Every day, the authenticity of those sending emails or running websites is questioned, as attackers will attempt to impersonate them to compromise the sensitive data of Internet users. A digital certificate is the most effective way to prove this authenticity. These certificates are not just created; they are also signed by trusted authorities known as Certificate Authorities, or CAs. CAs play a crucial role in establishing trust in the authenticity of digital certificates. They utilize a Chain of Trust, leading back to the original CA, which is kept offline and secure to ensure it cannot be compromised.
Certificates are not just created and given to users; they follow an important lifecycle that protects and renews them so that they can be continually used without fear of attackers stealing them and masking themselves as the certificate’s owner. Trust in certificates created by a certificate authority begins with the assurance that its certificate lifecycle is well-managed and immune to compromise. The certificate lifecycle is extremely important to implement, as it is the equivalent of the user’s identity to which it is issued.
How do you obtain a digital certificate?
The process of obtaining a digital certificate involves several steps. First, the applicant must generate a key pair, ensuring to keep the private key secret. Then, they need to create a Certificate Signing Request (CSR), which is a cryptographic file. This file is generated by an applicant seeking a digital certificate, such as an SSL/TLS certificate for a website. The CSR contains several pieces of information, including the public key generated by the entity, information about the entity requesting the certificate, and additional attributes such as email addresses or alternative names for Subject Alternative Name certificates.
The CSR can then be submitted to a private/public CA for certificate issuance. You can also generate self-signed certificates using tools like OpenSSL.
Once the CSR is submitted, the CA performs a validation process to verify the applicant’s authenticity. The process of verifying may change from one certificate type to another. Nevertheless, these are some common ways of validating:
-
Domain validation (DV)
The CA confirms that the entity controls the domain for which it has applied for certification. This may involve sending mail to a specified email address linked to the domain or adding particular DNS records to the domain’s DNS zone.
-
Organization Validation (OV) and Extended Validation (EV)
In the case of OV and EV certificates, CAs do further investigations to establish legal existence and organizational identity when requested for a certificate. They may look at official business documents like business licenses or articles of incorporation; they can manually check if the organization exists in real life by asking some questions about it.
Why is the Certificate Lifecycle important?
One of the reasons implementing the certificate lifecycle is important is due to what certificates are used for. Certificates identify websites and users on the Internet, meaning if a certificate were compromised at any point in its lifecycle, an attacker could pretend to be that person, and the user who that certificate belongs to would be blamed for any attacks associated with that certificate. Also, since the user’s key is associated with their digital certificate, that key would also be compromised, as would any data that was encrypted by that same key.
Another reason to maintain a strong certificate lifecycle is its use with websites. A compromise of a website’s digital certificate can result in outages, causing losses for the organization whose website it is. The website could also be used to infect user’s computers with malware or execute phishing campaigns, under the guise of the website owner. The first step to the proper implementation of a certificate lifecycle is knowing what each stage of the lifecycle is, and how to protect each stage.
Another reason is to ensure compliance with regulatory requirements. Many industries and jurisdictions have regulations and compliance requirements governing the use of digital certificates. Meta, the social media giant, was fined USD 1.3 billion in May 2023 after an Irish court ruled that it violated GDPR laws on international transfer. Meta and other big tech companies, such as Amazon and Twitter, have been slapped with hefty fines for noncompliance. With an increase in the number of digital certificates and proposals to decrease the validity period of certificates, it has become very important that organizations manage the certificate lifecycle to ensure compliance with industry standards.
What are the stages of the Certificate Lifecycle?
