Think about the major shifts we have seen over the years. Every few decades, a new wave of technology arrives and reshapes everything around us. The internet connected people in ways never imagined, smartphones put the world in our pockets, and cloud computing changed how businesses operate. And now, it is quantum computing’s turn. However, unlike those past revolutions, this one will not start with a flashy product launch or a viral app. Instead, it will arrive quietly, the moment quantum computers become powerful enough to break the cryptographic systems that secure our digital world.
Today, encryption protects everything from financial transactions and corporate secrets to personal messages and software updates by relying on mathematical problems that are very difficult for classical computers to solve, like factoring large prime numbers (RSA) or solving elliptic curve equations (ECC).
But quantum computers operate on entirely different principles. Once they reach a certain threshold, they will be able to solve these complex problems exponentially faster using algorithms like Shor’s. Tasks that would take classical machines thousands of years could be done in minutes or less. In fact, in December 2024, Google announced its 105-qubit Willow quantum processor, which performed a computation in under five minutes that would have taken the world’s fastest supercomputer an estimated 10 septillion years to solve. That is nearly a quadrillion times longer than the age of the universe.
This kind of advancement has caught the attention of researchers, governments, technology leaders, and cybersecurity experts. The systems we rely on today were never designed to withstand quantum threats, and patching them is not enough. We need a new foundation for digital security, one that can endure the power of quantum computation. This is where Post-Quantum Cryptography (PQC) comes in.
What is PQC?
Post-Quantum Cryptography refers to a new generation of cryptographic algorithms that are designed to resist quantum attacks. These algorithms rely on mathematical problems like structured lattices, hash-based constructions, and multivariate equations that remain difficult for both classical and quantum computers. One of the growing concerns driving the adoption of PQC is the risk of “harvest now, decrypt later” attack, where adversaries collect encrypted data today with the expectation that they will be able to decrypt it in the future once quantum computing capabilities become available. In fact, around 65 percent of organizations are already concerned about this threat, making it a critical motivation for beginning the transition to quantum-resistant solutions as early as possible.
To help everyone prepare, the U.S. National Institute of Standards and Technology (NIST) has been leading a global initiative to standardize post-quantum algorithms. After years of analysis, testing, and public review, these are the main algorithms that have been selected:
| Current Specification Name | Initial Specification Name | FIPS Name | Parameter Sets | Type |
|---|---|---|---|---|
| ML-KEM-1024 | CRYSTALS – Kyber | FIPS 203 | Kyber512 Kyber768 Kyber1024 |
Lattice-Based Cryptography |
| ML-DSA-87 | CRYSTALS – Dilithium | FIPS 204 | Dilithium2 Dilithium3 Dilithium5 |
Lattice-Based Cryptography |
| SLH-DSA | SPHINCS+ | FIPS 205 | SPHINCS+ – 128s SPHINCS+ – 192s SPHINCS+ – 256s |
Hash-Based Cryptography |
| FN-DSA | FALCON | FIPS 206 | Falcon – 512 Falcon – 1024 |
Lattice-Based Cryptography |
| HQC | HQC (Hamming Quasi–Cyclic) | Pending Standardization | HQC – 128 HQC – 192 HQC – 256 |
Code-Based Cryptography |
These standardized algorithms serve as the foundation for future-proof encryption and are now ready to be integrated into real-world systems.
