- What is Code Signing, and how does it work?
- Why Code Signing Matters in Software Development?
- Why Recent Cyber Attacks Prove Secure Code Signing is Essential?
- Some Best Practices in Code Signing for Securing the Software Supply Chain
- Encryption Consulting's Role in Enhancing Software Security Through Code Signing
- Conclusion
With the growing digital technologies, cyber threats are evolving at the same pace, ensuring that the security and integrity of software are non-negotiable. Code signing plays a major role in securing software authenticity, preventing tampering, and establishing trust between developers and end-users. However, simply signing the code is not enough for organizations. They must adopt best practices to mitigate risks and maintain a secure software supply chain.
Before diving into the best practices, let’s first understand what Code Signing is, its role in DevOps and CI/CD pipelines, and how it helps prevent real-world cyberattacks.
What is Code Signing, and how does it work?
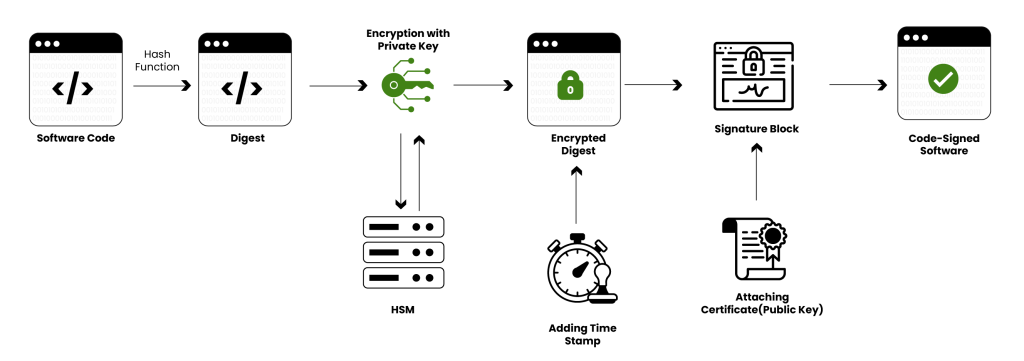
Code signing is a security mechanism used to verify the authenticity and integrity of software code, scripts, or executables. It involves digitally signing software to confirm that it comes from a trusted source and has not been altered or tampered with since it was signed.
The process begins with hashing, where the software is converted into a unique, fixed-length string (such as SHA-256). This hash is then encrypted with the developer’s private key (securely stored, often in a Hardware Security Module, or HSM) to create a digital signature, which is embedded into the software along with metadata such as the timestamp and certificate (public-key) details.
When a user downloads the software, their system decrypts the signature using the developer’s public key (from the attached certificate) and compares it with a freshly computed hash of the downloaded file. If they match, the file is verified as unaltered.
Why Code Signing Matters in Software Development?
As we have already mentioned, Code Signing plays an important role in securing software authenticity and tampering. We will be exploring in detail how code signing is crucial in software development.
Ensures Software Integrity
Code signing guarantees that the software has not been altered since it was signed by the developer. When the code is signed, a cryptographic hash is generated and encrypted with the developer’s private key. If even a single byte in the file changes (due to malware injection or corruption), the hash verification fails, thereby alerting users that the software may be compromised. This prevents attackers from distributing modified versions of legitimate software, protecting both developers and end-users.
Verifies Authenticity and Trustworthiness
Without code signing, users have no reliable way to confirm whether software comes from a legitimate publisher or not. Code signing certificates that are issued by trusted Certificate Authorities (CAs) can bind the software to a verified organization or developer. When users install signed software, their operating system displays the publisher’s name (e.g., “Microsoft Corporation” instead of “Unknown Publisher”), which increases trust and reduces security warnings. This is especially important for enterprise software, drivers, and financial applications where source verification is critical.
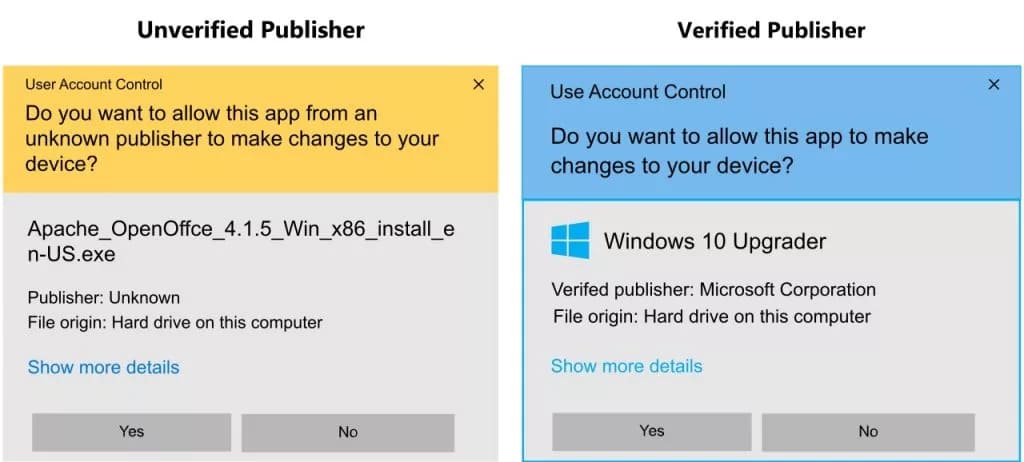
Issued by trusted Certificate Authorities (CAs), these certificates come in different types based on the level of validation and trust they offer.