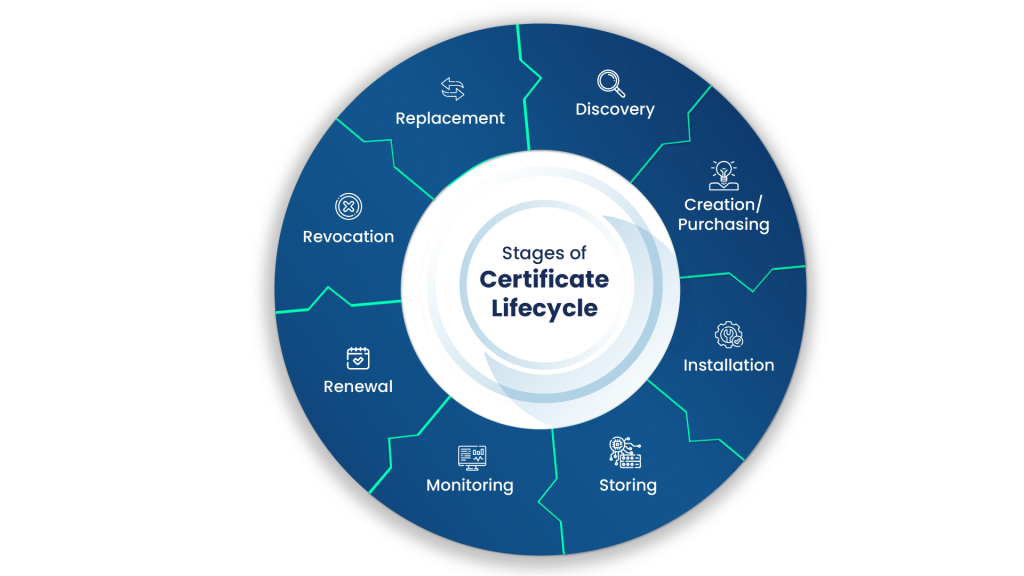
The stages of the certificate lifecycle are as follows:
-
Discovery
The discovery phase of the certificate lifecycle involves searching the network for missing, expired, compromised, or unused certificates that must be revoked, renewed, or replaced. This is an important part of the process, as it finds gaps in the security of certificates and relays these gaps to the monitoring phase, allowing for the sealing of these breaches. Normally, this phase also deals with the inventorying of certificates to help in future Discovery phases, along with any certificate audits that may occur.
-
Creation/Purchasing
This is the phase where the certificate is created. An online user, organization, or device requests a certificate from a Certificate Authority, which contains the public key and other enrollment information needed to enroll the user. The CA then verifies the given information and, if it is legitimate, creates the certificate. The Certificate Authority used to create the certificate can be owned by the organization that desires the certificate, or by a third-party. If the certificate is obtained from a third-party, then it must purchased from them.
-
Installation
The installation of the certificate is straightforward, but still just as important. The certificate must be installed in a secure, but reachable, location, as users attempting to verify the authenticity of the certificate must have access to it. When the certificate is installed, the CA puts policies in place to ensure the security and proper handling of the certificate.
-
Storage
As previously mentioned, when the certificate is installed, it must be in a secure location to prevent compromise. It should not, however, be so secure that the users that need to read the certificate cannot reach it. The proper policies and regulations to implement for storage of certificates will be discussed later in this document.
-
Monitoring
Monitoring is one of the most important stages of the certificate lifecycle. This is an almost constant phase where the certificate management systems, whether automatic or manual, watch for breaches, expirations, or compromises of digital certificates. The Monitoring stage uses the inventory created in the Discovery phase to keep track of when certificates should be revoked, renewed, or replaced. The certificate management system then moves those certificates to the next phase, which can be renewal, revocation, or replacement.
-
Renewal
Renewal of a certificate occurs when the expiry date of the certificate is reached. This occurs naturally with certificates, as best practice is to not use a certificate for more than 5 years at the most. Certificates can be set to renew automatically, or a list can be kept of certificate expiration dates and the administrator of the certificates can renew it at the proper time.
-
Revocation
If a certificate is found to be compromised, stolen, or otherwise negatively affected, then that certificate will be revoked. When a certificate is revoked, it is put on a Certificate Revocation List (CRL). This list ensures that other CAs know that this is no longer a valid certificate.
-
Replacement
The certificate is replaced when users switch from paying for certificates to creating their own Public Key Infrastructures (PKIs) and CAs. This is rarely done, as renewing a certificate from the original provider is much easier than replacing it.
Risks associated with Certificate expiry
Imagine a scenario where the digital certificate of your public-facing website, say an e-commerce website, expires. The user logs in, and all they see are errors and warning signs telling them your website is unsafe. If the organization is big, this can result in a loss of millions.
Some consequences of expired certificates are:
-
Service Disruptions and Downtime
When certificates associated with web servers, applications, or other online services expire, users may encounter error messages or security warnings when attempting to access these services. In many cases, web browsers block access to the website altogether, preventing users from accessing its content.
These websites are dependent on SSL/TLS certificates. If the certificate has expired, the TLS handshake will fail. When the expired certificate is presented, the client’s web browser or any other application will reject it as invalid. Such downtimes can lead to poor user experience.
