Education Center, Public Key Infrastructure (PKI)
What is Machine Identity Management?

Education Center, Public Key Infrastructure (PKI)

In a secure network environment, machine identity management refers to the systems and processes for managing credential authentication required for machines to access resources and other machines. In the context of machine identity management, a machine encompasses a broad range of entities that necessitate a unique identity for secure connections and communication. It includes not only tangible hardware components but can also include pieces of code and application programming interfaces (APIs). Every machine in a modern enterprise digital environment, from computers and mobile devices to servers and network infrastructure, has a machine identity.
An ever-increasing number of machine interactions inherent in digitalized processes pose a significant risk to business survival without adequate authentication management. With the help of cryptographic keys and digital certificates, these systems can determine whether the interaction is trustworthy or not.
This machine identification is a digital credential or “fingerprint” used to establish trust, authenticate other machines, and encrypt communication. Regardless of the number of identities involved or the complexity of the enterprise network, it’s essential that the whole machine identity lifecycles are effectively managed, ensuring that access is only allowed to legitimate users or machines.
Machine identities must be validated to implement a Zero Trust security model based on the concept of “Trust No, Always Verify.” Public Key Infrastructure (PKI) certificates and cryptographic key pairs can be used to strengthen verification and secure connections between entities outside of a firewalled network architecture.
Generally, the user identity is represented by username and password. When a user login into an application. They enter username and password, the application checks the username and password in the database, and if the credential matches, the user is authenticated and can access the application.
Similarly, machines need to be authenticated for secure communication with other machines. A machine identification is much more than a digital ID number or a simple identifier like a serial number or part number. It is a collection of authenticated credentials that confirm that a system or user can access online services or a network. A machine cannot enter a username and password. Instead, they use a set of credentials that are better suited to highly automated and linked settings. Machines have digital certificates and keys to establish their identity.
To secure network communications, every internet protocol (HTTPS, SSH, FTP, and so on) checks and authenticates machine identities.
To understand the working of machine identity, Let’s see the common machine-to-machine communication between server and client.
When a client tries to establish a connection with a web server, the server provides its digital certificate on receiving the connection request. After that, the client verifies the digital certificate (SSL/TLS certificates) and verifies the server’s identity. When dealing with sensitive applications, the server may also request that the client authenticate its identity by sharing its certificate. After authentication, both exchanges keys for encryption and hashing, and a secured session gets established.
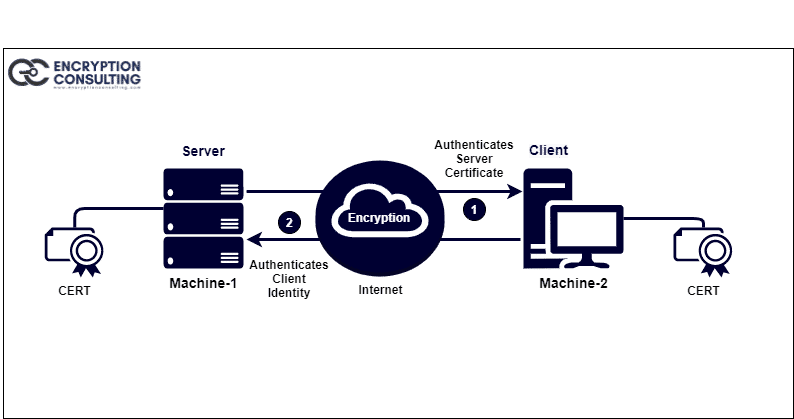
As the machines cannot enter a username and password, they use credentials better suited to highly automated and linked settings. Instead, digital certificates and keys are used to establish machine identities. On the other hand, certificates and key types vary depending on the machine, communication protocol, and usage.
Following are some commonly used certificates and keys that make up machine identity:
SSH keys and Certificates
Users, usually system administrators, use SSH keys to secure privileged access to critical systems. Because SSH keys are used to authorize access to important IT systems, the SSH protocol is more secure than TLS/SSL. While it is not common practice to use SSH certificates for authentication, it is recommended as it eliminates the manual, insecure process of key approval and distribution.
Code Signing Certificates
Code-Signing Certificates ensure that scripts, executables, and software builds are genuine and preventing them from tampering. It builds trust in users.
Cryptographic Keys
Cryptographic keys, particularly Symmetric keys, are used to protect data at rest, data in transit, and encrypting credit card and other PII (Personal Identifiable Information) data. However, Symmetric keys are less secure but faster and more efficient than public-key cryptography.
X.509 Certificates
X.509 Certificates are the most extensively used machine identification certificates and the backbone of the Public Key Infrastructure (PKI). Server-client authentication over the HTTPS protocol (based on the TLS/SSL protocol) as well as digitally signing offline applications use these certificates for authentication.
Machine identity management is a broad term that incorporates various technologies that are currently primarily isolated, like SSH key management, X.509 Certificate Management, etc.
To protect Machine Identity
Suppose someone gets your identity in any way. They can access your
personal information like your credit card details, social media accounts, etc. They can make a large transaction
from your account and impersonate their identity. A similar thing can happen if someone stole machine identities,
and they can do all those things on a large scale as the machine can have records of thousands of
individuals.
The attacker gains access to the deep network when the identity of a crucial network device, such
as
a web server or a load balancer, is compromised. Then they can gain administrator privileges and inject malicious
code into critical devices, causing them to malfunction or even shut down systems. This can result in severe
damage
to both customers and users of the organization.
Keep up with the explosive growth of machines
The number of machines in the world is outpacing the number of people who use them. The sheer number of machine identities that must be secured, including mobile, cloud, and IoT devices, makes keeping machine identities secure significantly more difficult.
