Exploring Active Directory Certificate Services (ADCS) containers within the Active Directory structure is crucial for understanding how digital certificates are managed and distributed in an organization. This comprehensive guide delves into the intricacies of ADCS containers, shedding light on their purposes and functionalities.
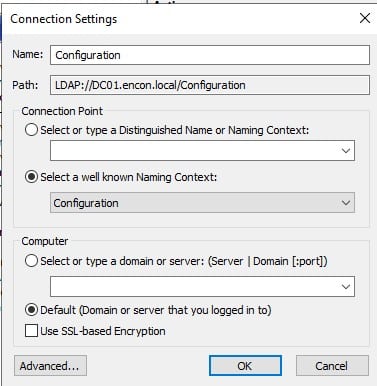
You will need to navigate to your domain controller and open ADSIEdit.msc. Once you open, you can click on Actions and then Connect to and then choose Configuration under well known Naming Context.
Understanding ADCS Containers
ADCS containers are stored within the configuration naming context under the Public Key Services container:
CN=Public Key Services, CN=Services, CN=Configuration, DC={forest root domain}
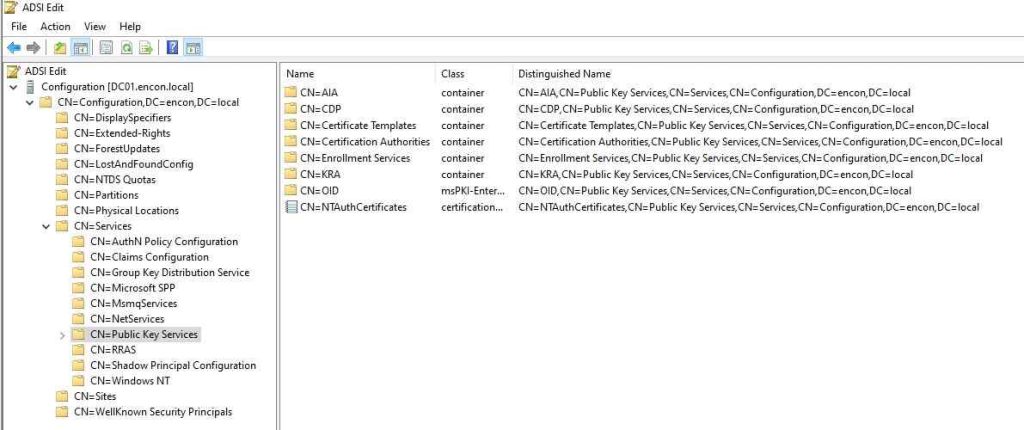
These containers facilitate storing and distributing various components essential for certificate management across the forest.
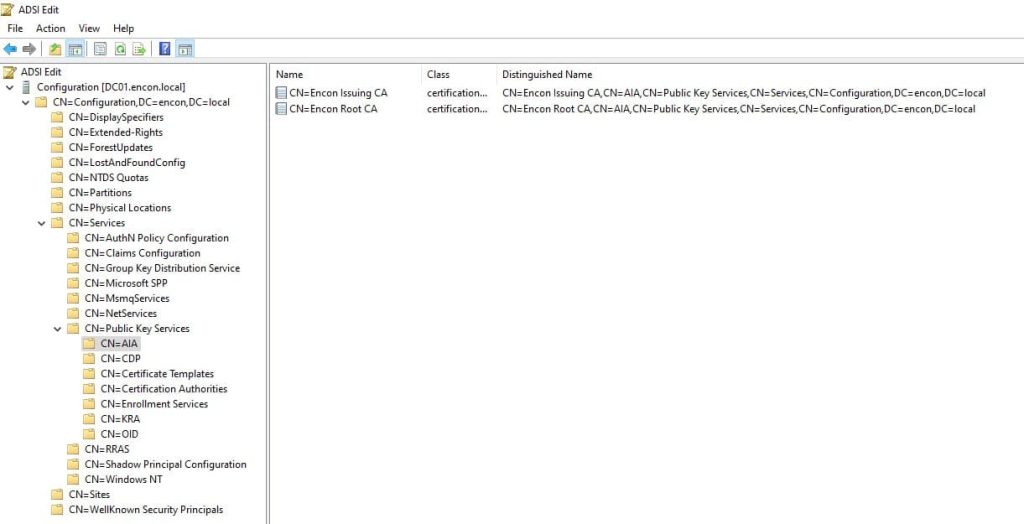
AIA (Authority Information Access)
The AIA container serves as a repository for intermediate CA certificates and cross-certificates. These certificates are crucial in establishing trust chains within the PKI infrastructure. New Enterprise CA installations automatically populate the AIA container.
