Encryption ensures the security of everything we do online. Whether logging into your bank, sending messages, or connecting to corporate networks, cryptographic protocols work silently to protect those interactions. However, the problem is that much of today’s protection, mainly RSA and ECC, was designed for classical computers. As quantum computing rises, these algorithms can eventually be broken. The threat becomes more serious with each passing day. The potential for “harvest now, decrypt later” assaults is already being anticipated by governments, businesses, and security professionals.
Classical algorithms, once the foundation of digital security, are becoming increasingly less relevant. Quantum computers, once purely theoretical, are now a hardware reality. Capable of solving certain mathematical problems exponentially faster than classical computers, they pose a threat to widely used cryptographic algorithms, such as RSA and ECC. For every organization that relies on cryptography to protect communications, transactions, and identities, the journey to post-quantum safety comes with promise, urgency, and an overwhelming number of challenges.
But where do things actually stand today? How far have we come in making the internet, VPNs, email, and certificates quantum-safe? The Post-Quantum Cryptography Coalition (PQCC) provides a clear answer by publishing monthly “State of the Migration” heatmaps that track the ongoing progress across these critical areas. These heatmaps serve as snapshots, illustrating how various security standards are evolving toward quantum safety. Let’s take a closer look at what they tell us.
Understanding the Heatmaps
Each PQCC heatmap is a visual representation that maps the progress of leading cryptographic protocols and standards as they transition to quantum-resistant methods. At first glance, the heatmap’s numeric codes can seem abstract, but each number tells a story about the status of post-quantum migration for a specific protocol and use case. A quick glance at any heatmap displays not only the current condition of each procedure, but also the subtle changes that occur month after month. These changes are more than just statistics; they represent indicators of industry momentum, goals, and obstacles that still need to be addressed.
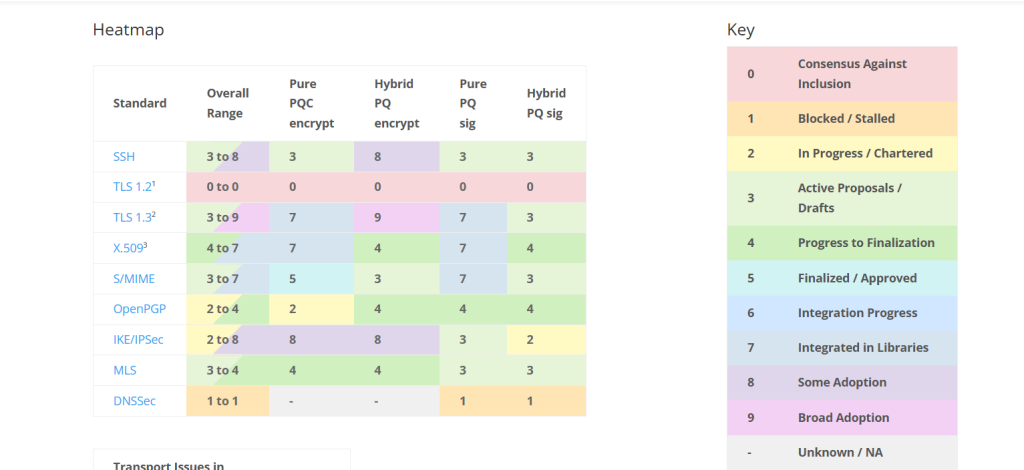
Each heatmap employs a numerical scale from 0 to 9, where zero represents either no progress or a consensus not to include PQC in a standard, and nine signifies broad adoption of post-quantum techniques in real-world deployments. The color spectrum, ranging from red tones for low scores to lush greens and purples for higher scores, enables viewers to interpret the maturity of each protocol’s PQC readiness instantly. This visual language is an effective way to track standards like TLS, SSH, and DNSSEC as they either advance or lag on the quantum safety path.
How the Heatmap Works
The heatmap is organized as a grid.
Rows
- Major security standards and protocols (e.g., SSH, TLS 1.3, X.509, S/MIME, OpenPGP, IKE/IPSec, MLS, DNSSec).
- SSH serves as the foundation for remote administration and secure server access, enabling encrypted file transfers and command-line interfaces that are essential to managing IT infrastructure. TLS 1.3 protects most internet traffic, ensuring safe communications for web browsing, banking, and online data transfers. X.509 digital certificates form the foundation of Public Key Infrastructure, authenticating users and devices for secure connections to websites and VPNs.
- Standards like S/MIME and OpenPGP maintain email security. S/MIME provides end-to-end email encryption and digital signatures, which are essential for safeguarding business correspondence. OpenPGP, popular among privacy-conscious users, secures emails, files, and software with robust encryption and signing features.
