The next time you are installing an app or a software update, you might wonder, “Should I trust this?” It’s a valid concern, specifically with the increasing risks of malware or other security threats. This is where code signing certificates come into the picture. These certificates ensure that the software you’re about to install hasn’t been tampered with and comes from a verified, trusted source. By authenticating the identity of the developer, code signing guarantees the integrity of the software.
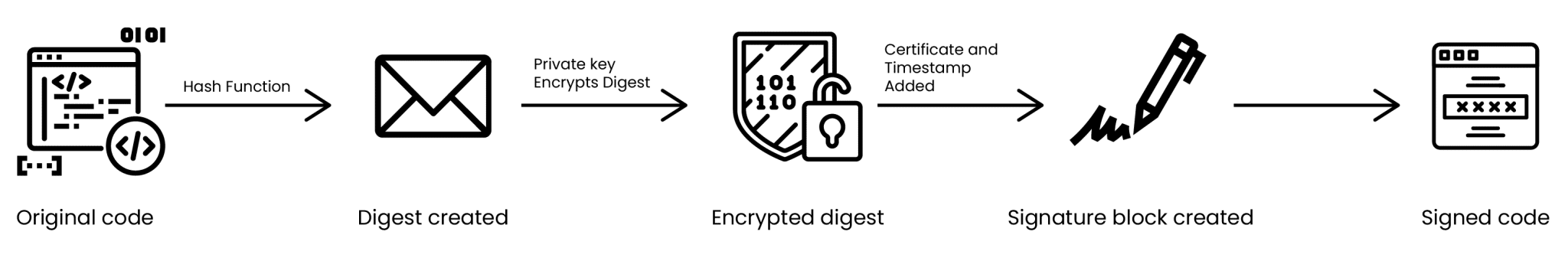
A code signing certificate can be described as an electronic approval from a software developer. It keeps you assured that the application is legitimate, i.e., it is coming from an authentic source and has not been corrupted during transmission. It’s much like closing an envelope containing a letter: if the envelope is closed, anyone who tries to open it will break the seal, making it obvious if it’s been tampered with.
Therefore, when you see the “trusted publisher” pop-up, that code signing functionality is in effect. This is the trust that certifies its software is real, has no changes, and can be used without any problems, ensuring software integrity and authenticity.
Types of code signing certificates
1. Standard Code Signing Certificates
Standard code signing certificates are a common service for developers or organizations who want to be trusted by their clients. Attached to these certificates, the software can be signed for several operating systems like Windows, macOS, or Java applications, thus allowing users to download and install it without fear. It’s a simple verification; moderate identity checks to prove that a certain company or developer’s name exists.
For instance, a start-up that provides software publishing services and develops a desktop application for the Windows platform utilizes a standard code signing certificate to stamp the software. This makes it recognized by the antivirus programs; hence, there is an assurance to the purchasers that the software is genuine.
2. Extended Validation (EV) Code Signing Certificates
EV code signing certificates are all about taking trust and safety a step further. If you want to assure your users that your application is of the highest quality and is downloaded only from a legitimate source, an EV certificate is the right solution. Obtaining one such certificate includes a longer procedure that will have to undergo a few more stages, including some background investigations, which will establish whether there really is an organization and prove that you are the owner of the domain.
Establishing Trust: Visual and Software Verification with EV Trustworthiness
When people use software with EV signs, for example, a visual element such as a green bar in browsers enhances their trust in the software. Where companies have a large footprint, EV certificates support everyone who encounters such applications; the software is verified and authenticated, so they have no fear of using it.
However, browsers such as Google Chrome and Mozilla Firefox no longer show the green address bar for EV certificates. Instead, they have added the ‘organization’s name’ in the address bar for easy recognition by users so that they can know what software publisher it is and how trustworthy its authenticity is.
For example, a bank has developed secure software for transacting business and thus acquired an EV code signing certificate. This ensures the software is validated and trustworthy, and visual indicators, such as a green address bar, reassure users that the software is from a legitimate, verified source.
3. Domain Validation Certificates
Domain Validation certificates provide basic encryption to ensure secure communication between a user’s browser and the website server. To validate the certificate, the person or entity requesting the certificate who controls the domain must be verified. This verification process is done via emails, adding a DNS record, or uploading a file to the server.
These types of certificates do not expose any information about the individual or the organization involved on the website. Therefore, they are suitable for blogs or small businesses that do not require additional trust parameters. The automated nature of the process makes it cost-effective.
4. Organization Validation Certificates
These types of certificates verify both the domain ownership and the organization requesting the certificate. The Certification Authority (CA) conducts an intense validation process, checking the organization’s details, including registration details and physical addresses. Therefore, OV certificates provide enhanced trust compared to DV certificates.
The OV certificate guarantees the website’s legitimacy by displaying the organization’s details in the certificate itself, making it ideal for businesses and e-commerce platforms where user trust is to be built. The validation process generally takes a couple of days and is reasonably priced.
5. Timestamping Code Signing Certificates
Time stamping is an optional part of the code signing process. By adding a timestamp, users are shown as ‘valid as of signing,’ even if their certificate expires afterward. This is suitable for long-term validity, allowing users to understand that the software was legitimate and safe when signing.
A software developing firm includes a timestamp in the code signing process as an extra layer to ensure that the software remains valid even when the signing certificate has already expired. This permits users to verify that the software was signed at a specific time, even decades after the expiration of the certificate.
Extended Validation (EV) vs. Domain Validation (DV) vs. Organization Validation (OV) certificates
| Description | EV certificate | DV certificate | OV certificate |
| Validation | A detailed manual validation of the domain, organization, and entity is done. | Verifies that the entity controls the domain by various methods such as emails, DNS records, etc. | Verifies domain ownership and the legitimacy of the organization. |
| Purpose | Provides the highest level of trust for organizations dealing with sensitive data. | Basic encryption is provided to secure data in transit with no assurance of identity. | Provides encryption with a basic level of identity assurance to build user trust. |
| Cost | Most expensive due to the in-depth validation process and the highest level of assurance. | Least expensive. | Moderately priced and therefore balances cost and trust building. |
| Information displayed on the certificate | The organization’s name is displayed in some of the browsers in the address bar. | No information about the organization is displayed. | The organization’s name and address are viewable by the users as they are included in the certificate details. |
| Trust indicators | Displays a padlock in the browser’s address bar. To enhance trust, the organization’s name is directly mentioned in the browser’s address bar in some browsers. | Displays a padlock with no information about the organization. | Displays a padlock with the organization’s detailed information in the certificate. |
Advanced practices for enhancing Code Signing security
Strong practices and advanced tools are important to maintaining effective measures against attacks in code signing.
1. Highest security by EV certificates
Extended Validation (EV) Code Signing Certificates rank among the top measures for trust since they provide the highest level of assurance through strict identity verification. Keeping the certificates on secure hardware, be it HSMs or USB tokens, would ensure unauthorized individuals do not get access to private keys, hence significantly reducing impersonation risks.
2. Greater security by implementing Hardware Security Modules (HSMs)
Integrating HSMs into the code-signing process enhances the level of security. These modules store private keys that are used to sign the codes so that they can never be exposed in plaintext. Additionally, timestamps ensure that even when a certificate expires, the signature remains valid to testify to the authenticity of the software with time.
3. Implementation of RBAC and key rotation
By implementing Role-Based Access Control (RBAC), organizations can restrict access to code signing and other resources based on the user’s role in the organization. This ensures that only authorized users can gain access to the critical process of code signing, including audit trails, minimizing risks posed by internal threats.
In the code signing process, a pair of keys is used, i.e., a public and private key. A public key, which is used to verify the integrity of the software, is embedded in the code signing certificate. The other key is a private key whose role is to sign the software digitally. It must be stored securely to prevent unauthorized access by enforcing access controls and implementing key rotation.
Key rotation refers to the periodic replacement of the cryptographic key with a new one to mitigate the risk of key compromise. By rotating the keys, their validity periods are shortened, reducing the possibility of attacks. Additionally, automated schedules of keys make the code-signing process more reliable.
4. Practice secure code development
Secure code development is a preventive measure so that the malware is not signed along with the real software. It will detect and remove potential vulnerabilities through a thorough static and dynamic analysis before signature. This is achieved by integrating automated tools to proactively identify vulnerabilities during the development phase, including input validation, enforcing authorization and authentication practices, implementing secure coding standards, and performing continuous code reviews.
5. Centralized Governance
Centralized code-signing platforms such as CodeSign Secure further simplify governance while reducing the attack surface, through which organizations can manage their code-signing activities.
It regularly monitors and audits signed codes and detects and displays unauthorized or suspicious signatures, thereby giving an indication of compromise; it also acts as a proactive approach to risk management.
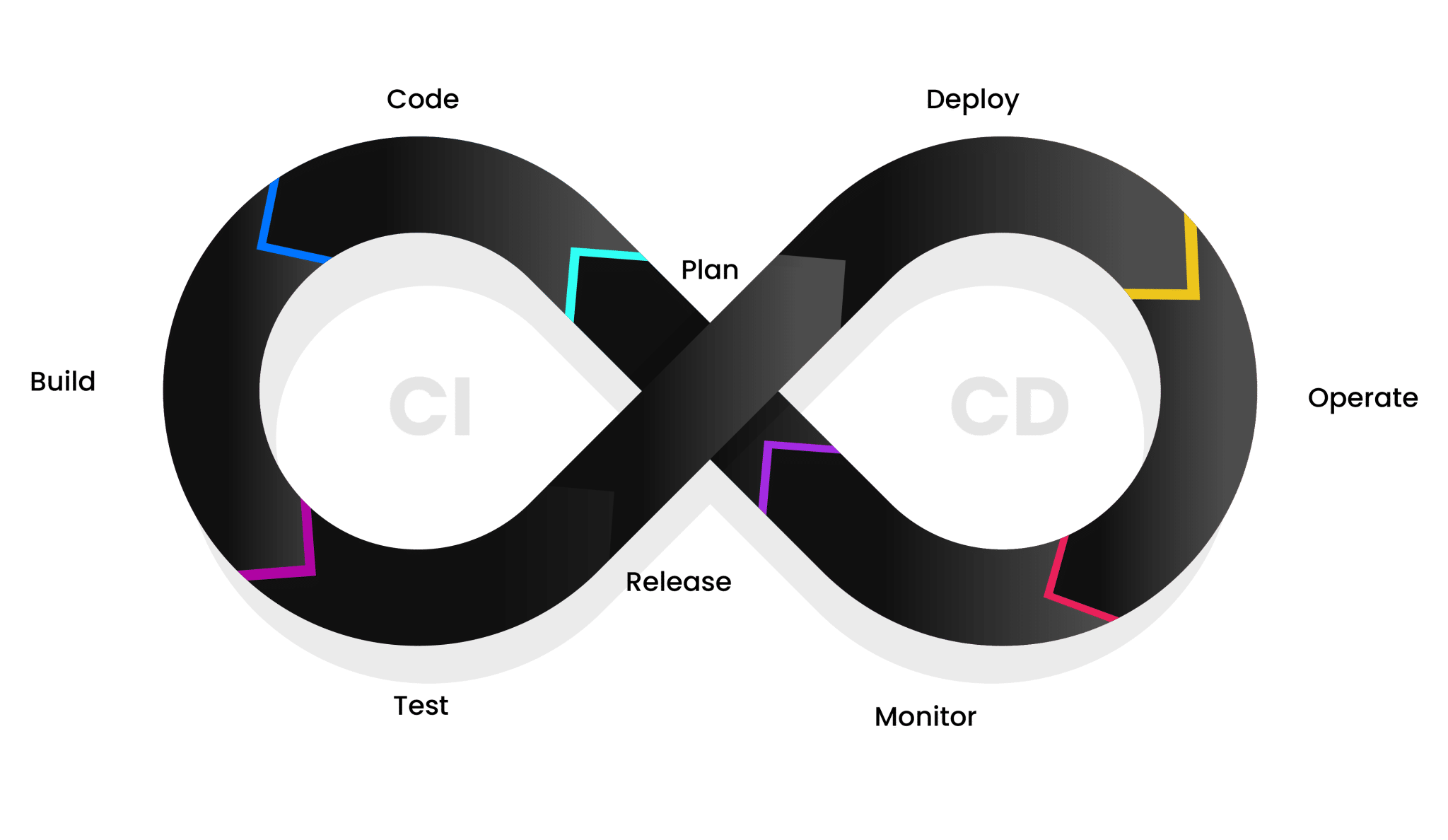
Code Signing in DevOps
DevOps is more than just a set of tools; it is a cultural shift that brings together development (Dev) and operations (Ops) teams. The goal is to bridge gaps between these traditionally separate groups, promoting better collaboration and communication. By doing so, DevOps aims to strengthen the entire software development lifecycle, making it faster, more efficient, and higher in quality.
At its core, DevOps is about automating as much of the process as possible and includes everything from code testing and deployment to managing infrastructure, all while ensuring smooth, continuous delivery of software. With this approach, organizations can release updates faster, improve the reliability of their software, and reduce the risk of errors or downtime, ultimately accelerating time to market. In short, DevOps is about building better software faster while ensuring that teams work together seamlessly to meet business needs. It’s a win for developers, operations teams, and customers alike.
When talking about Code Signing in DevOps, it is very important to ensure security and integrity during the whole software development life cycle (SDLC), which is a structured process that outlines the stages involved in the development, deployment, and maintenance of software. With this, the practice of code signing in DevOps has its advantages and solves some challenges:
1. Automated Signing Processes
Every time you release a new version of your software; it automatically goes through a signing process before reaching the public. When this process is integrated into your Continuous Integration/Continuous Deployment (CI/CD) pipelines, it ensures that each build and deployment is free from human error.
By automating code signing within your CI/CD workflow, you can deploy software quickly, knowing that every release is secure and has been verified. This guarantees that each update is both ready for launch and secured against any tampering, preserving the integrity of your software. With this approach, you can confidently push out updates to your clients without ever compromising security, making the entire release process faster, smoother, and more reliable.
2. Continuous Verification and Monitoring
Thorough checks of code signatures remain critical in DevOps because the software is regularly updated and deployed. Software updates need to be legitimate and secure, and this is where the signature check will help. Organizations should introduce tools for automatic checks for revoked certificates or compliance with security policies for even better security measures. Continuous monitoring will also help organizations detect vulnerabilities in real-time, which allows them to react to potential threats.
3. Audit and Compliance
Code signing is an aid when it comes to industry regulations. It gives an outline of when specific versions of the software are signed, including an audit trail. For example, code signing helps you adhere to some of the rules, such as the General Data Protection Regulation (GDPR), the National Institute of Standards and Technology (NIST), or the Payment Card Industry Data Security Standard (PCI DSS).
The signing keys should be stored in HSMs to ensure they are tamper-resistant in terms of protection. Additionally, when organizations comply with Federal Information Processing Standards (FIPS 140-3), strong encryption mechanisms and key management practices are reinforced. This level of transparency enables you to self-regulate and enhance the trust of your users, who might be apprehensive about using your software.
4. Security Integration
When code signing is integrated into DevOps practice, security becomes a built-in part of every step of the deployment process. Everyone on the team, from developers to operations, must incorporate the principle of ‘ this is safe’ into the workflow. With this, you are not just ensuring that the code is secure but also establishing confidence within the customers that the software they are using is reliable.
Vulnerabilities and Risks
The software delivery process has specific risks at each stage. The various vulnerabilities in the software supply chain process can be explored by dividing the process into two: Source Integrity and Build Integrity.
1. Source Integrity
The source integrity can be compromised through various attack vectors.
Harmful code can be injected during the initial commit phase by malicious developers or compromised accounts, emphasizing the need to review codes and enforce strict access controls.
Unauthorized access to source code repositories via credential theft can cause code theft and data loss.
If attackers gain access to the source code management (SCM) system, they can modify the code, including the introduction of vulnerabilities to create backdoors or altering the code’s functionality.
2. Build Integrity
Build integrity faces threats primarily within the CI/CD pipeline and distribution processes.
When targeted by attackers, the CI/CD environments can exploit platform vulnerabilities to inject malicious code, leading to the deployment of software without detection and impacting its integrity.
When attackers bypass the security checks and validations in the CI/CD pipeline, they can make malicious changes in the code, leading to compromised applications even before their production. A compromise of the package repository allows attackers to replace legitimate software packages with malicious versions, harming the entire supply chain.
Furthermore, malicious packages, when injected during distribution or utilized from untrusted external locations, can lead to malicious behavior in the deployed software.
By adhering to supply chain security frameworks, organizations can enforce security mechanisms to reduce vulnerabilities and mitigate risks.
An Overview of Supply Chain Security Frameworks
Prominent technology leaders like Google, Microsoft, IBM, Oracle, and the Cloud Native Computing Foundation (CNCF) introduced frameworks to deal with the rising threats to software supply chain security. The adoption of the frameworks will help organizations be resilient in their supply chain processes.
1. Google’s Supply Chain Levels for Software Artifacts (SLSA)
The application of SLSA is not limited to the public software supply chain; these levels, which were originally inspired by Google’s internal framework, can be applied to your own software development lifecycle for secure software delivery. Organizations advancing from SLSA Level 1, i.e., basic source integrity, to SLSA Level 4, i.e., tamper-proof build, can use various tools.
Additionally, this framework introduces various new tools and concepts for securing the software development lifecycle. Some of them are:
An artifact is a file generated during a build pipeline. Examples include container images and compiled libraries.
Provenance refers to the metadata about the building of an artifact, such as build processes, dependencies, etc.
A digest is a fixed-size value used to uniquely identify an artifact. A cryptographic hash function, such as the SHA-256 hash, generates this digest.
An Build integrity means verifying the output of the build pipeline via testaments.
2. Microsoft’s Supply Chain Security Framework
The Secure Supply Chain Consumption Framework (S2C2F) is based on three pillars- control of all artifact inputs, continuous process improvement, and scale. It is a consumption-based supply chain framework that uses a threat-based risk reduction approach. It aims to reduce the Mean Time to Remediate (MTTR) for addressing known vulnerabilities in Open-Source Software (OSS) by preventing the use of compromised and malicious OSS packages.
It combines processes and tools designed to protect developers from OSS supply chain threats. It also offers a maturity roadmap to secure the OSS consumption process.
3. CNCF’s Software Supply Chain Best Practices
The Cloud Native Computing Foundation (CNCF) highlights the importance of transparency and artifact verification. It states four key principles for supply chain security, which are as follows:
Digital trust: This refers to the “trustworthiness” step of the supply chain to ensure integrity and authenticity. This is achieved by cryptographic attestation, which involves the use of cryptographic methods such as digital signatures, hash functions, etc., to verify the identity or claim of software or hardware components and even data and verify the procedures followed during the supply chain process.
Automation: By automating code deployments and configuration management processes, human error risks are mitigated. By integrating CI/CD pipelines and security scanning tools, organizations can ensure that their security measures are consistent and aligned with defined standards and policies.
Clarity: This principle refers to the clear definition of the built environment to prevent complexity and limit the scope to enhance security by focussing on the location and procedure of code building and testing. By reducing the scope, the attack surface is also limited as the number of variables and configurations are minimized.
Mutual authentication: This emphasizes mutual authentication between all the entities operating in the supply chain environment is maintained so that they can verify each other’s identities. This is done to ensure that only legitimate parties can communicate in the supply chain, and this can be achieved by using mechanisms such as hardened authentication and regular key rotation.
The hardened authentication mechanism refers to the use of strong methods such as certificates, public key infrastructure (PKI), and two-factor authentication (2FA). To prevent the risk of key compromise, it is recommended that keys be rotated periodically.
Integrating Code Signing in CI/CD Pipelines
Adding code signing to the DevOps flow helps ensure that security becomes an integral part of the development process, leading to an increase in trust, compliance, and integrity. Code signing tasks are integrated into CI/CD pipelines for effective risk mitigation and sustained artifact authenticity while meeting regulatory compliance.
Now, let’s explore code signing integration within Continuous Integration and Continuous Delivery Tools.
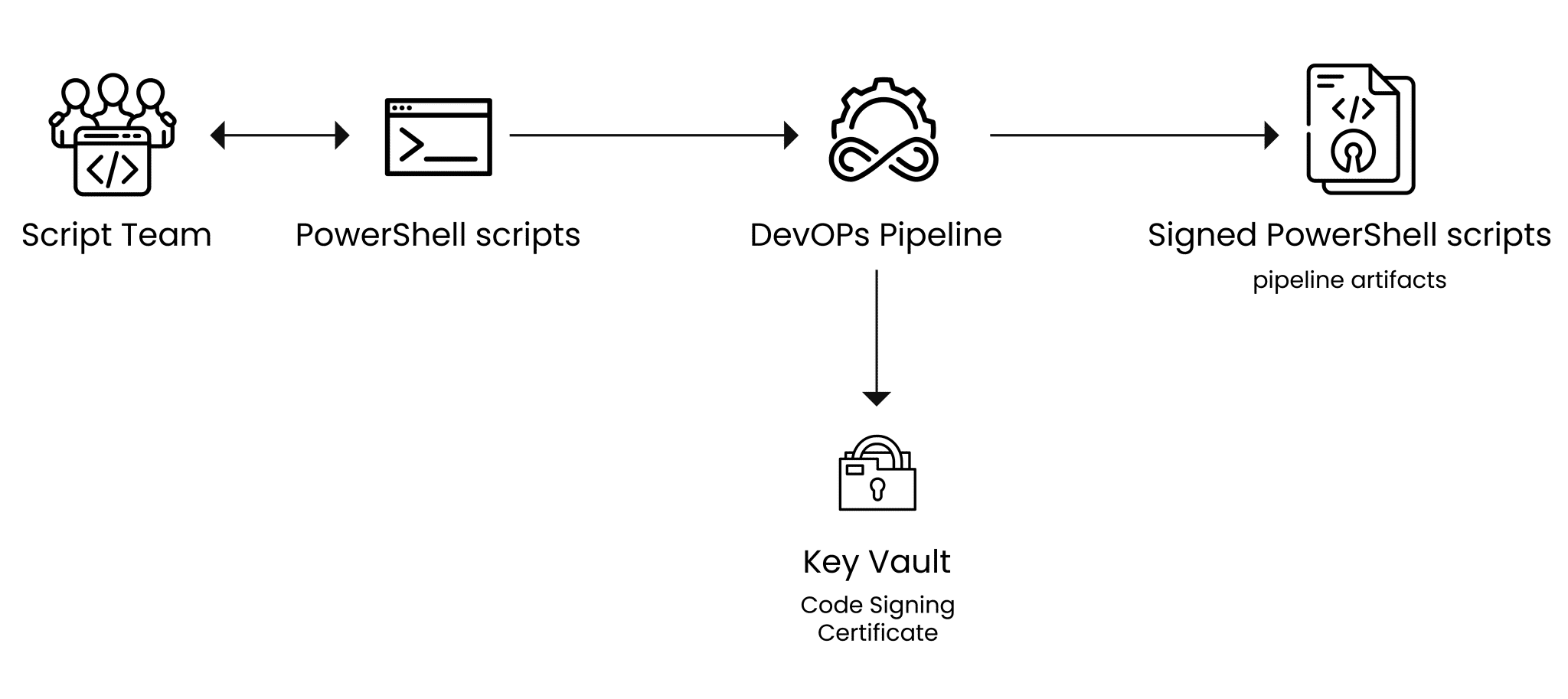
DevOps pipelines are dependent on automation tools such as Jenkins, GitHub Actions, and Azure DevOps. Integrating code-signing tasks into these tools makes security practices seamless without disturbing the development processes.
Thus, Azure DevOps enables any developer to add signing tasks directly into their pipelines, verifying and signing binaries and ensuring that artifacts are not tampered with during the release process. Through these capabilities, it becomes possible to see organizations safeguarding their applications and enhancing trust.
Developers can configure signing commands into a YAML pipeline template using tools and automatically sign all build artifacts before deploying them into production.
To learn more about the automation process, let’s dive more into it.