To programmatically install CA certificates into this container, utilize the following command:
certutil –dspublish –f
The AIA container stores intermediate CA certificates and cross-certificates and serves as a critical component in the certificate validation process. Clients rely on the AIA container to retrieve missing intermediate CA certificates necessary for building certificate chains, ensuring seamless trust establishment and validation across the PKI infrastructure.
CDP (CRL Distribution Point):
The CDP container is designated for storing Certificate Revocation Lists (CRLs). Each CA has its dedicated CDP container, typically identified by the CA host’s NetBIOS name. New Enterprise CA deployments automatically publish initial CRLs to the CDP container.
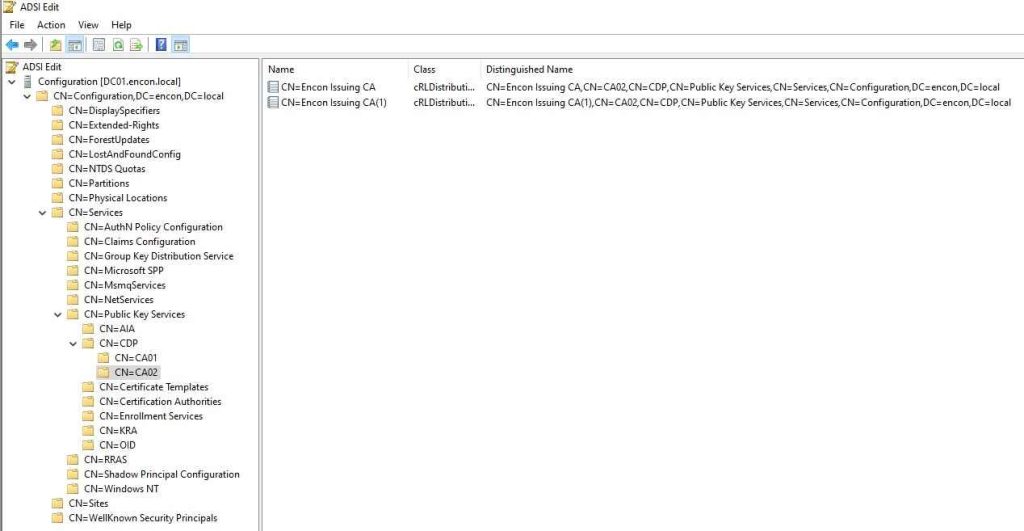
To programmatically install CRLs into this container, employ the following command:
certutil –dspublish –f
In addition to storing Certificate Revocation Lists (CRLs), the CDP container plays a vital role in ensuring the integrity and security of the PKI ecosystem. It facilitates timely dissemination of CRLs to clients, allowing them to verify the revocation status of certificates. Proper configuration of CDP locations is essential to ensure that clients can efficiently retrieve CRLs when needed, thereby enhancing the overall security posture of the environment.
Certificate Templates
This container houses enterprise certificate templates utilized by Enterprise CAs. While direct template editing is discouraged, administrators can manage templates using the Certificate Templates MMC snap-in (certtmpl.msc).