- Individual Validated (IV) Certificates: Designed for individual developers, IV certificates verify the person’s identity using official documents. While suitable for personal or small-scale projects, they offer basic trust and may still trigger warnings on certain systems.
- Organization Validated (OV) Certificates: Issued to legally registered organizations after verifying their business credentials. OV certificates display the company name in the digital signature, offering a moderate level of trust for distributing both internal and public software.
- Extended Validation (EV) Certificates: The highest assurance certificate, EV certificates involve thorough business and identity verification. They deliver instant reputation benefits, suppress security warnings, and prominently display the verified publisher’s name during installations — ideal for public, enterprise, and security-sensitive software.
Prevents Malware and Supply Chain Attacks
Cybercriminals often distribute malware by impersonating legitimate software or injecting malicious code into updates. Code signing mitigates this risk by ensuring that only properly signed and verified code executes. If an attacker attempts to modify a signed executable, the digital signature is broken, and the system blocks it. This is particularly vital in supply chain security, where attackers compromise software vendors to distribute trojanized updates, such as the SolarWinds attack. Code signing acts as a safeguard against such threats.
Facilitates Secure Software Updates
Software updates are a common attack vector where hackers use unsigned updates to push malware. Code signing ensures that only the original publisher can allow updates. When an application checks for updates, it verifies the digital signature before installation, which helps in preventing man-in-the-middle (MITM) attacks and unauthorized modifications.
Why Recent Cyber Attacks Prove Secure Code Signing is Essential?
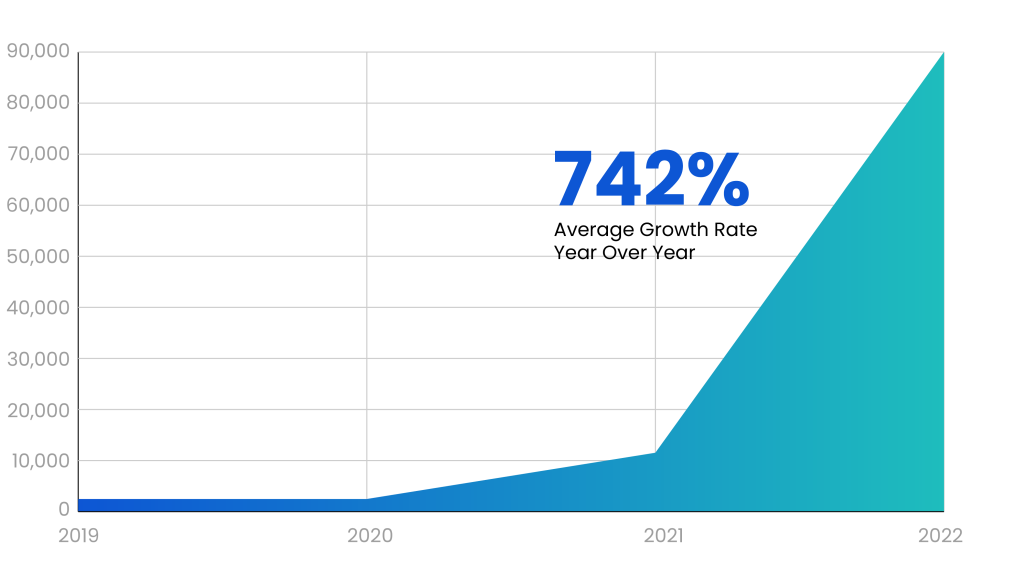
Numerous high-profile cyberattacks demonstrate how attackers exploit vulnerabilities in software supply chains, making Code Signing even more essential. In the past couple of years, there has bee a steep rise of around 742% in next-generation Software supply chain attacks.
Below are some real-world cyberattacks and the lessons learned over the past few years.
3CX Supply Chain Attack (March 2023)
The 2023 3CX supply chain attack made a significant rise in software supply chain compromises. Attackers invaded the company’s build system to install malicious updates that were digitally signed with 3CX’s legitimate certificates. This sophisticated attack was attributed to North Korean state-sponsored actors that affected over 600,000 organizations globally through trojanized versions of the 3CX desktop app.