- On the network level, IKE/IPSec enables VPNs that guard data in transit between remote locations, mobile users, and cloud resources. Messaging Layer Security (MLS) is emerging to secure group messaging and collaboration platforms, while DNSSec adds integrity checks to domain name lookups, protecting the internet’s “address book” from tampering.
Columns
The columns in the heatmap are designed to indicate the status and maturity of each protocol’s migration toward post-quantum cryptography, allowing for a clear comparison of progress across different protection mechanisms.
- Overall Range: Indicates the general maturity of migration for the standard.
- Pure PQC Encrypt: Status of post-quantum encryption.
- Hybrid PQC Encrypt: Status of hybrid approaches (combining classical and post-quantum methods).
- Pure PQC Sig: Status of post-quantum digital signatures.
- Hybrid PQC Sig: Status of hybrid digital signatures.
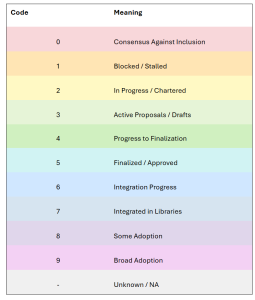
Each cell is filled with a numeric code, where higher numbers represent greater progress or adoption:
Monthly Heatmaps
The sections that follow provide a detailed breakdown of the monthly Heatmaps, beginning with March 2025, to illustrate the evolution of the migration to post-quantum cryptography.
March Heatmap
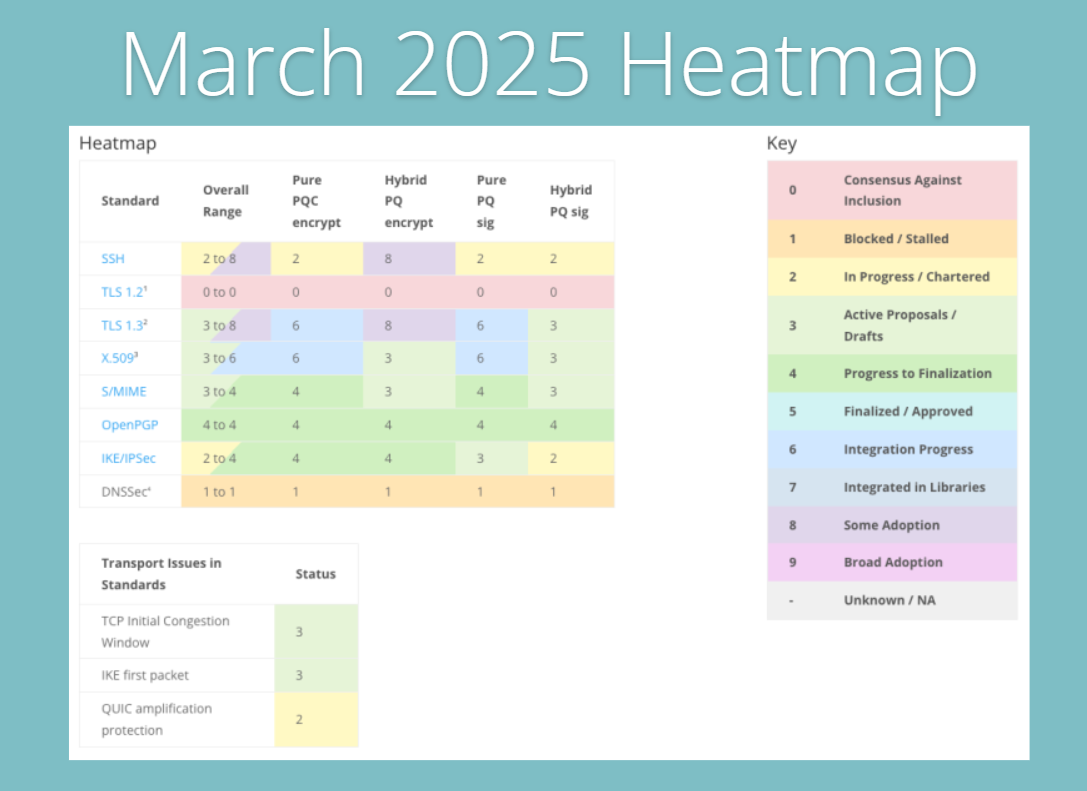
The March 2025 heatmap provides a snapshot of when major cryptographic standards began to take shape as the migration to PQC started to emerge. Most protocols are still in the early stages, with proposals being drafted, prototypes being run, and testing underway to determine how quantum-safe methods can be integrated into existing systems.