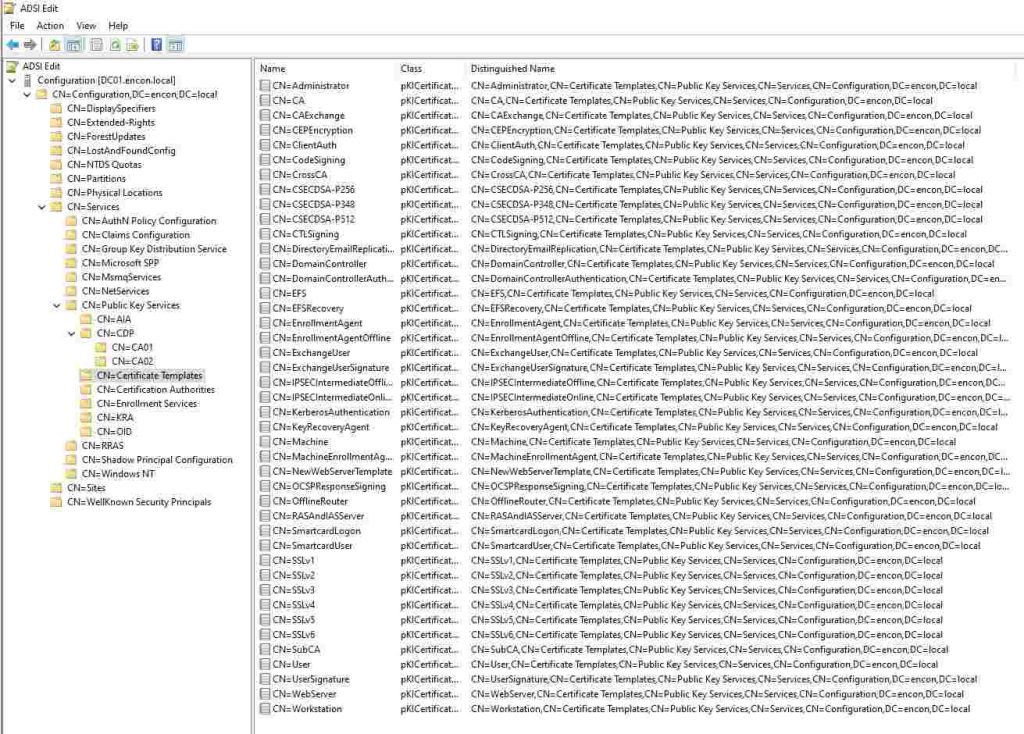
While the Certificate Templates container primarily houses predefined enterprise certificate templates, it also provides a framework for customizing certificate issuance policies. Administrators can tailor certificate templates to meet specific organizational requirements, defining key attributes such as key usage, subject name, and validity period.
By leveraging the flexibility of certificate templates, organizations can streamline the certificate issuance process while adhering to industry best practices and compliance standards.
Certification Authorities
The Certification Authorities container stores trusted root certificates, which are essential for establishing trust relationships within the PKI infrastructure. Enterprise Root CA installations automatically add their certificates to this container.
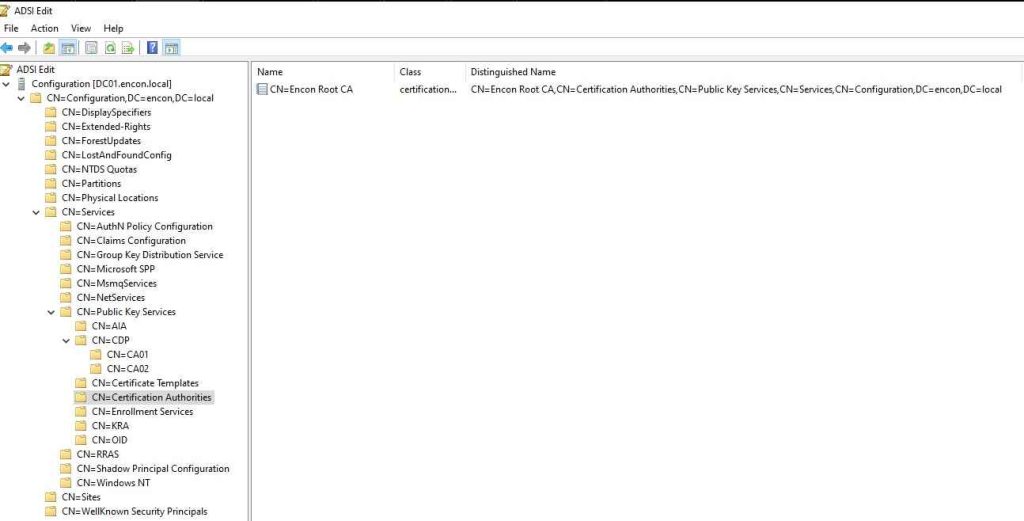
To programmatically install Root CA certificates into this container, execute the following command:
certutil –dspublish –f
Beyond storing trusted root certificates, the Certification Authorities container is a central repository for managing the trust anchors within the PKI hierarchy. By importing their root certificates, administrators can leverage this container to establish trust relationships with external entities, such as partners or third-party CAs. Furthermore, maintaining an up-to-date list of trusted certification authorities is essential for ensuring the authenticity and integrity of certificates issued within the organization.
