Spoofing is an impersonation of a user, device, or client on the Internet. It is often used during a cyberattack to disguise the source of attack traffic.
The most common forms of spoofing are:
- DNS server spoofing
Modifies a DNS server to redirect a domain name to a different IP address. It is typically used to spread viruses.
- ARP spoofing
Links a perpetrator’s MAC address to a legitimate IP address through spoofed ARP messages. It is typically used in denial of service (DoS) and man-in-the-middle attacks.
- IP address spoofing
Disguises an attacker’s origin IP. It is typically used in DoS assaults.
What is IP Spoofing?
IP spoofing is the creation of Internet Protocol (IP) packets that have a modified source address to either hide the identity of the sender, to impersonate another computer system, or both. It is a technique often used by bad actors to invoke DDoS attacks against a target device or the infrastructure surrounding that device.
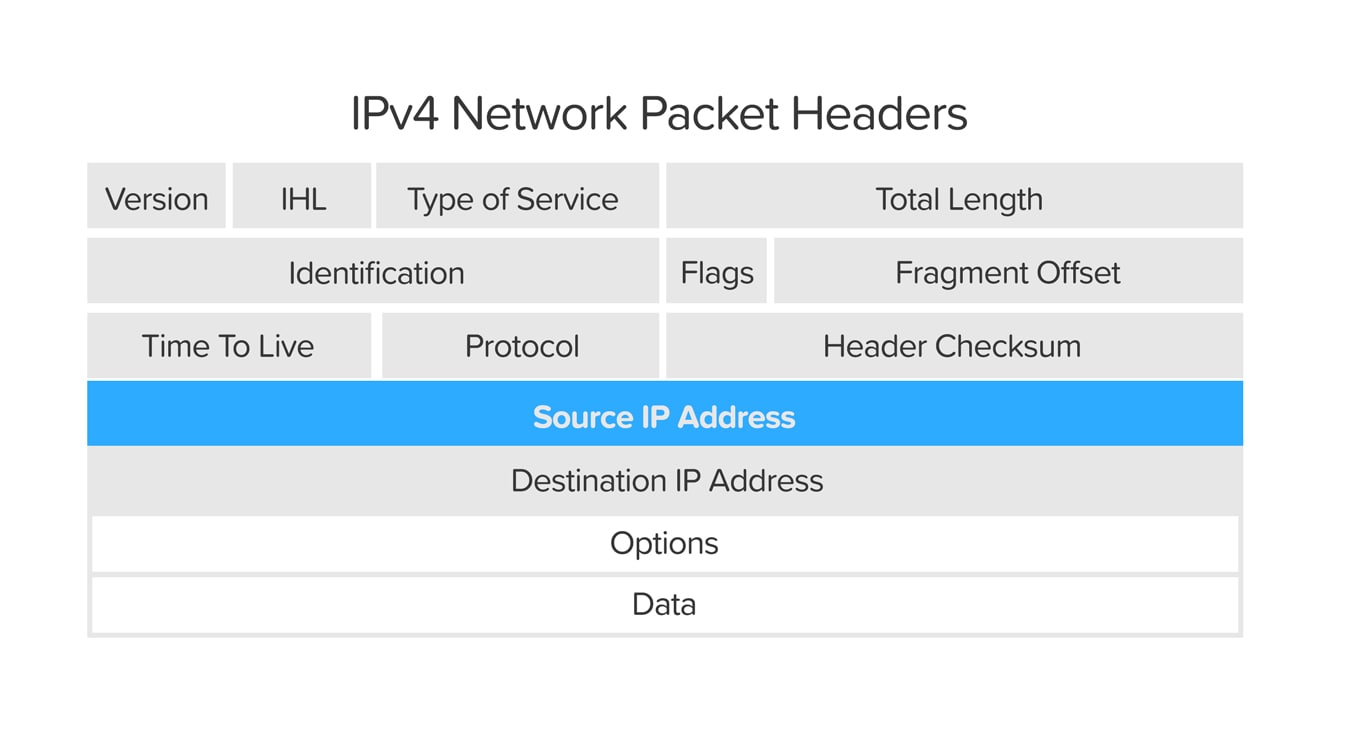
Sending and receiving IP packets is a primary way in which networked computers and other devices communicate and constitutes the basis of the modern Internet. All IP packets contain a header that precedes the body of the packet and contains important routing information, including the source address. In a normal packet, the source IP address is the address of the sender of the packet. If the packet has been spoofed, the source address will be forged.
IP Spoofing is analogous to an attacker sending a package to someone with the wrong return address listed. If the person receiving the package wants to stop the sender from sending packages, blocking all packages from the bogus address will do little good, as the return address is easily changed. Similarly, if the receiver wants to respond to the return address, their response package will go somewhere other than to the real sender. The ability to spoof the addresses of packets is a core vulnerability exploited by many DDoS attacks.
How Does IP Spoofing Work?
To start, a bit of background on the Internet is in order. The data transmitted over the Internet is first broken into multiple packets, and those packets are transmitted independently and reassembled at the other end. Each packet has an IP (Internet Protocol) header that contains information about the packet, including the source IP address and the destination IP address.
In IP spoofing, a hacker uses tools to modify the source address in the packet header to make the receiving computer system think the packet is from a trusted source, such as another computer on a legitimate network, and accept it. Because this occurs at the network level, there are no external signs of tampering.
IP spoofing facilitates anonymity by concealing source identities. This can be advantageous for cybercriminals for these three reasons.
- Spoofed IP addresses enable attackers to hide their identities from law enforcement and victims.
- The computers and networks targeted are not always aware that they’ve been compromised, so they don’t send out alerts.
- Because spoofed IP addresses look like they are from trusted sources, they’re able to bypass firewalls and other security checks that might otherwise blacklist them as a malicious source.
What are the Different Types of IP Spoofing Attacks?
IP spoofing attacks can take several forms. It depends on the vulnerabilities of victims and the goals of the attackers. Here are a few common malicious uses for IP spoofing:
- Masking Botnet Devices
IP spoofing can be used to gain access to computers by masking botnets, which are groups of connected computers that perform repetitive tasks to keep websites functioning. IP spoof attacks mask these botnets and use their interconnection for malicious purposes. That includes flooding targeted websites, servers, and networks with data and crashing them, along with sending spam and various forms of malware.
- DDoS Attacks
IP spoofing is commonly used to launch a distributed denial-of-service (DDoS) attack. A DDoS attack is a brute force attempt to slow down or crash a server. Hackers can use spoofed IP addresses to overwhelm their targets with packets of data. This enables attackers to slow down or crash a website or computer network with a flood of Internet traffic, while masking their identity.
- Man-in-the-Middle Attacks
IP spoofing is also commonly used in man-in-the-middle attacks, which work by interrupting communications between two computers. In this case, IP spoofing changes the packets and then sends them to the recipient computer without the original sender or receiver knowing they have been altered. An attacker becomes the so-called “man in the middle,” intercepting sensitive communications that they can use to commit crimes like identity theft and other fraud.
How to Protect Against IP Spoofing
Here are steps you can take to help protect your devices, data, network, and connections from IP spoofing:
Use Secure Encryption Protocols
to secure traffic to and from your server. Part of this is making sure “HTTPS” and the padlock symbol are always in the URL bar of websites you visit.
Be Careful of Phishing Emails
from attackers asking you to update your password or any other login credentials or payment card data, along with taking actions like making donations. Phishing emails have been a profitable tool for cybercriminals during the coronavirus pandemic. Some of these spoofing emails promise the latest COVID-19 information, while others ask for donations. While some of the emails may look like they are from reputable organizations, they have been sent by scammers. Instead of clicking on the link provided in those phishing emails, manually type the website address into your browser to check if it is legitimate.
Take Steps that will Help Make Browsing the Web Safer
That includes not surfing the web on unsecure, public Wi-Fi. If you must visit public hotspots, use a virtual private network, or VPN, that encrypts your Internet connection to protect the private data you send and receive.
Security Software Solutions
that include a VPN can help. Antivirus software will scan incoming traffic to help ensure malware is not trying to get in. It is important to keep your software up to date. Updating your software ensures it has the latest encryption, authentication, and security patches.
Set up a Firewall to Help Protect
your network by filtering traffic with spoofed IP addresses, verifying that traffic, and blocking access by unauthorized outsiders. This will help authenticate IP addresses.
Secure your Home Wi-Fi Network
This involves updating the default usernames and passwords on your home router and all connected devices with strong, unique passwords that are a combination of 12 uppercase and lowercase letters, at least one symbol, and at least one number. Another approach is using long passphrases that you can remember but would be hard for others to guess.
Monitor Your Network
for suspicious activity.
Use Packet Filtering Systems
like ingress filtering, which is a computer networking technique that helps to ensure the incoming packets are from trusted sources, not hackers. This is done by looking at packets’ source headers. In a similar way, egress filtering can be used to monitor and restrict outbound traffic, or packets that don’t have legitimate source headers and fail to meet security policies.
Real Uses for IP Spoofing
IP spoofing may also be used by companies in non-malicious ways. For example, companies may use IP spoofing when performing website tests to make sure they work when they go live.
In this case, thousands of virtual users might be created to test a website. This non-malicious use helps gauge a website’s effectiveness and ability to manage numerous logins without being overwhelmed.
Resources:
www.us.norton.com/internetsecurity-malware-ip-spoofing-what-is-it-and-how-does-it-work.html
www.cloudflare.com/learning/ddos/glossary/ip-spoofing/