-
Reputational damages
Expired certificates can damage the reputation of the website and its operators. Users may not want to visit the organization’s website again as they may associate it with security lapses. Customers, partners, and stakeholders may view the website as unprofessional or negligent in maintaining proper security measures, leading to reputational damage and potential loss of business opportunities.
-
Loss of Trust and Credibility
Users encountering security warnings or blocked access due to expired certificates can damage the trust between the organization and its customers. Although the customer may not be well-versed in the authentication process running in the background, the warning signs or messages would clearly create doubts regarding the security of their data while surfing the website.
-
Loss of revenue
Potential customers may go to your competitor’s website, considering your website unsafe. Some customers may view the content of the website despite the warning signs but not enter any personal details required for payments, leading to financial loss to your company.
-
Increased Risk of Cyber Attacks
Expired certificates increase an organization’s risk of cyber attacks by leaving systems vulnerable to exploitation by attackers. Some of the possible cyber attacks are:
- Man-in-the-Middle (MITM) Attack: A man-in-the-middle (MITM) attack is a cyber-attack where a malicious actor intercepts and possibly alters communications between two parties without their knowledge. In a typical MITM attack, the attacker may eavesdrop on the conversation, manipulate the transmitted data, or impersonate one or both parties.
- Compression Ratio Info-leak Made Easy(CRIME) Attack: The CRIME attack is a security vulnerability that targets the compression mechanisms used in the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. Due to this vulnerability, attackers can exploit the behavior of data compression combined with the encryption provided by these protocols to extract sensitive information.
- Padding Oracle On Downgraded Legacy Encryption(POODLE) Attack: The POODLE (Padding Oracle On Downgraded Legacy Encryption) attack is a security vulnerability that targets the SSL 3.0 protocol. Due to this vulnerability, attackers can decrypt sensitive information, such as cookies or authentication tokens, transmitted over SSL 3.0 connections.
- Raccoon Attack: The Raccoon attack is a cryptographic vulnerability that targets the Diffie-Hellman key exchange protocol used in many secure communication protocols, including TLS (Transport Layer Security) and IPsec (Internet Protocol Security). The attacker can recover the shared secret key exchanged during the key exchange process, compromising the communication channel’s confidentiality and integrity.
Protection of each phase of the Lifecycle
Each portion of the certificate lifecycle requires its level and methods of protection. The Discovery phase acts as a security measure in and of itself. By searching for expired or missing certificates, breaches can be detected before they become an issue. The Monitoring phase is similar, as it monitors for expired, improperly implemented, or compromised certificates. Both of these phases can be automated to allow for a better detection process. There is the potential for a manual management system missing a compromised or expired certificate.
The remaining phases require a strong level of protection and authentication. The Creation stage should ensure that the CA issuing the certificates has a valid Chain of Trust each time a new certificate is created. Installation should be correct, as poorly implemented certificates are a breach of security that an attacker can leverage for malicious purposes. The storage phase needs strong security so that threat actors do not compromise or misuse the certificates. The revocation, renewal, and replacement of certificates must also be done securely and correctly, as these stages begin the cycle again from the beginning.
Why automate Certificate Lifecycle Management?
Managing digital certificates manually involves numerous time-consuming tasks, such as issuance, renewal, deployment, and revocation. Tracking the expiration dates of certificates and creating certificate signing requests (CSRs) for installation on servers that need them, as well as updating configurations after new certificates have been installed, all these things take up valuable IT administrator hours that could be better spent elsewhere. They are labor-intensive processes that demand careful attention to be completed correctly within any reasonable timeframe.
Here are several reasons why automating the certificate lifecycle is essential:
-
Efficiency
Manually managing certificates is time-consuming and error-prone, especially in large-scale environments with many certificates. Automating the lifecycle of a certificate can smooth processes, save time for IT teams, and reduce their manual intervention.
-
Accuracy
Errors like misconfigurations missed renewals, or incorrect deployments of certificates may arise during manual management procedures for certificate lifecycles. Automating tasks involved in a certificate’s life cycle can minimize these mistakes.
-
Timeliness
Automated systems ensure that all necessary certificate renewals are done promptly and rotate or replace them where needed. To prevent expiry-induced service disruptions, there should be reminders for renewal, notifications on expiry dates, and workflows for automatic renewal of these documents.
-
Security
Administrators dealing with expired, invalid, or compromised certificates should enforce security policies by using strong key lengths and secure protocols, such as revocation of such certificates.