Some protocols stand out more than others. SSH, TLS 1.3, X.509, and S/MIME dominate the map, with scores ranging from 2 to 8. This illustrates a combination of early integration work and active development efforts. For example, during the PQC Standardization breakout session at IETF (Mike Ounsworth’s presentation, Austin 2025), researchers discussed real-world tests and integrations for these protocols, moving them beyond theory.
In contrast, TLS 1.2 remains stuck at zero. There’s a clear industry consensus that PQC won’t be added to this older standard. That means organizations still relying on TLS 1.2 should view this as a wake-up call; it’s time to redirect energy and investment toward TLS 1.3 or newer protocols that can support hybrid and quantum-safe encryption.
TLS 1.3, in particular, shows strong momentum. Pure PQ encryption already scores a 6, while hybrid PQ encryption hits 8, signaling that pilot deployments are underway. The IETF TLS Working Group’s draft on hybrid key exchange, which combines classical ECDHE with post-quantum KEMs like ML-KEM, is a significant step forward. This hybrid approach delivers the best of both worlds: the reliability of established classical methods with the resilience of quantum-safe algorithms. As a result, TLS 1.3 is quickly becoming the frontrunner for organizations preparing their infrastructures for the quantum era.
Meanwhile, OpenPGP and IKE/IPSec are making slower progress. They’re still in transition phases, with work focused on proposals and drafts rather than large-scale adoption. DNSSEC comes in lowest on the map, underscoring the challenges of adapting core internet infrastructure to post-quantum methods.
Transport issues add another layer of complexity. The TCP Initial Congestion Window continues to struggle with latency and efficiency. The IKE first packet, crucial for starting VPN sessions, hasn’t seen much improvement in reliability or security. And QUIC amplification protection, designed to block DDoS-style reflection attacks, continues to lag. Taken together, these underscore the fact that PQC migration isn’t just about new cryptographic algorithms; it also requires technical work at the network layer to ensure performance and security remain intact.
April Heatmap
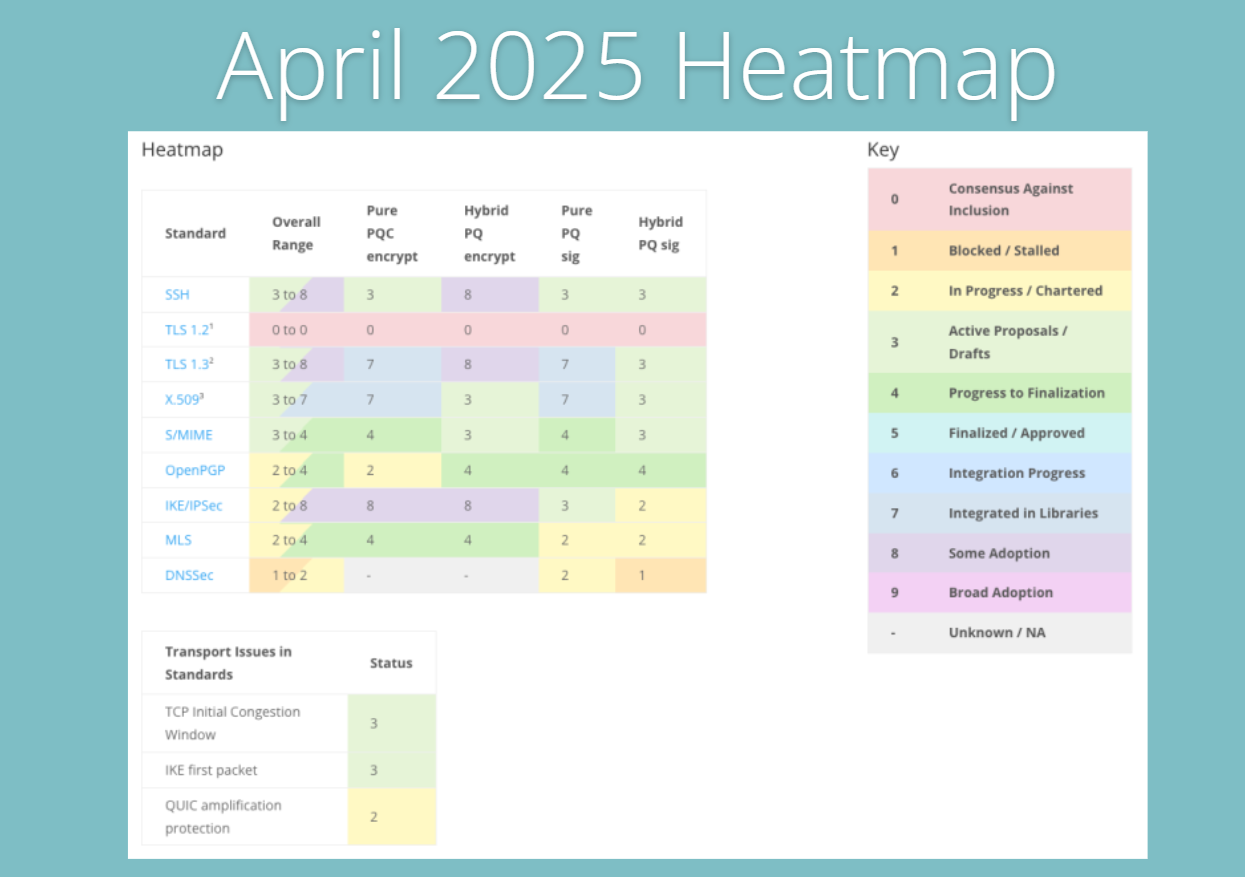
By April, the heatmap begins to show visible momentum. Some protocols that were only in the planning phase a month earlier are now starting to move toward real adoption. SSH and IKE/IPSec take notable steps forward, especially with hybrid PQ encryption reaching a score of 8, indicating that testing and broader implementation are now underway.
