Introduction
For our digital security and communication infrastructure, it is crucial to secure sensitive data during transmission. This is where encryption becomes necessary. Encryption allows us to secure sensitive data from unauthorized users. This is achieved by turning the plain text into ciphertext using an encryption algorithm and a unique key. The nature of the key defines the difference between symmetric and asymmetric encryption. While symmetric encryption requires a single key, asymmetric encryption requires a pair of public and private keys to ensure the separation of concerns. Understanding the working of each technique is crucial to designing a secure infrastructure with maximum security.
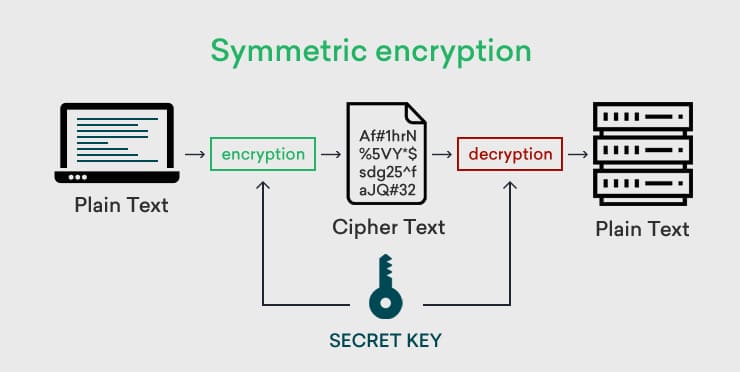
What is Symmetric Encryption?
Symmetric encryption allows for encrypting and decrypting data with a single unique key. In this system, both sender and receiver have the same secret key used for encryption and decryption.
For Symmetric encryption, a secret key is generated by a trusted party; this key is central to all cryptographic processes involved and hence cannot be compromised. Then the plaintext data is encrypted by the sender using the secret key, turning it into ciphertext. This ciphertext is secure for storage and transmission, as any breached data cannot be used in any meaningful way unless decrypted with brute force (computationally infeasible). The ciphertext is then sent over the network without any additional layer of security, as all the data is encrypted and will retain all the data throughout the transmission if no tampering or data loss occurs.
The receiver uses the same secret key to decrypt the ciphertext and recovers the original plaintext.
Banking Sector: In the banking industry, symmetric encryption, especially Advanced Encryption Standard (AES), is used as the key tool in the protection of confidential payment data, which protects card transactions and reduces the chances of identity theft and fraud. Furthermore, validation processes that can prove the authenticity of the sender of financial operations are put in place to facilitate secure financial operations by these systems.
Data at Rest: Regarding data at rest, there are technologies like BitLocker that use AES-based symmetric encryption to secure information stored in hard drives, as well as laptops and flash drives, to maintain confidentiality when data is unused.
File Encryption: With each file protection, such as VeraCrypt and AxCrypt, symmetric encryption is used to protect specific files or the whole drive, ensuring data privacy.
Database Protection: The confidential information in a database, such as customer records, is protected using algorithms like AES to prevent unauthorized access to the information, further strengthening its security.
Secure Messaging: Such messaging services as WhatsApp and Signal implement a symmetric encryption protocol, namely AES-256, to offer fast and secure messaging and protocols, including Signal Protocol, to protect messages as they are sent.
Encrypted Backups: What is more, cloud-based backup and storage, such as iCloud and Google Workspace, encrypt backups under AES-256 and, thus, safeguard large volumes of data against possible data leaks.
Cloud Storage: Last, symmetric encryption is also used in the storage of data in a cloud environment since it protects the information of users from being accessed by unauthorized persons.
Because of its efficiency, symmetric encryption (made possible by algorithms like AES, DES, Blowfish, etc.) is suitable for use in closed systems where key distribution is in control. However, it is important to transfer secure keys successfully since a leak might expose the encrypted content.
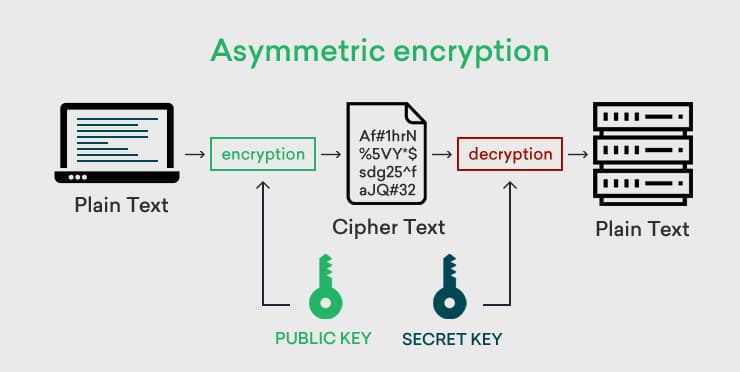
What is Asymmetric Encryption?
Asymmetric encryption uses a pair of keys to encrypt and decrypt data, respectively. Both keys can be used for encryption, but the encrypted data cannot be decrypted by the same key.
