- What are the Implementation Strategies for Homomorphic Encryption?
- How Homomorphic Encryption Works
- Emerging Footprints of Encrypted Processing in the Industry
- How Homomorphic Encryption Ensures Compliance with Regulatory Standards
- Industry Adoption Trends for Homomorphic Encryption and Market Growth
- Performance Challenges and Research Directions for Data Privacy
- Available Documentation and Industry Resources for Homomorphic Encryption
- How Can Encryption Consulting Help?
- Conclusion
Homomorphic encryption (HE) is an advanced cryptographic technique that allows data to remain encrypted even while it is being processed. In other words, a server can perform computations on ciphertexts, and the decrypted result matches the operation on the original plaintext. For example, one recent description explains that HE “enables calculations to be carried out on encrypted data”, producing an encrypted outcome that aligns with the computation on the raw data. This property enables cloud services or third parties to process sensitive data (e.g., analytics, AI/ML tasks) without ever seeing the unencrypted data.
In practice, the client generates a key pair (public and private) and an evaluation key. The public key is used to encrypt the data, and the evaluation key is given to the server to perform arithmetic on ciphertexts. The server never sees plaintext; it only returns an encrypted result. Finally, the client uses the private key to decrypt the outcome. Because HE “supports arbitrary computations on encrypted inputs”, it preserves data confidentiality end-to-end. As mentioned in the ISACA white paper, HE “can be used to obtain insights from computation without revealing the contents of a dataset” and it keeps personal data encrypted “at rest, in transit, and during computation”.
What are the Implementation Strategies for Homomorphic Encryption?
HE comes in three main implementation architectures, differing in what operations they allow on ciphertexts:
- Partially Homomorphic Encryption (PHE): Supports one kind of operation (either addition or multiplication) on ciphertexts an unlimited number of times. Classic examples include RSA or Paillier for adding encrypted values.
- Somewhat Homomorphic Encryption (SHE): Supports both addition and multiplication, but only for a limited number of total operations before the ciphertext noise grows too large.
- Fully Homomorphic Encryption (FHE): Supports arbitrary circuits, any combination of additions and multiplications (and thus any computable function). FHE enables unlimited chained operations on encrypted data.
The choice of architecture depends on the use case: PHE is simplest and fastest when only one operation is needed; SHE allows more flexibility but still limits complexity; FHE is the most powerful (truly general-purpose) but also the most complex. An authoritative ENISA report notes that FHE “has good protection and utility but poor performance,” reflecting this trade-off.
How Homomorphic Encryption Works
HE is typically based on lattice-based cryptography, such as learning with errors (LWE) or related problems. Modern FHE schemes (e.g., BFV, BGV, CKKS) use ring-LWE and number-theoretic transforms. These constructions conceal the data in structured, high-dimensional “noise” patterns, which are challenging for classical or even quantum computers to decipher. Lattice-based schemes used by FHE are considered post-quantum secure.
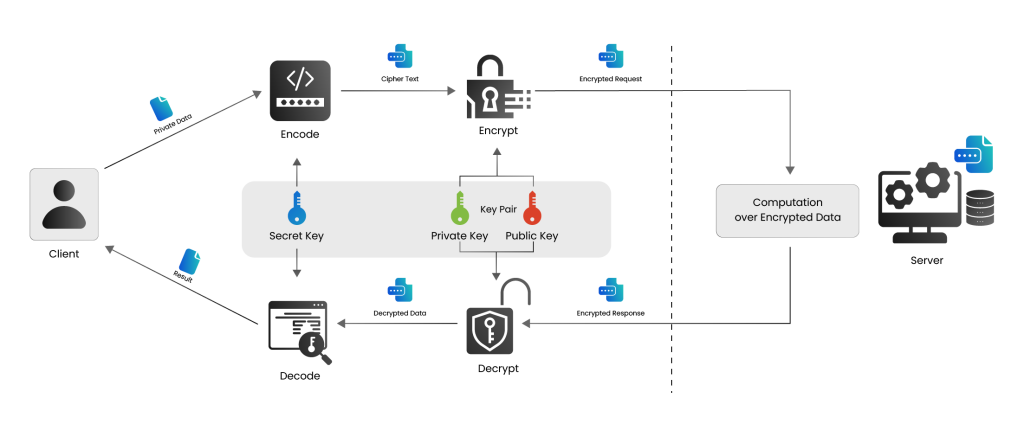
A Typical HE computation workflow looks like this:
- Encryption: The client encodes data into polynomials, encrypts it with a Ring-LWE-based scheme, and sends it to the server.