Scripting and APIs are important mechanisms in the process of automating code signing to generate maximum efficiency. PowerShell and Bash scripts can invoke tools such as SignTool, a command line utility for signing code and verifying signatures that are commonly used within Windows environments to dynamically sign binaries, ensuring that even complex signing workflows will be able to execute programmatically in the pipeline.
Code-signing solutions such as CodeSign Secure offer APIs compatible with the modern CI/CD workflow. Such APIs could be configured inside Azure DevOps pipelines to automate the signing of certain files programmatically, thus increasing scalability and consistency. Therefore, through the use of scripting and APIs, Azure DevOps can help teams automate repetitive tasks, eliminate manual errors, and secure deployments.
See the successful implementation of this integration in an organization here.
Code Signing Challenges
| Challenge | Description | Mitigation/Recommendation |
| Private Key Theft and Misuse | Attackers focus on the private keys saved within the build server or workstation and misuse them to sign the coded malicious programs. | Utilize HSMs for secure key storage, enforce Role Based Access Control (RBAC) and Identity and Access Management (IAM) in key policy, and adopt strong key management practices. |
| Lack of Visibility and Control over Code Signing Events | Private keys and certificates at the developer’s endpoints and CI/CD machines lead to risks of unauthorized access and mismanagement of keys or certificates, causing delays in the CI/CD processes. | Implement centralized key management systems and manage the lifecycle of code signing certificates by implementing Certificate Management Solutions such as CertSecure Manager. |
| Key sprawl | The excessive number of unmanaged cryptographic keys scattered around the organization’s environment may cause compliance violations, operational inefficiencies, and security risks, such as exploitation of untracked or outdated keys by the attacker. | Implement a code signing platform such as CodeSign Secure to centralize key storage and maintain a real-time inventory of the keys for monitoring. Furthermore, rotate the keys periodically and revoke unused or compromised keys. |
| Signing Breaches and Insider Threats | Compromised servers or malicious insiders may utilize legitimate certificates or keys to sign harmful software. | Enforce stricter access control policies, conduct audits, and use immutable build environments and signed containers. |
| Ensuring Compliance and Secure Key Lifecycle Management | Regulatory frameworks require a secure mechanism for key storage, logging, and management of the entire life cycle of usage for compliance. | Implement key management solutions that provide key discovery and analysis capabilities to gain visibility of their usage and facilitate efficient rotation and revocation. |
| Improperly configured signing keys and certificates. | Misconfigurations of keys and certificates compromise the overall security. These include weak key sizes, untrusted certificates, or missing expiration dates. | Strict policies should be enforced for key and certificate configurations, including regular audits. |
| Expired certificates | Expired certificates cause trust issues for the end-users as they cannot be verified. | Timestamping should be included to preserve signature validity for smooth workflows. |
How can Encryption Consulting Help?
Encryption Consulting’s CodeSign Secure is a secure and flexible solution for code signing on multiple operating systems, namely Windows, Linux, macOS, and Docker containers. CodeSign Secure protects digital devices from harmful software by digital code signing, protecting them from alterations while in transit, which forms a vital part of security in today’s digitalized world.
CodeSign Secure allows an organization to secure information while it is being transmitted. It also allows the code’s recipients to provide additional trust by knowing that the code is intact and original across all platforms.
Conclusion
Certificates for code signing are essential in trying to develop software that is secure and reliable. By selecting the right category of the certificate, knowing the difference between public trust and private trust, and integrating code signing into your DevOps pipeline, you are also improving the security and reliability of your software.
Complying with regulations is one thing, but instilling confidence in your users and safeguarding their applications against all forms of tampering is another. All in all, code signing enhances the level of security of all programs and software created for the users.
- Types of code signing certificates
- Extended Validation (EV) vs. Domain Validation (DV) vs. Organization Validation (OV) certificates
- Advanced practices for enhancing Code Signing security
- Code Signing in DevOps
- Vulnerabilities and Risks
- An Overview of Supply Chain Security Frameworks
- Integrating Code Signing in CI/CD Pipelines
- Code Signing Challenges
- How can Encryption Consulting Help?
- Conclusion