Roadmap to PQC migration
Adopting post-quantum cryptography is not a one-time fix. It is a step-by-step process that touches every layer of an organization’s digital infrastructure. To make this transition easier, organizations can follow a well-defined PQC migration roadmap divided into four coordinated phases. While the exact sequence and timing may differ based on organizational needs, the phases are often closely connected and build on each other to ensure a smooth and effective transition. These four phases are:
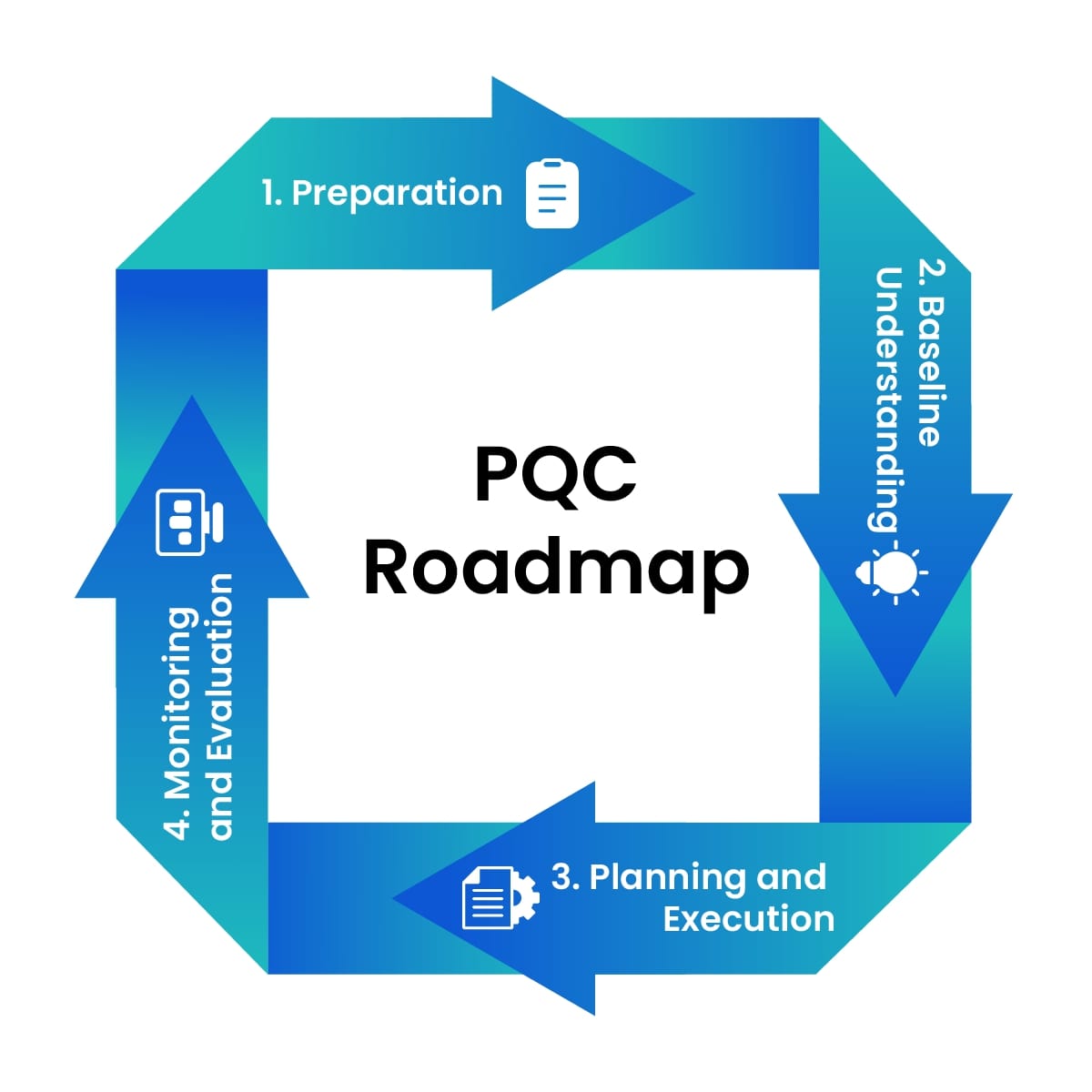
Phase 1: Preparation
This first step lays the groundwork. It involves setting clear migration goals, appointing a responsible lead, identifying key stakeholders, and aligning teams around a shared strategy. A solid foundation at this stage ensures smoother progress ahead.
Phase 2: Baseline Assessment
With leadership in place, the focus shifts to understanding the cryptographic environment of the organization. This includes creating a detailed inventory of cryptographic assets, such as digital certificates, algorithms, protocols, and keys, across your organization and prioritizing them based on sensitivity, expected lifespan, business needs, and exposure to quantum threats.
Phase 3: Planning and Implementation
This is where strategy meets execution. Organizations begin designing, acquiring, and deploying PQC solutions. Whether these solutions are developed in-house or procured from partners, this phase focuses on integration, testing, and secure rollout across systems.
Phase 4: Monitoring and Evaluation
The final phase ensures that the cryptographic posture stays strong over time. It includes tracking progress, validating the effectiveness of implementations, aligning with compliance standards, and continuously adapting as quantum technology evolves.