TLS 1.3 continues to build on its strong position, maintaining high scores in both pure and hybrid PQ encryption, as well as in digital signatures. This steady progress reflects its role as the backbone of secure internet communication and its readiness to carry quantum-safe methods into production environments.
Other key building blocks, such as X.509 certificates and S/MIME, are also making progress. In fact, some parts are now marked as “integrated in libraries”, a clear sign that post-quantum methods are starting to move from academic drafts into the software tools developers actually use.
On the other hand, OpenPGP and Messaging Layer Security (MLS) continue to advance slowly. They’re not stalled, but their adoption pace is much more gradual compared to TLS or SSH. This highlights the uneven speed of progress across the ecosystem.
DNSSEC exhibits only slight movement, particularly in terms of signature readiness, but still remains near the bottom of the scale. This lag reinforces concerns about the fragility of domain name security in a post-quantum world. Without significant attention, DNSSEC risks becoming the weak link in an otherwise advancing security chain.
Transport layer issues remain relatively unchanged compared to March. Challenges surrounding TCP congestion control, IKE packet handling, and QUIC protections persist, underscoring that upgrading cryptography is only half the battle; network fundamentals also need to evolve in parallel.
Taken together, the April heatmap reflects a turning point: the community is no longer just drawing up plans but starting to execute them. Developers, implementers, and vendors are engaging more directly, signaling the start of broader PQC adoption across real-world systems.
