In today’s digital landscape, securing sensitive information and maintaining the integrity of IT environments are paramount concerns for organizations. Microsoft’s Active Directory (AD) is a critical component for many enterprises, serving as a centralized system for managing user identities and permissions. However, like any complex system, AD is not without its vulnerabilities. In this blog, we will delve into two critical security concerns: ESC1 (Certificate-Based Privilege Escalation) and ESC8 (NTLM Relay Attack via AD CS Web Enrollment). We will explore what these vulnerabilities are, how they can impact your organization, and most importantly, how to mitigate them effectively.
Understanding ESC1: Certificate-Based Privilege Escalation
Vulnerability Description
ESC1 is a privilege escalation attack that specifically targets Microsoft Active Directory Certificate Services (AD CS). Attackers leverage vulnerabilities in certificate templates to gain unauthorized access to higher privileges, potentially compromising the entire AD environment. In essence, it’s a technique that allows an attacker to escalate their privileges from a low-level domain account to domain administrator access, a nightmare scenario for any organization.
Mitigation Steps
To protect your AD environment from ESC1, follow these crucial mitigation steps:
-
Review and Secure Certificate Templates
Conduct a Comprehensive Audit
Begin by conducting a thorough audit of all your certificate templates. Identify templates that possess vulnerable attributes.
-
Modify Vulnerable Templates
For templates identified as vulnerable, make the necessary modifications to enhance security. Pay attention to the following key attributes:
-
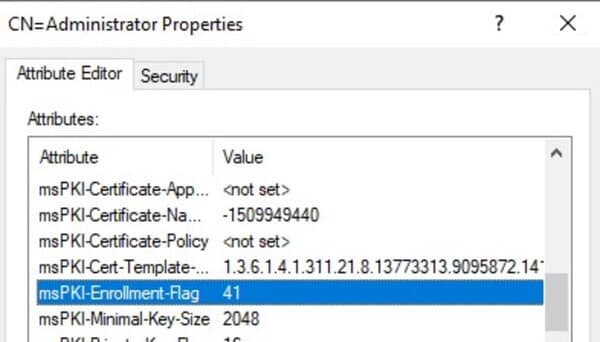
msPKI-enrollment-flag
Ensure this attribute is set to “None” or 0, or requires CA manager approval for critical templates.
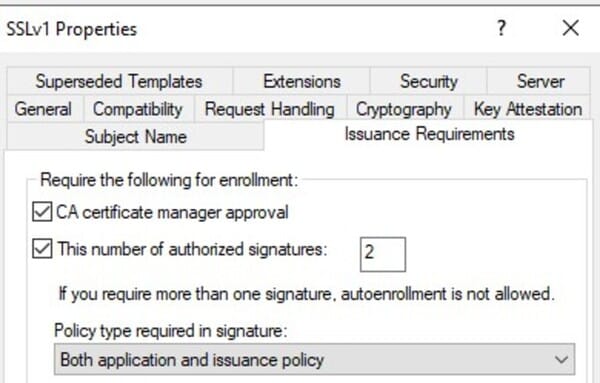
Authorized Signatures Required
Set the required number of authorized signatures based on your organization’s policy.
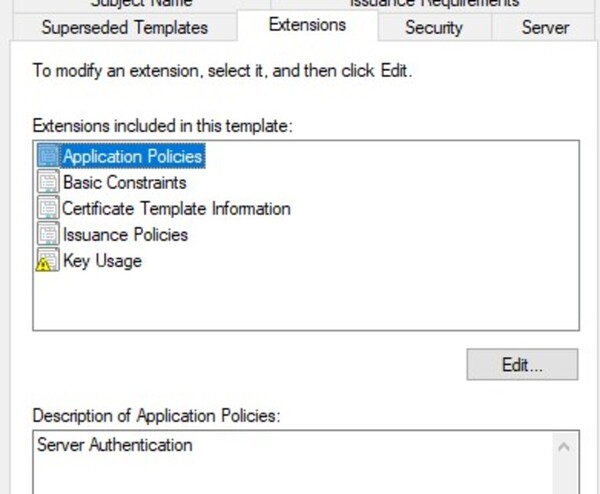
PKI-extended-key-usage
Review and restrict the certificate’s usage to only necessary purposes.
