Quantum computing has moved beyond academic discussion and into real-world preparation. Whether the timeline is five years or fifteen, the security community agrees on one thing: we must begin the preparation for transition to quantum-resistant cryptography now, not later. For CISOs, this shift represents both a technical and strategic challenge that spans technology, governance, vendor management, and long-term data protection.
Why This Matters Now
The idea that powerful adversaries are already collecting encrypted data today, waiting for the quantum capability to decrypt it tomorrow, has become a serious concern. This method, often described in the industry as “harvest now, decrypt later,” targets sensitive information with long-term value: healthcare records, legal communications, national security intelligence, or intellectual property that may still be valuable in a decade. The risk here is subtle but significant. If quantum computers eventually succeed in breaking RSA and ECC algorithms, any data protected by those methods will retroactively become readable.
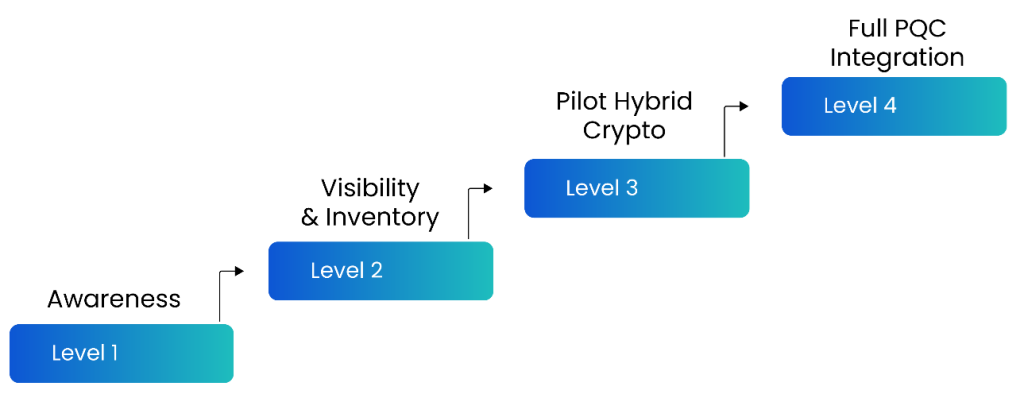
In fig 1, Each level represents a different stage organizations should move through as they progress toward full readiness:
Level 1 – Awareness:
Organizations at this stage are just beginning to understand the risks posed by quantum computing. They are learning what “harvest now, decrypt later” means and starting conversations about PQC, but have no structured plan in place yet.
Level 2 – Assessment:
Here, organizations begin to take stock of their cryptographic assets. They identify what algorithms, keys, and certificates are in use, and evaluate which systems are most vulnerable to quantum threats. This stage is heavily focused on discovery and risk assessment.
Level 3 – Planning:
At this level, organizations start building a formal roadmap for migration. This includes engaging with vendors, choosing quantum-resistant algorithms (once standardized), and creating policies around crypto-agility so systems can adapt more quickly.
Level 4 – Implementation:
The final stage involves actually deploying post-quantum algorithms and replacing legacy cryptography across the enterprise. It requires close coordination across IT, security, and compliance teams to ensure business continuity and minimal disruption.
But it’s not just data confidentiality at stake. Digital signatures, code integrity, firmware updates, and secure device onboarding all rely on asymmetric cryptography. If these mechanisms can be forged, the security of your entire supply chain could unravel. The quantum threat is less about a single catastrophic event and more about the quiet erosion of trust in the digital systems we depend on daily.
What Preparedness Looks Like?
For security leaders, the first phase of preparedness isn’t technology, it’s visibility. Most organizations lack a full picture of where cryptography is used within their environment. Public-key cryptography touches everything from TLS connections and VPN tunnels to email gateways and mobile apps. If you haven’t conducted a cryptographic inventory in the past year, or ever, it’s nearly impossible to manage the risk effectively.
