SSH or Secure Shell or Secure Socket Shell is a network protocol is how users, sysadmins can access other computers over an unsecured network.
SSH provides strong password and/or public key authentication using which a sysadmin or network admin can connect to any computer or application remotely, execute commands and also move files using SFTP or SSH File Transfer Protocol.
Where can we use SSH?
We can use SSH protocol in various scenarios such as:
- Providing secure access for users and automated processes
- Interactive and automated file transfers
- To issuing remote commands
- Managing network infrastructure and other mission-critical system components
How does SSH work?
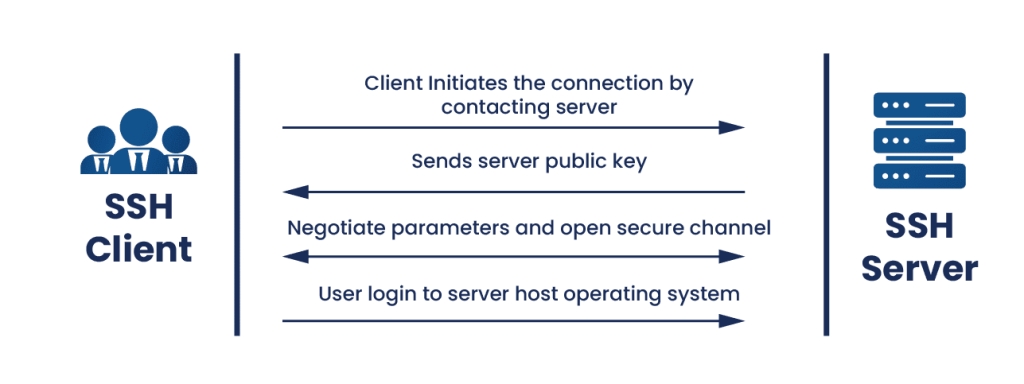
SSH protocol works in a client-server architecture, thus an SSH client connects securely to an SSH server. SSH client would drive the connection set up process and use Public Key Infrastructure to verify the authenticity of the SSH server. Following the setup, SSH protocol uses strong symmetric encryption and hashing algorithm to ensure privacy, and integrity of the data exchanged.
Source: https://www.ssh.com/
What kind of authentication can be used with SSH?
Several options can be used for user authentication. The most common ones being passwords and public key authentication.
Public Key authentication is mostly used for automated purposes and system administrators for single sign-on. There are two keys namely, the public key and the private key. The public key is configured to the server, and anyone with the private key is granted access to the server and authentication respectively. These private keys are also called SSH Keys.
SSH Key-based authentication is primarily used to enable security automation. We can have automated secure file transfers, automated systems, and also bulk configuration management which can turn out to be helpful.
Using SSH protocol to communicate can be beneficial as SSH provides strong encryption over the messages transferred and also integrity protection against any attacks. Once the connection is established between the SSH client and the SSH server, the data is encrypted using the parameters that were exchanged during the setup. During the setup, symmetric encryption is agreed upon, and keys are exchanged to continue the communication via symmetric encryption. The data transferred between the client and the server is encrypted using industry-standard strong encryption algorithms (such as AES), and the data is also hashed to ensure the integrity of the data being transferred. A hashing algorithm such as SHA-2 is used for this purpose.
Benefits of Using SSH
-
Security
SSH is renowned for its robust security features. Encryption and authentication mechanisms ensure that data remains confidential and the integrity of the connection is maintained.
-
Versatility
SSH is not limited to just remote terminal access. It can securely transfer files, tunnel other protocols, and even act as a VPN-like solution, making it a versatile tool for various use cases.
-
Cross-Platform
SSH is available on virtually all major operating systems, making it accessible and compatible across diverse environments.
-
Open Source
Several open-source implementations of SSH, such as OpenSSH, are widely used and continuously improved by the community.
-
Auditing and Logging
SSH provides robust logging and auditing capabilities, allowing administrators to track and monitor user activities and potential security incidents.
Conclusion
In a world of ever-evolving cybersecurity threats, Secure Shell (SSH) is a stalwart guardian of data privacy and security. Its ability to establish secure connections, encrypt data and authenticate users makes it an essential technology for anyone who values secure communication over the Internet. Whether you’re accessing remote servers, transferring files, or securing network traffic, SSH remains a trusted and indispensable tool in digital security.
Encryption Consulting provides comprehensive expertise and customized solutions. With a team of top experts, Encryption Consulting provides Encryption Advisory Services including Assessment, Audit Service, Strategy and Implementation Planning, ensuring that clients receive tailored answers that match their unique security desires.