The proliferation of secure cloud-based machines
The rapid evolution of cloud services requires a rapid assessment of machine trustworthiness, including cloud workloads, virtual machines, containers, and microservices. Because of the fluid nature of their interactions, their identities may be compromised.
Protect the identity of connected devices
There are a number of devices whose identities are connected to the Internet, like robots, medical devices, sensors, etc. Many of these devices use encrypted channels controlled by machine identities to transmit and store important data.
Following are some reasons that cause machine identity compromise:
CA Compromise
Certificate Authorities (CAs) are compromised when attackers steal their private key, used to sign certificates issued to companies. Attackers can use these stolen private keys to sign certificates for malicious applications and fool browsers into believing they are trustworthy. These certificates, known as rogue certificates, are widely used by attackers to spread phishing and man-in-the-middle attacks. And this rouge intermediate root CA can misuse their authority and sign certificates of fraudulent servers and applications.
Certificate Outages
Certificates issued have a validity period associated with them. If a certificate is not renewed before it expires, it can result in a certificate-related outage on the system it supports. Until a new certificate is installed, the unplanned outage and associated downtime will persist. Certificate-related outages are difficult to identify without knowing exactly where a certificate is installed and who controls that system.
Operational Inefficiencies
Each digital certificate that serves as a machine identification takes some time per year for the organizations to manage. With thousands of machine identities, the overhead can quickly increase. And the administration of these identities can be more complicated when the administrator unfamiliar with certificates or trust stores. And the time required will be increase quickly if the machine identity operations are not running smoothly, especially when there is a breach or outage.
Unknown Revoked Certificates
Sometimes, digital certificates get revoked before their validity period because of their private key compromised or the application to which certificate is associated no longer operational. Sometimes certificates may not be revoked by Certificate Authority (CA) or Certification Revocation List (CRL) not updated on time that leads to recognize a revoked certificate as valid. For example, attackers can use an orphan certificate for phishing attacks if an application has been taken down, but its certificate has not been revoked on time.
Following are some challenges that make Machine Identity Management critical:
Visibility
When there is a large number of certificates and keys in an organization, it is difficult to track them. Many organizations even do not know how many certificates and keys they have, their validity period, and the policy they comply with.
Governance
The next problem is a lack of ownership and control. In organizations, SSH keys and SSL/TLS certificates are used by various teams. But there is no consistent policy of how they are issued, who can access them, rotation of keys, renewal of the certificates, etc.
Protection
Digital certificates to the machine identities must be provided by a trusted Certificate Authority (CA). Private keys must be stored in Hardware Security Module (HSM) and protected from compromise. Machine identities cannot be trusted unless these safeguards are in place.
Automation
Manual management of certificate lifecycle is not just time-consuming. It is error-prone and highly inefficient also. Manually issuing, revoking, renewing, and auditing certificates can lead to downtimes and outages.
Centralize Management
There should be a centralized machine identity that helps streamline policy implementation across various devices. Certificates can also be grouped based on multiple parameters like expiry date, criticality, etc., and implement group policy, making it easy to manage them. There should be proper policy management that prevents unauthorized access and allows machine identities to do their job securely.
Automation
Machine Identity Management process can be automated that helps in defining an action for a single machine identity as well as for an entire group. All the actions can be defined in advance and can be triggered based on specific conditions. Enrollment, provisioning, renewal, revocation of certificates, etc., can be automated, which helps maintain machine identities up to date and effectively eliminating outages. In short, the entire machine identity lifecycle should be automated, including certificate and key lifecycle management that prevent errors that can be done in manual actions.
Storage
All the machine identities like SSH keys, digital certificates must be stored in a centralized, secure environment. Identities can be stored in Hardware Security Module (HSM), FIPS 140-2 Level 3 compliant. HSM keeps the certificate and keys secured even if the user network gets compromised.
SSH key rotation
Organizations must rotate their SSH keys after a certain period that prevents using the same SSH keys for a long time by generating new keys. Key rotation helps strengthen SSH keys security and protects against risks like key sprawl. The key rotation process should be automatic rather than manual so that keys should be rotated regularly.
Enforce strong security policies
Organizations must set up and enforce strong security policies to keep their machine identities secure and ensures that every machine identity complies with appropriate government regulations. Implementing strong security policies allows monitoring every aspect of machine identity.
Machine Identities Auditing
There should be auditing of machine identities at regular intervals, which helps in finding vulnerabilities like expiring certificates, weak passwords, etc., and prevent outages. Auditing can also be automated using third-party tools. Regular auditing helps an organization to improve its management strategies.
The machine identity lifecycle encompasses various components, each playing a crucial role in the journey of a machine identity from creation to retirement. Here are the key components of the machine identity lifecycle:
Generation/Creation
The initial phase involves the generation or creation of a machine identity, such as digital certificates or API keys. Organizations obtain digital certificates from a Certificate Authority (CA).
Inventory
Once certificates are issued, it is crucial to document key details such as validity period, type, position in the chain, and network location. This information becomes essential as certificates approach their expiration dates.
Distribution/Deployment
The process of deploying the machine identity to the intended systems, devices, or applications to enable secure communication.
Monitoring/Management
Ongoing oversight and management activities to ensure the proper functioning, security, and compliance of machine identities.
Renewal/Rotation
The process of updating or renewing the machine identity to maintain security and prevent expiration.
Revocation/Invalidation
The intentional termination of a machine identity before its expiration date, often due to security concerns or misuse.
In today’s digital environments, device management is essential to ensure secure communications and prevent identity theft. Encryption Consulting provides comprehensive solutions to address the challenges of device identity management, including visibility, governance, security and automation.