A cryptographic inventory should go beyond just certificates. It must include applications, libraries, protocols, and systems that use or enforce cryptography. This often involves scanning internal applications and APIs, identifying hard-coded algorithms, and working with developers and architects to understand dependencies. Several tools can assist with this, including code scanners and specialized discovery platforms.
Once you’ve achieved visibility of your cryptographic assets and landscape, the next goal is agility. Cryptographic agility refers to the ability to swap algorithms without rewriting or re-architecting entire systems. Sounds simple, but in practice, it’s one of the most difficult aspects of this transition. Many legacy systems are not designed with modular cryptography in mind, which means even minor algorithm changes can introduce operational risk.
This is where the post-quantum transition intersects with broader IT strategy. Making your infrastructure agile doesn’t just benefit quantum resistance, it improves your ability to respond to any cryptographic vulnerability, whether it’s discovered next week or next decade. Agility also allows you to test new quantum-safe algorithms alongside traditional ones, a process commonly referred to as hybrid cryptography.
Hybrid Cryptography: A Practical First Step
Hybrid cryptography is quickly becoming the industry’s preferred strategy for initial implementation. Instead of replacing RSA or ECC outright, hybrid models allow for two algorithms, typically one classical and one quantum-resistant to work together. This creates a safety net during the migration phase. If one algorithm is broken or fails validation, the other provides continued protection.
Leading organizations are already rolling out hybrid solutions. Google Cloud has deployed hybrid key exchange in its Key Management Service, combining elliptic curve cryptography with CRYSTALS-Kyber. Cisco has been piloting hybrid TLS using Kyber in real-world scenarios. Cloudflare, another major player, has committed to PQC support in its Zero Trust product suite by 2025. These are not theoretical proofs-of-concept, they’re live implementations meant to be tested, scaled, and refined.
For organizations still early in their journey, starting with hybrid deployments in lower-risk environments such as internal development, test labs, or partner pilot programs that can provide valuable experience and help identify operational challenges before a broader rollout.
Building a Governance Model Around PQC
Quantum preparedness is not purely a technical initiative. It demands engagement from governance, legal, risk, and procurement functions. CISOs must help translate cryptographic risk into enterprise risk, a language that resonates with the board and executive stakeholders.
This includes aligning PQC with risk registers, building it into business continuity strategies, and incorporating it into M&A due diligence, vendor risk assessments, and regulatory planning. If you’re in a regulated industry, such as financial services or healthcare, quantum-readiness is likely to become a compliance issue within the next few years. NIST has already selected Kyber, Dilithium, Falcon, and SPHINCS+ as the first standardized PQC algorithms. With FIPS publications expected in 2025, organizations bound by federal, or industry requirements should already be reviewing their roadmaps.
Engaging your vendors is a necessary part of this governance process. Begin asking about post-quantum cryptography in RFPs and vendor assessments. Seek clarity on timelines, support for hybrid modes, and whether the vendor is planning to meet upcoming compliance benchmarks. If third-party services are managing cryptographic operations, especially in cloud environments. It’s critical to understand how and when they plan to adapt.
Executing a Long-Term Transition Plan
The most successful transitions to PQC will be gradual, deliberate, and iterative. This is not a wholesale rip-and-replace. Instead, think of it as a phased maturity model.
Start with systems where cryptographic transitions are lower risk: development pipelines, internal APIs, service-to-service communication. Then expand outward, layering PQC protections into your certificate authority, identity systems, email, mobile apps, and public-facing services.
Your long-term roadmap should include the following elements: establishing metrics for quantum readiness (e.g., percentage of systems with hybrid cryptography enabled), scheduling periodic reviews of vendor alignment, maintaining a central cryptographic inventory, and running internal tabletop exercises that simulate the failure of current cryptographic standards. These activities help normalize PQC across your organization’s culture—not just its codebase.
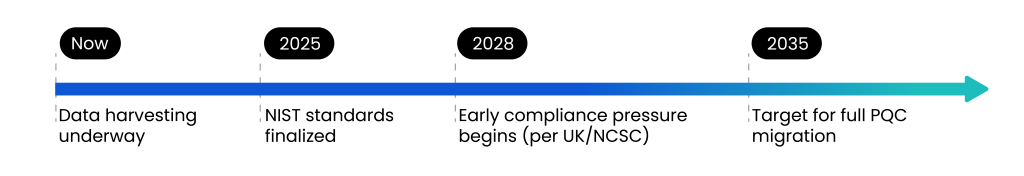
Fig 2 lays out the expected timeline for PQC migration, from today through 2035:
Now – Data Harvesting is Underway:
Adversaries are already collecting encrypted data with the intention of decrypting it once quantum computers become powerful enough. This means the clock is already ticking, even if practical quantum threats are still years away.
2025 – NIST Standards Finalized:
The U.S. National Institute of Standards and Technology (NIST) is finalizing the official post-quantum cryptographic algorithms. These standards will serve as the foundation for global adoption.
2028 – Early Compliance Pressure:
According to the UK’s National Cyber Security Centre (NCSC), organizations will begin to feel regulatory and compliance pressure to adopt PQC. Industries such as finance, defense, and healthcare may face earlier mandates due to their sensitivity.
2035 – Target for Full PQC Migration:
By this point, organizations are expected to have fully transitioned to PQC. While it may seem far off, large-scale cryptographic migrations often take a decade or more, which makes it critical to start planning today. This timeline underscores the urgency: while the final deadline may be 10 years away, the work to prepare needs to start now.
Key Takeaways
It’s important to view the quantum shift not as an isolated event, but as a transformational phase in digital trust. The decisions we make now, about architecture, standards, vendor selection, and risk management will shape the future of enterprise security in a post-quantum world.
Preparedness is not about predicting the exact year when quantum computers will break today’s encryption. It’s about ensuring your organization is structured to adapt when it happens. That kind of resilience doesn’t begin with panic or passive observation, it begins with leadership.
For CISOs, this is a moment of clarity. The post-quantum future is coming, and our responsibility is to meet it with a plan, not just for survival, but for strategic advantage.
How Encryption Consulting Can Help?
At Encryption Consulting, we help organizations navigate the complexity of post-quantum preparedness with a proven, structured approach:
- Cryptographic Assessments & Inventory: We provide discovery services to help CISOs gain complete visibility into where cryptography is used across their environments, covering certificates, applications, APIs, and embedded systems.
- Roadmap Development: Our experts design phased transition strategies tailored to your business priorities, ensuring PQC adoption aligns with governance, compliance, and operational requirements.
- Hybrid Cryptography Implementations: We assist in deploying hybrid approaches that combine classical and quantum-safe algorithms, allowing organizations to test, validate, and scale PQC solutions without business disruption.
- Governance & Compliance Alignment: From building governance models to embedding PQC into risk registers and regulatory planning, we help CISOs translate cryptographic risks into enterprise risks the board can understand.
- Documentation & Support: We deliver end-to-end documentation for build processes, firmware upgrades, cryptographic inventories, and key ceremony procedures to ensure operational excellence and audit readiness.
Whether your organization is in the early stages of PQC exploration or already running hybrid cryptography pilots, Encryption Consulting provides the expertise, tools, and frameworks to ensure a secure and seamless transition.
Conclusion
Quantum computing represents one of the most disruptive forces cybersecurity has ever faced. The shift to post-quantum cryptography isn’t simply a technical upgrade, it’s a fundamental transformation of how organizations protect data, maintain trust, and build resilience for the decades ahead. For CISOs, the task is clear: develop visibility into cryptographic assets, build agility into IT and security infrastructures, and align governance and risk management processes with this new reality. Those who act early will not only protect against tomorrow’s threats but also gain a strategic advantage in resilience and trustworthiness. The quantum era is approaching, and the time to prepare is now.