- Computation: The server performs additions and multiplications on ciphertexts, using NTT for efficiency and managing noise growth.
- Decryption: The client decrypts the result using the private key, recovering the computed output.
HE systems introduce a small amount of noise with each homomorphic operation; therefore, schemes must include a bootstrapping step to “refresh” ciphertexts or utilize built-in noise management. The net result is that an FHE system correctly performs the same computation as if it were done on plaintext. In practice, evaluation requires specialized software libraries, such as Microsoft SEAL, IBM HElib, PALISADE, and TFHE, or even hardware accelerators. For example, the Cloud Security Alliance (CSA) notes that as HE technology and hardware improve, FHE “is likely to become a ubiquitous information security tool” that encrypts data during all stages of use.
Emerging Footprints of Encrypted Processing in the Industry
HE is still an emerging technology, but several sectors are actively exploring it for privacy-preserving analytics:
- Finance: In the finance sector, banks and fintech companies manage highly sensitive customer information, such as transaction records and risk profiles. HE allows these organizations to perform analytics—like fraud detection and credit scoring—on encrypted data. IBM researchers, for instance, demonstrated encrypted machine learning (ML) on banking data with accuracy matching the unencrypted baseline. HE can also secure credit scoring or fraud detection by keeping all account data encrypted in a public cloud.
- Healthcare and Genomics: Healthcare providers and researchers often need to analyze patient data, such as electronic health records (EHRs) or genomic sequences, across multiple institutions without compromising patient privacy. HE enables this collaboration by allowing computations on encrypted records. For example, in 2019, Duality Technologies, Inc. and the Dana-Farber Cancer Institute collaborated to apply HE in the healthcare domain. The initiative focused on enabling secure, large-scale genome-wide association studies by analyzing multisourced, encrypted data without ever decrypting it, preserving privacy while advancing medical research. An AHIMA report highlights FHE’s promise for cross-institutional data analytics in healthcare. This makes HE a critical tool for secure, AI-driven healthcare analytics.
- Cloud Computing and SaaS: Any cloud-deployed computation (analytics, AI, databases) can, in principle, run on encrypted inputs. HE is revolutionizing cloud computing by enabling secure data processing in untrusted environments. A typical use case involves a client encrypting their data locally, uploading it to a cloud service, and receiving encrypted results after computation, all without the cloud provider accessing the plaintext. The cloud never decrypts the data; instead, it returns an encrypted result. As one IEEE source explains, this means “cloud providers will never have access to the unencrypted data they store and compute on,” making HE ideal for public cloud environments. This is particularly valuable for software-as-a-service (SaaS) platforms handling sensitive data, offering a new level of privacy in public cloud deployments.
- IoT and Edge Computing: With billions of IoT devices collecting personal data (such as health monitors, smart homes, and connected cars), HE can help secure data-in-use at the edge. For example, proposals for “quantum-resistant homomorphic encryption for IoT” show that FHE can encrypt sensor data to run analytics without revealing user identity. Although such systems incur extra computational cost, they demonstrate HE’s potential for secure edge-cloud processing in the quantum era.
- Elections and Voting: FHE can enable end-to-end verifiable elections by allowing vote tallying on encrypted ballots. Microsoft’s ElectionGuard utilizes HE to count votes without decrypting individual ballots, ensuring that votes remain secret while results are provably correct. This approach has been cited as a way to achieve “end-to-end verifiable elections” without exposing voter choices.
- Data Marketplaces and Outsourced Computation: Companies may sell the ability to query their data without revealing it. For instance, a search engine could compare encrypted queries against an encrypted index, returning results without seeing the query in plaintext. Financial and insurance industries also consider HE for privacy-preserving data sharing and model training.
The CSA working group summary specifically highlights finance, healthcare, and government as fields where cryptographic protection during processing is highly desirable. Many of these use cases are still under development or in the research and prototype stages, but they illustrate the broad potential of encrypted computation.
How Homomorphic Encryption Ensures Compliance with Regulatory Standards
HE ensures secure data processing, aligning with GDPR, HIPAA, and PCI DSS by keeping data encrypted, reducing breach risks, and supporting NIST and ISO/IEC standards.
GDPR (EU General Data Protection Regulation)
GDPR encourages strong data protection by design. While encrypted data is still “processing,” using HE can help satisfy security requirements. Notably, the European Data Protection Board (EDPB) guidelines on breach notification allow an exemption when data is rendered “unintelligible” by encryption. If HE ensures that leaked ciphertext cannot be decrypted by attackers (no key compromise), a breach of encrypted data “may not need to be notified”. However, legal analysts caution that HE itself is still considered a form of processing that requires a lawful basis under the GDPR.
