Public Key Infrastructure (PKI) is mostly about managing secure digital identities that enable ways to protect data and know the subject’s (a subject could be anything such as a computer, a person, a router or a service) identity when sharing information over untrusted networks. PKI is essential to most businesses and their applications today.
As the adoption of various forms of cloud models (i.e., public, private, and hybrid) across multiple industry is increasing, the cloud buzzword is on a new high. However, customers still have concerns about security areas and raise a common question:
“How can I trust the cloud?” The most straightforward answer to this question will be to “build trust around the cloud,” but how? Well, we will discuss a few wonderful concepts of PKI, which, if planned and implemented correctly, can be a good solution
to building customers’ trust in a cloud.Before discussing in detail about cloud-based PKI architecture models, let’s refresh some basics.
What is Public Key Infrastructure (PKI)?
Public Key Infrastructure combines different technological components for authenticating users and devices within a digital ecosystem. A PKI’s primary goals are for confidentiality and authentication i.e. allow for very private conversations over any
platform while keeping individual identities available for authentication. Cryptosystems use mathematical functions or programs/protocols to encrypt and decrypt messages.Each security process, layer, or software must implement and cover the CIA triad.
- Confidentiality: It refers to the process to ensure that information sent between two parties is confidential between them only and not viewed or disclosed by/to anyone else.
- Integrity: It refers to the process to ensure that the message in transit must maintain its integrity, i.e., the message’s content must not be changed. The Integration of data is secured by hashing.
- Availability: Availability is the final component of the CIA Triad and refers to the actual availability of your data. Authentication mechanisms, access channels, and systems all have to work correctly for the information they protect and ensure it’s available when it is needed.
Along with these, there are some important parameters which are described below:
- Authentication: The process of confirming someone’s identity with the supplied parameters like username and password. PKI offers this through digital certificates.
- Authorization: The process of granting access to a resource to the confirmed identity based on their permissions.
- Non-Repudiation: A process to make sure that only the intended endpoint has sent the message and later cannot deny it. PKI offers non-repudiation through digital signature.
Challenges when adopting a cloud-based PKI model
There are various challenges in PKI as per industry and business trends. Here we will discuss some of the most common challenges.
- Lack of understanding of PKI concepts and design aspects. Also, meeting compliance requirement such as NIST-800-57 (provides recommendation for cryptographic key management) post-deployment is important.
- Ignoring the importance of HSMs . When the use of HSMs is ignored, know that your PKI will not be FIPS-140 Level 3 compliant.
- Knowing and understanding cloud providers (AWS, Azure, GCP etc.) which cloud provider can fulfil all the requirements, as per your business needs, is something that needs to be taken care of.
- Integration with your existing PKI infrastructure. Choosing the right model for your organization is a must.
- Choosing the right tools and processes for your certificate lifecycle management.
Considering Cloud-based PKI
Unlike on-premises counterpart, cloud-based PKIs are externally hosted PKI services, supplying PKI capabilities on demand. The cloud-based approach drastically reduces the burden on individual organizations – financially, resource-wise, and timewise, by eliminating organizations’ need to set up any infrastructure in-house.
The service provider handles all the ongoing maintenance of PKI while ensuring scalability and availability – providing a hassle-free, efficient service.Scalability to match the growing needs of the organization is another advantage. The service provider handles all additional requirements – installing software, hardware, backup, disaster recovery, and other infrastructure – that would otherwise become
a burden for owners of on-premises PKI solutions.
Options for Cloud-based PKI models
PKI or Public Key Infrastructure can be leveraged in several ways to benefit the organization. In each cloud-based PKI options, data security is utmost important, a properly functioning PKI is a must. Here are the following options of cloud-based PKI.
- Simple Model
- Two Tier hybrid Model
- Three Tier Model
- Three Tier Hybrid Model
Simple Model
This is the simplest model for cloud-based PKI to deploy and can be useful for small scale business models. In this approach Root CA is placed on-prem and offline the same way it is done for the traditional PKI. Issuing CA is kept on the cloud and acts
as a primary enterprise CA which issues certificates to the end-entities. Here, we leverage the cloud providers to provide management and availability for the virtual machines and certificate authorities.
For example: If your issuing CA is on AWS Certificate management private CA (ACM PCA) then to store the private keys, AWS cloud HSMs will be used.
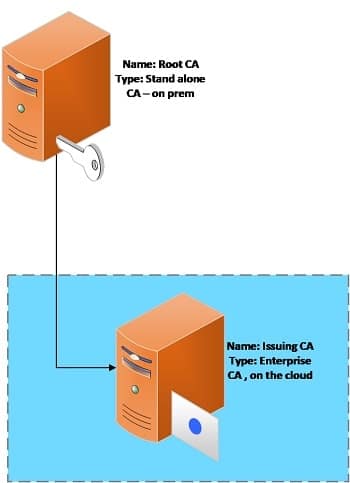
NOTE: In the above model, the security of the private keys for the issuing CA relies entirely on the cloud providers, as you are using cloud HSMs.
