SSL stands for Secure Sockets Layer; it is the standard technology for keeping an Internet connection secure and safeguarding any sensitive data sent between two systems. The two systems can be server to client (for example, a shopping website and browser) or server to server (for example, an application with personal identifiable information or payroll information).
Table of Contents
What is a TLS Certificate?
TLS stands for Transport Layer Security, which is just an updated, and more secure, version of SSL. TLS is a cryptographic protocol that establishes an encrypted session between applications over the Internet.
TLS certificates usually contain the following information:
- The subject domain name
- The subject organization
- The name of the issuing CA
- Additional or alternative subject domain names, including subdomains, if any
- Issue date
- Expiry date
- The public key (The private key, however, is kept a secret.)
- The digital signature of the CA
How does TLS work?
TLS uses a combination of symmetric and asymmetric cryptography, as this provides a good negotiation between performance and security when transmitting data securely.
Lean more about TLS handshake:
Certificate Management | Usage | Security | Encryption Glossary (encryptionconsulting.com)
Standard SSL handshake
The communication over SSL always begins with the SSL handshake. The SSL handshake allows the browser to verify the web server, get the public key, and establish a secure connection before the beginning of the actual data transfer.
The following steps are involved in the standard SSL handshake:
-
Client Hello
Server communicates with the client using SSL.This includes the SSL version number, cipher settings, and session-specific data.
-
Server Hello
The server responds with a “server hello” message.This includes the server’s SSL version number, cipher settings, session-specific data, an SSL certificate with a public key, and other information that the client needs to communicate with the server over SSL.
-
Authentication
The client verifies the server’s SSL certificate from the CA (Certificate Authority) and authenticates the server.If the authentication fails, then the client refuses the SSL connection and throws an exception. If the authentication succeeds, then they proceed to the next step.
-
Decryption
The client creates a session key, encrypts it with the server’s public key and sends it to the server.If the server has requested client authentication (mostly in server to server communication), then the client sends their own certificate to the server.
-
Encryption with Session Key
The server decrypts the session key with its private key and sends the acknowledgement to the client encrypted with the session key.
Thus, at the end of the SSL handshake, both the client and the server have a valid session key which they will use to encrypt or decrypt the original data.

What are the types of SSL certificates?
There are multiple types of SSL certificates available today based on the validation level and number of domains they secure.SSL Certificates based on Validation Level:
-
Domain Validated certificate
The Domain Validated (DV) certificate requires the lowest level of validation because, the main purpose of DV certificates is to secure communication between the domain’s web server and browser. The CA only verifies that the owner has a control over the domain.
-
Organization Validated Certificates
The Organization Validated (OV) certificate requires a medium level validation where the CA checks the rights of an organization to use the domain and the organization’s information. The OV certificate enhances the trust level of the organization and its domain.
-
Extended Validated Certificates
The Extended Validated (EV) certificate requires a high-level validation where the CA conducts rigorous background checks on the organization according to guidelines. This includes verification of the legal, physical, and operational existence of the entity.
SSL Certificates based on the Number of Domains:
-
Single Domain Certificate
Single Domain Certificates secure one fully qualified domain name or subdomain name.
-
Wildcard SSL Certificate
Wildcard certificates cover one domain name and an unlimited number of its subdomains
-
Multi-Domain SSL Certificate
The Multi-Domain SSL certificate secures multiple domains using the same certificate with the help of the SAN extension. It is especially designed to secure Microsoft Exchange and Office Communication environments.
How will visitors know my site has an SSL certificate?
There are a few visual clues mentioned below to indicate a website has an SSL certificate:
- Padlock to the left of a URL
- An https URL prefix instead of http
- A trust seal
- A green address bar (when an EV SSL certificate is issued)
How does SSL/TLS use both asymmetric and symmetric encryption?
SSL uses symmetric encryption to encrypt data between the browser and web server while asymmetric encryption is used to exchange generated symmetric keys which validate the identity of the client and server.