Enrollment Services
Enterprise CA objects are stored within the Enrollment Services container, facilitating client access to Enterprise CAs across the forest. This container plays a vital role in certificate enrollment processes.

The Enrollment Services container facilitates the discovery of Enterprise CAs by clients and plays a crucial role in automating the certificate enrollment process. Clients leverage this container to identify available enrollment services within the forest, enabling them to request and obtain certificates seamlessly. By centrally managing enrollment services, organizations can enforce consistent certificate issuance policies and ensure compliance with security requirements.
KRA (Key Recovery Agent)
The KRA container stores key recovery agent certificates for each Enterprise CA, enabling key recovery operations when required.

In addition to storing key recovery agent certificates, the KRA container supports key archival and recovery operations essential for data protection and compliance purposes. Organizations can designate specific individuals or entities as key recovery agents, allowing them to recover encrypted data in the event of key loss or compromise. Proper management of the KRA container, including regular review and rotation of key recovery agent certificates, is crucial for maintaining the integrity and confidentiality of sensitive information.
OID (Object Identifier)
The OID container maintains object identifiers registered within the enterprise, which is essential for defining custom Application Policies, Issuance Policies, and certificate templates.
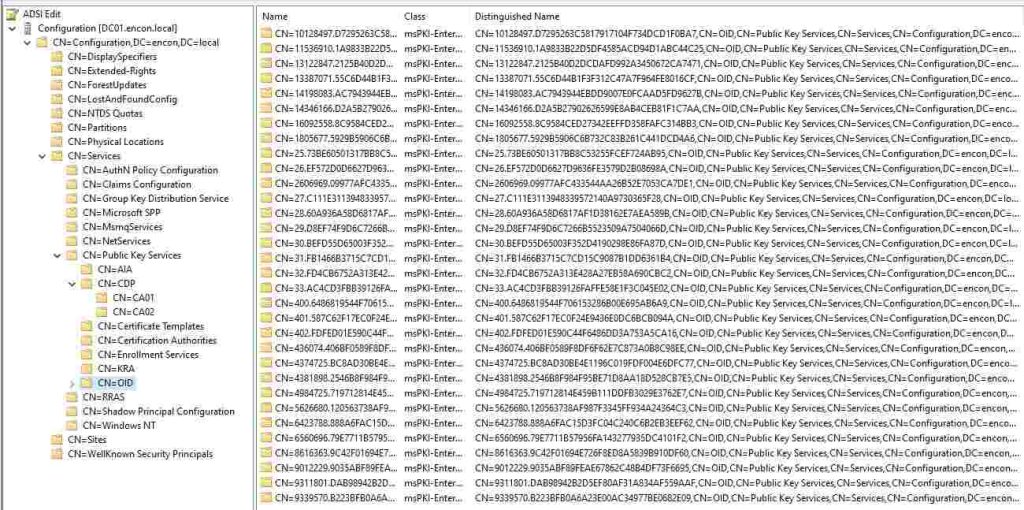
The OID container serves as a registry for object identifiers (OIDs) registered within the enterprise, facilitating interoperability and standardization across diverse systems and applications. Administrators can allocate unique OIDs to custom application policies, issuance policies, and certificate templates, ensuring consistent identification and interpretation of cryptographic objects. Organizations can avoid conflicts and promote compatibility with industry standards and protocols by maintaining a centralized OID repository.
NTAuthCertificates
NTAuthCertificates is not a container but an entry. This entry stores certificates for CAs eligible to issue smart card logon certificates and perform client private key archivally. Smart card logon and certificate enrollment processes rely on certificates stored within this container.
