Education Center, Public Key Infrastructure (PKI)
What is the Average Total Cost of a Data Breach?

Education Center, Public Key Infrastructure (PKI)

In the era of digital transformation and increasing reliance on technology, data breaches have become a significant concern for organizations across the globe. A data breach occurs when unauthorized individuals gain access to sensitive or confidential information, posing serious threats to data integrity, privacy, and financial stability. The cost of a data breach extends far beyond the immediate financial implications, encompassing legal consequences, reputational damage, and the need for comprehensive cybersecurity measures.
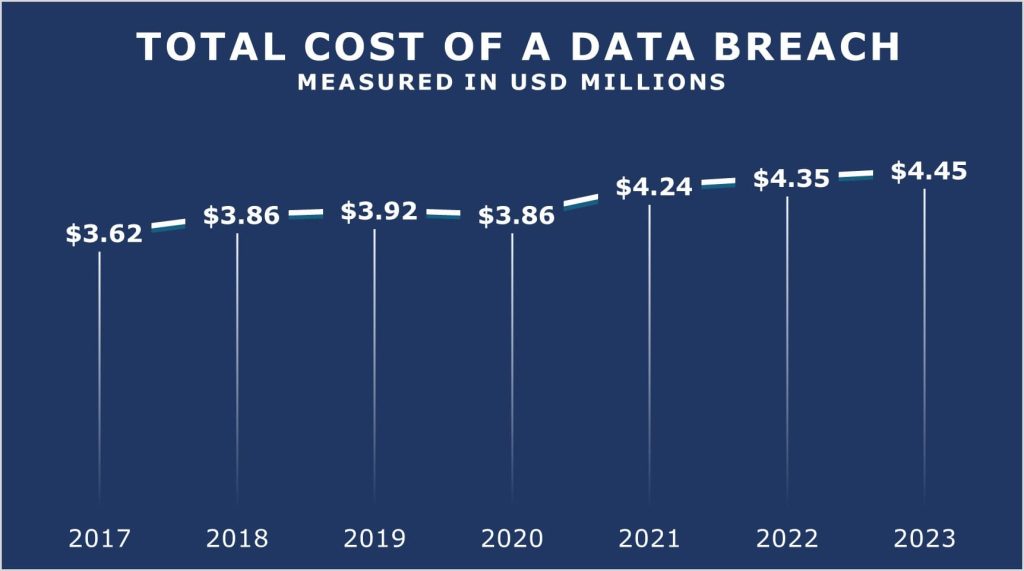
On a global scale, the average expense incurred due to a data breach has climbed to $4.45 million, marking a $100,000 upturn from the figures reported in 2022. This translates to a 2.3% escalation compared to the 2022 average cost of $4.35 million. In 2014, the average cost of a data breach was $3.5 million. Today, the average cost of a data breach has surged nearly 30%. Since 2020, when the average cost was $3.86 million, there has been a significant 15.3% increase. In 2014, the average cost of a data breach stood at $3.5 million, illustrating a remarkable 30% increase in the present day.
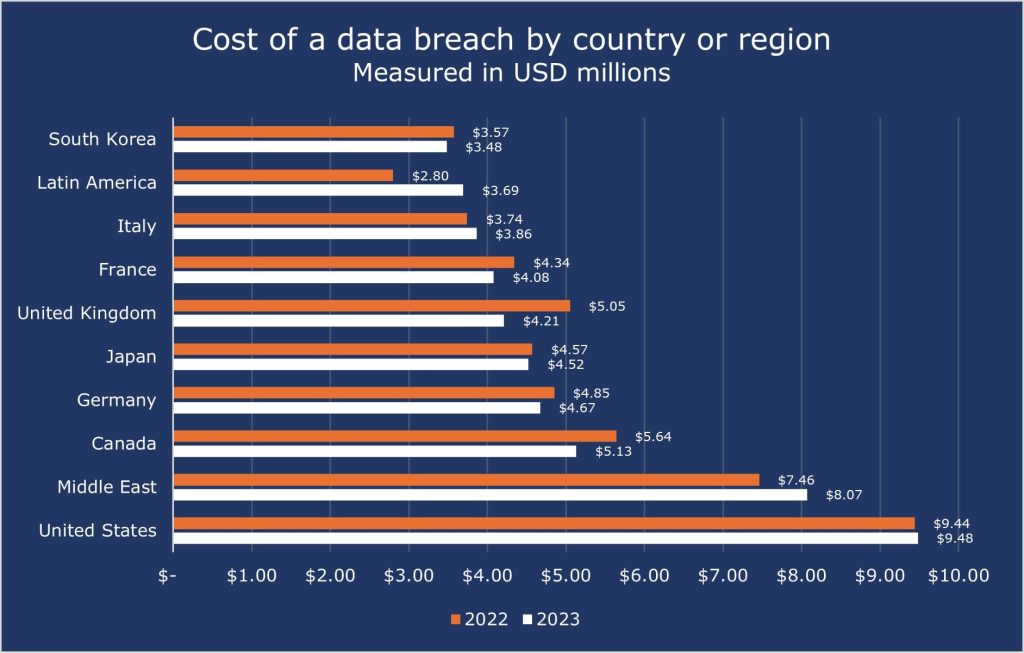
The top five countries and regions with the highest average cost of a data breach include the United States at $9.48 million, the Middle East at $8.07 million, Canada at $5.13 million, Germany at $4.67 million, and Japan at $4.52 million.