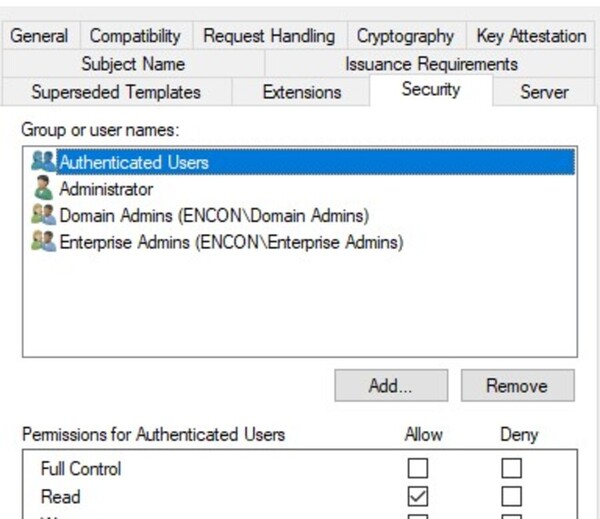
Enrollment Permissions
Restrict permissions for requesting certificates, avoiding overly permissive settings like “Everyone” or “Authenticated users.”
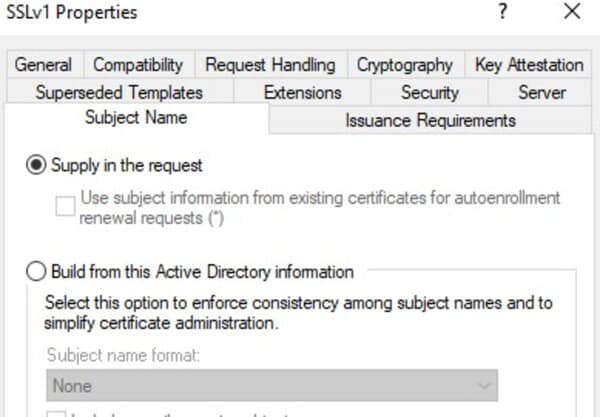
Allow Subject Information in Certificate Request
Configure templates to permit clients to specify SAN attributes in CSR (Certificate Signing Request).
-
Update AD CS to Account for KB5014754
Deploy the KB5014754 update to your AD CS environment to incorporate necessary security enhancements.
Impact on Environment for ESC1 Mitigation
Implementing these measures enhances the security of your AD CS environment but may require some administrative effort. It can lead to a more restrictive process for requesting and issuing certificates, which could affect usability. Users may need to adapt to new workflows for certificate requests. However, the trade-off is a significantly reduced risk of privilege escalation attacks.
Understanding ESC8: NTLM Relay Attack via AD CS Web Enrollment
Vulnerability Description
ESC8 targets the web enrollment interface feature of AD CS, exploiting NTLM relay attacks. Attackers can use this technique to authenticate as a domain controller, potentially gaining access to sensitive resources. It’s a serious security concern because it allows attackers to leverage AD CS web interfaces to compromise AD environments.
Mitigation Steps
To safeguard your organization from ESC8, follow these essential mitigation steps:
-
Secure Web Enrollment Interfaces
- Ensure that all AD CS web interfaces have HTTPS enabled. This security measure protects against NTLM relay attacks by encrypting communication between clients and the web interfaces.
-
Limit Certificate Templates
- Restrict certificate templates that allow client authentication and domain computer enrollment. By narrowing the templates’ scope, you reduce the potential attack surface.
Impact on Environment for ESC8 Mitigation
Implementing HTTPS for web enrollment is a necessary security measure that may require obtaining and deploying SSL certificates. While limiting access to enrollment endpoints might affect some legitimate users, it is essential to ensure proper access controls are in place. Implementing stronger authentication methods may necessitate user reconfiguration or reauthentication. The resulting security benefits far outweigh the inconvenience caused by these changes.
Conclusion
In today’s threat landscape, organizations must be proactive in identifying and mitigating security vulnerabilities within their IT infrastructure. ESC1 and ESC8 vulnerabilities in Active Directory are critical concerns that demand immediate attention.
By understanding these vulnerabilities, following the recommended mitigation steps, and taking proactive security measures, organizations can significantly reduce the risk of privilege escalation attacks and NTLM relay attacks via AD CS web enrollment.
Securing your AD environment is an ongoing process that requires vigilance and continuous monitoring. Regular audits, updates, and adherence to best practices are crucial in maintaining a robust security posture. Remember, the security of your organization’s digital assets is only as strong as your weakest link, so taking steps to address vulnerabilities like ESC1 and ESC8 is a fundamental aspect of safeguarding your enterprise.