Publishing Root CA’s Certificate Revocation List (CRL)


Organizations must update their Root Certification Authority’s (CAs) CRL once or twice a year. This operation is important and necessary to ensure that the Microsoft PKI remains operational and trusted. If the Root CA’s CRL is not published on time, it may cause the operation to break and halt all processes. The PKI would not be trusted anymore, and this could be catastrophic for the operation.
The whole PKI and the infrastructure that uses its certificate would become unoperational, and the organization may face an outage.
First, we will open PKIView.msc and check when the Root CA’s CRL expires.
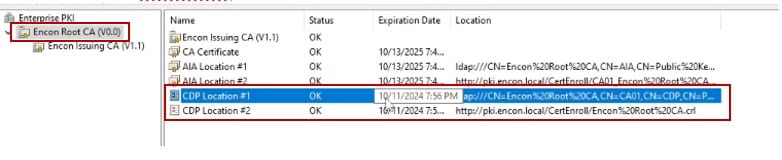
Next, we navigate to the Root CA and open command prompt on administrative privileges.
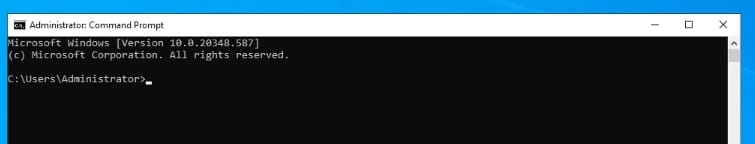
We run the command certutil -crl to publish the Root CA’s CRL. This will publish a new CRL for the Root CA.
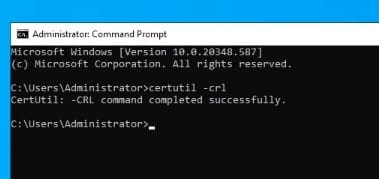
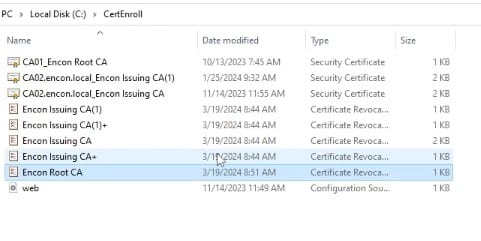
We will then open up the folder in “C:\Windows\System32\CertSrv\CertEnroll\” to check if the CRL is present.
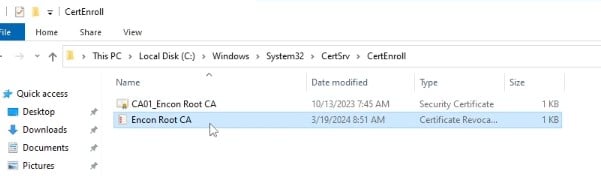
We will open the CRL file to check the date of expiration.
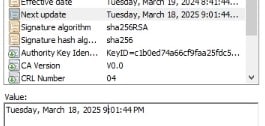
Now, we will copy the file onto a USB drive or temporary folder. Since Root CA is supposed to be offline, we will advise that the file can be copied to a USB drive so we can copy it onto our Issuing CAs and CDP servers.
Note: Instead of Issuing CA, we can also use any machine that is joined to the domain.
We will copy the CRL file into one of our Issuing CAs (or any other domain joined machine).
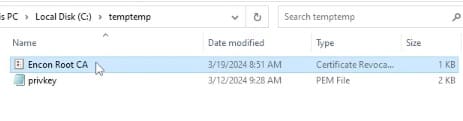
We will open a command prompt with administrative privileges and navigate to the folder containing the CRL file.
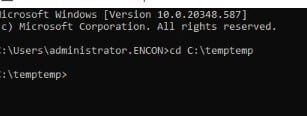
Now we will run the command certutil -f -dspublish “*.crl”
Note: In this case, CA01 is the hostname of the RootCA.
Next, we copy the CRL to each server, which serves as a CDP/AIA point.
Our CRL files should be circulated to every location needed for the PKI to function.
Now, we will navigate back to the issuing CA, refresh PKIView.msc, and check when the new CRLs are expiring.
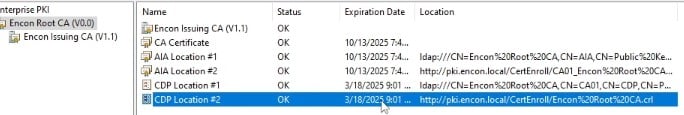
The new dates should now be different from the dates we noted in the prerequisites.
We will now open a command prompt with administrative privileges on Issuing CA and run the command certutil -crl
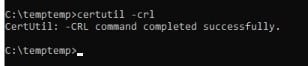
Once both of them are satisfied, we can conclude this objective to be completed.
Publishing your Root CA’s CRL on time is necessary for a PKI to function properly and remain operational. Since an organization’s infrastructure depends on PKI, it becomes a crucial part of the organization’s operations, as a non-functioning PKI can result in outages throughout the organization. This article should help organizations publish their Root CA’s CRL without any major hurdles.
Encryption Consulting provides specialized services customized to identify vulnerabilities and mitigate risks by providing PKI Services. Our strategic guidance aligns PKI solutions with organizational objectives, enhancing efficiency and minimizing costs. By partnering with Encryption Consulting, organizations can unlock the full potential of PKI solutions, realizing tangible financial benefits while maintaining strong security measures.
Encryption Consulting’s PKIaaS provides a flexible and secure PKI solution tailored to your specific needs, offering benefits such as customizable options, high assurance standards, and a low-risk managed approach. PKIaaS automates key and certificate management tasks, reducing operational overhead and minimizing the risk of human error. Additionally, it enhances network visibility by requiring certificates for access. It will take care of building the PKI infrastructure to lead and manage the PKI environment (cloud/ hybrid or On-Prem) of your organization.
CertSecure Manager has a comprehensive suite of lifecycle management features. From discovery and inventory to issuance, deployment, renewal, revocation, and reporting. CertSecure provides an all-encompassing solution. Intelligent report generation, alerting, automation, automatic deployment onto servers, and certificate enrollment add layers of sophistication, making it a versatile and intelligent asset.