-
Scalability
With more organizations extending their digital presence, it becomes inevitable that they will have to handle an increasing number of certificates. The best way to do this is by having an automated certification life cycle management solution that can easily scale up with the increased number of certificates.
-
Adaptability
PCI DSS, HIPAA, and GDPR require compliance in their respective industries. To maintain compliance, a certificate lifecycle manager should enforce policies, monitor certificate usage, and generate audit reports.
-
Resource optimization
Automating the regular tasks associated with managing certificates can free IT resources within an organization to concentrate on more important activities, such as infrastructure optimization or innovation projects, regarding cyber security enhancement.
-
Prevention of risks
An expired certificate or a misconfigured encryption setting may result in certificate-based incidents that could expose an organization to various risks, including compliance violations and data breaches. Such risks can be managed through automation of the life cycle of certificates, which allows for proactive management and enforcement of security controls.
Best Practices in Certificate Lifecycle Management
To guarantee security, compliance, and operational efficiency in each stage of their existence, you need to manage certificates properly. Below are some good practices:
-
Inventory Management
Keep track of all the certificates used within your organization. Include information like when they were issued when they expire, what they’re for, who owns them, and which infrastructure they’re associated with. Consider grouping the certificates, say, by templates, to simplify management and tracking. Ensure the inventory data is updated periodically and the results are stored safely.
-
Centralized Management
Use one system or tool to manage certificates from a central location to simplify provisioning, renewals, and revocations. This will also enforce uniformity while minimizing manual mistakes. A dashboard that shows basic information about your certificates can be quite useful.
-
Automated Provisioning and Renewal
Establish certificate provision and renewal automation. This means an automated system can monitor expiry dates and renew certificates before services go down due to outdated certificates.
-
Policy Enforcement
Set out policies governing certificate issuance, use, and renewal. Apply such rules organization-wide without fail; this guarantees conformity to safety standards and statutory demands. These policies should specify who is authorized to request certificates, the types of certificates allowed, validation processes, and the acceptable Certificate Authorities (CAs). Establish validation procedures to verify the identity and authorization of certificate requesters.
-
Key Management
Ensure that private keys associated with certificates are managed correctly and kept safe. Use Hardware Security Modules (HSMs) to eliminate the possibility of theft or misuse and prevent human intervention in the key management process.
-
Least Privilege
Only authorized individuals should have access rights to certificate management systems or private keys. Use role-based access controls, where only people holding certain positions have specific privileges tied to their roles.
-
Regular Auditing and Monitoring
Regularly audit how certificates are used and configured to find potential weaknesses or misconfigurations. Implement systems that can detect unauthorized certificate usage or any other abnormality.
-
Enable Alerts and Notifications
Alerts and notifications can remind administrators about the approaching expiration of certificates so that they are renewed on time. Without these reminders, service disruptions or security vulnerabilities can occur if certificates expire and then are not renewed.
-
Backup and Recovery
Regularly back up both certificates and private keys. Such backups must also be stored securely and easily recoverable in the event of data loss or system failure.
-
Stay Updated
Stay informed about emerging technologies, industry standards, and best practices. Contact certificate authorities (CAs) and certificate management vendors to receive notifications about product updates, security patches, and new features.
Certificate Lifecycle Management Use Cases
Certificate Lifecycle Management (CLM) applies to different sectors and industries that use digital certificates to secure communication, verify identities, and meet regulatory compliance. Below are some areas where CLM can be employed:
-
Information Technology (IT) and Cybersecurity
SSL/TLS certificates are required for securing web servers, email servers, and other networked devices, making CLM an essential part of IT and cybersecurity operations. CLM facilitates the timely issuance of certificates and their renewal or revocation, which helps prevent security breaches while maintaining data confidentiality.
-
Financial Services
In this digital age, most of our transactions have become online. Online banking platforms and payment gateways require security, which is typically achieved by using digital certificates to encrypt financial data. CLM helps ensure the safety of the data and compliance with regulatory requirements.
-
Healthcare
Electronic health records (EHRs), patient portals, and telehealth platforms should be secured according to healthcare settings’ needs. Digital certificates are needed to encrypt healthcare data, verify doctors’ identities, and meet regulatory requirements concerning patient data’s safe transmission and storage. The absence of CLM can result in data breaches and service downtime.