May Heatmap
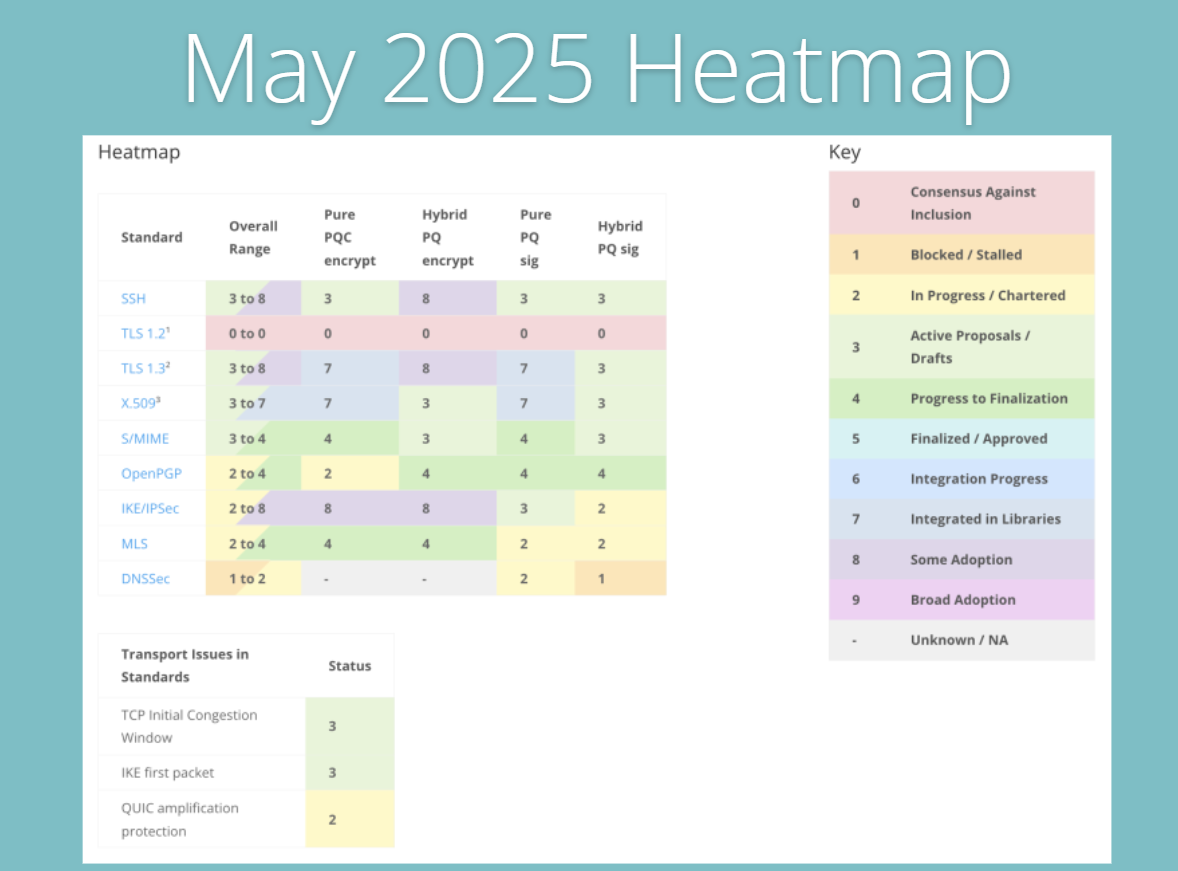
May’s heatmap reveals deeper integration progress and some adoption in key protocols. TLS 1.3 hybrid PQ encryption sees an increase, approaching full adoption, a signal that influential software libraries and major cloud providers are gearing up or already deploying quantum-safe cryptographic options.
SSH and IKE/IPSec maintain their strong hybrid PQ encryption scores, reinforcing their importance in securing infrastructure and communication. X.509 and S/MIME steadily advance with mixed progress in signature adoption and encryption capabilities. OpenPGP and MLS, although still slow, continue to advance in integration progress and experimental deployments.
DNSSEC remains one of the most lagging protocols, with low scores persisting. This highlights a systemic concern about quantum resistance in foundational internet infrastructure components.
Transport issues show incremental improvement, particularly in IKE packet handling, suggesting enhanced readiness in the secure network transport segment. May’s heatmap shows a surge in practical implementation efforts, backed by pilot deployments and an increase in positive feedback from real-world testing.
June Heatmap
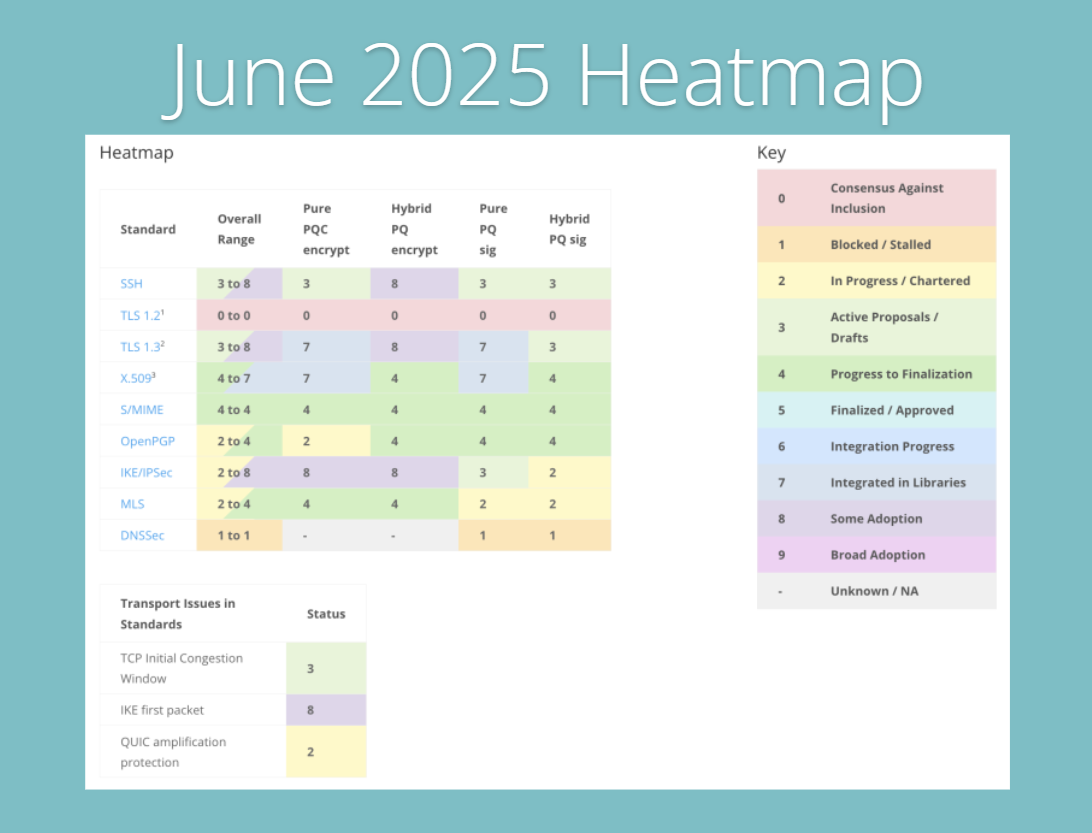
June’s chart continues the positive trend, with most protocols maintaining or improving their standing. TLS 1.3 edges closer to broad adoption, especially for hybrid PQ encryption, with pure PQ encryption also showing strong traction.
