Common Encryption Algorithms, Education Center
What is AES? How does it work?

Common Encryption Algorithms, Education Center

The Advanced Encryption Standard (AES), introduced by the National Institute of Standards and Technology (NIST) in 2001, is a strong encryption algorithm derived from the Rijndael cipher family. AES employs the Rijndael block cipher to enhance security with three distinct key sizes: 128, 192, and 256 bits. It operates as a symmetric block cipher, employing a single key for encryption and decryption processes. In contrast to asymmetric encryption, which utilizes two keys, AES simplifies the process by relying on a single secret key. Initially exclusive to the United States, AES has gained global recognition, becoming one of the most widely adopted and secure encryption algorithms, symbolizing its effectiveness and adaptability in safeguarding sensitive information worldwide.
DES was established as the encryption standard by NIST in the early 1970s and was widely adopted by the U.S. government and other organizations. However, with the passage of time and the advancement of computing power, DES’s 64-bit key size (56 usable bits) became a security concern. The relatively small key size made DES susceptible to brute-force attacks, where an attacker could guess the key through repeated attempts.
In response to DES’s limitations, NIST initiated a process to select a new encryption standard that would offer a higher level of security while being efficient and practical for widespread adoption. In 1997, NIST issued a public call for cryptographic algorithms, inviting submissions from the global cryptographic community.
The Bureau of Industry and Security (BIS) has several controls and regulations in place that make it difficult to export encrypted products encrypted with AES. The Rijndael algorithm, chosen as the basis for AES, provided a solid foundation for encryption. It operated on 128-bit blocks of data, ensuring high security. AES has become a widely accepted encryption standard published by NIST for various frameworks and regulations.
AES’s block cipher encrypts data by breaking the plaintext into 128-bit blocks. Encryption involves bitwise operations using keys of varying lengths—128, 192, or 256 bits. The key size directly impacts security, with larger keys providing greater protection. For a 128-bit key, encryption occurs ten times, 12 times for 192 bits, and 14 times for 256 bits. While 256-bit keys offer the highest security, 128-bit keys are generally sufficient for most cases. The key size choice depends on the data’s security requirements, where higher security levels warrant larger key sizes. AES provides flexibility in key selection to cater to diverse encryption needs.
| Specification | AES-128 | AES-192 | AES-256 |
| Key Length (bits) | 128 bits | 192 bits | 256 bits |
| Number of Rounds | 10 rounds | 12 rounds | 14 rounds |
| Key Schedule Size | 176 bytes | 208 bytes | 240 bytes |
| Encryption Strength | Moderate | Higher | Strongest |
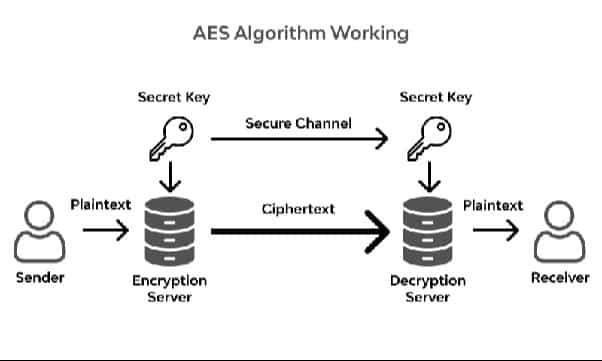
AES (Advanced Encryption Standard) is a symmetric encryption algorithm that applies transformations to plaintext data to produce ciphertext. Here’s a high-level overview of how AES works:
Key Expansion
AES operates on fixed-size blocks of data (128 bits in the case of AES-128). The secret key, 128, 192, or 256 bits long, undergoes a key expansion process to generate a set of round keys. Each round key is derived from the original key and is used in the successive encryption rounds.
Initial Round
AddRoundKey
Each block byte is combined with the corresponding byte of the round key using bitwise XOR.
Rounds (9 or 11 rounds for AES-128 or AES-256, respectively)
SubBytes
Non-linear substitution step where each byte in the block is replaced with a corresponding byte from the S-box.
ShiftRows
A transposition step where varying offsets shift the rows of the block.
MixColumns
A mixing operation that operates on the columns of the block, providing diffusion.
AddRoundKey
Similar to the initial round, each byte of the block is XORed with the corresponding byte of the round key.
Final Round (differs for AES-128, AES-192, and AES-256)
MixColumns are not performed for AES-128 in the final round. The number of rounds and the key size determine the number of transformation rounds.
Decryption
The decryption process is essentially the reverse of encryption. It involves an inverse series of transformations using a set of round keys derived from the original key.
Let’s consider a brief example of encrypting a message “CONFIDENTIAL” using AES-256:
Generate a strong 256-bit key for AES-256 encryption.
Apply the AES encryption process with 14 rounds (AES-256). Each round involves substitution, shifting, mixing, and further encryption steps. For simplicity, let’s represent the encryption result as “X1Y2Z3…”.
The encrypted message, or ciphertext, is now “X1Y2Z3…” and appears as random data.
Now, imagine sending this ciphertext over the internet. The recipient, possessing the same 256-bit key, can use the reverse process to decrypt the message and reveal the original content “CONFIDENTIAL.” The security of AES-256 ensures that even with significant computational power, attempting to decipher this message without the proper key would be practically impossible within a reasonable timeframe.
AES (Advanced Encryption Standard), initially developed by NIST for government use, has become a cornerstone in public and private applications. It finds applications in diverse sectors, such as VPNs, password managers, mobile applications, wireless networks, file encryption, and video games.
For instance, in VPNs like PureVPN, AES secures internet traffic, while password managers like Keeper use AES to protect stored passwords. Video game developers leverage AES to combat piracy by encrypting game data.
AES is also employed in critical areas, including encrypting data on hard drives, securing electronic communications in messaging apps, and forming an integral part of programming libraries such as Java, Python, and C++. Its role extends to file compression programs and internet browsers.
| Advantage | Disadvantage |
| AES is a globally recognized and widely adopted encryption standard. | AES-256, especially, can be computationally intensive, requiring more processing power. |
| AES provides advanced security against various cryptographic attacks, ensuring data confidentiality. | Proper key management is crucial for AES. The security is only as strong as the protection of the encryption keys. |
| ES can be used for various applications, from securing data on hard drives to internet communications. | As quantum computing evolves, it may threaten AES, although this is a concern for the distant future. |
| Offers flexibility with key sizes (128-bit, 192-bit, and 256-bit) to cater to different security needs. | Side-channel attacks, where attackers exploit information leaked during encryption, could pose a threat. |
| Being a NIST-approved standard, AES is recommended for government and private-sector use. | The initial key setup and distribution can be a logistical challenge, especially in large systems. |
| Feature | DES | Triple- DES | AES |
| Full Name | Data Encryption Standard | Triple Data Encryption Algorithm | Advanced Encryption Standard |
| Year Introduced | 1976 | 1998 (as a response to DES limitations) | 1999 |
| Key Length | 56 bits (weak) | 112 or 168 bits (only 112 bits secure) | 128, 192, or 256 bits |
| Block Size | 64 bits | 64 bits | 128 bits |
| Security | Weak, vulnerable to brute-force attacks | It is more secure than DES but still considered less secure than AES | Strong, no known successful attacks |