Upgrading Vormetric Data Security Manager (DSM) can seem relatively straightforward, but if something goes wrong, the data can be lost or can get corrupted. This article does not provide the steps you would need to upgrade, but rather would provide what organizations need to be careful about, a few technical and non-technical points that you may not find in the upgrade guide.
This article will highlight all the steps you need to be careful about and a few details you might be curious about.Readers can use this article as a checklist or a base to develop a plan for upgrading their DSM. Every DSM upgrade can be different and unique to the organization, so it would be best if the organization gets some outside consultation to get the best planning for their environment.
Planning
Everything starts with good planning, and the DSM upgrade is no different. A full scan of the current environment is vital to assess any future roadblocks or challenges you might face.
-
Keeping a note of all the agents along with their agent versions and guardpoints When you upgrade the DSM, you can check the list of all the agents available and if all the guardpoints are up or not. If something doesn’t match as expected, you may need to troubleshoot them before proceeding. Agent versions can also highlight if you have any agents in the environment which are incompatible with the DSM version you desire to upgrade.
A compatibility matrix will help you determine which agents are compatible and which need to be upgraded. You can also develop an upgrade path that you would need. Thales has defined an upgrade path that must be followed if you desire a particular version. For example, if you upgrade to 6.2 from 5.3, you cannot directly upgrade to 6.2 without upgrading to the intermediate version 6.0.0.
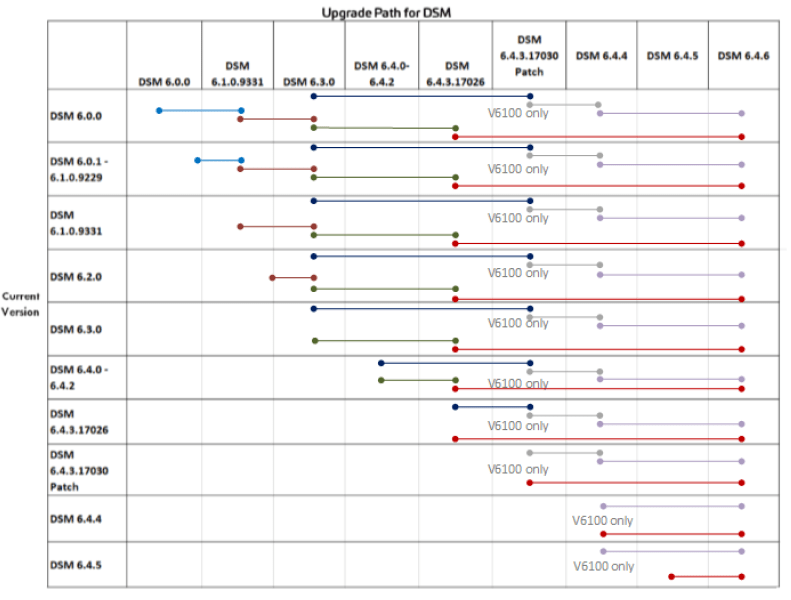
- Production cutover
Many organizations looking forward to upgrading should already have a production DSM working in their environment. They would not like to upgrade their existing production DSM, instead would use another DSM to upgrade and conduct pilot testing before switching to the new DSM as the production DSM. Organizations should plan the cutover accordingly.
Planning can ensure the following steps are smooth and DSM can be upgraded to the desired version without hiccups.
Upgrading DSMs
Planning can help soothe the upgrade, but upgrading a production DSM can expose challenges you might not have expected. Some of the challenges we have faced are:
- Cutting over from old DSM to new DSM without agent registration
- Upgrading DSM to a particular version where agents remain compatible
- Configuring HA cluster with DSMs being on different subnets
- Upgrading DSMs can also take time, and without proper planning of cutover, the production can also face downtime. But with adequate planning, DSM cutover can be seamless with no downtime.
Organizations should prepare exhaustively for upgrading DSMs as a wrong move can cost them terabytes of unobtainable data.
Migration to CipherTrust Manager
Thales announced that Vormetric DSM will reach the end of life on June 2024; as a result, many organizations are also looking forward to migrating their DSMs to CipherTrust Manager.
Migrating to CTMs can come with a unique wave of challenges where some organizations might be concerned with the availability of policies, keys, usersets, process sets, and other configurations that may already exist in their DSM. Other concerns organizations may have can be:
- Policies, keys, user sets, and process sets migration
- Migration of hosts
- High Availability configuration
- Downtime and system disruption
- Data Loss
If organizations are already on DSM 6.4.5 or 6.4.6, they can migrate to CipherTrust Manager and restore the following objects:
- Agent Keys, including versioned keys and KMIP accessible keys
- Vault Keys
- Bring Your Own Keys (BYOK) objects
- Domains
- CipherTrust Transparent Encryption (CTE) configuration
The objects that are not restored are:
- Most Key Management Interoperability (KMIP) keys except KMIP-accessible agent keys
- Keys associated with CipherTrust Cloud Key Manager (CCKM), including key material as a service (KMaaS) keys.
- DSM hostname and host configuration
When customers migrate, we recommend exhaustive pilot testing to ensure the migration goes smoothly without data loss. Customers should also conduct a cleaning session of the DSM where all decommissioned servers and users are removed before migrating to CipherTrust Manager. If customers migrate from DSM to CTM, agents running VTE agents (below version 7.0) would need to be upgraded to CipherTrust Transparent Encryption before upgrading so that migration can be seamless.
Benefits of migrating to CipherTrust Manager
- Improved browser-based UI
- No hypervisor limitation
- Fully featured remote CLI interface
- Embedded CipherTrust Cloud Key Manager (CCKM)
- Better Key Management capabilities with KMIP key material – integrates policy, logging, and management – bringing simplified and richer capabilities to KMIP
- Supports CTE agents (renamed from VTE agents) from version 7.0
- New API for better automation
Even though these improvements are for the CTM platform as a whole, there are also some specialized improvements organizations may want to consider:
- Password and PED Authentication
Similar to S series Luna HSM, Thales provides the choice of password and Pin Entry Device (PED) as authentication mechanisms for CTM. This can provide improved security but is only available for k570 physical appliances.
-
Multi-cloud deployment is also possible where customers can deploy on multi-cloud such as AWS, Azure, GCP, VMWare, HyperV, Oracle VM, and more. They can also form hybrid clusters of physical and virtual appliances for high-availability environments.
Conclusion
Upgrading to DSMs can be challenging and require thorough planning and troubleshooting, but migrating to CTMs can be another level, as CTMs are a different product. If organizations opt to migrate, they would need to develop new runbooks, standard operation procedures (SOPs), and architecture and design documents. With two years remaining to reach the end of life, organizations should plan if they plan to migrate to CTM or if they would want to explore other options.
Encryption Consulting can help customers plan and also help in upgrading and migrating their existing DSMs. Being a certified partner with Thales and supporting Vormetric customers with their implementations and upgrading for years, Encryption Consulting can help plan a full-fledged migration to CipherTrust Manager.
Encryption Consulting can also provide gap assessments and pre-planning to ensure customers do not face any data loss or serious challenges that would lead to downtime or other production issues. Contact us for more information.
Sources:




