Education Center, Encryption Basics
Types of Tokenization: Vault and Vaultless

Education Center, Encryption Basics

Throughout the day, customers use payment cards for transactions, and these transactions must be done in a secure environment. Data used in a transaction with a customer is extremely valuable to attackers, so these transactions become a target for outside attack. According to PCI DSS compliance, the cardholder’s data should be kept secure, which can be done with tokenization. Tokenization is the process of replacing sensitive data with non-sensitive data. For example: if a customer is going to pay using payment card, the payment card number should not be readable. If the payment card’s number is xxxyyyzzzz, then using tokenization on this number would change it to apxcladajedpo9iiuwqdw.
There are two options for tokenizing information to choose from: vault and vaultless tokenization.
Vault Tokenization: In vault tokenization, we maintain a secure database called a tokenization vault database, in which we store the sensitive data, as well as it’s corresponding non-sensitive data. This table of sensitive and non-sensitive data can be used to detokenize the newly tokenized data.
Detokenization is the reverse process of tokenization where we fetch our original data from the tokenized data in the vault. In other words, we replace non-sensitive data with sensitive data to get the original data.
How Vault Tokenization Works: –
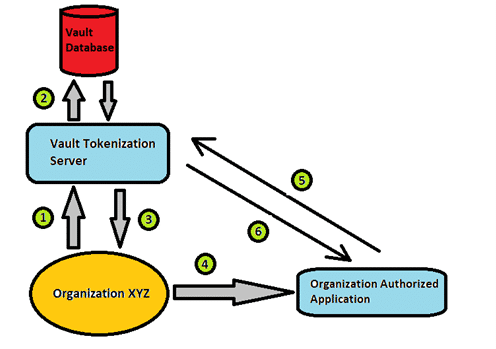
1. The organization passes its sensitive data to the vault Tokenization server.
2. The vault tokenization server converts the original data into non-sensitive data and saves its mapping in the vault database.
3. And the non-sensitive data is then sent back to the organization.
Note: – The organization always saves non-sensitive data.
4. To comply with PCI DSS, access control is necessary. So, whenever original data is required, the organization authorized application gets the non-sensitive data from the organization.
5. The application passes the non-sensitive information to the vault tokenization server which converts it into the original data, with the help of the vault database.
6. The organization authorized application now has the original data.
Disadvantage of Vault tokenization: – As the data increases, the size of the vault database increases, which in turn increases the processing time for detokenization. This also increases the detokenization implementation process.
To overcome the disadvantages of vault tokenization, vaultless tokenization comes into play.
Vaultless tokenization is more efficient and safer than vault tokenization, as it does not maintain a database, but instead uses secure cryptographic devices.
Secure cryptographic devices use standards-based algorithms to convert sensitive data into non-sensitive data or to generate tokens. For detokenization, these tokens can be used to generate original data without needing a tokenization vault database.
Compliance with PCI DSS standards necessitates robust measures like tokenization, which replaces sensitive data with non-sensitive equivalents. While vault tokenization involves storing data and corresponding tokens in a secure database, vaultless tokenization offers a more efficient and secure alternative, utilizing cryptographic devices without the need for a tokenization vault database. As organizations prioritize data security, implementing tokenization methods ensures the protection of sensitive information in payment card transactions.
With a strong focus on Encryption Advisory services and decades of consulting expertise, Encryption Consulting offers a range of cryptographic solutions. Among these, PKI as a Service (PKIaaS) stands out, providing round-the-clock support to clients for any issues related to their PKI environment. This comprehensive approach enhances security, ensuring organizations remain resilient against potential misconfigurations in their encryption setups.