What is session hijacking?


A lot can happen in-between login and logout. Two different machines communicate on a network and share a few common communication parameters. This is done by sending data packets between these two machines; this process is called a three-way handshake. Some attackers look for sessions to which they can gain access and exploit users’ data from those sessions. Users must ensure that they login into a secure environment and use web application firewalls to detect anomalies in the traffic. These are primary measures. To fix more serious issues, we need to know about Session Hijacking.
Session hijacking (also known as Cookie hijacking or Cookie side-jacking) is one of the most sophisticated man-in-the-middle attacks which gives the attacker access to the victim’s web sessions. It also refers to the attacker’s ability to take control over a portion of the user’s session. This process would provide them access to sensitive data such as personal and financial data (PII and PCI) that might be protected using a passkey or passphrase.
Session Hijacking allows an attacker to avoid all kinds of protection from passwords by authenticating the existing connection. Suppose an attacker is sniffing User A’s network; this attacker will know what sessions are open in the user’s network management system. This process happens if the attacker knows the address, suppose 14.0.0.1, and the user’s key system 14.0.0.100. Then, this attacker will send packets to the Network Management System (NMS) at this address, 14.0.0.1. This process causes the user to drop their connection and continue sending packets at 14.0.0.100 with the spoofed address 14.0.0.1. This whole scenario means that User A’s session has been hijacked.
Session hijack is generally waged against users that are members of large networks which contain a large number of open sessions. Network protocols like FTP, Telnet, and login are attackers’ favorite because these have the session-oriented nature of their connections and their length of communication sessions.
Hypertext Transfer Protocol (HTTP) is a stateless protocol with session cookies attached to its header. When a user logs in to a website, the concept of HTTP comes. This way server identifies the user’s browser.
Recently, session hijacking has been overshadowed by spyware, rootkits, bot networks, and denial of service attacks, but it remains a commonly used cyber-attack.
There are various exploits and tools that attackers may use to gain entry. In 2017, a security researcher found an issue in GitLab. In which a user’s session token was directly in the URL. Upon further inspection, it was found that GitLab’s session token never expired, which means an attacker could use it without any expiration.
Another example is CookieCadger, an open-source tool that can find leaking information from websites and web applications. It can monitor unsecured Wi-Fi and wired ethernet to see the session cookies
Similarly, FireSheep was a browser extension released by Firefox in 2010. This extension opened a vulnerability for people using the browser on public networks.
The risks resulting from session hijacking can’t be eliminated by various software patches, multi-factor authentication, or complex passwords. This attack exploits all three sides of the CIA triad, where the CIA triad is a representative model of security concepts – Confidentiality, Integrity, and Availability. When an attack is successful, the attacker now gains the ability to read and modify data, which violates the CIA model.
There are various types of Session Hijacking methods and knowing how they work helps identify them and be aware of them.
The most common are –
The hijacker finds weak spots in the target server and takes advantage by inserting scripts into the web page. This page then loads this code, thinking everything looks legitimate on the client side. Once this code is loaded, the web browser reveals the user’s session ID (session key) to the hijacker
This, also known as Session Sniffing, is a more active type of attack. But for this type, the hijacker needs to have access to the user’s network traffic. So, to achieve that, the hijacker or attacker uses packet sniffing techniques like Kismet or Wireshark to monitor and steal session cookies after searching the user’s session.
In this type of attack, attackers create a session ID, and the user uses this session ID after being tricked. The session ID can be set via URLs or forms through emails, leading to the attacker’s website. Once the user logs in, the hijacker gains access to the user’s data.
This works mainly if the website or the target user uses predictable session Ids, where the attacker has to guess them and perform the attack. Another scenario is if the hijacker gains access to a list of session IDs from a website with weak security measures.
This is also known as Man in the Middle Attacks or Malware. Here, the attacker infects the user’s computer with malware and viruses, allowing them to hijack a session. It is very tough to detect any issues with the web application or the site’s security in this type of attack.
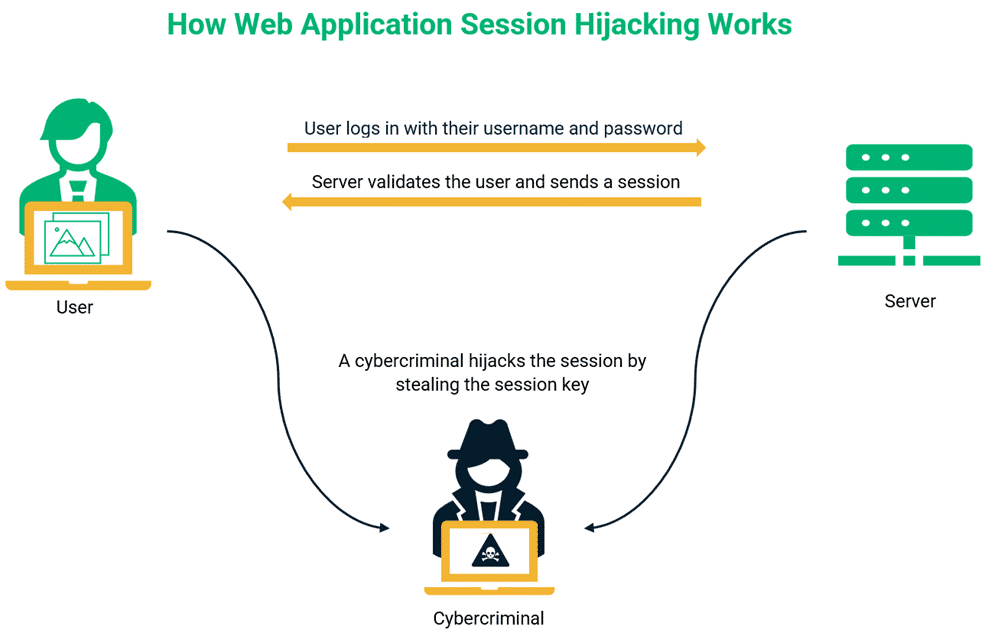
There are several techniques or ways for hijacking a session like – session sniffing, cross-site scripting, predictable session token ID, etc. But the basic scenario remains the same –
It happens when a hijacker gains access to a user’s session without authorization by stealing their session cookie and confusing the browser into believing that the attacker is an actual user.
This step happens in two major important steps, like when the user may open a web application or site, which installs a temporary cookie, also known as a Session cookie. These session cookies help keep the user authenticated and track their activity. But these will remain in the browser until the user’s session automatically gets over or they manually log out. These hijackers may cyber-attack using various methods to steal session IDs (like mentioned above). So, the basic flow is to locate the session ID from the cookie and use the information within it to hijack the original user’s session. After gaining the session, these hijackers can reap the stolen session ID benefits. Depending on their motive, they can use the continuing session and extract personal data or perform illegal activities
Session Hijacking is one of the topmost cyber-security threats, but there are several ways in which a user can protect themselves. Some steps are:
Users should never use public Wi-Fi, mainly when dealing with important online transactions like – banking, shopping, payment, etc. An attacker nearby can use packet sniffing to pick up a user’s session cookies.
The longer and more random session cookies are, get tougher to guess or predict. The best way is to use a web framework to generate and manage a system ourselves.
The best protection method is to change the session key immediately after the login process is completed. This way, even after knowing the original key, the attacker will have no idea which key the user will use for the test session.
These compare site traffic to the database of many known attack signatures. If a match is found, these block that traffic and alert the owner. These are expensive but effective approaches.
This is to ensure SSL or TLS types of encryption on all session traffics. This step helps stop the attacker from intercepting the session ID, even after observing their network traffic. An even better approach is using HSTS (HTTP Strict Transport Security).
One such cybersecurity tool is DDoS Protection software and Deception Technology for carefully logging in and out of every session
There’s always a possibility of falling victim to session hijacking, but following the above steps and being cautious of the symptoms can help. There is much ongoing research regarding solving this vulnerability, but the best prevention till now is – for users being aware of getting their session ID stolen.