The incident revealed critical vulnerabilities in the build system security and demonstrated how even properly signed software updates can’t be blindly trusted. It signifies the need for multi-layered verification of software integrity that includes precise checks of build environments and continuous monitoring for abnormal behaviour in signed applications.
Other than checks and monitoring, we require multiple layers of protection beyond Code Signing. Some of these include:
Software Vulnerability Scanning
Software vulnerability scanners are tools that automatically check applications, code, and software environments for known security weaknesses. These scanners identify issues like outdated libraries, misconfigurations, insecure code patterns, and publicly known vulnerabilities (CVEs). By scanning software before release and during regular updates, developers can detect and fix security problems early, reducing the risk of attackers exploiting them later. Vulnerability scanning is a key part of modern DevSecOps practices, ensuring continuous security throughout the software lifecycle.
Software Bill of Materials (SBOM)
An SBOM (Software Bill of Materials) is a detailed list of all the components, libraries, and dependencies used in a software application. It works like an ingredient list for software, making it easy to track what’s inside a program. By maintaining an SBOM, organizations can quickly identify if any third-party or open-source component they use has known vulnerabilities, outdated libraries, or licensing risks. It plays a vital role in improving software security, especially in managing and reducing risks from the software supply chain.
MOVEit Transfer Exploitation (June 2023)
The MOVEit attack by the Cl0p ransomware group showed how supply chain vulnerabilities can bypass code signing protections. While not a direct code-signing breach, the mass exploitation of this widely used file transfer solution allowed attackers to intercept software updates and patches in transit.
This created a scenario where properly signed software could be swapped with malicious versions during delivery. The incident demonstrated that code signing alone is insufficient – organizations must also verify the integrity of distribution channels and implement checksum validation to ensure that signed packages remain unaltered after signing.
Applied Materials Incident (February 2023)
The semiconductor giant’s breach involved stolen credentials being used to access sensitive systems, potentially including code-signing infrastructure. While full details remain undisclosed, the attack demonstrated how social engineering and credential theft can avoid even strong code-signing protections.
This case also underscores the risks of integrating code signing into automated CI/CD pipelines without proper security controls. While automation boosts development speed and efficiency, it can also increase exposure if not managed securely. When signing processes are built into pipelines, attackers who compromise build servers or CI/CD environments can potentially push malicious code and have it automatically signed without triggering alerts.
To mitigate this, organizations must treat code signing operations as high-trust actions. That means implementing multi-factor authentication, limiting access to signing credentials, using hardware security modules (HSMs) or cloud-based key management solutions, and adding manual approval steps or policy checks before any signing takes place. Automation should be balanced with strong access controls and monitoring to ensure security doesn’t get sacrificed for speed.
SolarWinds Attack (December 2020)
The SolarWinds attack was a sophisticated supply chain compromise in which Russian state-sponsored hackers infiltrated the company’s software development systems and secretly inserted malicious code into legitimate updates for SolarWinds’ Orion IT monitoring platform. These tampered updates were digitally signed with SolarWinds’ valid certificates and then distributed to approximately 18,000 customers, including government agencies and major corporations, enabling attackers to spy on victims for a very long time.
By utilizing trusted update mechanisms and misusing code signing, the breach revealed critical weaknesses in software supply chain security, proving that even properly signed software can be weaponized if build environments are compromised. Therefore, Code Signing alone is not enough — if the build environment is compromised, even signed software can be malicious. To counter such risks, the industry is increasingly turning to reproducible builds as a powerful defense.
A reproducible build ensures that every time source code is compiled, it produces the same binary output, making it possible to verify that what was built is exactly what was intended. This process is often combined with pre-build and post-build hash validation, where a hash of the source code is recorded before the build, and the hash of the output binary is checked after the build. Any mismatch between the expected and actual output can signal tampering or unauthorized changes. Together, reproducible builds and hash validation help detect build-time compromises and add an extra layer of trust and transparency to the software supply chain.
Some Best Practices in Code Signing for Securing the Software Supply Chain
As stated earlier, improper code signing practices can introduce vulnerabilities that make applications susceptible to supply chain attacks, malware injections, and unauthorized modifications. Implementing high-end code-signing best practices helps organizations maintain trust, prevent tampering, and safeguard end-users from malicious threats. We will now be discussing some of the code-signing best practices that need to be implemented for secure software development.
Secure Private Key Storage in HSM
The foundation of secure code signing lies in protecting private keys from theft or misuse. Hardware Security Modules (HSMs) provide the highest level of protection by storing keys in specialized and tamper-resistant hardware that prevents extraction even if any server is compromised. These devices enforce strict access controls to ensure that keys can only be used for cryptographic operations but never exposed in plaintext.