In practice, HE is more often treated as a pseudonymization or encryption measure that reduces risk under GDPR. For example, experts note that HE’s encrypted data could be considered “de-identified” for certain regulatory purposes, as it’s not directly attributable to individuals without the keys. In short, HE ensures GDPR compliance by strengthening data security (Article 32: Security of Processing) and potentially easing breach liability; however, controllers must still maintain a valid consent or basis for processing, even when encrypting.
HIPAA (US Health Privacy Law)
Health Insurance Portability and Accountability Act (HIPAA) requires covered entities to protect electronic protected health information (ePHI) with “technical safeguards,” including encryption where reasonable. A detailed HIPAA analysis suggests that if PHI is encrypted with HE and the decryption key remains solely with the covered entity, that data could be treated as de-identified outside HIPAA’s scope.
Essentially, HE can serve as a form of encryption-based pseudonymization under HIPAA. As long as the data remains encrypted and the key is secret, the risk of unauthorized disclosure is “very small,” potentially satisfying HIPAA’s standards. In practice, HE can help healthcare organizations comply with HIPAA by enabling the secure outsourcing of analytics on patient data without exposing raw PHI.
PCI DSS (Payment Card Industry)
PCI-DSS mandates strong encryption for cardholder data both at rest and in transit. While PCI-DSS does not explicitly discuss HE, it can, in principle, enhance the security of card data. For example, a payment processor might run fraud detection algorithms on encrypted card data without decrypting it, further reducing exposure. As regulations evolve to emphasize end-to-end data protection, HE’s ability to keep sensitive fields encrypted during processing aligns well with PCI’s goals, as well as with newer privacy laws like CCPA.
NIST and ISO/IEC Standards
On the cryptography side, standardization efforts for HE are underway. NIST’s Cryptographic Standards and Guidelines (CSRC) recognizes HE as a “special type of encryption scheme” enabling evaluations on encrypted data. NIST has been actively organizing workshops, such as WPEC 2024, on Privacy-Enhancing Cryptography, which include sessions on FHE, use cases in health and finance, and performance guidelines.
Meanwhile, ISO/IEC has already published standards covering HE. For instance, ISO/IEC 18033-6:2019 specifies mechanisms for HE (e.g., Exponential ElGamal, Paillier). Additionally, HomomorphicEncryption.org published a Homomorphic Encryption Security Standard in 2018 and continues to work on API/SDK standards. As one 2024 analysis notes, ISO is advancing FHE standardization “to support wider adoption” of these techniques.
Encryption is already a required control under GDPR, HIPAA, and PCI-DSS, and HE extends encryption into the computation phase. Regulatory and standards bodies are actively examining HE: GDPR guidelines implicitly treat encrypted data as lower-risk, HIPAA allows re-identification keys, and NIST/ISO are formalizing HE schemes. Organizations can leverage HE to strengthen “privacy by design” and demonstrate cutting-edge protection to regulators.
Industry Adoption Trends for Homomorphic Encryption and Market Growth
The adoption of HE is growing, driven by increasing demands for data privacy and the growing adoption of cloud services. While HE is still not ubiquitous in production systems, surveys and analyses indicate rising interest:
- Market Size: Recent market research reports value the global HE market at a low of hundreds of millions of USD. For example, a 2024 report estimated the market at approximately $178.4 million in 2023, with an annual growth rate of around 8% into the early 2030s. Another analysis forecasted roughly $189.5M in 2022, growing to approximately $358.9M by 2030 (CAGR of ~8.3%). These figures reflect that HE is a niche but rapidly expanding segment of the data security market.
- Sector Adoption: Certain sectors lead the way in HE exploration. Financial services, including banks and fintech, are keen on secure analytics and risk computation; CSA specifically highlights finance as a primary target for FHE adoption. Healthcare and biotech are also prominent, driven by secure genomic analysis and multi-hospital studies. Cloud service providers and tech companies are developing High-End capabilities. For example, IBM Research offers an “HE for Cloud” platform, and Microsoft’s SEAL library is widely utilized. Government and defense agencies are exploring HE for securing citizen data and intelligence analytics. In contrast, adoption in other industries, such as retail and manufacturing, is more experimental.