With the full PQC migration roadmap now outlined, let us take a closer look at each phase and explore the key activities involved in building a secure and future-ready migration path.
Preparation
The first phase focuses on establishing a strong foundation for PQC migration. This involves clarifying objectives, setting clear goals, assigning leadership, understanding the current cryptographic environment, and aligning all stakeholders around the migration effort.
To build this foundation, the following key steps should be taken:
Understand Why PQC Matters and Define Your Goals
Start by determining whether your organization should begin migrating now or later. This depends on how long your data needs to remain secure, how complex your systems are, and how long the PQC migration process might take. While there is no exact timeline for when quantum computers will become a real threat, it is likely to happen sooner than many expect.
Even if your data is not at risk today, it may still be stored by attackers and decrypted in the future once quantum computers mature. Therefore, while defining the migration goals, one must consider factors like the organization’s attack surface, interdependence, sensitivity of the data, and the urgency of action.
Assign a PQC Migration Lead
Choose someone to lead the PQC migration process. This individual or team will be responsible for setting clear timelines, coordinating with vendors, managing internal communication, and pushing the effort forward. Since PQC impacts many parts of the organization, the lead must be capable of working across departments and communicating with both technical and business teams.
Alongside appointing a lead, it is also recommended to establish a dedicated PQC team. This team should assign clear responsibilities, oversee risk mapping, align efforts with the overall business strategy, and act as the nerve center for the PQC migration project. Together, the lead and the team play an active role in embedding PQC goals into all enterprise initiatives, ensuring that quantum readiness becomes a core part of the organization’s long-term security and technology planning while enabling a coordinated and future-ready approach.
Review Existing Cryptographic Assets and Dependencies
The next step is to understand your organization’s current cryptographic setup. Start by reviewing any existing inventories, risk assessments, and cryptographic bills of materials. These may have been created at different times for various purposes. While reviewing them, document where your data and assets are located, who is responsible for them, who has access, why they were created, and how they are used.
This thorough review provides a complete picture of your cryptographic environment and helps to identify any gaps. It also helps prevent duplication of effort during migration and can reveal if there are any existing infrastructures, platforms, or libraries that already support post-quantum cryptography.
Identify Key Stakeholders and Begin Engagement
Identifying and involving relevant stakeholders early in the process is essential. These may include system owners, application teams, infrastructure managers, compliance leaders, and third-party vendors. Engaging these groups early helps to assess solution readiness, understand potential integration challenges, and uncover practical considerations such as hardware limitations, cost implications, or software constraints.
Document the goals and scope of the migration effort, share clear summaries of planned changes, and monitor how well teams are aligned and responding. This communication builds internal support and reduces friction during implementation.
Outcomes
By the end of this phase, the organization will have established a strong foundation for PQC migration by clearly defining its rationale for transitioning to post-quantum cryptography and setting a realistic timeline based on its unique risk profile and data sensitivity. A qualified migration lead and team are appointed to coordinate the effort, ensuring alignment across departments and with external partners.
Existing cryptographic inventories are thoroughly reviewed and documented, providing a clear view of the organization’s current cryptographic posture and readiness. Key stakeholders, including internal teams and external vendors, are identified and actively engaged through consistent communication, helping to align priorities, gather essential insights, and build broad-based support. As a result, the organization is equipped with the clarity, leadership, and stakeholder alignment necessary to confidently advance to the next phase of PQC migration.
Baseline Assessment
Building on the foundation established in Phase 1, the next phase focuses on developing a comprehensive understanding of the organization’s cryptographic environment. This includes identifying what cryptographic assets are in place, how critical they are, and what resources are needed to support further discovery and prioritization. The insights gained during this phase empower the migration lead and supporting teams to make informed decisions about where to begin implementation and how to allocate effort based on risk, data sensitivity, system dependencies, and urgency.
To support this phase, the following activities are critical for understanding the organization’s current cryptographic landscape and potential risks:
Define a Discovery Strategy and Allocate Resources
In this step, the PQC migration lead checks if the existing inventory from Phase 1 is detailed enough or if further discovery of cryptographic assets and their usage is needed. Based on this assessment, a discovery plan is established, outlining whether to continue exploring cryptographic assets or to move forward with prioritization. As part of this process, it is important to map cryptographic assets to business risk in order to understand which systems or data are most critical and require immediate attention. The lead also figures out the budget and resources needed to support the next steps.
