CertSecure Manager
Prevent Outages Before They Happen!
Your One-Stop Solution for All Your Digital Certificate Management Requirements.
CertSecure Manager
Your One-Stop Solution for All Your Digital Certificate Management Requirements.
Automated renewals eliminate expirations and downtime, ensuring continuous security.
Instantly issue, revoke, and renew certificates with automation, adapting quickly to security needs.
Reduce manual effort with centralized management, policy enforcement, and automated certificate workflows.
Seamlessly connect with existing PKI, ITSM, and security tools without disrupting workflows or operations.
Gain complete certificate visibility, track expirations, and automate renewals in one unified dashboard.
Simplify certificate management with automation, security, and seamless integration across your IT ecosystem.
Learn More
Automate
Enforce
Streamline
Effortlessly integrate CertSecure Manager into your existing infrastructure with powerful automation and flexible APIs. Streamline certificate issuance, renewal, and compliance across diverse environments while ensuring security, scalability, and minimal manual intervention.
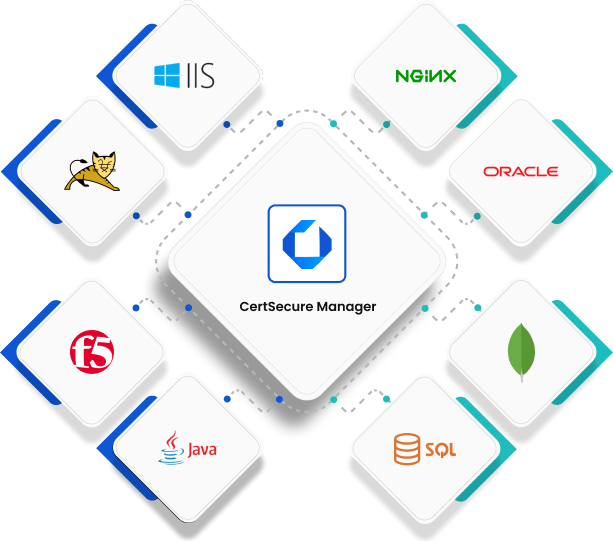
Enable seamless certificate automation, lifecycle management, and security across diverse infrastructures to mitigate outages, streamline operations, and ensure compliance.




Deploy CertSecure Manager in the environment that best fits your security, scalability, and operational needs. Choose on-premises for full control, cloud for flexibility, SaaS for simplicity, or hybrid for a balanced approach.
Maintain full control and security with an in-house deployment tailored to your infrastructure.
Leverage flexible, scalable deployment with seamless integration into your preferred cloud provider.
Experience hassle-free deployment with a fully managed, cloud-hosted solution for streamlined certificate management.
Combine on-premises control with cloud scalability for a balanced, flexible deployment strategy.
Global Encryption Trends 2025 Report
Spanning multiple geographies and industry sectors across the globe for the latest insights.
Read more
Certificate Lifecycle Maturity Model
Enhance automation, improve resilience, and achieve crypto agility with our white paper.
Read more
Discover Our Bi-Weekly Podcast: The Encryption Edge
Bridging the gap between technical depth and practical application to decode the complexities of modern cryptography.
Listen Now