Organizations handling sensitive software should use FIPS 140-2 Level 3-certified HSMs as they not only secure keys but also perform all cryptographic operations internally, thereby eliminating risks associated with memory-scraping attacks. This approach seems more essential after incidents like the SolarWinds attack, where compromised build systems could have been avoided by HSM-protected keys.
Enforce Multi-Factor Authentication and Approval Workflows
While HSMs technically protect keys, procedural controls prevent unauthorized use. Implementing multi-factor authentication (MFA) for accessing signing systems ensures that stolen credentials alone can’t initiate signing operations.
More importantly, establishing multi-person approval workflows where critical releases require authorization from multiple trusted team members creates accountability and reduces risks from both insider threats and credential compromise.
These controls should be integrated directly into CI/CD pipelines, with clear audit logs showing who approved each signing event. For example, after the JetBrains TeamCity breach, organizations realized that automated signing without human oversight could let attackers freely sign malicious code once they infiltrated build systems.
Implement Comprehensive Certificate Lifecycle Management
Effective code signing requires active management of certificates beyond just their initial issuance. Organizations should issue short-lived certificates that automatically expire after weeks rather than years, immediately revoke certificates at any sign of compromise through OCSP/CRL checks, and systematically rotate keys to limit exposure windows.
The MOVEit attack showed how long-valid certificates can become liabilities for an organization when vulnerabilities emerge. Modern approaches like certificate transparency logs and automated monitoring tools can help detect suspicious certificate usage patterns before they lead to breaches. For enterprises, integrating these practices with existing PKI infrastructure ensures consistent policy enforcement across all development teams.
Ensure Secure Signing Access Controls and Enforcement
Implementing least-privilege RBAC (Role-Based Access Control) for code signing is essential to mitigate supply chain risks. Production signing should be restricted to authorized release engineers through mandatory multi-factor authentication, while developers receive limited permissions in the test environment.
Automated policy enforcement must block high-risk actions, such as bulk signing of unusual file types, with all activities logged for audit. Modern solutions integrate these controls directly into CI/CD pipelines, combining technical restrictions with workflow approvals. This layered approach, when paired with HSM-protected keys, makes sure that stolen credentials alone can’t compromise signing operations, as demonstrated by post-SolarWinds security enhancements. Regular access reviews maintain both security and operational efficiency.
Establish Continuous Monitoring and Incident Response
Effective code signing security requires real-time monitoring of all signing activities through centralized logging and alerting. Security teams should monitor for abnormalities such as bulk signing requests, unusual file types being signed, or signing events arising from unexpected locations.
Integration with SIEM (Security Information and Event Management) systems enables correlation with other security events, facilitating the detection of coordinated attacks. Prepared incident response plans are also equally important, as they outline important steps for key rotation, certificate revocation, and software recall in the event of breaches.
The Okta breach demonstrated how a delayed response to credential compromises can exponentially increase damage, making rapid detection and containment capabilities critical for signing infrastructure.
Encryption Consulting’s Role in Enhancing Software Security Through Code Signing
Encryption Consulting strengthens software security through its CodeSign Secure solution, which enforces best code signing practices to build verifiable trust in software integrity. The platform automates secure signing workflows using HSM-protected keys, cryptographic validation, and granular access controls, all tightly integrated with CI/CD pipelines to ensure security doesn’t slow down development.
Beyond signing, CodeSign Secure embraces a multi-layered approach to secure the entire software supply chain. This includes support for reproducible builds and pre/post-build hash validation to detect tampering during the build process, generation and management of Software Bills of Materials (SBOMs) to track component-level risks, and seamless integration with vulnerability scanners to identify known threats before code is released.
By combining enterprise-grade automation with deep security expertise, Encryption Consulting helps organizations stay compliant, prevent supply chain attacks, and turn code signing into a strategic defense layer that protects both their software and brand in today’s high-risk digital environment.
Conclusion
Code signing is crucial in securing the software supply chain against tampering, malware, and unauthorized modifications. Real-world attacks have demonstrated that compromised signing processes can lead to devastating breaches, underscoring the importance of secure code signing in maintaining trust and compliance.
By implementing advanced practices, such as HSM-protected keys, granular access controls, and automated policy enforcement, organizations can ensure software integrity throughout the entire software development lifecycle, from development to deployment.
- What is Code Signing, and how does it work?
- Why Code Signing Matters in Software Development?
- Why Recent Cyber Attacks Prove Secure Code Signing is Essential?
- Some Best Practices in Code Signing for Securing the Software Supply Chain
- Encryption Consulting's Role in Enhancing Software Security Through Code Signing
- Conclusion