At this stage, engaging with external partners or vendors who specialize in PQC readiness assessments, such as Encryption Consulting, can provide valuable guidance and significantly accelerate discovery efforts. These collaborations offer deeper visibility into cryptographic usage, help uncover hidden vulnerabilities, and validate internal assessments. A clear and realistic discovery plan, shaped by available resources, helps keep the process focused, avoids unnecessary effort, and sets the stage for smooth progress in later phases.
Develop a Centralized Cryptographic Inventory
With the discovery plan in place, the focus shifts to creating or refining a centralized inventory of cryptographic assets. This inventory is crucial for managing PQC migration at scale, identifying where legacy cryptography is used, and ensuring no critical systems are overlooked. The migration lead and his team work closely with system operators to document key technical details such as what algorithms are in use, which assets they protect, and how systems are architected.
To support this effort, organizations may use automated tools that scan hardware, software, and embedded components to detect cryptographic algorithms and key usage. The choice of tools depends on the organization’s risk tolerance and the level of visibility needed. Additionally, teams also collect detailed information about each asset, including who manages it, the data it protects, and any protocols or interfaces it relies on. It is also important to flag unknowns, like offline or undocumented keys, to highlight blind spots that could impact PQC migration. Grouping assets by supplier helps prepare the organization for vendor coordination in the upcoming phases.
Identify and Prioritize Critical Cryptographic Assets
With a clear inventory in place, the next step is to determine which assets are most critical and should be prioritized for PQC migration. The migration lead evaluates assets based on data sensitivity, expected lifespan, exposure to threats, complexity of dependencies, and the asset’s role in key business initiatives. Prioritizing assets by their impact on business operations ensures that migration efforts align with enterprise goals and risk tolerance. This evaluation helps to identify systems that need immediate PQC updates and those that can follow in later stages. The lead works with vendors and system operators to finalize these priorities.
A detailed risk assessment may also be conducted to uncover security, operational, and compliance risks, especially considering threats from future quantum computers. Whether or not a formal risk assessment is done, the team should use timelines for migration urgency and asset lifespan to create a practical, prioritized migration plan that balances risk and resources. In cases where high-risk systems are clearly identified during discovery, early migration efforts may begin in this phase, especially when supported by vendor-ready solutions. This proactive approach helps reduce exposure while the broader planning continues.
Outcomes
By the end of Phase 2, the organization has gained a structured and actionable understanding of its cryptographic landscape. The migration lead has developed a discovery plan, evaluated whether further inventorying is needed, and identified an appropriate budget to support it. A centralized and categorized inventory has been created, capturing essential technical details and exposing gaps in visibility.
The organization has also identified which cryptographic assets are more critical and established migration priorities based on data sensitivity, system lifespan, and quantum risk exposure. In cases where high-risk systems have been clearly identified, early migration efforts may also be initiated at this stage. Equipped with this clarity, the organization is ready to move into the planning and implementation phase with precision and purpose.
Planning and Implementation
This phase is where planning meets action. With a prioritized asset list in hand, your organization begins defining how to migrate each asset to post-quantum cryptography (PQC). This stage marks the full-scale enterprise rollout of PQC, including the start of decommissioning legacy cryptographic systems. Alongside these long-term PQC migration strategies, immediate security measures are put in place to reduce risk during the transition period. Budgeting, technical evaluations, vendor coordination, and solution deployment all come together in this phase to ensure the transition to PQC is both practical and aligned with the organization’s needs.
To prepare for implementation, organizations should focus on the following coordinated planning and implementation efforts:
Set a Migration Plan and Budget
Using the prioritized list from Phase 2, the migration lead decides the next steps for each asset, whether to mitigate risk, start migration to PQC, or accept quantum risk for now. This includes coordinating with vendors to better understand each asset’s risk and requirements, especially if solutions will come from external providers.
The team estimates migration costs, identifies necessary resources, and sets a realistic budget. To plan effectively, it is important to outline what work needs to be done, when it will happen, and what each task might cost.
