Education Center, Encryption Basics
What is Key Management? How does Key Management work?

Education Center, Encryption Basics

Cryptographic keys are a vital part of any security system. They do everything from data encryption and decryption to user authentication. The compromise of any cryptographic key could lead to the collapse of an organization’s entire security infrastructure, allowing the attacker to decrypt sensitive data, authenticate themselves as privileged users, or give themselves access to other sources of classified information. Luckily, proper management of keys and their related components can ensure the safety of confidential information. Key Management is the process of putting certain standards in place to ensure the security of cryptographic keys in an organization. Key Management deal with the creation, exchange, storage, deletion, and refreshing of keys. They also deal with the members access of the keys.
Key management forms the basis of all data security. Data is encrypted and decrypted via the use of encryption keys, which means the loss or compromise of any encryption key would invalidate the data security measures put into place. Keys also ensure the safe transmission of data across an Internet connection. With authentication methods, like code signing, attackers could pretend to be a trusted service like Microsoft, while giving victim’s computers malware, if they steal a poorly protected key. Keys provide compliance with certain standards and regulations to ensure companies are using best practices when protecting cryptographic keys. Well protected keys are only accessible by users who need them.
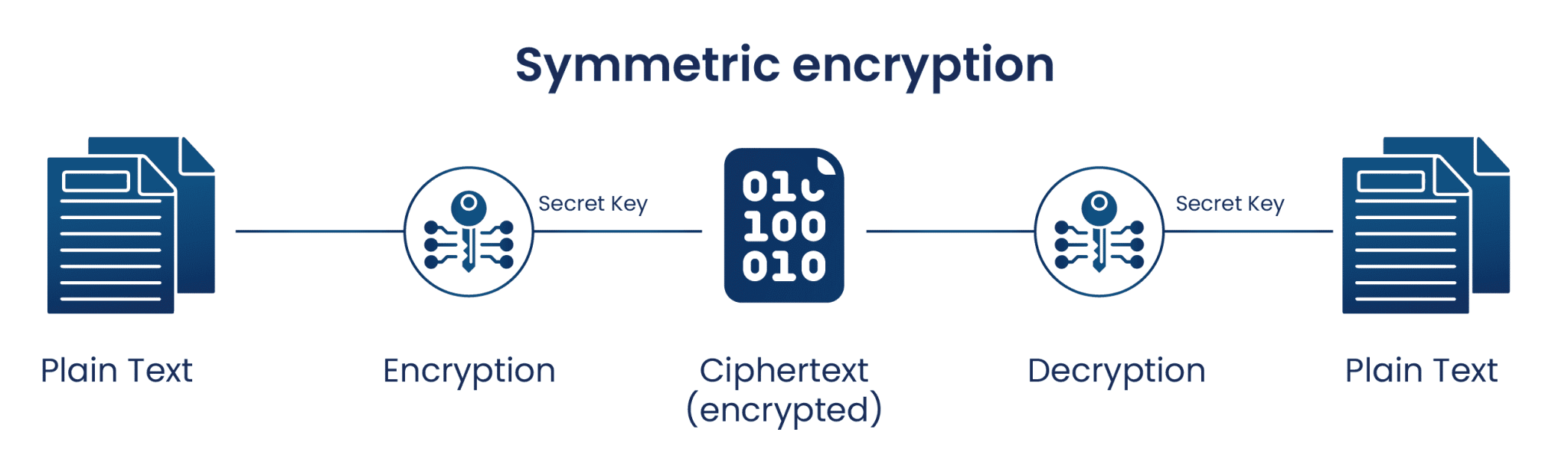
There are two types of cryptographic keys, symmetric and asymmetric keys. Symmetric keys deal with data-at-rest, which is data stored in a static location, such as a database. Symmetric key encryption uses the same key for both encryption and decryption. Using data in a database as an example, while the data is stored in the database, it is encrypted with the symmetric key. Once an authorized user attempts to access the data, the information is decrypted with the same symmetric key and made accessible to the user. The other type of cryptographic key is an asymmetric key.
Encryption using asymmetric keys is a little more complicated than symmetric key encryption. Instead of using the same key for both encryption and decryption, two separate keys called a public and private key, are used for the encryption and decryption of data. These keys are created as a pair, so that they relate to each other. The public key of a pair of asymmetric keys is mainly used to encrypt data. This key can be shared with anyone since it encrypts, not decrypts, data. The private key is used for the decryption of data encrypted by its public key counterpart, so it must stay secure.
Asymmetric keys focus on encrypting data-in-motion. Data-in-motion is data sent across a network connection, whether it be a public or private connection. When transporting sensitive data, most encryption processes use both symmetric and asymmetric keys to encrypt data.
Key management follows a lifecycle of operations which are needed to ensure the key is created, stored, used, and rotated securely. Most cryptographic keys follow a lifecycle which involves key
The generation of a key is the first step in ensuring that key is secure. If the key in question is generated with a weak encryption algorithm, then any attacker could easily discover the value of the encryption key. Also, if the key is generated in an insecure location, the key could be compromised as soon as it is created, resulting in a key that cannot be safely used for encryption. Key generators, AES encryption algorithms, or random number generators tend to be used for secure key generation.
