Certificate revocation is the process in which a certificate’s usage is terminated before the validity period expires. The choice to revoke involves knowing the available revocation reasons, mapping the revocation reasons to your organization’s revocation policy, and then performing the revocation.
Reasons for certificate revocation
Certificates are revoked by declaring them invalid if the relying parties are not using them. There can be multiple reasons for revoking a certificate which are:
-
AffiliationChanged
An individual is terminated, resigns, or dies, or the computer account to which the certificate was issued is no longer in use. These revocation reasons can also be used if a person changes roles within an organization and no longer requires using the certificate associated with that person’s previous role.
For example, an employee could move from the purchasing department and no longer require a certificate to authorize purchase requests.
-
CACompromise
You suspect that a CA’s private key has been compromised and is in the hands of an unauthorised individual. If a CA’s private key is revoked, the CA hierarchy considers all certificates below that CA (Certificate Authority) revoked.
-
CertificateHold
A temporary revocation that indicates a CA will not validate a certificate at that specific time.
Note: Although CertificateHold allows a certificate to be unrevoked, using the CertificateHold reason code is not recommended because it makes determining whether a certificate was valid at a specific time difficult.
-
CessationOfOperation
A server or workstation is decommissioned, and all certificates issued to the server are no longer required. When decommissioning a CA, you can also use this revocation reason.
-
KeyCompromise
You suspect that the private key associated with a certificate is compromised.
For example, if a laptop belonging to a user in your organization is stolen, any private keys stored on the laptop may be compromised.
-
RemoveFromCRL
You can unrevoke a certificate that you revoked using CertificateHold. The certificate is still listed in the CRL after the unrevocation process, but it also appears in a delta CRL with the revocation code set to RemoveFromCRL. The CA removes the certificate from all forms of the CRL when the next base CRL is published. If delta CRLs are not used, the certificate is removed from the following base CRL.
-
Superseded
A new certificate must be issued if an issued certificate is replaced for any reason with a new updated certificate. For example, if you update a certificate template and reissue certificates, you could revoke the previous certificate with this reason code.
-
Unspecified
You can revoke a certificate without providing a specific revocation code. However, Unspecified is not recommended because it does not provide an audit trail identifying why a certificate was revoked.
How to perform certificate revocation?
To revoke a certificate, a user must be designated as a certificate manager. You designate a user as a certificate manager by assigning the user or a group containing the user the Issue and Manage Certificates permission at the issuing CA. The permission assignment is performed by a CA Administrator, which is a user assigned the Manage CA permissions. Perform the following steps to provide the necessary permissions:
-
From Administrative Tools, open the Certification Authority console.
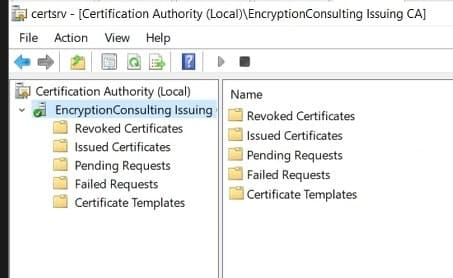
-
In the console tree, right-click CAName (where CAName is the logical name of the CA) and then click Properties.
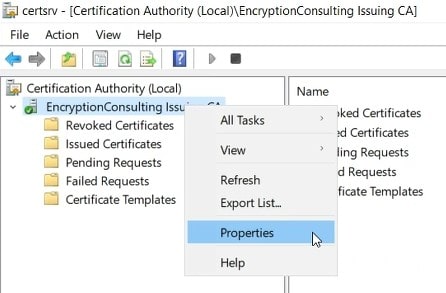
-
In the CAName Properties dialog box, select the Security tab to ensure that the user account or a group that the user is a member of is assigned the Issue and Manage Certificates permission.
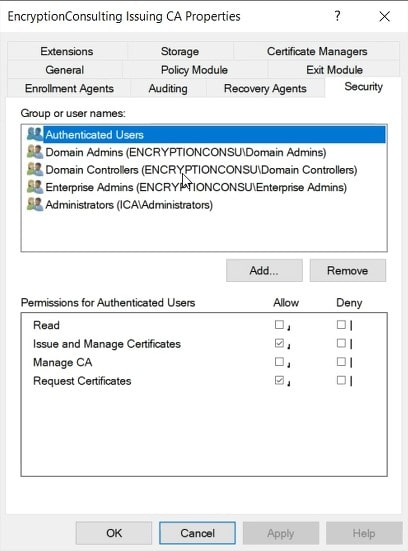
Once you assign the necessary permissions, the following procedure revokes a certificate:
-
From Administrative Tools, open the Certification Authority console.