Identify Suitable Solutions and Strengthen Short-Term Defenses
Next, the focus shifts to finding the right technical solutions. The migration lead works with system operators to figure out what can be done in-house and what must be acquired from vendors. For each system, it is important to identify whether the migration can happen through software updates or if hardware upgrades will be required. The team should also verify whether available solutions comply with recognized PQC standards like those from NIST. Exploring agile cryptography options is encouraged to enable easier future updates and avoid vendor lock-in.
Throughout this process, engagement with vendors remains critical. Key questions to address include: When will PQC-ready products be available? Will updates require hardware changes? What will they cost? How disruptive will implementation be? And will vendors provide a cryptographic bill of materials (CBOM) for visibility?
While waiting for full PQC migration, implement short-term steps to reduce risk. This can include shortening certificate lifespans, increasing key sizes, modernizing protocols like TLS 1.3, tightening physical security, and adding extra data protection layers. Where commercial solutions are not yet available, internal development is initiated in parallel, supported by detailed planning, realistic timelines, and continuous market monitoring.
Implement PQC Solutions
With planning, budgeting, and technical evaluations in place, the organization moves to execution. The migration lead begins acquiring commercial PQC solutions or allocating resources for internal development based on the asset priorities established earlier.
Finally, implementation begins. This includes installing PQC updates, deploying internal solutions, and applying both short-term and long-term mitigations. The migration lead manages timelines, tracks progress, and prepares for any disruptions that migration efforts might cause. If systems are deployed in phases, it is important to ensure forward and backward compatibility between legacy and updated components. As updates are rolled out, the organization updates its inventory to reflect the new cryptographic status of each system. Where applicable, this is also the time to begin decommissioning legacy cryptographic systems that are no longer needed, reducing long-term risk exposure.
Outcomes
By the end of this phase, the organization transitions from planning to hands-on execution. A clear PQC migration plan and budget drive the process forward. The organization identifies the right solutions, determines how they will be implemented, and puts short-term protections in place for sensitive systems. This stage also marks the beginning of decommissioning legacy cryptographic systems, reducing long-term exposure to known vulnerabilities.
Vendors are engaged, compliance is documented, and agile cryptographic strategies are considered for long-term flexibility. PQC solutions are either acquired or developed and rolled out across systems. The organization’s inventory is updated throughout, offering a current and accurate view of progress and preparedness for the next phase.
Monitoring and Evaluation
The final phase focuses on sustaining momentum and ensuring long-term effectiveness. As PQC solutions are deployed, the organization shifts focus to tracking, validating, and maintaining the progress of its PQC migration. This includes ensuring cryptographic upgrades are effective, documenting compliance, measuring the success of migration efforts, and staying aligned with evolving industry standards. The migration lead also reassesses workforce readiness and creates ongoing processes to adopt crypto agility, which means the ability to quickly adapt cryptographic systems as new threats and technologies emerge. This approach ensures the organization remains resilient against future challenges.
For this phase, the following operational steps are essential:
Validate Implementation and Ensure Standards Alignment
The first step in this phase is verifying that deployed PQC solutions are operating as intended. The migration lead works with system operators to validate that systems meet their cryptographic and operational requirements, such as forward and backward compatibility, and that any identified issues have been resolved. Once verified, the inventory should be updated to reflect the current status.
Alongside technical validation, the organization must make sure its migration efforts align with relevant industry regulations. For example, healthcare providers may need to align with HIPAA, while organizations operating in the EU should reference NIS2. These standards encourage activities like regular risk assessments, system resilience, and future-proofing, and aligning with them strengthens both security posture and audit readiness.
Track Progress and Support the Workforce
The migration lead defines performance indicators that track how well PQC is being implemented. This might include metrics on how much sensitive data is now protected with post-quantum cryptography or how many systems have migrated. These indicators are tied to the migration strategy established earlier and may be benchmarked against NIST or NSA guidance to ensure relevance and consistency.
At the same time, it is important to assess whether internal teams are ready to support and maintain PQC systems. If gaps are identified, targeted training should be provided to ensure teams have the necessary knowledge and skills to manage, operate, and troubleshoot post-quantum cryptographic solutions effectively. The migration lead works with system owners and operators to identify any skills gaps or workflow challenges, and helps develop targeted training, adjusting responsibilities, or bringing in new talent. This ensures that post-migration support is not only technically sound but also sustainable over time.
