In the fast-evolving landscape of modern business operations, the automation of certificate management has become indispensable. This is particularly true given the exponential growth of machine identities required for diverse applications such as IoT devices, cloud systems, APIs, containers, and applications. In this blog, we will explore the pivotal role of the Automated Certificate Management Environment (ACME).
Demystifying ACME
ACME, or Automated Certificate Management Environment, is a communication protocol designed to automate the intricate procedures involved in certificate issuance and domain validation. It empowers organizations to effortlessly deploy a public key infrastructure without the need for user interaction. Initially conceived by the Internet Security Research Group (ISRG) for their Let’s Encrypt service, ACME has undergone significant advancements.
The key versions of ACME and their respective milestones are as follows:
-
ACMEv1 (April 12, 2016
The initial release of ACME primarily focused on single-domain certificate issuance. It marked the beginning of ACME’s journey in automating certificate management.
-
ACMEv2 (March 13, 2018)
ACMEv2 was a pivotal update that brought substantial changes. It introduced support for Wildcard SSL/TLS certificates and enhanced user experience by streamlining existing functions. ACMEv2 aimed to make certificate automation more versatile and user-friendly.
-
ACME Becomes RFC 8555 (March 11, 2019)
This milestone elevated ACME’s status by standardizing it as RFC 8555. It solidified ACME’s position as a recognized protocol for certificate issuance and management on the Internet.
-
ACMEv1 End-of-Life (June 2021)
The official end-of-life announcement for ACMEv1 marked its discontinuation, pushing users to transition to the more advanced ACMEv2 protocol. This change ensured that ACME remained aligned with evolving security requirements.
Exploring ACME Certificate Management Protocol
ACME primarily serves the purpose of obtaining Domain Validated (DV) certificates, which undergo minimal verification. DV certificates validate only the domain’s existence, requiring no manual intervention. While ACME can also be employed to procure higher-value certificates, such as Organization Validated (OV) and Extended Validation (EV), these scenarios necessitate additional support mechanisms in conjunction with the ACME agent.
The core objective of the ACME protocol revolves around establishing HTTPS servers and automating trusted certificates, eliminating the potential for error-prone manual procedures. To utilize the protocol, two essential components come into play:
-
The ACME client, operational on any server or device requiring a trusted SSL/TLS certificate, initiates certificate management actions like issuance and revocation.
-
The ACME server, situated at a Certificate Authority (CA) such as Let’s Encrypt, responds to the requests of authorized clients.
Note: Communication between the client and server is carried out through JSON messages over HTTPS.
ACME offers flexibility in choosing CA providers, provided they support the protocol. While Let’s Encrypt recommends using the user-friendly certbot client due to its wide compatibility and robust documentation, alternative ACME clients like ACMESharp, acme-client, GetSSL, and others are available on platforms like GitHub, catering to diverse preferences and requirements.
Configuring ACME Clients
Before integrating ACME into your operations, you’ll need to select an ACME client, and there’s a wide array of client implementations available catering to various programming languages and environments. ACME’s design allows flexibility in choosing CAs, provided they support the protocol. The steps involved in setting up an ACME client are :
- The client requests the user to specify the domain they wish to manage.
- The client presents a selection of Certificate Authorities (CAs) compatible with the protocol.
- After the client’s choice, it establishes communication with the chosen CA and creates an authorization key pair.
- The CA issues challenges involving DNS or HTTPS to verify the client’s control over their domain(s).
- The CA supplies a nonce, a randomly generated number, which the agent signs with its private key to confirm its ownership of the key pair.
How do you utilize ACME to issue and revoke certificates?
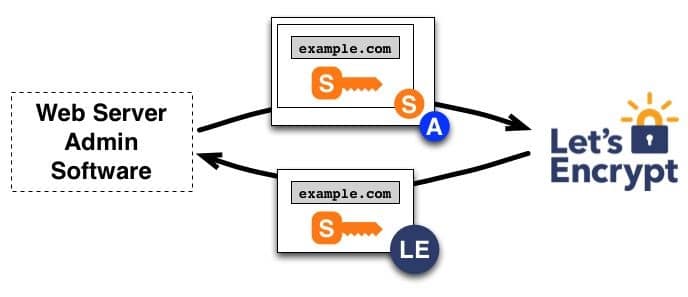
For issuance or renewal, a web server equipped with the ACME agent generates a Certificate Signing Request (CSR), which is then forwarded to the CA for processing.