-
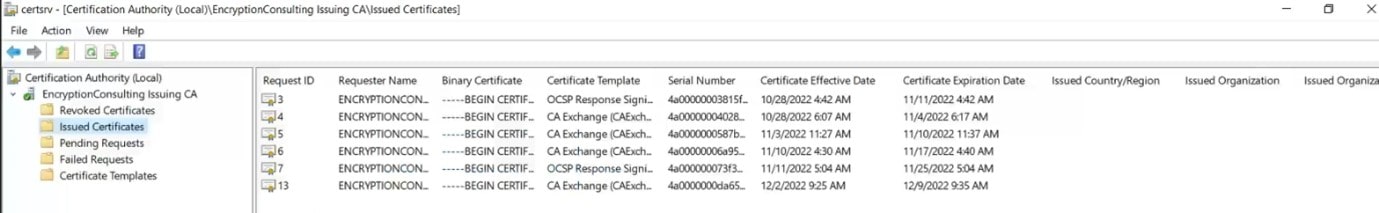
In the console tree, expand CAName and click Issued Certificates
-
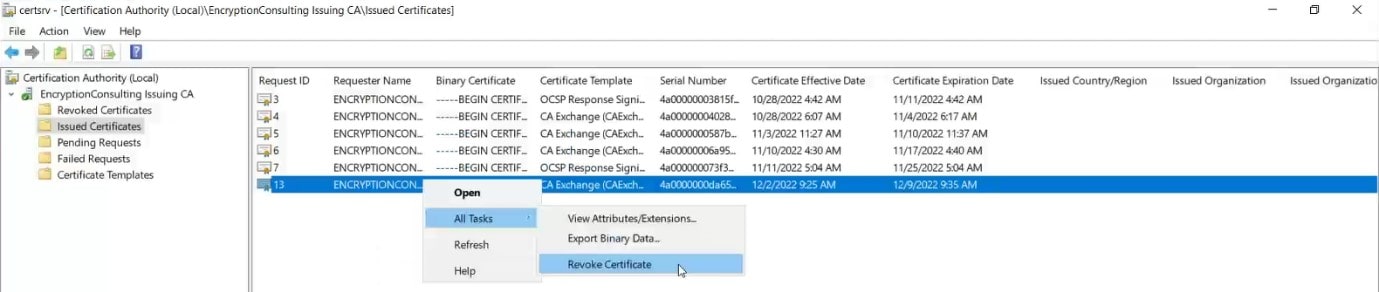
In the details pane, find the certificate you need to revoke, right-click the certificate, point to All Tasks, and click Revoke Certificate.
-
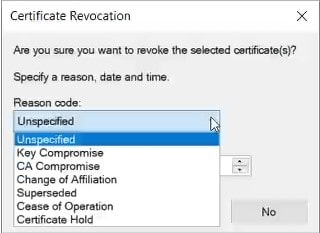
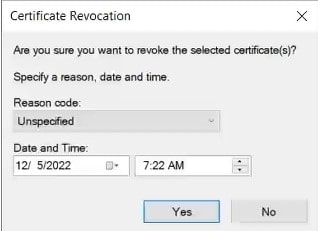
Select the appropriate reason code in the Reason Code drop-down list in the Certificate Revocation dialog box, and then click Yes.
-
Check if the certificate revoked recently is visible in the revoked certificates section.
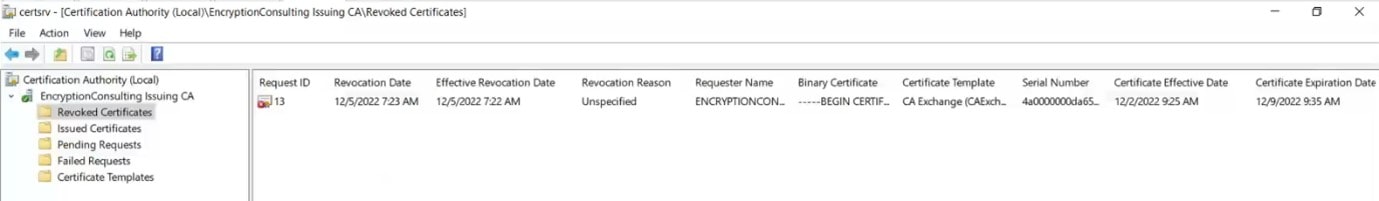
How to identify revoked certificates?
Public key infrastructure (PKI) provides three ways to determine if a certificate has been revoked:
-
Base CRL
Certificate Revocation List (CRL) contains the serial numbers of certificates revoked by the CA that are signed with the CA’s private key. If you renew a CA’s certificate with a new key pair, the CA maintains two separate CRLs—one for each key pair maintained by the CA. All versions of the Microsoft Windows operating system recognize base CRLs.
-
Delta CRL
This contains only the serial numbers of certificates revoked by the CA since the last base CRL publication. Again, if the CA’s certificate is renewed with a new key pair, separate delta CRLs are maintained for each CA key pair. Delta CRLs allow you to publish revocation information quicker and allow smaller updates to be downloaded by client computers.
-
OCSP
Online Certificate Status Protocol (OCSP) provides a responder service that can either connect directly to a CA database or inspect the base and delta CRLs published by the CA to determine the revocation status of a specific certificate.
Conclusion
We must revoke the certificates when not being used by relying on parties to prevent the attackers from impersonating themselves and causing significant damage. For more information, please get in touch with us at: [email protected]
Reference: PKI and certificate security by Brian Komar