Troubleshooting LDAP issues can seem tricky, which is where this blog should help you on your troubleshooting journey. We will discuss 2 scenarios that should solve your LDAP errors.
Scenario 1
This scenario takes into consideration that your certificate was not published in Active Directory. To resolve this issue run the commands:
To resolve AIA issues: certutil -dspublish -f <path to root certificate> RootCA
To resolve CDP issues: certutil -dspublish -f <path to root crl> <hostname>
If the issue exists for Issuing CA, you need to replace RootCA with SubCA and use the issuing CA’s hostname.
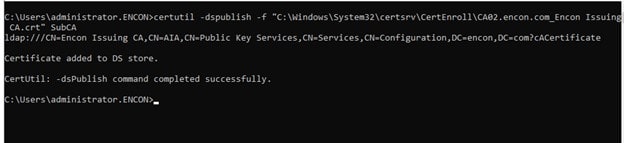
After this, you can check if the certificate is present in Active Directory or not.
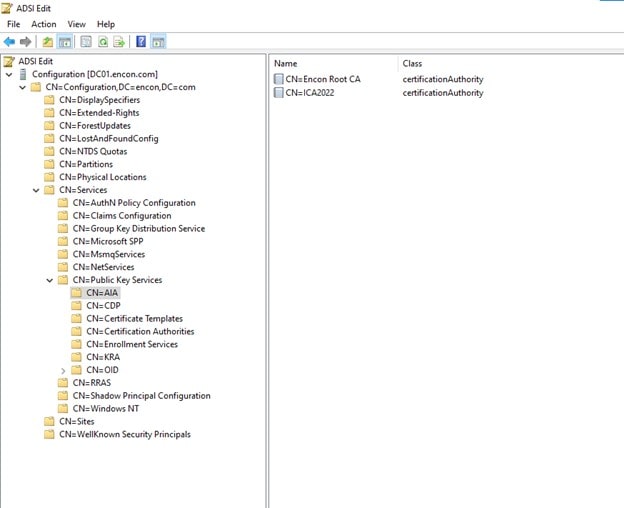
For that, log in to Domain Controller, and open adsiedit.msc, connect to Configuration, and then we can navigate to Services > Public Key Services > AIA and check the present certificates. If the certificates are present and you still receive that error, then follow Scenario 2.
Scenario 2
If Scenario 1 does not fix the issue, then it may be possible that LDAP URL was incorrectly configured while configuring the AIA points on your Root CA.
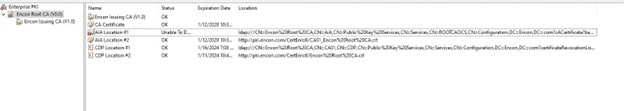
To resolve this, first open PKIView.msc to check which LDAP URL your PKI is looking for. For this scenario, my PKI is looking for:
ldap:///CN=Encon%20Root%20CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=ROOTCAOCS,CN=Configuration,DC=Encon,DC=com?cACertificate?base?objectClass=certificationAuthority
But the certificate is published on:
CN=Encon Root CA,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=encon,DC=com
You can check the distinguished name on the object present in ADSIedit.msc.
To resolve this, we would follow the steps:
-
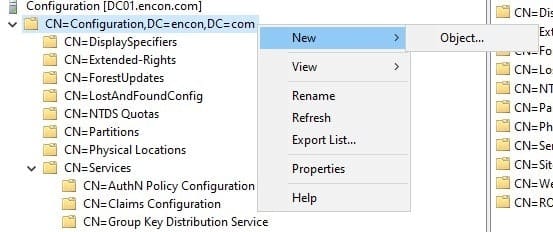
Create a new Container Structure in your Domain partition
CN=Encon%20Root%20CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=ROOTCAOCS,CN=Configuration,DC=Encon,DC=com
-
Create an Object under Configuration
-
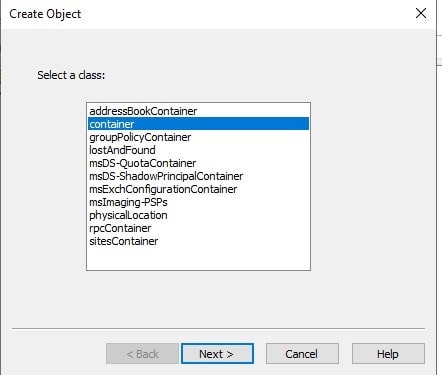
Choose the object class “container”
-
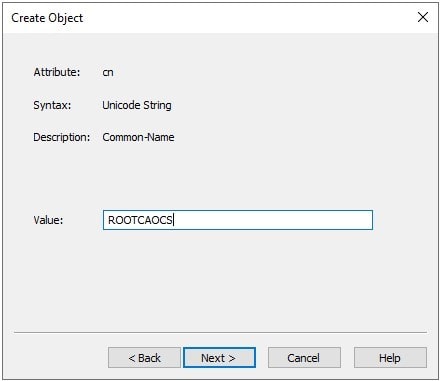
Provide the exact value ROOTCAOCS as highlighted above
-
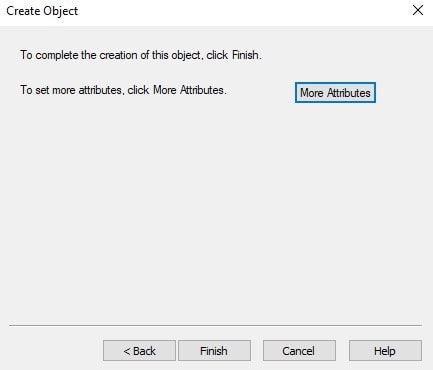
Click Finish
-
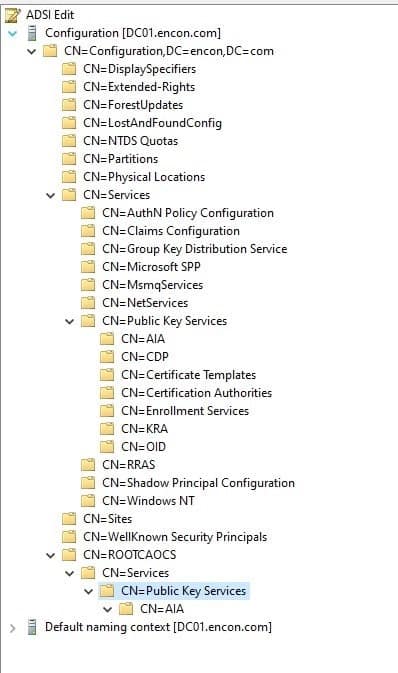
Follow steps 2-5 to create further containers in ROOTCAOCS > Services > Public Key Services > AIA
-
Run the command on Domain Controller to extract the published object
LDIFDE -d ” CN=Encon Root CA,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=encon,DC=com” -f c:\export.txt
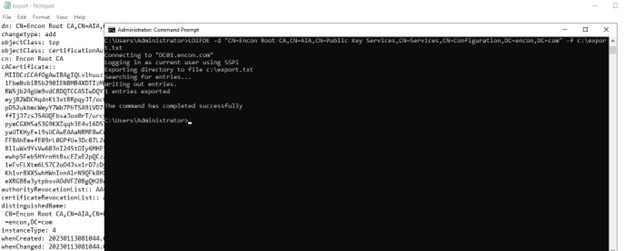
-
Make changes to export.txt where you replace the existing dn with the LDAP URL your PKI is looking for
CN=Encon Root CA,CN=AIA,CN=Public Key Services,CN=Services,CN=ROOTCAOCS,CN=Configuration,DC=encon,DC=com
You also need to remove GUID, USN Information, and other details.
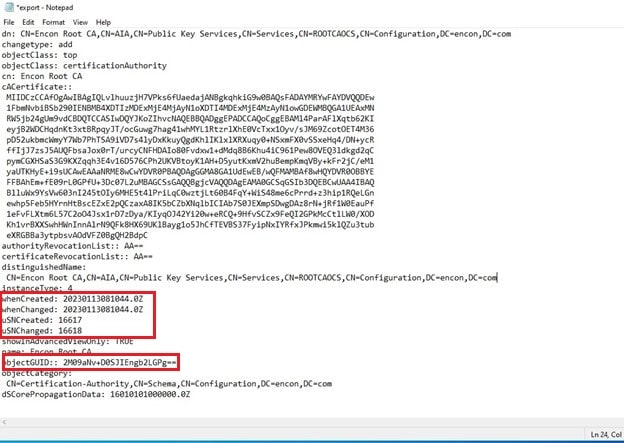
-
Publish the u ldifde -i -f c:\export.txt
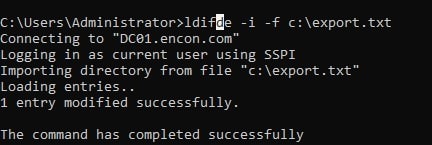
-
Object should now be in new place
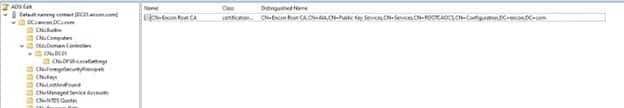
-
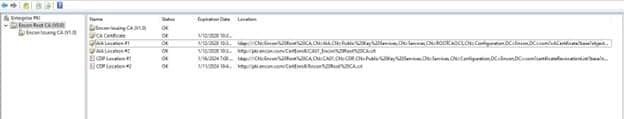
PKI View should show no errors
Conclusion
Issues with CDP and AIA LDAP locations can be tricky. Misconfiguration can often cause issues, which can be harder to track. This should solve all the LDAP URL issues that you may face in your PKI environment. LDAP issues can be tricky at times, but if Scenario 1 does not fix your issue, Scenario 2 definitely will.