-
Government and Public Sector
Government organizations and public sector authorities use CLM to protect their websites, citizen portals, and digital services. The technology supervises certificates deployed to secure online transactions between individuals or businesses, verifies that different government entities are genuine, and ensures adherence to rules.
-
Manufacturing and Industrial IoT (IIoT)
The manufacturing industry, where production takes place on a large scale with machines being controlled automatically through an internet connection to achieve higher efficiency levels, requires many more security measures than any other sector. CLM enables such enterprises to secure their devices used in the Internet of Things (IoT), industrial control systems (ICS), and supervisory control and data acquisition (SCADA). Certificates are issued for authentication purposes between devices themselves or between device controllers, protecting sensitive information from unauthorized access while ensuring its integrity remains intact during transmission over networks, thus preventing cyber attacks against vital physical infrastructures like power plants.
-
Retail and E-commerce
When it comes to online business transactions, especially those involving payments made electronically through various platforms, many people want assurance that all risks have been taken care of before proceeding further. Therefore, retailers must keep up with the latest technologies, such as CLM, which can help them create secured points where customers can shop without fear of losing money due to fraudulent activities. In addition, this system also manages SSL/TLS certificates essential in encrypting financial details provided by clients during the purchase process, safeguarding them from being intercepted along the way. Moreover, they ensure that only authorized merchants gain entry into payment gateways, thereby reducing cases related to cardholder data breaches.
-
Telecommunications and Networking
With the rapid growth rate experienced by communication networks worldwide today, coupled with the increase in the number of connected devices, an urgent need arises for stronger mechanisms capable of protecting against emerging threats within this sector. This is where CLM comes in handy since it deals mainly with secure configuration, monitoring, and control of various network elements, such as routers, switches, etc., used by service providers. Its key functions include authentication between different parts, such as VPN connections over public networks, provisioning devices on private ones, and authenticating users before allowing them access to specific resources or applications.
-
Energy and Public Services
CLM secures smart grid systems, energy management platforms, and utility networks in the energy and utilities sector. It authenticates devices, encrypts data transmissions, and ensures cyber security for energy delivery systems so they are not hacked or interrupted.
-
Education and Academic Institutions
CLM is an important part of any educational institution’s information technology infrastructure because it helps protect against unauthorized access to learning management systems (LMS), student portals, or online collaboration platforms. Additionally, CLMs authenticate users when needed, encrypt data being transmitted between different parts of the same system or across networks, thereby preventing unauthorized interception of such information, and provide secure access controls over student records, ensuring privacy compliance with relevant laws.
-
Transportation & Logistics
In the transportation & logistics industry, companies use CLMs to secure vehicle-to-vehicle communication (V2V), logistics tracking systems, and supply chain networks. This is done through authentication of vehicles involved in these operations, encryption of shipment-related information before sending it out, thus making sure only authorized persons can read such data while in transit or storage, verifying integrity during the transportation process, etc.
How can Encryption Consulting help?
Encryption Consulting provides a specialized Certificate Lifecycle management solution CertSecure Manager. From discovery and inventory to issuance, deployment, renewal, revocation, and reporting. CertSecure provides an all-encompassing solution. Intelligent report generation, alerting, automation, automatic deployment onto servers, and certificate enrollment add layers of sophistication, making it a versatile and intelligent asset.
Conclusion
The lifecycle of a certificate involves several key stages: discovery, creation, installation, storage, monitoring, renewal, revocation and replacement. Each stage plays a crucial role in maintaining the security and trustworthiness of digital communications and services. It is important to adhere to best practices for each stage of the certificate lifecycle to ensure safety against cyber-attacks. A Certificate Lifecycle Management solution can be of great help in managing your digital certificates and in preventing downtime and security breaches.
A CLM solution empowers your IT team to focus on strategic initiatives rather than tedious administrative tasks, saving time and resources while bolstering your organization’s security posture. Thus, in today’s age when the reliance on digital certificates is ever increasing, effective certificate lifecycle management becomes paramount.
- How do you obtain a digital certificate?
- Why is the Certificate Lifecycle important?
- What are the stages of the Certificate Lifecycle?
- Risks associated with Certificate expiry
- Protection of each phase of the Lifecycle
- Why automate Certificate Lifecycle Management?
- Best Practices in Certificate Lifecycle Management
- Certificate Lifecycle Management Use Cases
- How can Encryption Consulting help?
- Conclusion