- Benchmarks & Tools: Multiple open-source libraries now implement HE (e.g., Microsoft SEAL, Intel PALISADE, IBM HElib, CUFHE, TFHE, OpenFHE). Benchmark studies (such as “FHEBench” in 2022) are characterizing performance across schemes. These benchmarks highlight that different schemes trade off speed versus functionality: e.g., some schemes handle integer math efficiently, while others are optimized for bit operations. Overall, however, current HE operations remain orders of magnitude slower than plain computations. Most reports note that FHE is still “inefficient in practical settings”, with very high computing and memory costs.
- Drivers and Barriers: Growth drivers include stricter privacy laws, data breach risks, and demand for cloud AI on sensitive data. For example, increasing ransomware and breaches (the FBI reported over 2,285 ransomware complaints in 2023) motivate stronger in-use protections. HE is often positioned as a key part of “data protection by design.” Barriers include computational overhead, complexity of implementation, and the need for skilled cryptographers. Many implementations still require custom engineering. Performance remains the top hurdle: as one IEEE summary puts it, HE is “one of the most powerful” but also “still in an early phase” and not yet fast enough for general business use.
Despite challenges, analysts predict healthy growth. The continual maturation of HE (through academic research and startup efforts) is expected to widen its use. Cloud vendors, security firms, and open-source communities are all investing in making HE more practical. For example, startups like Zama and Duality are developing optimized FHE compilers and ML frameworks. These efforts, along with upcoming standards and hardware accelerators, suggest that adoption will gradually expand from niche pilots to broader applications. In the next few years, adoption trends are likely to follow an S-curve, with early adoption by high-privacy sectors (such as finance, healthcare, and government) and later spillover to other industries as performance improves.
Performance Challenges and Research Directions for Data Privacy
Fully HE is a powerful but computationally intensive technique. Every homomorphic operation on ciphertexts is much slower than the same plaintext operation. Common statements from experts include: “FHE schemes… are currently still inefficient in practical settings”. Real-world benchmarks reveal that simple operations, such as adding two 32-bit numbers, can take milliseconds or more, while bootstrapping (noise refresh) can require seconds on current hardware. This large overhead, often hundreds or thousands of times slower, is the main bottleneck.
Key research directions to overcome performance limits include:
- Algorithmic Improvements: New FHE schemes and optimizations (e.g., CKKS for approximate arithmetic, TFHE for fast bootstrapping) continue to emerge. For instance, a 2024 study reports a new integer FHE construction that maintained ~98% accuracy over many operations with only modest additional cost compared to traditional methods. FHE compilers and frameworks (such as Concrete and OpenFHE) automatically optimize parameters and circuits for speed. In July 2024, Zama showed that its Concrete-ML compiler could “beat previous performance benchmarks” for encrypted neural network inference, demonstrating rapid progress in applying FHE to ML tasks.
- Hardware Acceleration: Since HE is parallelizable at the bit or word level, it can benefit from the use of GPUs, FPGAs, or specialized hardware. Researchers are exploring FPGA and ASIC designs for FHE. NIST PEC documents note talks on “FHE hardware performance” at recent workshops. For example, prototype chips implementing homomorphic operations have been reported in the literature, aiming to offload the costly computation of polynomial arithmetic. As one ENISA report notes, HE is a “balancing act,” and performance will improve as hardware and engineering catch up.
- Noise Management and Bootstrapping: Bootstrapping (refreshing ciphertext noise) was once too costly for all but simple tasks, but new techniques are making it more practical. Some modern FHE schemes delay bootstrapping or use leveled FHE to reduce the need for frequent refresh. Ongoing work focuses on “programmable bootstrapping” and other techniques to make deep circuits feasible.
- Standardization of Parameters: A unique challenge of FHE is selecting the correct security parameters (keys, moduli, noise budgets) for each application. The 2024 “Security Guidelines for Implementing FHE” paper reports that parameter selection is hard because it affects both security and allowed operations. Work like this aims to provide reference tables and toolkits that enable developers to select safe and efficient settings. HomomorphicEncryption.org and NIST are collaborating on such guidelines, which should accelerate safe adoption.
In summary, performance challenges continue to be the primary limitation of higher education today. However, active research in algorithms, hardware, and compiler tooling is closing the gap. Every year sees faster implementations: recent blog reports of practical encrypted inference show run-times improving significantly. As one expert concludes, FHE is “new and extremely powerful,” and as core technology improves, it will likely become ubiquitous.
Available Documentation and Industry Resources for Homomorphic Encryption
Several key publications and organizations provide detailed guidance on HE:
- Standards and Guidelines: NIST’s Privacy-Enhancing Cryptography (PEC) project and HomomorphicEncryption.org (an industry consortium) have produced security standards and guidelines. Notably, the Homomorphic Encryption Security Standard (2018) describes the security of schemes and parameter sets. The ISO/IEC standards (ISO/IEC 18033-6:2019 and draft ISO/IEC 18033-8) formally specify homomorphic algorithms. In academia, recent papers (e.g., “Security Guidelines for Implementing FHE”, 2024) survey FHE schemes and propose standardized parameter sets.
