Fixing “Denied by Policy Module” Error


This blog post covers how to resolve a common misconfiguration of a Template that causes a Denied by Policy Module error when issuing certificates. The error may range from
This blog will cover two phases: Problem Diagnosis and Problem Resolution.
Perform the following steps to troubleshoot the error; ensure you have enterprise admin rights for these steps.
Run the certutil command to get the config value.
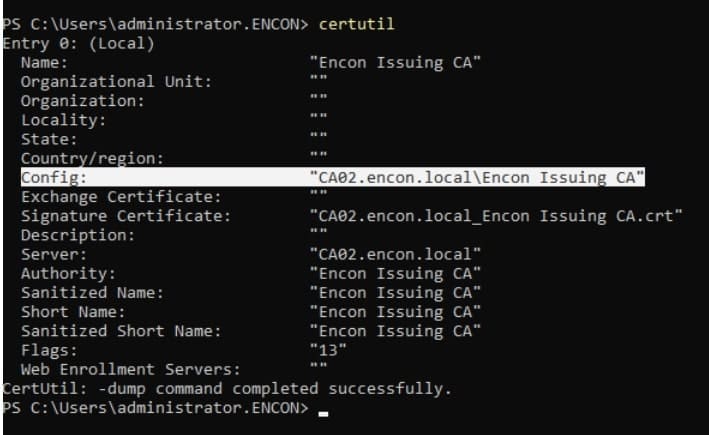
Replace the config value obtained in the following command
certutil -config “{config}” -cainfo templates
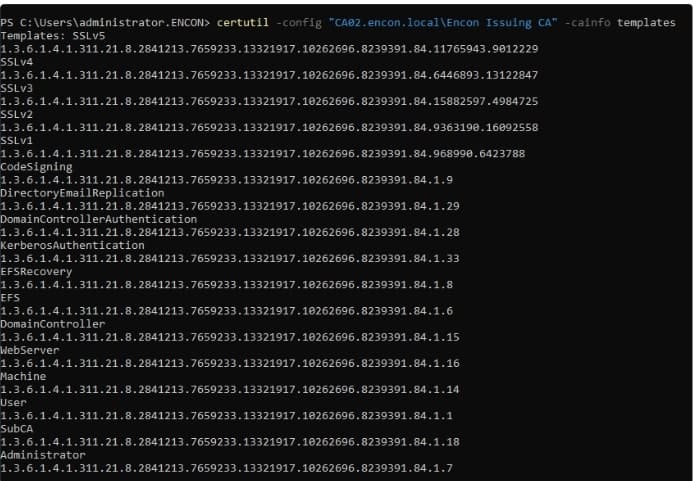
This will present you with all the templates available on this Certification Authority. This data is pulled from the domain controller, and so is the data that is displayed to the users.
Note: If you don’t see your template, navigate to “certsrv.msc” and issue a new template.
To check the permissions on the concerned template, run the following command-
certutil -v -template {Template Name}
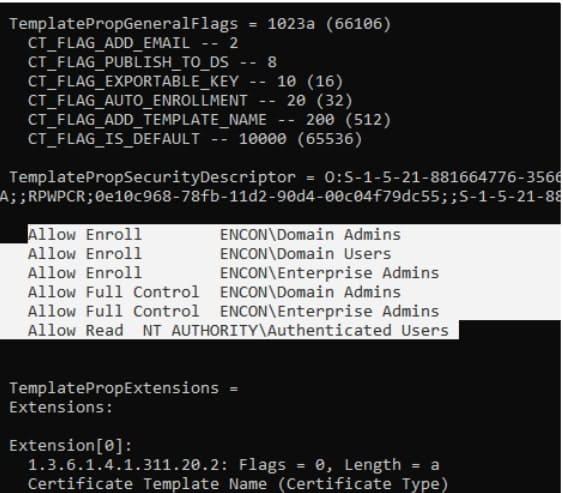
If you can’t find the concerned user here with the required enroll permissions, the concerned user needs to be granted enroll permission by following the steps in the Resolution part.
Note: If you just made the change, please wait a couple of minutes for the domain controllers to sync.
Step-by-step process to resolve the issue found in the diagnosis phase, please follow the steps:
Open Certificate Authority and right-click on Certificate Templates, and choose Manage.
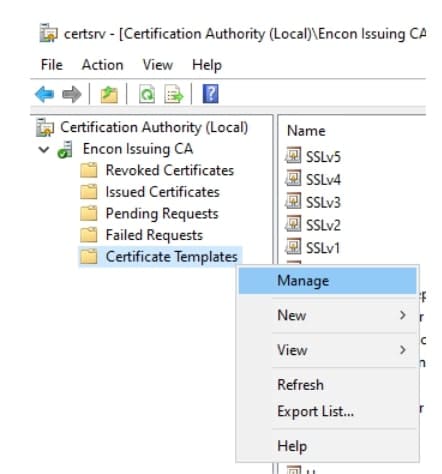
Find the concerned Certificate Template, right-click, and choose Properties
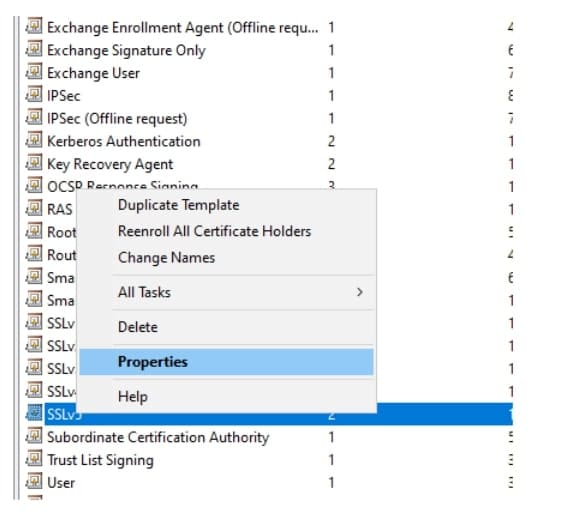
Navigate to the Security tab, and click Add
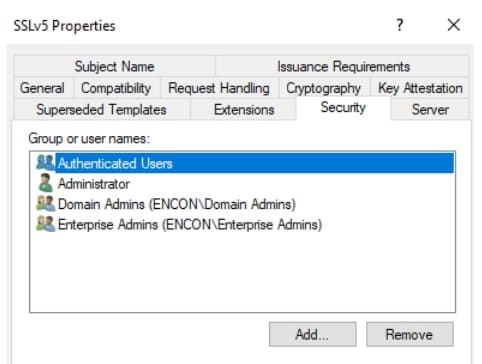
Provide appropriate permissions to the user. Click Apply and exit.
This should add the user with appropriate permissions. Run diagnostic steps again to ensure no errors are encountered.
“Denied by Policy” errors often stem from elusive misconfigurations in system settings and policies. To identify these problems, one needs a thorough grasp of authorization, authentication, and access control systems. The difficulty comes from the intricacy of dynamic rules and procedures and the possibility of human error. Maintaining a good security posture requires regular audits, automated configuration tools, and thorough administrator training to mitigate such failures.
At Encryption Consulting, we offer PKI as a Service (PKIaaS) to prevent these issues before they escalate. Our service includes expert guidance on certificate management, template configuration, and policy enforcement, ensuring your environment is always in compliance with best practices. With real-time support and proactive monitoring, our Encryption Advisory Services are designed to help you avoid misconfigurations like the “Denied by Policy” error and ensure smooth certificate issuance.
Contact us at [email protected]today to explore how our tailored encryption solutions can keep your organization secure from certificate-related issues and misconfigurations.