Encryption, Cloud Key Management
Key Management in Multi-Cloud Environments

Encryption, Cloud Key Management

Once overlooked, key management in the cloud is becoming a high priority for CISOs as multi-cloud environments become the next step in the continual goal of reducing downtime. Each major cloud provider has its own internal key manager. Amazon Web Services (AWS) has the AWS Key Management Service tucked away inside of the Identity and Access Management (IAM). Azure has the Key Vault to store keys used within its environment. Google has the Cloud Key Management Service. All of them have very different interfaces and offer little control over key sovereignty.
External Key Management services have been slow to answer the problem with their focus on the internal data center. Cloud key managers have not been keen to adopt standards such as the Key Management Interoperability Protocol (KMIP). The latest generation of Key Managers, however, is starting to close the gap. By leveraging the REST interfaces provided by cloud providers, Key Managers can enable Bring Your Own-Key (BYOK) functionality at multi-cloud and enterprise scales. Functionally, most Key Managers can support these new use-cases through APIs and clients. Migrating to a secure cloud infrastructure requires some research as BYOK integrations are still emerging.
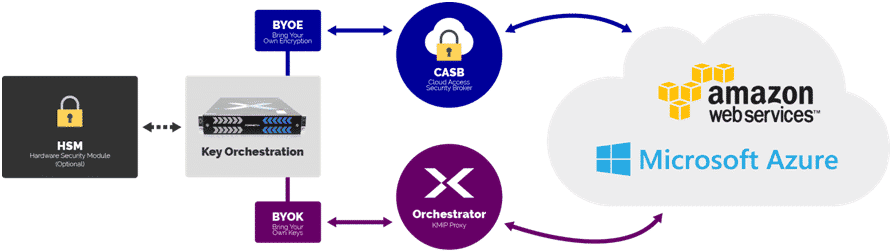
There are several questions you should consider before deciding on your key management partner:
By working with experts, you greatly increase your chances of having a platform that performs and provides the security your organization needs to thrive while still protecting vital data. With the right strategy, encryption of your multi-cloud infrastructure can be integrated into your existing DevOps platforms with ease.
Jon Mentzell is a cyber security expert with two decades of systems administration and DevOps experience including security for a cabinet-level government agency. He is currently the Product Security Manager at Fornetix.
Ability of different cloud platforms like GCP, AWS etc to seamlessly work together and managing encryption across multiple providers.
Security can be enchanced with regularly changing the encryption keys. In a multi-cloud environment, managing key rotation across different platforms can be complex due to varying key management mechanisms and policies.
Maintaining consistency and synchronization of encryption keys across multiple cloud environments is crucial to ensure data integrity.
Different cloud providers may adhere to varying security standards and regulations. Managing keys in compliance with these standards across multiple clouds requires careful planning and implementation to avoid compliance breaches.
With a strong focus on Encryption Advisory services and decades of consulting expertise, Encryption Consulting offers a range of cryptographic solutions. Among these, PKI as a Service (PKIaaS) stands out, providing round-the-clock support to clients for any issues related to their PKI environment. This comprehensive approach enhances security, ensuring organizations remain resilient against potential misconfigurations in their encryption setups.