Public Key Infrastructures (PKIs) are necessary to verify the identity of different people, devices, and services. In a nutshell, PKIs go way beyond the use of user IDs and passwords, employing cryptographic technologies such as digital signatures and digital certificates to create unique credentials that can be validated beyond reasonable doubt and on a mass scale.
Before we deep dive into Modern PKI demand, lets understand:
What is PKI?
PKI stands for Public Key Infrastructure. Public Key Infrastructure is a solution where, instead of using an Email ID and Password for authentication, certificates are used. PKI also encrypts communication, using asymmetric encryption, which uses Public and Private Keys. PKI deals with managing certificates and keys and creates a highly secure environment that can also be used by users, applications, and other devices. PKI uses X.509 certificates and Public Keys, where the key is used for end-to-end encrypted communication, so that both parties build trust each other and test their authenticity.
Private and Public PKI
Organizations trying to come up with a Public Key Infrastructure (PKI) plan are often confronted with the choice between public and private PKI.
Today, most organizations take a hybrid approach, using a mix of digital certificates from both public and private CAs. As a result, it has become much more challenging to know how many certificates you have, where they reside, and whether they are compliant. Although following best practices is mandatory while deploying a solution, it is next to impossible when you are too busy chasing down application owners to renew certificates or recover from the latest outage.
Previously, the IT team of an organization had to sit and discuss the CA hierarchy (Two-tier or Three-tier hierarchy) of their PKI Infrastructure. In the modern world, with so many successfully deployed and managed PKIs, it has become easier to understand which hierarchy should deployed for an organization, based on their business needs. Today, most PKI deployments are two-tier. The three-tier architecture comes into the picture only when there is a specific technical/industrial requirement of the organization. Nowadays, as per the standard practice, it is also important to implement HSMs to store Private Keys and protect CAs, as attackers have realized the value of using private keys to breach enterprise networks.
In this article we will talk about the Modern demands for PKI, such as does your PKI fulfil all your needs, what do you use it for, etc.
Modernize your PKI
PKI is one of the most critical security tools for an organization. As the use cases continue to grow, it is important that the organization take the right expertise to keep the PKI up and running securely.
Encryption Consulting has the right expertise and helps customers deploy or migrate from Traditional PKI to a fully managed PKI, or to a highly scalable PKI-as-a-Service platform in the cloud.
A new cloud-based approach to PKI
Encryption consulting helps building and manage PKI infrastructure in the cloud as per the customers business requirements. For a two-tier based PKI model, the Root CA is offline and kept On-prem, where the issuing CA resides on the cloud. In the approach that is mentioned below, the Root CA is offline and kept On-prem. There are also two issuing CAs which were deployed, one of which is on-prem while the other is in the cloud. The on-prem CA will have security focus on non-cloud resources (such as workstation authentication etc.) and the other issuing CA will be focus on the cloud resources. Keys are secured in HSMs.
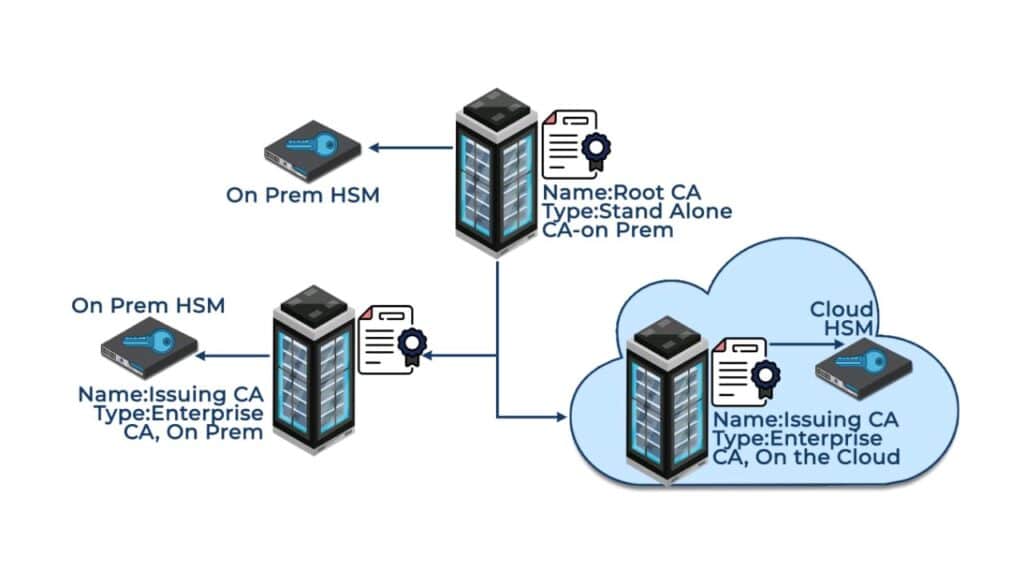
Unlike on-premises counterparts, cloud-based PKIs are externally hosted PKI services, supplying PKI capabilities on demand. The cloud-based approach drastically reduces the burden on individual organizations – financially, resource-wise, and timewise, by eliminating organizations’ need to set up any infrastructure in-house. The service provider handles all the ongoing maintenance of the PKI while ensuring scalability and availability – providing a hassle-free, efficient service.
Scalability to match the growing needs of the organization is another advantage. The service provider handles all additional requirements – installing software, hardware, backup, disaster recovery, and other infrastructure – that would otherwise become a burden for owners of on-premises PKI solutions.
To Learn more about Cloud-based PKI visit :
www.encryptionconsulting.com/cloud-based-public-key-infrastructure-architecture/
The advantages of PKI-as-a-Service
- Reduces Cost & Complexity
A quicker deployment of your PKI infrastructure, less in-hours issues, reduces spending for in-house PKI, and periodic PKI assessments and trainings are all offered with PKI-as-a-Service.
Enhance security posture with a trusted, privately rooted PKI deployed with industry best practices. - Dedicated Security Expert
Security Experts will be assigned to the service, offering consistent and flexible support to meet customer requirements and demands.
Reduced time and frustration spent on PKI-related tasks such as CA and CRL maintenance is also offered by a dedicated security expert. - Scalability and Flexibility
Provides observations and recommendations regarding current and future initiatives to help achieve desired future state capabilities.
Integrate your PKI with devices and applications using REST APIs, plug-in integrations, and standard enrollment protocols.
Additional Services
Encryption Consulting can also offer further services related to the Root CA such as:
- Sub CA signings
- Root CA and sub CA certificate lifecycle management advice (e.g. hashing algorithms / cryptographic algorithms)
- Policy / certificate profile advice
- Root maintenance
- Root migration / rollover
Encryption Consulting’s Managed PKI
Encryption Consulting LLC (EC) will completely offload the Public Key Infrastructure environment, which means EC will take care of building the PKI infrastructure to lead and manage the PKI environment (on-premises, PKI in the cloud, cloud-based hybrid PKI infrastructure) of your organization.
Encryption Consulting will deploy and support your PKI using a fully developed and tested set of procedures and audited processes. Admin rights to your Active Directory will not be required and control over your PKI and its associated business processes will always remain with you. Furthermore, for security reasons the CA keys will be held in FIPS140-2 Level 3 HSMs hosted either in in your secure datacenter or in our Encryption Consulting datacenter in Dallas, Texas.
Conclusion
Encryption Consulting’s PKI-as-a-Service, or managed PKI, allows you to get all the benefits of a well-run PKI without the operational complexity and cost of operating the software and hardware required to run the show. Your teams still maintain the control they need over day-to-day operations while offloading back-end tasks to a trusted team of PKI experts.