Establish Continuous Monitoring and Future Preparedness
PQC migration is not a one-time effort. The organization must stay agile by regularly monitoring the cryptographic landscape, updating its inventory, tracking compliance with new standards, and re-evaluating risk. The migration lead should establish a routine process for documenting changes, retiring obsolete systems, staying ahead of quantum developments, and maintaining long-term cryptographic resilience by adapting crypto-agility.
Outcomes
By the end of this phase, the organization has validated the success of its PQC migration and ensured alignment with applicable regulatory requirements. Progress is tracked through clear, measurable indicators, and the workforce is equipped to manage post-quantum systems effectively. Continuous monitoring processes are established to update inventories, adjust to new risks, and stay aligned with evolving standards.
With crypto agility embedded into its strategy, the organization is positioned to swiftly adapt to future cryptographic challenges and remain secure and adaptable in a rapidly changing threat landscape.
How can Encryption Consulting help?
If you are still wondering where and how to begin your post-quantum journey, Encryption Consulting is here to support you. You can count on us as your trusted partner, and we will guide you through every step with clarity, confidence, and real-world expertise.
-
PQC Assessment
We begin by helping you get a clear picture of your current cryptographic setup. This includes discovering and mapping out all your cryptographic assets, such as certificates, keys, and other cryptographic dependencies. We identify which systems are at risk from quantum threats and assess how ready your current setup is, including your PKI, HSMs, and applications. The result? A clear, prioritized action plan backed by a detailed cryptographic inventory report and a quantum risk impact analysis.
-
PQC Strategy & Roadmap
We develop a step-by-step migration strategy that fits your business operations. This includes aligning your cryptographic policies with NIST and NSA guidelines, defining governance frameworks, and establishing crypto agility principles to ensure your systems can adapt over time. The outcome is a comprehensive PQC strategy, a crypto agility framework, and a phased migration roadmap designed around your specific priorities and timelines.
-
Vendor Evaluation & Proof of Concept
Choosing the right tools and partners matters. We help you define requirements for RFPs or RFIs, shortlist the best-fit vendors for quantum-safe PQC algorithms, key management, and PKI solutions, and run proof-of-concept testing across your critical systems. You get a detailed vendor comparison report and recommendations to help you choose the best.
-
PQC Implementation
Once the plan is in place, it is time to put it into action. Our team helps you seamlessly integrate post-quantum algorithms into your existing infrastructure, whether it is your PKI, enterprise applications, or broader security ecosystem. We also support hybrid cryptographic models combining classical and quantum-safe algorithms, ensuring everything runs smoothly across cloud, on-premises, and hybrid environments. Along the way, we validate interoperability, provide detailed documentation, and deliver hands-on training to make sure your team is fully equipped to manage and maintain the new system.
-
Pilot Testing & Scaling
Before rolling out PQC enterprise-wide, we test everything in a safe, low-risk environment. This helps validate performance, uncover integration issues early, and fine-tune the approach before full deployment. Once everything is tested successfully, we support a smooth, scalable rollout, replacing legacy cryptographic algorithms step by step, minimizing disruption, and ensuring systems remain secure and compliant. We continue to monitor performance and provide ongoing optimization to keep your quantum defense strong, efficient, and future-ready.
Reach out to us at info@encryptionconsulting.com and let us build a customized roadmap that aligns with your organization’s specific needs.
Conclusion
The quantum era is not coming; it is already on the horizon. While we may not know exactly when large-scale quantum computers will arrive, we do know that the time to prepare is now. Waiting until the last minute simply is not an option when your data and systems could be vulnerable for years.
Transitioning to post-quantum cryptography may feel complex, but with the right plan and the right partners, it becomes manageable and even empowering. By following a phased approach, your organization can take control of the journey and build a future-ready security posture that keeps your most valuable assets protected.
Whether you’re still figuring out where to start or you’re ready to dive into implementation, the most important thing is to take that first step and keep the momentum going. And if you are looking for a partner to walk that path with you, we are here.
At Encryption Consulting, we are ready to help you move forward with clarity, confidence, and a plan that fits your goals. Let us get started and make sure your organization is secure, not just for today, but for what is next.