Microsoft had given its digital imprimatur to a rootkit that has decrypted all the encrypted communications and sent them to the attacker-controlled servers. This malicious driver has been spread within gaming environments. This driver is known as “Netfilter,” whose primary purpose or critical role is as a rootkit that communicates with the Chinese command-and-control (C2) IPs.
Discovery
Karsten Hahn, who is a researcher at security firm G Data, discovered this driver using his company’s malware detection system. The initial observation was declared a false alarm as Microsoft had digitally signed Netfilter under the company’s Windows Hardware Compatibility Program. After further testing and research, Karsten concluded that this was not a false warning or positive. He and his fellow researchers discovered that “The core functionality seems to be eavesdropping on SSL connections. In addition to the IP redirecting component, it also installs and protects a root certificate to the registry” [1] (by reverse engineer Johann Aydinbas on Twitter)
What is a Rootkit?
A rootkit is a type of malware written to prevent or stop itself from being shown in file directories, other standard OS functions, and task monitors. A root certificate is usually used to authenticate traffic sent through connections protected by the Transport Layer Security protocol; this helps encrypt the data in transit and ensures the server whether a user connected is genuine or an imposter.
Typically, these TLS certificates are issued by a Windows-trusted Certificate Authority (or CA), and by installing these root certificates in Windows, hackers can bypass the CA requirement.
Origin story
The driver Netfiler was seen communicating with China-based C&C IPs providing no legitimate functionality, which further led to suspicions. Around this time, G Data’s malware analyst Karsten Hahn shared the signature info publicly on Twitter and contacted Microsoft.
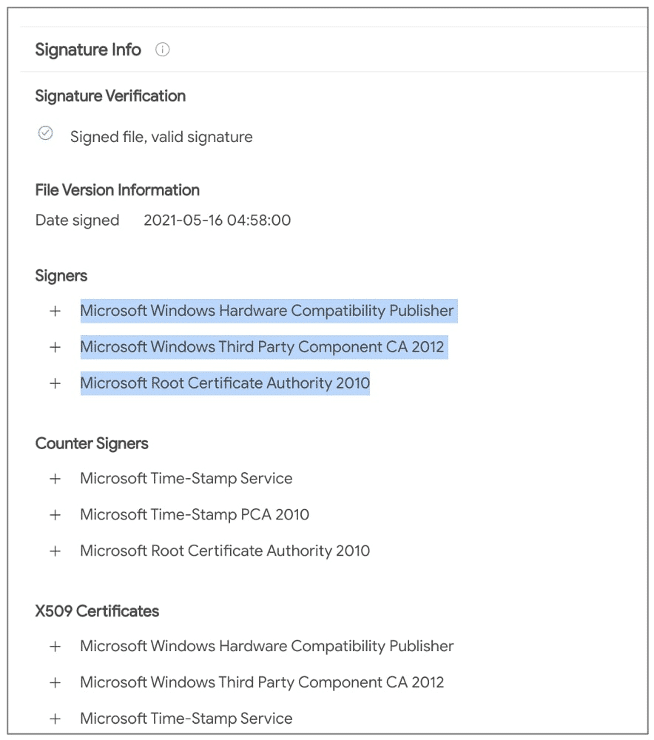
According to Hahn, any code that runs in kernel mode must be tested and signed before being released publicly to ensure stability for the Operating System. At this time, BleepingComputer also began observing the behavior of C2 URLs and contacted Microsoft for a valid reason or explanation.
The first few C2 URL returns a set of more routed separated by the pipe (“|”) symbol:
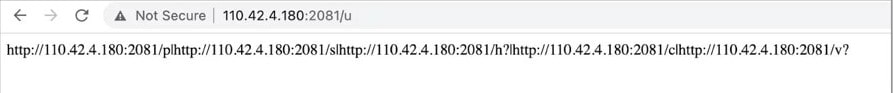
Each of these serves a purpose:
- The URL which is ending in “/p” means it’s associated with proxy settings
- “/s” denotes encoded redirection IP addresses.
- “/h?” is for representing CPU-ID.
- “/c” gave a root certificate
- “/v?” denotes the malware’s self-update functionality.