The next step of the key lifecycle is ensuring the safe distribution of the keys. Keys should be distributed to the required user via a secure TLS or SSL connection, to maintain the security of the keys being distributed. If an insecure connection is used to distribute the cryptographic keys, then the security of any data encrypted by these keys is in question, as an attacker could execute a man-in-the-middle attack and steal the keys.
After distribution of the key, it is used for cryptographic operations. As previously noted, the key should only be used by authorized users, to make certain the key is not misused, copied, etc. When the key is used to encrypt data, it must then be stored for later decryption. The most secure method is via a Hardware Security Module (HSM) or CloudHSM. If an HSM is not used, then the keys can either be securely stored on the client’s side, or, if the keys are used on the Cloud, then the Cloud Service Provider’s Key Management Service can be used.
Once a key’s cryptoperiod, or time period the key is usable, passes, the key must be rotated. When the key of an encrypted set of data expires, the key is retired and replaced with a new key. First the data is decrypted by the old key or key pair and then encrypted by the new key or key pair. Rotation is necessary because the longer a key is in rotation, the more chance there is for someone to steal or find out the key. Rotation of keys can happen before the cryptoperiod expires in cases where the key is suspected to be compromised.
Two other ways of dealing with a compromised key are revoking or destroying the key in question. Revoking a key means the key can no longer be used to encrypt or decrypt data, even if its cryptoperiod is still valid. Destroying a key, whether that is due to compromise or due to it no longer being used, deletes the key permanently from any key manager database or other storage method. This makes it impossible to recreate the key, unless a backup image is used. NIST standards require that deactivated keys be kept in an archive, to allow for reconstruction of the keys if data encrypted in the past must now be decrypted by that key or key pair.
A very common term you will hear in the Key Management space is Key Management Services, also referred to as KMS. KMS is Key Management offered as a service to end-users, allowing you to create and manage your keys without needing to deal with the management of the hardware involved. Certain cloud service providers offer KMS to customers, basically offering them a cloud-based HSM to store their keys. This allows the customer to focus on managing their keys without having to deal with the management or price of an on-premises HSM of their own. The service provider themselves will actually manage the HSM, while you maintain full control and access to your keys.
Compliance standards and regulations ask a lot of key management practices. Standards, created by the NIST, and regulations, like PCI DSS, FIPS, and HIPAA, expect users to follow certain best practices to maintain the security of cryptographic keys used to protect sensitive data. The following are important practices to follow to ensure compliance with government regulations and standards.
Avoid hard-coding keys
The most important practice with cryptographic keys is never hard-coding key values anywhere. Hard-coding a key into open-source code, or code of any kind, instantly compromises the key. Anyone with access to that code now has access to the key value of one of your encryption keys, resulting in an insecure key.
Least privilege
The principle of least privilege is the idea that users should only have access to keys that are absolutely necessary for their work. This assures only authorized users can access important cryptographic keys, while providing better tracking of key usage. If a key is misused or compromised, only a handful of people have access to the key, so the suspect pool is narrowed down if the breach was within the organization.
HSMs
HSMs are a physical device which stores cryptographic keys and performs cryptographic operations on-premises. For an attacker to steal the keys from an HSM, they would need to physically remove the device from the premises, steal a quorum of access cards needed to access the HSM, and bypass the encryption algorithm used to keep the keys secure. HSMs on the Cloud are also a viable key management storage method, but there is always the chance that the Cloud Service Provider’s security fails, allowing an attacker to access the keys stored therein.
Automation
Automation is widely practiced method of ensuring keys do not go past their cryptoperiod and become over used. Other portions of the key lifecycle can be automated as well, like creating new keys, backing up keys regularly, distributing keys, revoking keys, and destroying keys.
Create and Enforce Policies
Creating and enforcing security policies relating to encryption keys is another way many organizations ensure the safety and compliance of their key management system. Security policies provide the methods everyone within an organization follows, and creates another method of tracking who can and has accessed certain keys.
Separate Duties
Separating duties related to key management is another important practice for any organization. An example of separation of duties is that one person is assigned to authorize new user’s access to keys, while another distributes the keys, and a third person creates the keys. With this method, the first person cannot steal the key during the distribution phase, or learn the value of the key during the generation phase of the key lifecycle.
Split Keys
One final practice to ensure the strength of any key management system is by splitting the keys into multiple portions. In this way, no one person knows the full key, rather multiple people must come together to use the key. This assures that others can be held responsible by their peers, if their portion of the key is compromised.
Encryption Consulting Training and Blogs
Encryption Consulting provides a variety of methods to create your own successful system for encryption key management. We host monthly webinars relating to key management, public key infrastructure (PKI), and more. We also provide assessments and training for HSMs, PKIs, and more. We can ensure your system is meeting compliance standards, and protecting data with the best methods possible. We also write weekly blogs that can help you find the best practices to use for your key management needs and learn more about the different aspects of data security.