For 13 consecutive years, the United States has consistently held the record for the highest average cost of a data breach. In 2013, the average total organizational cost of a breach in the U.S. was $5.4 million. However, by 2023, this figure had surged to $9.48 million per breach, marking a substantial 75.5% increase over the years.
The cost of a data breach for the top 10 countries or regions is shown below:
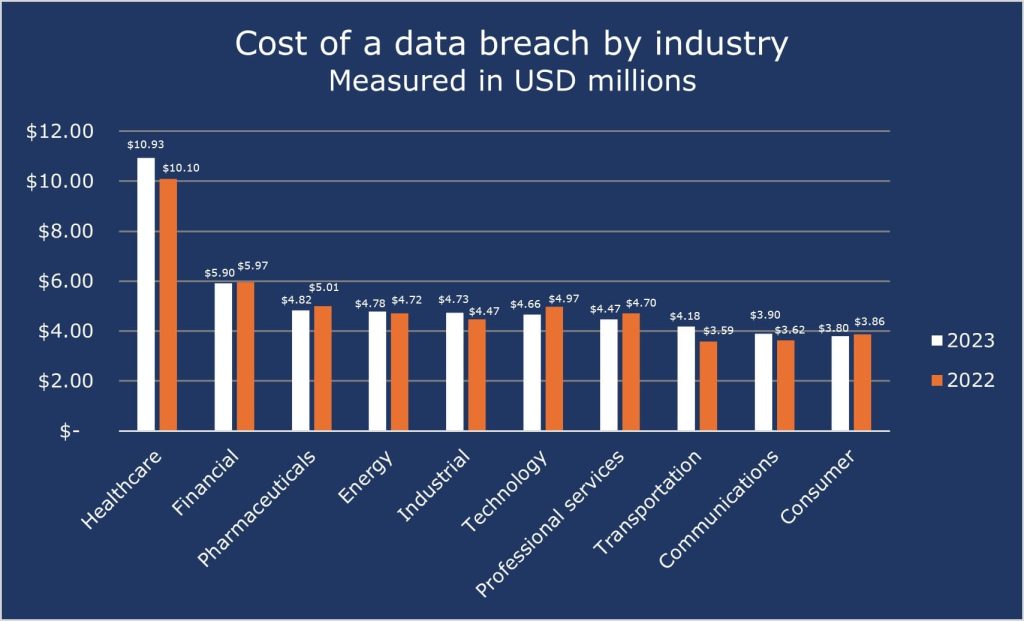
For the past 13 years, the healthcare sector has consistently ranked as the industry with the highest cost of a data breach. The 2023 report indicates that healthcare organizations incurred an average expense of $10.93 million per breach. Throughout most of the reporting periods, the financial and pharmaceutical sectors have consistently occupied the second and third positions, respectively, in terms of the cost per industry.
The cost of a data breach for the top 10 industries is shown below:
As technology advances, the threat landscape continues to evolve, requiring a comprehensive approach to cybersecurity. Organizations must recognize the importance of investing in pre-emptive measures, incident response planning and employee education to protect against the potentially damaging consequences of a data breach. By prioritizing cybersecurity, organizations can not only protect their financial interests but also maintain stakeholder trust and confidence in an increasingly interconnected digital world. Encryption consulting offers complete solutions to protect against data breaches, ensuring financial security and stakeholder trust.