Introduction
Let’s briefly discuss Code signing.
Code signing is a method of putting a digital signature on a file, document, software, or executable to test its authenticity and genuineness in regards to the functionality and features that it provides. This also ensures that the software entity (file, document, software, or executable) is not tampered with while in transit.
Code signing has become a quintessential requirement for software developers, The reason is code signing ensures a trust among users for the software, and also provides confidence to users to avoid the warning messages which appear when a user downloads/installs the executable in their environment.
What is Time Stamping?
Time stamping is an optional part of the code signing process, which allows software to recognize whether an applied code signing signature is valid–even after a code signing certificate expires. In other words, we can say that time stamping preserves the signature applied to the software.
Whenever the signed software’s executable is run/executed on any client machine/system, its digital signature is verified by the user’s operating system. Now, suppose the user has time stamped the software. The users’ computer will verify the signature based on the time it was digitally signed, rather than the current time of the system when the software is executed.
Below is the work flow for a time stamping process:
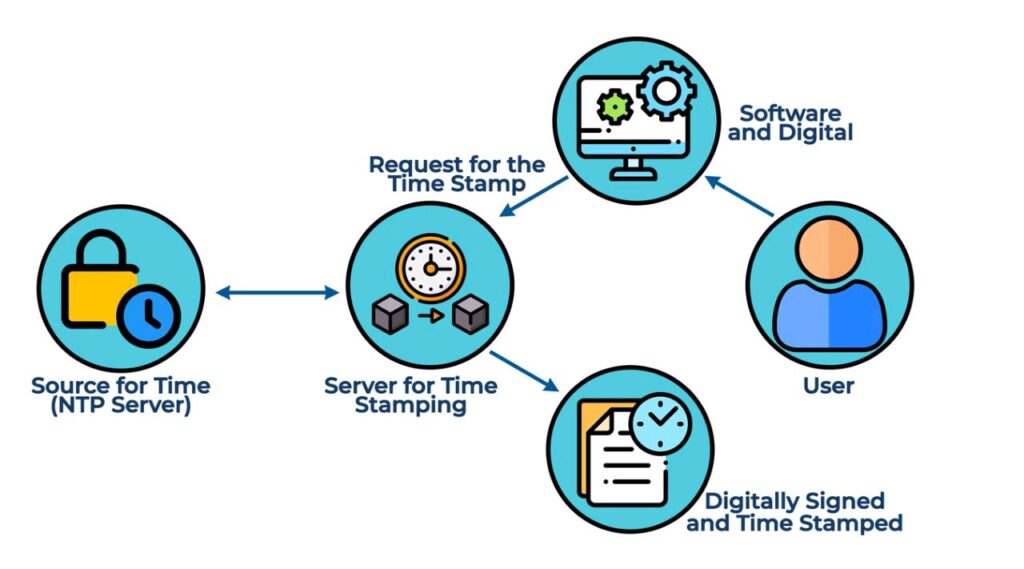
Time Stamping is provided by the Time Stamp Authority (TSA) which uses Public Key Infrastructure (PKI) principles and technology for applying timestamps.
The following steps are performed to Time Stamp software:
- A hashed value is created and sent to the TSA by the requester for the software that needs to be time stamped.
- Hash value, authoritative time and other related information such as data and time of the digital signature are combined by the TSA and signed by its private key to create a new hash value.
- Next, the new hash and the software’s hash is bundled up and sent to the requester.
- A requester’s application then receives the bundle and verifies it. Once the verification is done, the time stamp becomes valid and embedded within the code signature of the software.
Let’s try to understand this in terms of a real-world scenario.
Let’s assume that you are the developer, you did the code signing of your software, and the certificate is valid from January 2021 to till January 2022. Now, a user who downloads your software on October 2021 forgets to install it due to his busy schedule. He tries to install the software in February 2022, but he gets an error.
Let’s understand the same scenario with the only exception that you have time stamped the software in July 2021. Now, when the user tries to install the software in February 2022, he is able to install it and doesn’t get any error at all. This is the effect of Time Stamping!!
Protocols used in Time Stamping
The following protocols are used in Time Stamping software:
RFC 3161
RFC 3161 is updated and designated as RFC 5035 which additionally allows the use of ESSCertIDv2.
Microsoft Authenticode
Microsoft Authenticode can be utilized in various formats such as .cab, .exe, .ocx, and .dll
Code Sign Time Stamping best practices
The following best practices can be adapted while Code sign Time Stamping is done:
- Always make sure that the time stamping option is enabled in your signing tool, such as Microsoft Signtool. Also, choose a signing tool which supports the time stamping option as it’s an optional feature by default.
- Ensure that time stamping is included as part of your software development lifecycle process. This will avoid any unexpected issues occurring due to version mismatches.
- Document the complete process for your signing tool while using the time stamping option, as every sign tool has a different workflow for time stamping. Also, distribute this document to every stakeholder involved in the code signing process.
- Time stamping allows the client system to verify if the software was signed before or after the revocation of the code signing certificate. So, if you want to revoke the code signing certificate for any reason, such as private key compromise, you may do so. The client system will not have any difficulty while installing the software, as time stamping was done when the code signing certificate was valid.
Conclusion
Time stamping appears to be an optional step, whereas it is a vital component of the code signing ecosystem in your organization. Without time stamping, expiration/revocation of code signing certificates would lessen the confidence of customers in the same software product. Timestamps make sure that even if certificates lose their validity or are revoked for some reason, their signatures remain valid, secure and trusted.