The high-level architecture of Intune involves several components working together to manage and secure devices across different platforms. Intune architecture is designed to provide a comprehensive solution for modern device management and application deployment. The high-level architecture of Microsoft Intune comprises the following components:
Microsoft Intune Service
The Microsoft Intune Service provides us with the following capabilities:
-
Configuration of devices
To define settings and customize devices.
-
Protection of data
Control access, interaction, and deletion of company data on various devices.
-
App management
To deploy apps and configure application-related settings.
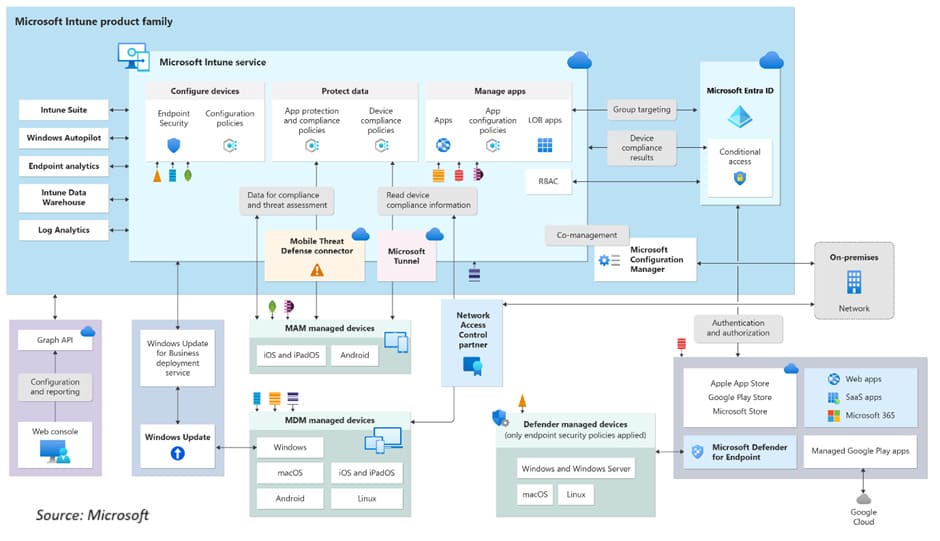
Microsoft Entra ID
Microsoft Entra ID, previously known as Azure Active Directory, is a cloud-based identity and access management service. It empowers the organization’s employees to reach external resources, such as Microsoft 365, the Azure portal, and numerous other SaaS applications. Additionally, Microsoft Entra ID facilitates access to internal resources, including applications on the corporate intranet and any cloud apps specifically developed for the organization.
Intune primarily relies on Microsoft Entra groups for grouping and targeting purposes. Upon enrollment in Intune, a device registers in Microsoft Entra ID. The compliance status of devices is communicated to Microsoft Entra ID. If the Conditional Access policies include Access controls set to “Require device to be marked as compliant,” Conditional Access utilizes this compliance status to decide whether to allow or block access to email and other organizational resources.
Intune Suite
Microsoft Intune Suite provides advanced endpoint management and security capabilities into Microsoft Intune.
Windows Autopilot
Windows Autopilot encompasses a set of technologies designed for the setup and pre-configuration of new devices, ensuring their seamless preparation for productive use. It is versatile, allowing deployment for both Windows PCs and HoloLens 2 devices. Furthermore, Windows Autopilot offers the capability to reset, repurpose, and recover devices as needed.
Endpoint Analytics
These analytical tools provide valuable insights for evaluating the operational efficiency of the organization and assessing the quality of the experience delivered to the users. Endpoint analytics is instrumental in identifying potential policies or hardware-related issues that could be impeding device performance. By utilizing these insights, one can proactively implement improvements before end-users encounter issues and submit help desk tickets.
Intune Data Warehouse
Intune Data Warehouse refers to a repository or storage system within the Microsoft Intune platform that gathers and organizes data related to device management, user activities, and other relevant information.
Log Analytics
Log Analytics in Intune refers to the feature that allows administrators to collect, analyze, and gain insights from logs generated by devices and applications managed through Microsoft Intune.
Mobile Threat Defense Connector
Intune can incorporate data from a Mobile Threat Defense (MTD) vendor, serving as a data source for both device compliance policies and device Conditional Access rules.
Microsoft Tunnel
Microsoft Tunnel serves as a VPN gateway solution within Microsoft Intune, operating within a Linux-based container. It enables secure access to on-premises resources from iOS/iPad and Android Enterprise devices through the use of modern authentication and Conditional Access. In instances where a device lacks compliance, access to both the VPN server and on-premises network is restricted.
Microsoft Configuration Manager
Microsoft’s Configuration Manager (SCCM) is Microsoft’s legacy tool for managing Windows devices. Co-management allows simultaneous management of Windows 10 or later devices using both Configuration Manager and Microsoft Intune. This approach enables the organization to leverage its existing investment in Configuration Manager while seamlessly incorporating new functionalities through cloud attachment.
Mobile Device Management (MDM) and Mobile Application Management (MAM)
MAM solely governs corporate applications and data. It offers finer control options within corporate resources, particularly applications.
MDM lets the user manage a corporate-owned device for personal or shared usage. There is more emphasis on security and compliance.
Network Access Control partner
Network Access Control (NAC) solutions verify device enrollment and compliance status with Intune to determine access control decisions. If the device is not enrolled or is enrolled but does not meet Intune device compliance policies, the device should be directed to Intune for enrollment or undergo a device compliance check.
Applications and application stores
Organizations can add and assign apps to devices and users. Microsoft Entra ID can be used by end users to authenticate and authorize various apps downloaded from different application stores.
Microsoft Defender for Endpoint
Integrating Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution aids in preventing security breaches and minimizing the impact of potential breaches across the organization.
Windows Updates
The Windows Update service is a built-in feature for Windows that allows the system to download and install updates.
The Windows Update for Business deployment service enables organizations to exert control and manage the deployment of Windows Updates to their devices.
Web Portal and Graph API
The Microsoft Graph API for Intune allows programmatic access to tenant-specific Intune information, enabling the execution of Intune operations equivalent to those accessible through the Azure Portal.
Conclusion
In conclusion, Microsoft Intune presents a comprehensive suite of services and features designed for advanced endpoint management and security. The high-level architecture encompasses key components that make it a robust solution for end-point management. Encryption Consulting provides Microsoft Intune services by integrating it with PKI, enabling features like Windows Hello for Business and remote device management. It empowers secure access from various devices while simplifying app management and policy automation. Microsoft Intune also integrates with mobile threat defense services and uses a web-based admin center to protect organizations’ data and focus on endpoint management.
- Microsoft Intune Service
- Microsoft Entra ID
- Intune Suite
- Windows Autopilot
- Endpoint Analytics
- Intune Data Warehouse
- Log Analytics
- Mobile Threat Defense Connector
- Microsoft Tunnel
- Microsoft Configuration Manager
- Mobile Device Management (MDM) and Mobile Application Management (MAM)
- Network Access Control partner
- Applications and application stores
- Microsoft Defender for Endpoint
- Windows Updates
- Web Portal and Graph API
- Conclusion
