In the world of hardware and software, compatibility is key. Ensuring that your hardware drivers work seamlessly with the Windows operating system is critical in providing a positive user experience. This is where HLK (Windows Hardware Lab Kit) signing comes into play. In this blog post, we’ll explore the ins and outs of HLK signing, its significance, and why it’s vital for hardware manufacturers and driver developers.
In the ever-evolving landscape of hardware and software, ensuring that your drivers and hardware components are seamlessly compatible with the Windows operating system is paramount. That’s where the HLK (Windows Hardware Lab Kit) signing, coupled with the expertise of Encryption Consulting LLC, comes into play. In this post, we’ll discuss the importance of the HLK signature and how Encryption Consulting LLC can be a reliable ally on this path.
Understanding the Windows Hardware Lab Kit (HLK)
The HLK is a comprehensive suite of tools, tests, and documentation provided by Microsoft. It’s designed to validate the compatibility and reliability of hardware and drivers with the Windows OS. Think of it as the gatekeeper that ensures only quality, compatible drivers and hardware components make it into the Windows ecosystem. Microsoft’s Windows OS is used by millions of users worldwide, each with a unique combination of hardware. To ensure a consistent and stable user experience, Microsoft uses the HLK to test and validate third-party hardware and drivers rigorously.
Encryption Consulting LLC harnesses the power of HLK to ensure that your hardware components meet Microsoft’s stringent standards.
Why HLK Signing Matters?
-
Ensuring Driver and Hardware Compatibility
HLK signing guarantees that your hardware and drivers play nicely with Windows. It’s a stamp of approval that says, “This hardware or driver has been thoroughly tested and meets Microsoft’s compatibility standards.”
-
Enhancing System Stability
Unreliable hardware or poorly designed drivers can lead to system crashes and frustrating user experiences. HLK signing helps prevent these issues by ensuring that only high-quality, tested components are integrated into the Windows environment.
-
Meeting Microsoft’s Standards
Microsoft has strict standards for hardware compatibility. HLK signing is your ticket to demonstrate that your products meet these standards and can be trusted by Windows users.
When you collaborate with Encryption Consulting LLC for HLK signing, you ensure that your drivers and hardware are dependable and won’t lead to issues on Windows systems. This reliability builds trust and confidence among your customers while mitigating potential challenges.
The Process of HLK Code Signing with Encryption Consulting LLC
What is Code Signing?
Code signing involves digitally signing your driver or hardware component to confirm that it has passed the necessary compatibility tests. It’s marking your product as safe, reliable, and compatible with Windows.
Why is it Necessary for HLK-Certified Drivers?
Code signing is an essential component of HLK certification. Without a valid digital signature, your driver will not be installable on Windows systems, which could severely limit its usability.
Why choose Encryption Consulting’s CodeSign Secure for HLK Signing?
We have three main benefits which support and help promote our CodeSign Secure as an ideal fit for HLK Signing. Those are:
By integrating these advanced security measures and technologies into our code-signing process, Encryption Consulting LLC ensures that your HLK certification is reliable and fortified against potential threats, meeting the highest industry standards.
-
Fortified Security – FIPS 140-2 Level 3 HSM Compliance
Encryption Consulting LLC has taken security to the next level in response to CA/Browser Forum’s June 1, 2023, requirement. Our private keys for CodeSigning certificates are stored, generated, and used within a Hardware Security Module (HSM) that complies with FIPS 140-2 Level 3 standards and never leaves the HSM in any situation. This rigorous compliance ensures the highest level of security for your code signing process, meeting industry standards and safeguarding your digital signatures.
-
Client-Side Hashing – Unveiling the Benefits with CodeSign Secure
Our CodeSign Secure, utilised in both the utility tool and KSP methods, employs client-side hashing for your code signing needs, and it brings several benefits to the table:
-
Enhanced Efficiency
Client-side hashing reduces the load on your infrastructure, making the code-signing process more efficient. It minimises the need to transfer large files to a remote server for hashing, saving time and resources.
-
Privacy and Control
You maintain complete control over your data with client-side hashing. Your sensitive code and files remain within your network, reducing the risk of data exposure or interception during transmission.
-
Improved Compliance
Client-side hashing ensures that your code signing process complies with industry regulations and standards. It provides a transparent and auditable process, making demonstrating compliance to stakeholders, auditors, or regulatory authorities easier. This can be particularly crucial for industries with stringent compliance requirements.
-
-
Proxy-Based Access to HSM for Enhanced Security
Proxy-based access to the keys stored in a Hardware Security Module (HSM) is one of the essential security elements provided by Encryption Consulting LLC. This approach significantly enhances security by safeguarding your private keys from unauthorised access and potential breaches. Our CodeSign Secure utilises proxy-based access to interact with the private keys stored in the HSM, ensuring the integrity and security of your code-signing process. This approach is crucial in establishing trust, verifying digital signatures, and securing the communication between your components and the HSM.
Steps to Digitally Sign Your Code
Encryption Consulting LLC’s expertise in this domain ensures your code signing process is seamless, secure, and compliant with Microsoft’s standards. Digitally signing your HLK package (.hlkx) involves a series of steps to create a secure and verifiable digital signature. These steps ensure that the code meets Microsoft’s standards. We understand that flexibility is key, so we offer two methods for HLK signing. You can pick the one that best suits your requirements.
-
Using our custom Utility Tool
This method involves leveraging our in-house utility tool designed to perform all kinds of Windows signing (even HLK signing). This tool streamlines the signing process, making it efficient and hassle-free.