Following are the steps for issuance of a certificate:
- The agent dispatches a Certificate Signing Request (CSR) to the CA, requesting the issuance of a certificate for the authorized domain, specifying a designated public key.
- The CSR is securely signed with the corresponding private key and the authorized key associated with the domain.
- Upon receiving the request, the CA verifies both signatures. If all checks pass, the CA issues a certificate for the authorized domain, utilizing the public key specified in the CSR, and promptly transmits it back to the agent.
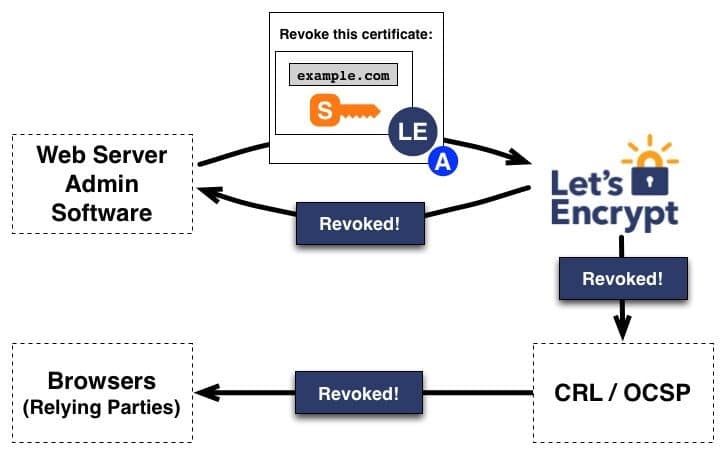
Below are the steps involved in the certificate revocation process:
The agent initiates the certificate revocation process by utilizing the authorized key pair associated with the domain to create a revocation request.- This revocation request is signed with the key pair to provide the necessary authentication.
- The CA receives the revocation request and proceeds with thorough validation to confirm its authorization.
- Once the CA confirms the authorization and validates the revocation request, it takes action to prevent the acceptance of the revoked certificate.
- To achieve this, the CA disseminates the revocation information through widely recognized revocation channels, such as Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP).
Unlocking the Benefits and Applications of ACME Protocol
The vision of the ACME initiative, championed by ISRG, revolves around achieving a 100% HTTPS web, highlighting the paramount importance of encryption. ACME accomplishes this by automating certificate procurement and management, simplifying HTTPS deployment, and enhancing PKIX-based authentication for a spectrum of TLS-based protocols.
ACME offers an array of advantages:
- It is cost-free, enabling anyone with a domain name to obtain a trusted certificate without financial constraints.
- It automates the entire certificate lifecycle, from issuance and renewal to revocation.
- It promotes implementing TLS security best practices for CAs and site operators.
- It operates as an open standard, promoting widespread adoption.
- It represents a collaborative endeavour that transcends the influence of any single organization
While debates may arise over the security of free certificates obtained via ACME, in practice, the validity and security of certificates rely on technical criteria rather than their cost.
Why ACME Outshines Other Certificate Automation Protocols?
ACME distinguishes itself among certificate automation protocols due to its status as an open standard, robust error-handling capabilities, adherence to industry best practices for TLS and PKI management, sustained support from a dedicated community, flexibility in handling backup CAs, and cost-effectiveness. Unlike alternative protocols, ACME offers a comprehensive, secure, and collaborative approach, rendering it the preferred choice for enterprises.
Improving Certificate Management with CertSecure Manager
CertSecure Manager is a cutting-edge solution that simplifies certificate management with a centralized platform. It automates the entire certificate lifecycle, from issuance to renewal and revocation, reducing the risk of errors and security vulnerabilities. CertSecure Manager enforces consistent security policies, offers real-time monitoring and alerts, and integrates seamlessly with existing infrastructure. This automation enhances security and scalability for organizations of all sizes in today’s digital landscape.
Conclusion
In conclusion, ACME stands as a revolutionary force in the realm of PKI and digital security. This protocol automates and simplifies certificate management, making it an essential tool for modern businesses navigating the complexities of digital security and encryption.
Embracing ACME is not merely a step towards a safer online environment but a giant leap towards a more secure, efficient, and cost-effective approach to certificate management.
- Demystifying ACME
- Exploring ACME Certificate Management Protocol
- Configuring ACME Clients
- How do you utilize ACME to issue and revoke certificates?
- Unlocking the Benefits and Applications of ACME Protocol
- Why ACME Outshines Other Certificate Automation Protocols?
- Improving Certificate Management with CertSecure Manager
- Conclusion