For Asymmetric encryption, a pair of keys is generated.
- Public Key: The primary purpose of this key is to encrypt data from other users. This key can be distributed publicly, as no encrypted data can be decrypted with this.
- Private Key: The primary purpose of this key is to decrypt the data coming from other users. For which this key is kept secret, as this is the single point of failure.
Once the keys are generated, the sender obtains the public key and encrypts the data. The ciphertext cannot be converted back with the same public key. The encrypted ciphertext is then sent over a network to the recipient, without any additional security. Even though the public key is available to everyone, no one can decrypt this message.
The recipient uses their private key (which they keep secret) to decrypt the ciphertext and recover the original plaintext data.
Secure Email: Organizations will be able to rely on asymmetric encryption through security email protocols like PGP and S/MIME to ensure confidentiality through an ASN, which ensures that only the recipient will be able to read their messages.
Digital Signatures: Similarly, digital signatures can be used in emails, financial transactions, and software delivery with a corresponding use of authenticating content and confirming integrity. Industry-standard tools that make use of asymmetric encryption, like Adobe Sign to implement non-repudiation, are FIPS 186-4 (NIST FIPS 186-4) compliant.
Key Exchange: To have a secure transaction of the exchanged keys, Diffie-Hellman algorithms allow both parties to share symmetric keys without prior knowledge and allow them to communicate through an encrypted route.
Secure Websites: HTTPS-enabled TLS handshakes and other online security programs like it use the asymmetric method of RSA to create encrypted connections between servers and web browsers, which enables safe browsing.
Device Security: Management systems such as prey rely on asymmetric encryption to protect their mobile devices in the event of loss or theft and allow remote lock or wipe options to secure data.
Online Banking and E-Commerce: E-commerce and online banking also use asymmetric encryption to secure financial transactions by protecting them against the interception of information.
Blockchain: Asymmetric encryption is a key mechanism in cryptocurrencies that allows only the rightful owners to spend money by verifying the authenticity of the transactions.
Public Key Infrastructure (PKI): Encryption keys are regulated using digital certificates, which is in the view of the PKI that guarantees safe communications between organizations.
Comparison of Symmetric and Asymmetric Encryption
Symmetric and asymmetric encryption satisfy each other’s different needs, each perfectly suited to distinct situations. For data protection, symmetric encryption is faster and more efficient to encrypt big data sets in insular environments; however, it builds on protected key shadowing. Adscript, although slow, allows safe key exchanges and authentication in an open system, making a secret mutual. Their difference has been summed up in the following table:
| Aspect | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Single key for encryption and decryption | Public key for encryption, private key for decryption |
| Speed | Faster, efficient for large data | Slower, computationally intensive |
| Security | Secure if key is protected, vulnerable if compromised | More secure for key exchange and authentication |
| Key Management | Requires secure key distribution | Public key can be shared openly |
| Use Cases | Banking, file encryption, VPNs, secure storage | Secure email, digital signatures, HTTPS, key exchange |
| Algorithms | AES, DES, Blowfish, 3DES, IDEA | RSA, ECC, DSA |
Hybrid Encryption
Hybrid encryption processes use the properties of symmetric and asymmetric methods to combine the high speed of data processing and high security. Within this structure, the exchange of the symmetric key is handled by asymmetric cryptography which in turn helps faster encryption of application data. An example is: HTTPS uses asymmetric encryption to authenticate the server and to establish a server-side symmetric session key to protect subsequent session communications at the time of the TLS handshake.
In a similar fashion, the messaging systems like Signal and WhatsApp will first transfer the public keys using asymmetric encryption and then use symmetric encryption protocols with high encryption speeds like the AES256 in CBC mode by using HMAC-SHA256 to ensure an efficient and secure message transfer (Signal Blog, WhatsApp Security). This hybrid model allows safe distribution of keys, without sacrificing performance, to build the most common standard in secure web communication and messaging. Through the combination of the security of asymmetric systems with the performance of symmetric systems, hybrid systems form the foundation of some of the most important applications of today.
Conclusion
Digital security, it is impossible to deploy an effective shield without understanding the application of symmetric, asymmetric, and hybrid encryption. The relatively high performance of symmetric encryption makes that specific domain especially applicable to applications in banking, file encryption, VPNs, and secure messaging, but requires secure key management.
Compared to its relatively slow performance, the enhanced security provided by asymmetric encryption is congruent with secure email, digital signature, HTTPS, and blockchain. A combination of both is represented in hybrid encryption, the foundation of the current technology of HTTPS and messaging applications that currently offers a balance between effectiveness and safety. Selection of the suitable encryption option will depend on the critical needs of the application, viz., skillfulness, scalability, and secure key communication. Since cyber threats keep changing, it is crucial to be aware of the encryption best practices, which would protect the digital environment.
What specific use cases are most suitable for symmetric encryption? How do organizations effectively manage the challenges of key distribution in symmetric encryption? What are the current advancements or alternatives to traditional asymmetric encryption methods?