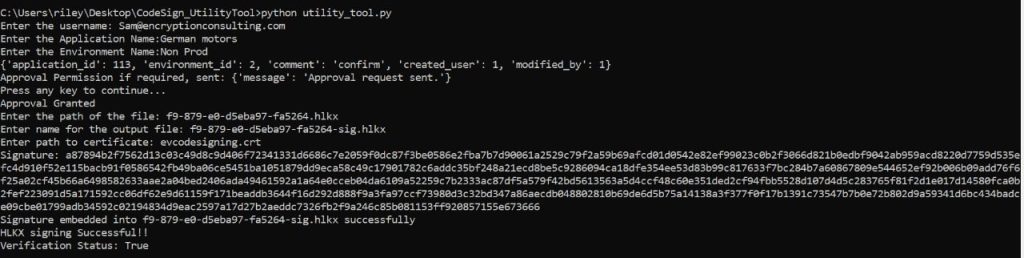
Figure 1: Enter the appropriate details which will be prompted. With this method, you can expect the following benefits:
-
Simplicity
Our utility tool is designed with user-friendliness in mind. It simplifies the HLK signing process, reducing complexities and saving time.
-
Customization
We understand that each hardware component and driver is unique. Our utility tool allows for customization to meet your specific requirements.
-
Efficiency
Time is of the essence, and our tool is optimized for efficiency. You can expect quicker results without compromising quality.
-
-
Using our KSP (Encryption Consulting Key Storage Provider) with Signtool
This method involves using our KSP (Encryption Consulting Key Storage Provider) with Microsoft’s signtool. This method offers a higher level of security and is ideal for clients who prioritize security and compatibility.
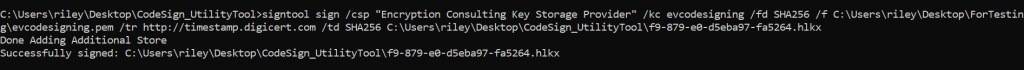
The command is:
signtool sign /csp “Encryption Consulting Key Storage Provider” /kc evcodesigning /fd SHA256 /f C:\Users\riley\Desktop\ForTesting\evcodesigning.pem /tr http://timestamp.digicert.com /td SHA256 C:\Users\riley\Desktop\CodeSign_UtilityTool\f9-879-e0-d5eba97-fa5264.hlkx
| /csp | To enter our KSP (Encryption Consulting Key Storage Provider). [This will not vary and remain constant] |
| /kc | A key container within the CSP that holds the private key. [Rename it to the private key alias you’re going to use] |
| /fd | File digest algorithm to use for creating file signatures. |
| /f | Indicates the location of the public key file or certificate. [Make sure to sign using a .pem file only] |
| /tr | Specifies the URL of the RFC 3161 timestamp server. This helps provide a timestamp for when the file was signed. |
| /td | Specifies the digest algorithm used by the RFC 3161 timestamp server. |
With this method, you can expect the following benefits:
-
Enhanced Security
Our KSP adds a layer of security to the signing process, safeguarding your code and drivers from potential threats.
-
Integration with Microsoft Tools
By combining our KSP with Microsoft’s signtool, you benefit from the best of both worlds – our expertise and Microsoft’s trusted tools.
-
Compliance
We ensure your signing process aligns with Microsoft’s standards, keeping your hardware and drivers fully compliant.
Overcoming Common Challenges with Encryption Consulting LLC
While HLK signing is essential, it can come with its challenges. Such as:
-
Addressing Driver Compatibility Issues
HLK signing can uncover compatibility issues that must be addressed. This might involve revising code, fixing bugs, or adjusting hardware components.
-
Troubleshooting Code Signing Problems
Code signing can sometimes be tricky, and errors can occur. Knowing how to troubleshoot and resolve these issues is crucial to achieving a successful HLK signing.
This is where Encryption Consulting LLC excels. Our team can swiftly address compatibility issues and troubleshoot code signing problems, ensuring your journey to HLK certification is smooth.
The Benefits of HLK Signing with Encryption Consulting LLC
Collaborating with Encryption Consulting LLC offers a range of benefits. Our guidance will help you stand out in the competitive hardware and driver landscape like:
-
Earning User Trust
When your hardware or driver is HLK signed, users can trust that it’s been thoroughly tested and is unlikely to cause problems on their Windows systems. This trust can lead to increased adoption and positive reviews.
-
Access to the Windows Hardware Compatibility Program (WHCP)
The WHCP, which might offer extra benefits like access to Microsoft’s support and promotional possibilities, frequently applies to HLK-signed items.
-
Building a Reputation for Reliability
HLK signature is a means to establish a reputation for dependability and quality in the business, not merely a symbol of approval.
Conclusion: A Seamless and Secure User Experience
In Windows compatibility, HLK signing is vital in ensuring your hardware and drivers are trustworthy and reliable. It’s not just about meeting Microsoft’s standards; it’s about creating a positive user experience and building a reputation for excellence. Whether a hardware manufacturer or a driver developer, HLK signing is your pathway to success in the Windows ecosystem.
In conclusion, HLK signing with the support of Encryption Consulting LLC is your gateway to a seamless and secure user experience. Whether you’re a hardware manufacturer or a driver developer, trust in our expertise to ensure your products are compatible with Windows, enhancing system stability and user trust. Try out our free trial of CodeSign Secure, available on our website. Experience the benefits of enhanced cod signing security with us today!
- Understanding the Windows Hardware Lab Kit (HLK)
- Why HLK Signing Matters?
- The Process of HLK Code Signing with Encryption Consulting LLC
- Overcoming Common Challenges with Encryption Consulting LLC
- The Benefits of HLK Signing with Encryption Consulting LLC
- Conclusion: A Seamless and Secure User Experience