According to BleepingComputer, the “/v?” path provided the URL to the malicious Netfilter driver in the question itself (at “/d3”):
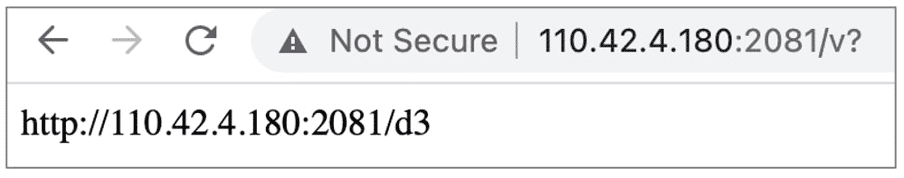
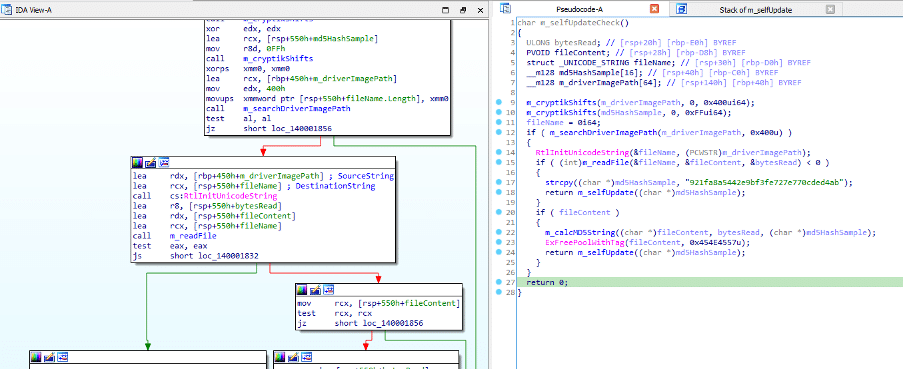
The G Data researcher, Hahn spent quite some time sufficiently analyzing the driver, result concluded that this driver has self-update functionality. According to him, the sample has a self-update routine that sends its MD5 hash to the server through “hxxp://110.42.4.180:2081/v?v=6&m=”.
The server then replies with the URL for the latest sample with “OK” if the model is up-to-date and the malware replaces its file accordingly.
Security Lapse
Microsoft said they investigate a malicious actor who distributed these negative drivers (Netfilter) within gaming environments. This actor submitted drivers for certification through the Windows Hardware Compatibility Program. These drivers were built by a third party, so Microsoft has suspended their account and reviewed their submissions for additional signs of malware. The company (Microsoft) could not find evidence of either the Windows Hardware Compatibility Program signing certificate or its WHCP signing infrastructure being compromised. So, they have since added Netfilter detections to the Windows Defender AV engine built into Windows and provided this detection to other AV providers.
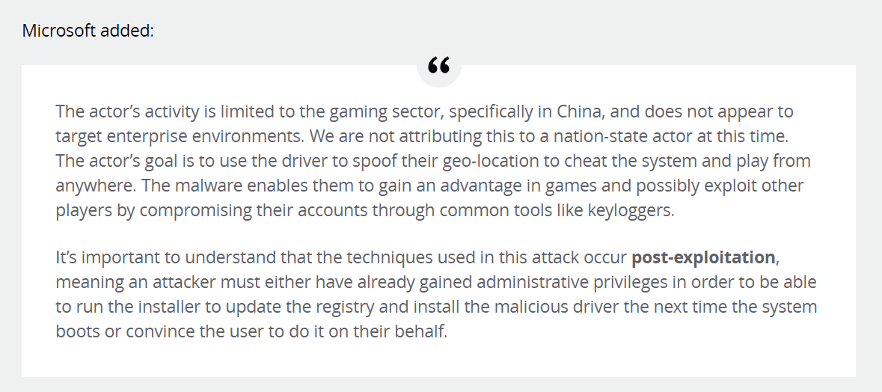
Update regarding the Malware [2]
- Jun 26th, 12:26 PM ET: Clarified that BleepingComputer did not see the DoD list explicitly mentioning the alleged Chinese company, contrary to the details in the researcher’s report. Also reached out to Hahn for clarification.
- Jun 27th, 04:58 AM ET: A previous version of the blog post mentioned another researcher, @cowonaut alleging that the company mentioned above was previously marked by the U.S. Department of Defense (DoD) as a “Communist Chinese military” company. The claim has since been retracted from the original blog post, and we have updated our article to reflect the same. However, BleepingComputer did not see Ningbo Zhuo Zhi Innovation Network Technology Co., Ltd. present on any of the DoD lists available.
Conclusion
Despite the limitations, this security lapse was a serious one. Microsoft’s certification program was designed to block precisely the kind of attack which G Data first discovered. Microsoft has yet to say how they came to sign the malware digitally; company representatives also declined to explain.