- Government Publications: EU and national data-protection bodies have acknowledged HE in privacy engineering reports. For example, a 2022 ENISA whitepaper on data protection engineering highlights HE as a privacy-enhancing technology and notes its trade-offs. Workshops like the EU’s Privacy-Enhancing Technologies conferences often include FHE in their agenda. In the US, NIST’s Cryptographic Technology Group is funding research, such as the PEC workshops, and may eventually include HE in future cryptographic guides.
- Industry Whitepapers: Leading cybersecurity organizations and tech companies publish analyses and tutorials on HE. For instance, IEEE’s Digital Privacy portal has articles on HE advantages and use cases. CSA provides working group materials on FHE in cloud security. Companies like IBM, Microsoft, Google, Duality, and Zama publish blog posts and whitepapers demonstrating HE techniques and benchmarks. These resources often include technical overviews and case studies.
- Academic Surveys: Numerous academic surveys and conference papers exist on higher education. (Given user instructions, we would cite some, but space is limited in a blog format.) Seminal works (such as Gentry’s 2009 construction) and subsequent improvements (e.g., Brakerski-Gentry-Vaikuntanathan schemes) are often referenced in crypto literature. IEEE and Springer journals have recent survey articles on HE in healthcare, finance, etc., which detail performance and security considerations.
These documentation sources emphasize that HE is at the cutting edge of privacy technology. As standards crystallize and more implementations emerge, these references will help organizations adopt HE correctly. Stakeholders should consult them for best practices, such as secure parameter choices and compliance guidance, when planning HE deployments.
How Can Encryption Consulting Help?
HE offers unparalleled security for data processing, but implementing it can be complex. From choosing the right scheme to optimizing performance, organizations face numerous challenges. This is where expert guidance becomes invaluable.
At Encryption Consulting, we specialize in helping organizations navigate the intricacies of advanced cryptographic techniques like HE. Our Encryption Advisory Services provide tailored solutions to enhance your data security and ensure compliance with industry standards.
Our Compliance Services offers a comprehensive assessment of your current encryption practices, identifying gaps and providing actionable recommendations. We leverage a custom encryption assessment framework that incorporates globally recognized standards such as NIST, FIPS 140-2, and ISO/IEC 18033, ensuring our solutions are both cutting-edge and compliant.
Whether you’re looking to implement HE or strengthen your existing cryptographic infrastructure, our team of experts is here to guide you. Ready to harness the power of Homomorphic Encryption for your organization? Contact Encryption Consulting today to learn how our advisory services can help you implement secure, privacy-preserving data processing solutions.
Conclusion
HE is transforming the way we think about data privacy and security. By enabling computations on encrypted data, HE can break the trade-off between utility and confidentiality. Its main types (PHE, SHE, FHE) offer a spectrum of options for different needs. While still in its early adoption phase, HE is finding real-world use cases in finance, healthcare, cloud computing, elections, and more. It directly supports regulatory compliance goals under GDPR, HIPAA, PCI-DSS, etc., by keeping data encrypted throughout its lifecycle.
The industry is bullish about HE’s prospects: markets are growing, and large tech players are investing in HE tools. Adoption is guided by emerging standards (ISO, NIST/PEC) and bolstered by academic and industry research. The chief barrier remains performance, but active research is steadily closing that gap. The rate of improvement is accelerating – new libraries and algorithms continue to make HE faster and more practical.
For organizations dealing with sensitive data, now is the time to learn about HE. Pilot projects and proof-of-concepts can help teams understand their promises and limitations. As one security group notes, FHE “offers significant improvements” for data in finance, healthcare, and government by keeping it encrypted even during processing. By following standards and leveraging the growing ecosystem of HE tools, companies can be ready to apply this “powerful computer-based security technology” as it matures.
- What are the Implementation Strategies for Homomorphic Encryption?
- How Homomorphic Encryption Works
- Emerging Footprints of Encrypted Processing in the Industry
- How Homomorphic Encryption Ensures Compliance with Regulatory Standards
- Industry Adoption Trends for Homomorphic Encryption and Market Growth
- Performance Challenges and Research Directions for Data Privacy
- Available Documentation and Industry Resources for Homomorphic Encryption
- How Can Encryption Consulting Help?
- Conclusion