SSH and IKE/IPSec remain leaders in PQC adoption among infrastructure protocols, further cementing their role in the migration roadmap. X.509 and S/MIME reach new milestones in signature and encryption integration, pointing to gradually expanding trust and usability in enterprise environments.
OpenPGP and MLS, despite slower progress, sustain steady improvements, reflecting ongoing experimental adoption in specialized or privacy-minded sectors.
DNSSEC’s persistent struggle to move beyond low scores remains a concern, highlighting the need for a focused and coordinated effort.
Transport-layer refinements, such as those in TCP congestion window and IKE first packet strategies, make slow but steady headway, which is critical for ensuring that PQC doesn’t introduce latency or reliability trade-offs. June’s heatmap reveals an industry that is increasingly confident in deploying PQC capabilities, driven by stronger software and interoperability support.
July Heatmap
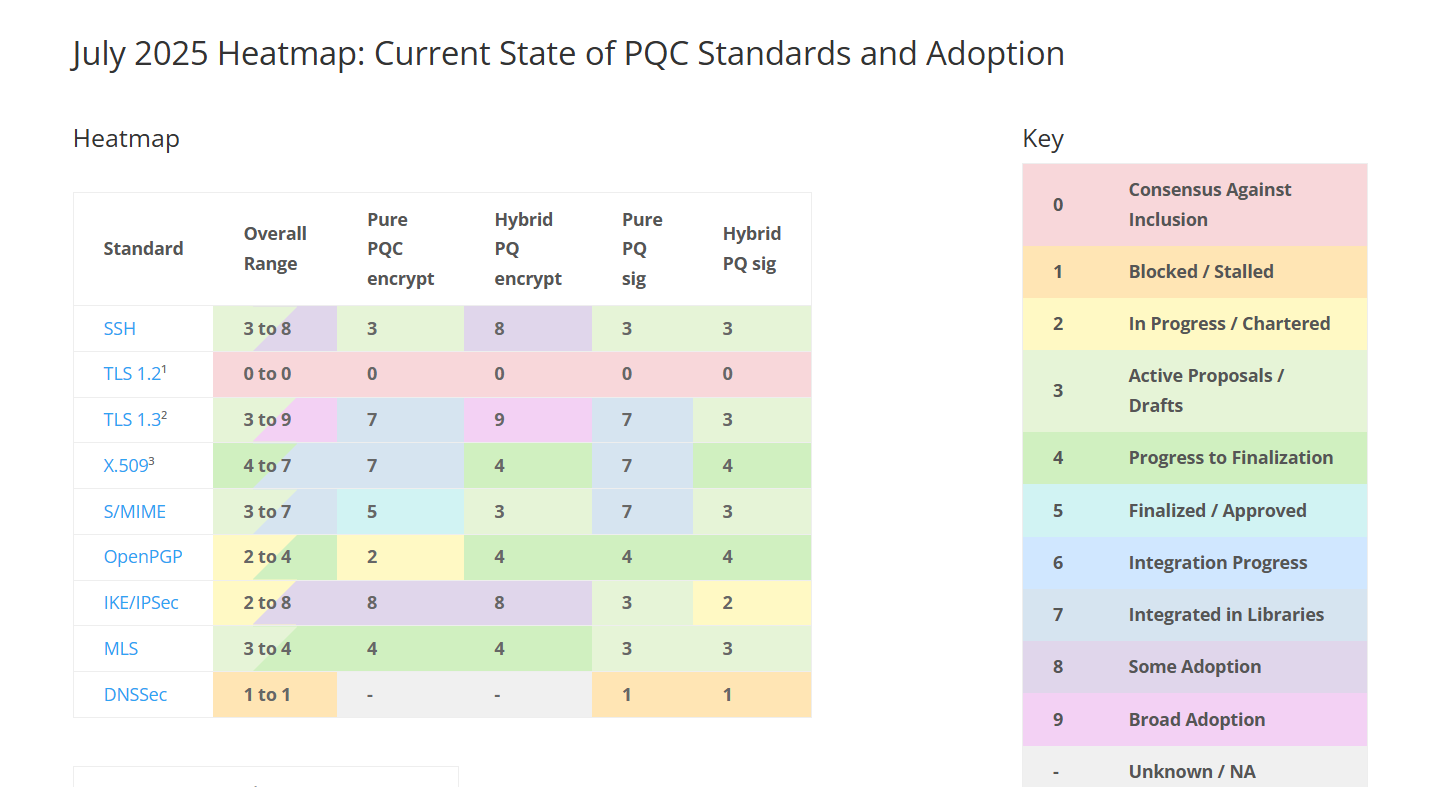
The July heatmap represents the most recent and encouraging snapshot of the post-quantum cryptography (PQC) migration effort. It captures a pivotal moment where progress has shifted from cautious experimentation to confident and practical deployment.