The NTAuthCertificates entry supports advanced authentication mechanisms within the Active Directory environment, such as smart card logon. By storing certificates for CAs eligible to issue smart card logon certificates and perform private key archival, this container enables secure authentication and data protection for users and systems.
Organizations can enhance their security posture by ensuring that only trusted CAs are included in the NTAuthCertificates entry, mitigating the risk of unauthorized access and data breaches.
Alternate AD Container Management Options
While ADSIEdit.msc provides insights into ADCS container details, tools like PKI Health Monitor (PKIView.msc) offer a more user-friendly interface for managing container contents. Additionally, certutil.exe proves instrumental in adding certificates and CRLs to various containers.
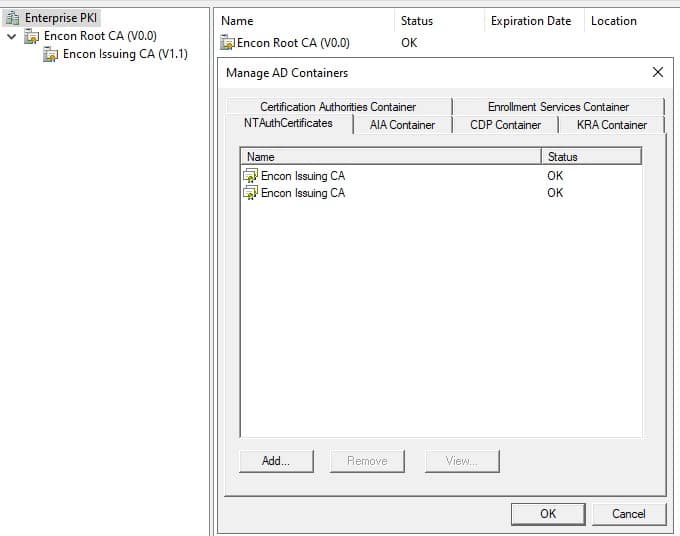
To open this, AD Containers
- run PKIView.msc on your issuing CAs.
- Click on Enterprise PKI, and then click on Actions, and then click on Manage AD Containers
- This will open the AD Containers pane, which has a more user-friendly UI and can be used to view and modify the AD containers.
Permissions
By default, only members of the Enterprise Admins group possess permission to modify Public Key Services’ contents. However, administrators can delegate appropriate permissions via ADSIEdit.msc as needed.
Conclusion
Understanding the intricacies of ADCS containers is pivotal for effective certificate management within Active Directory environments. By leveraging these containers and adopting best management practices, organizations can ensure a strong and secure PKI infrastructure.
How can Encryption Consulting help?
Encryption Consulting provides specialized services to identify vulnerabilities and mitigate risks by providing PKI Services. Our strategic guidance aligns PKI solutions with organizational objectives, enhancing efficiency and minimizing costs. By partnering with Encryption Consulting, organizations can unlock the full potential of PKI solutions, realizing tangible financial benefits while maintaining strong security measures.
Encryption Consulting’s PKIaaS provides a flexible and secure PKI solution tailored to your specific needs, offering benefits such as customizable options, high assurance standards, and a low-risk managed approach. PKIaaS automates key and certificate management tasks, reducing operational overhead and minimizing the risk of human error. Additionally, it enhances network visibility by requiring certificates for access. It will take care of building the PKI infrastructure to lead and manage the PKI environment (cloud/ hybrid or On-Prem) of your organization.
CertSecure Manager has a comprehensive suite of lifecycle management features. From discovery and inventory to issuance, deployment, renewal, revocation, and reporting. CertSecure provides an all-encompassing solution. Intelligent report generation, alerting, automation, automatic deployment onto servers, and certificate enrollment add layers of sophistication, making it a versatile and intelligent asset.
- Understanding ADCS Containers
- AIA (Authority Information Access)
- CDP (CRL Distribution Point):
- Certificate Templates
- Certification Authorities
- Enrollment Services
- KRA (Key Recovery Agent)
- OID (Object Identifier)
- NTAuthCertificates
- Alternate AD Container Management Options
- Permissions
- Conclusion
- How can Encryption Consulting help?