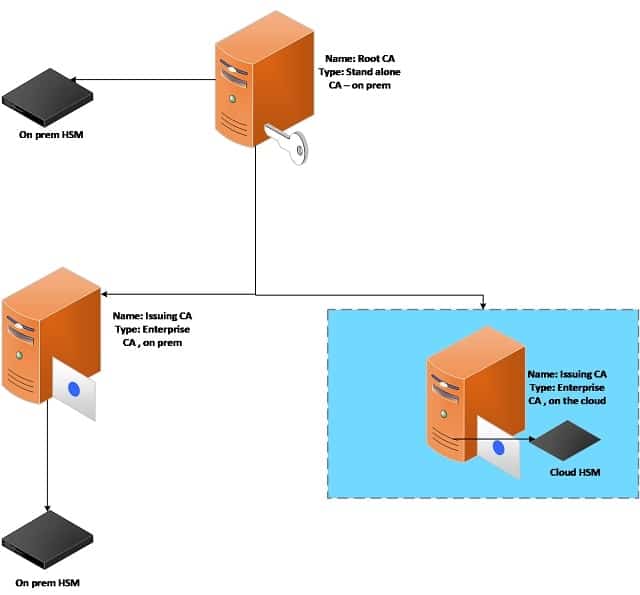
Two Tier hybrid Model
In this architectural model, we are expanding the simple model for more security. The Root CA is kept on-prem and offline. Here, we have two issuing CAs, one is kept on-prem, and another one is kept on the cloud, and both are online.If you see the previous model, there will be trouble addressing the devices of the On- premise. However, in this model we are achieving the hybrid option as we are addressing both the resources (on-premises and cloud).
The cloud Issuing CA will focus on the things which need issuance and availability outside the On-premises, whereas the on-prem Issuing CA will be focusing on the security of non-cloud resources e.g., Workstation authentication, Domain Certificates etc.
Also, the other PKI components such as CDP, AIA and OCSP can be placed on the cloud in a highly available state. By doing this, the cloud providers can be leveraged for revocation information.For this model, the signing keys are protected by both on-prem and cloud HSMs.
Three Tier Model
In this model, The Root CA is on-prem and offline and a Policy CA or Intermediate CA is added in the hierarchy (kept offline and secure) where you can explicitly define issuance and application policies. The Policy CA will decide which policies are going
to be issued and how it is going to be issued in an issuing CA.If you want to have tight control over the issuance of your certificates, while leveraging cloud providers at the same time, then putting the Policy CA on-prem and the Issuing CA on the cloud is the right use of this model.
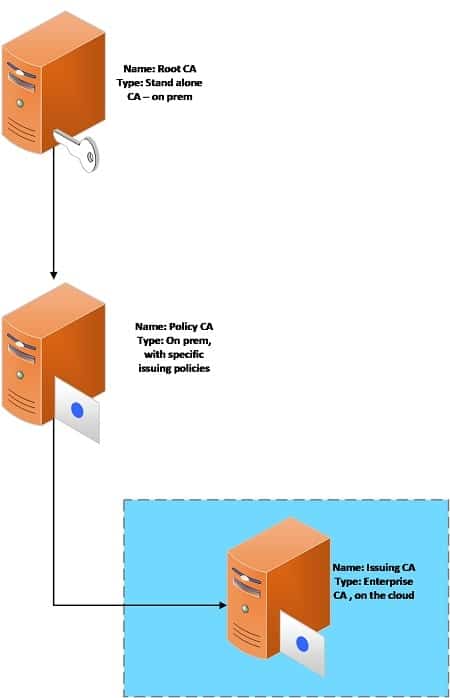
However, in this model the issuing CA will not be able to issue certificates for any other purpose except the ones explicitly mentioned in the Policy CA.
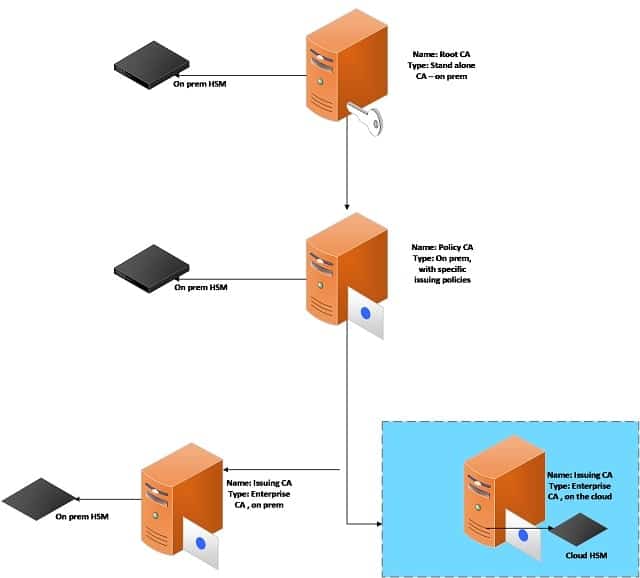
Three Tier Hybrid Model
This model is almost like the previous three-tier option. The Root CA and Policy CA are kept on-prem and offline. There are two issuing CAs, one on-prem and another one on the Cloud to address different use cases. The explicit policies will be mentioned
in the Policy CA and Issuing CAs will issue certificates according to that.In this model, HSMs are used both on-prem (for the On-prem Issuing CA) and in the cloud (for the cloud Issuing CA) to store the signing keys. However, if you wish to use an on-prem HSM for your cloud issuing CA to store keys, you can do this by putting your Microsoft CA on the AWS EC2 instance.
The cost of a cloud-based PKI
Cloud-based PKI imposes a reduced financial burden on the organisation compared to
on-premises PKI. While on-premises PKI incur both hidden and traditional costs, cloud-based PKI services only incur a single monthly fee – ensuring all outgoing PKI costs
are fixed. On-premises PKI cost organisations approximately $305,000 more than the cloud-based Managed PKI service.
Conclusion
Cloud-based PKI services allow organisations to reduce some of the expensive costs associated with PKI deployment, which includes infrastructure and personnel training. Cloud-based PKI services are a cost-effective solution for all critical business transactions, which means organisations do not have to choose between expensive security or a costly breach any longer.