SSL (Secure Socket Layer) and TLS (Transport Layer Security) are like bodyguards for websites, making sure that when information is sent over the internet, it stays safe and can’t be messed with by sneaky people. They use a special code to lock up the data and keep it private.
Think of TLS as the upgraded version of SSL. It’s like when you get a new and improved phone with better features. TLS is on its third version, called TLS 1.3, and it’s more secure than SSL, which is kind of like the older version.
Even though SSL is outdated and not used in modern systems anymore, people still use the term “SSL” when talking about both protocols. For example, they might say “SSL certificate.”
When you see “HTTPS” in your web browser’s address bar, it means that the website is using TLS to protect your connection. It’s like a green light that tells you it’s safe.
TLS doesn’t just protect websites; it also keeps things like emails and calls safe from prying eyes. It’s like a superhero for your online conversations!
When SSL version 3.0 was updated, instead of it being called SSLv4.0 it was renamed to be TLSv1.0.
How does it work?
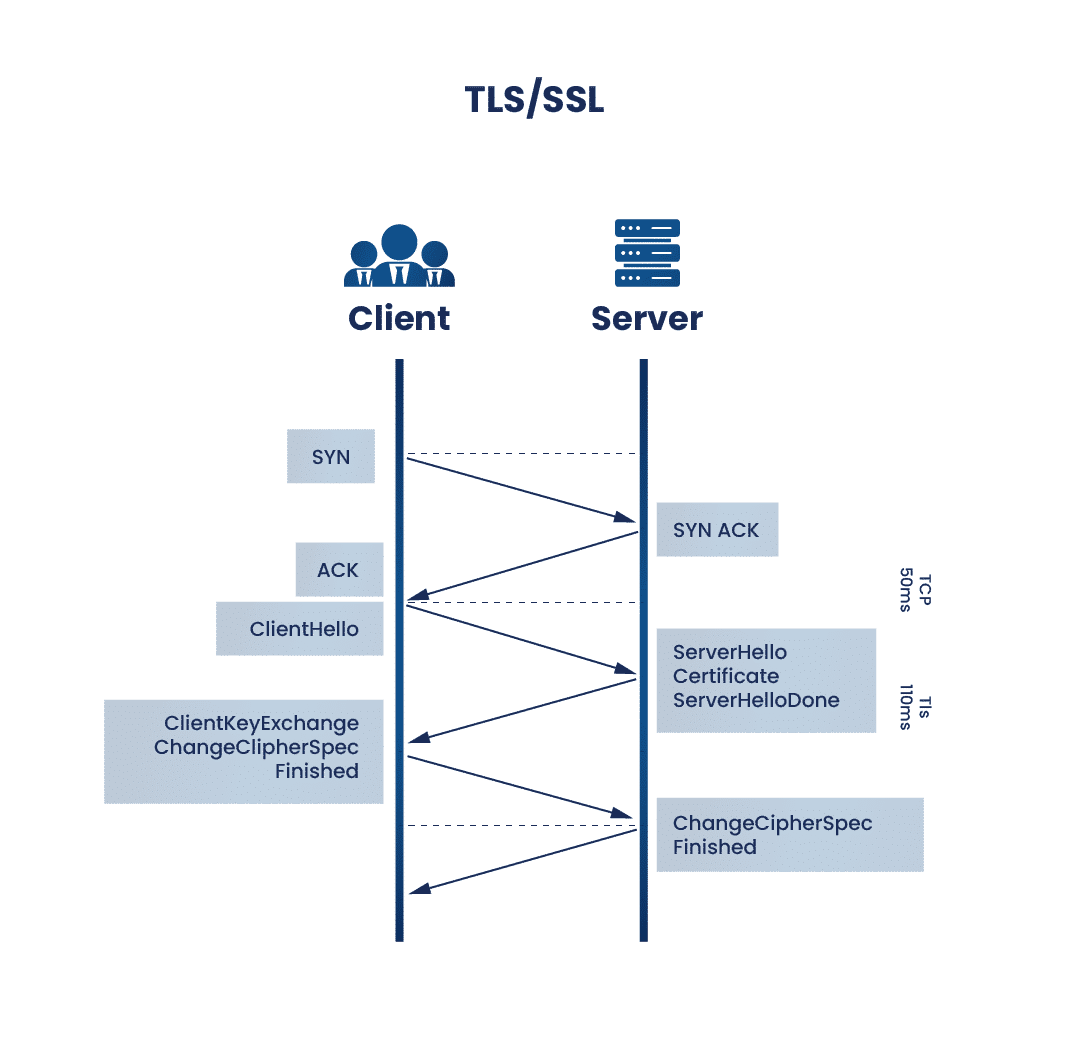
When two systems employing TLS attempt to establish a connection, they go through a process known as the TLS handshake. During this handshake, both parties verify each other’s support for TLS and agree on parameters like TLS version, encryption algorithm, and cipher suite. Once the TLS handshake is successful, a secure line is established for data exchange.
Encryption and decryption in TLS rely on keys, where public keys encrypt information, and private keys decrypt it. This asymmetric cryptography involves two different keys for security.
The TLS handshake typically follows these steps, considering a scenario where a client (browser) connects to a server hosting a website:
- The client requests the server to open a secure line, and the server responds by presenting a list of compatible TLS versions and cipher suites. Once they agree on common parameters, the handshake begins.
- The server sends its public key, attached to a digital certificate, to the client. The client verifies the certificate to ensure the server’s legitimacy before proceeding.
- Using the server’s public key and its private key, the client encrypts a ‘session key.’ This session key is used by both parties for encrypting and decrypting information during the session and becomes invalid upon connection termination.
- Both parties test the connection by sending encrypted messages to each other. If the other party can successfully decrypt these messages using the session key, the connection is secured.
Why is it necessary?
Web connections can exist without TLS to safeguard them. However, in the absence of a security protocol, communication becomes vulnerable to external access. For instance, if a browser connects to an online store’s website where users need to enter credentials, without TLS, those credentials could be easily intercepted by a third party.
TLS fundamentally aims to provide end-to-end encryption for all transmitted data, employing cryptography to ensure that only the involved parties can decipher the information. Presently, virtually every service requires secure connections through TLS. Major browsers enforce this by not allowing users to access websites lacking a valid TLS connection.
Conclusion
In conclusion, SSL (Secure Socket Layer) and its successor, TLS (Transport Layer Security), serve as vital guardians for websites, ensuring the secure transmission of information over the internet. TLS, being the upgraded version of SSL, employs advanced features to enhance security, with TLS 1.3 representing its latest iteration. Despite SSL being outdated, the term is still colloquially used, as seen in phrases like “SSL certificate.” The TLS handshake, a crucial part of establishing a secure connection, involves a meticulous process of verifying compatibility and exchanging cryptographic keys. In today’s digital landscape, TLS has become indispensable, with major browsers insisting on its use to ensure secure connections, reflecting its pivotal role in safeguarding online interactions.
Encryption Consulting provides comprehensive expertise and customized solutions. With a team of top experts, Encryption Consulting provides Encryption Advisory Services including Assessment, Audit Service, Strategy and Implementation Planning, ensuring that clients receive tailored answers that match their unique security desires.