At the forefront, TLS 1.3 stands as a clear leader. Its hybrid post-quantum encryption achieves a peak score of “9,” signaling broad industry deployment and a maturity that extends beyond theoretical validation. This indicates that quantum-safe configurations within TLS 1.3 are no longer confined to labs; they are actively protecting real web traffic, supported by major cloud providers, browser vendors, and critical internet infrastructure. Alongside this, the presence of pure PQ encryption and signatures has likewise solidified in key cryptographic libraries, providing developers with the tools needed to implement fully quantum-resistant communication channels.
SSH and IKE/IPSec, two protocols fundamental to infrastructure security and VPN connectivity, continue to gain steady adoption. Their hybrid PQ integrations have become more extensive and operational, reflecting a growing ecosystem readiness to embrace quantum-safe mechanisms in server authentication and secure remote access. This maturation ensures that critical internal networks and administrative functions receive early protection against the emerging quantum threat.
Meanwhile, standards such as X.509 and S/MIME are showing promising growth in library integration and real-world testing environments. These advancements mark a significant milestone, bridging the gap between foundational cryptographic frameworks and large-scale deployment. Although widespread adoption is still gathering momentum, the progress points towards a future where quantum-safe certificates and secure email communications will be routine components of enterprise cybersecurity.
On the other hand, OpenPGP and Messaging Layer Security (MLS) are still navigating the earlier phases of this journey. Their incremental advances underscore the varied pace within the PQC ecosystem, likely influenced by the diversity of their user bases and technical complexity. These protocols represent specialized yet vital sectors that will require continued focus and innovation to achieve full quantum readiness.
Among these developments, DNSSEC stands out as the consistent outlier. Its progress is negligible, reinforcing concerns about this critical element of internet infrastructure lagging significantly behind. Without urgent attention to quantum-safe DNS authentication, the broader cryptographic gains risk being undermined by vulnerabilities at the domain resolution level, creating a fundamental security bottleneck that the industry must address.
Transport-layer issues have also seen meaningful improvements, notably in IKE’s first packet handling. This signals that lower-level networking protocols are evolving to support the demands of PQC, ensuring that higher-layer protocols, such as TLS and VPN tunnels, can operate efficiently without introducing latency or instability. Addressing these transportation challenges is crucial to a seamless migration that maintains performance while enhancing security.
What do the Heatmaps teach us?
The heatmaps collectively offer valuable insights into the current landscape of post-quantum cryptography migration. TLS 1.3 is leading the way with rapid adoption, reflecting the web’s strong push toward quantum-safe security. Its progress is crucial, as TLS protects the vast majority of online communications and transactions. Infrastructure protocols such as SSH and VPNs are also making significant strides, ensuring that core systems and secure remote access channels are not left vulnerable during the transition.
Certificates, especially X.509, play a pivotal role in this ecosystem. Without quantum-resistant certificates, other protocols such as TLS and VPNs cannot operate securely, making the advancement of PQC essential for the comprehensive deployment of these protocols. However, not all areas are advancing at the same pace. Email and messaging protocols, including S/MIME and OpenPGP, are lagging and will require increased focus and industry collaboration to overcome their slower adoption rates. DNSSEC remains a particularly glaring weak point; its stalled progress poses a risk to the overall security framework, as secure domain name authentication is fundamental for trustworthy communications.
