moving architectures, traditional tools often need additional flexibility and modernization.
Encryption Consulting helps bridge that gap by assessing your current posture, refining your strategy, and guiding secure, practical implementation. We extend the value of platforms like Vormetric while enabling a more agile, future-ready encryption approach. With the right combination of proven technology and modern advisory support, your organization can stay secure, compliant, and fully prepared for what’s next.