Lastly, the heatmaps send a clear warning that TLS 1.2, still in use in many environments, offers no path to PQC, and organizations clinging to this outdated protocol face growing security risks, underscoring the urgency of migrating to modern, quantum-safe alternatives.
These heatmaps aren’t just monthly updates. They showcase the collaborative efforts of researchers, vendors, regulators, and operations teams. They highlight the gap between an idea and a solution, as well as between hope and actual protection. For anyone planning a PQC strategy, these heatmaps serve as practical roadmaps. They guide upgrades, demonstrate the maturity of different standards, and indicate whether it’s safe to move quickly or whether it’s better to be cautious. If your systems rely on protocols still in “draft,” integration will be experimental. When the heatmap indicates a shift from adoption proposals, it signals that industry leaders are leading the way, and it’s time to follow suit.
How can Encryption Consulting Help?
If you are wondering where to start your Post-Quantum Cryptography (PQC) journey, Encryption Consulting is here to guide you. Utilizing NIST-aligned planning, targeted risk reduction, and in-depth crypto discovery, our PQC Advisory Services enable you to transform your environment into an audit-ready, quantum-resilient infrastructure.
-
Comprehensive PQC Risk Assessment
This foundational phase builds visibility into your cryptographic infrastructure. We identify systems at risk from quantum threats and assess the readiness of PKI, HSMs, and applications. Certificates, keys, algorithms, and protocols across on-prem, cloud, and hybrid environments are scanned. Key metadata such as algorithm type, key size, and expiration is collected, creating a detailed inventory of cryptographic assets to support risk assessment and planning.
-
Personalized PQC Strategy & Roadmap
With visibility established, we engage stakeholders to assess quantum vulnerabilities and readiness for PQC transition. Cryptographic elements, especially RSA, ECC, and similar algorithms, are analyzed for their exposure to quantum threats. PKI and HSM configurations are reviewed, and applications with hardcoded cryptography are identified and addressed. The outcome is a comprehensive report detailing vulnerable assets, risk levels, and migration priorities.
-
Cryptographic Agility
After identifying risks and setting priorities, we develop a tailored, phased strategy that emphasizes cryptographic agility, enabling your systems to support multiple algorithms and seamlessly transition as standards evolve flexibly. This approach aligns with business, technical, and regulatory requirements, incorporating agile system designs that allow algorithm updates without major disruptions.
-
Vendor Evaluation and Proof of Concept
We help identify and test the right tools, technologies, and vendors to support your post-quantum goals. RFI/RFP requirements, covering algorithm support, integration, and performance, are defined, and leading PQC-capable vendors are shortlisted. Proof-of-concept testing is conducted in isolated environments to assess fit, with results summarized in a vendor comparison matrix and recommendation report.
-
Pilot Testing and Scaling
Before full rollout, solutions are validated through controlled pilot tests to ensure readiness and reduce disruption. Cryptographic models are tested in sandbox environments, typically on one or two applications, to verify interoperability with existing systems. Feedback from IT, security, and business teams is incorporated to refine the plan. Following successful testing, a phased rollout gradually replaces legacy algorithms while maintaining security and compliance.
-
PQC Implementation
With the strategy finalized, we execute a full-scale migration, integrating PQC into your live environment while ensuring compliance and continuity. Hybrid models that combine classical and quantum-safe algorithms enable a seamless transition. PQC support is deployed across PKI, applications, infrastructure, cloud, and APIs. We provide hands-on training, detailed documentation, and establish monitoring and lifecycle management to track cryptographic health, detect issues, and enable future upgrades.
Our services categorize data by lifespan and implement customized quantum-resistant protection for long-term confidentiality. We provide enterprise-wide crypto strategies and remediation plans to address weak or outdated algorithms. Migration to post-quantum algorithms is seamless, ensuring lasting resilience. We emphasize the development of crypto-agile PKI architectures and robust governance structures that define roles, responsibilities, and standards for cryptography in the post-quantum era.
Contact us at info@encryptionconsulting.com to leverage our PQC Advisory Services and future-proof your cryptographic environment.
Conclusion
The journey toward post-quantum cryptography is both important and complex, and every organization needs to approach it with careful planning and consideration. Heatmaps give a clear and dynamic view of this changing landscape, offering both a big-picture overview and detailed insights into the progress of key cryptographic standards. By highlighting which protocols are moving forward quickly and which are still lagging, these heatmaps enable organizations to make informed decisions, set the right priorities, and adopt post-quantum solutions with confidence.
As quantum computing approaches reality, moving in time is not just a technical step, but a strategic one to protect digital trust and security. Using the insights from these heatmaps as a guide, organizations can turn uncertainty into opportunity and build strong, future-ready systems for the quantum era.