Difference between SSL and TLS Certificates
The Difference between SSL and TLS certificates are minor, the notable differences include:
| For Comparison | SSL | TLS |
|---|---|---|
| Abbreviation | SSL stands for “Secure Socket Layer.” | TLS stands for “Transport Layer Security.” |
| Cipher suites | SSL protocol offers support for Fortezza cipher suite | Cipher suites SSL protocol offers support for Fortezza cipher suite The TLS standardization process makes it much easier to define new cipher suites, such as RC4, Triple DES, AES, IDEA, etc. |
| Version | Three versions of SSL have been released: SSL 1.0, 2.0, and 3.0 | Four versions of TLS have been released: TLS 1.0, 1.1, 1.2, and 1.3 |
| Version Status | All versions of SSL have been found vulnerable, and they all have been deprecated | TLS 1.0 and 1.1 have been “broken” and are deprecated as of March 2020. TLS 1.2 is the most widely deployed protocol version |
| Secure Communication | SSL is a cryptographic protocol that uses explicit connections to establish secure communication between the web server and client | TLS is also a cryptographic protocol that provides secure communication between the web server and client via implicit connections. It is the successor to the SSL protocol. |
| Master Secret | SSL creates a master secret, the message digest of the pre-master secret is used | TLS uses a pseudorandom function to generate the master secret |
How to check an SSL certificate in Chrome and Firefox?
Any site visitor can follow the below step to get certificate information in Chrome:
- Click the padlock icon in the address bar for the website
- Click on Certificate (Valid) in the pop-up
- Check the Valid from dates to validate the SSL certificate is current
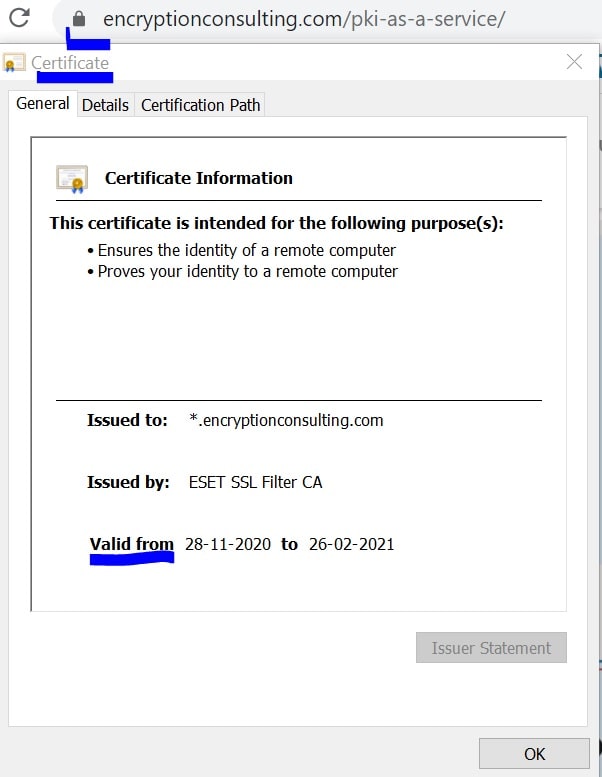
Any site visitor can follow the below step to get certificate information in Firefox:
- Click the padlock icon in the address bar for the website
- To check the details of the certificate, click on more information’
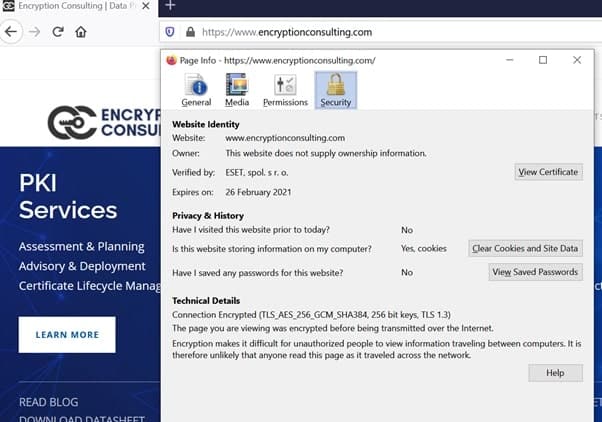
For more details about the certificate, just click “View Certificate”.

How to find your SSL certificate?
There are two methods to locate the installed SSL certificates on a website you own. In Windows Server environment, the installed certificates are stored in Certificate Stores, there are containers which holds one or more certificates. These containers are:
- Personal, which holds certificates associated with private keys to which the user has access.
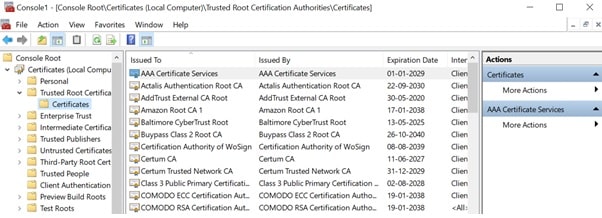
- Trusted Root Certification Authorities, which includes all the certificates in the Third-Party Root Certification Authorities store, plus root certificates from customer organizations and Microsoft
- Intermediate Certification Authorities, which includes certificates issued to subordinate CAs.
You can check the certificate stores manually on your local machine:
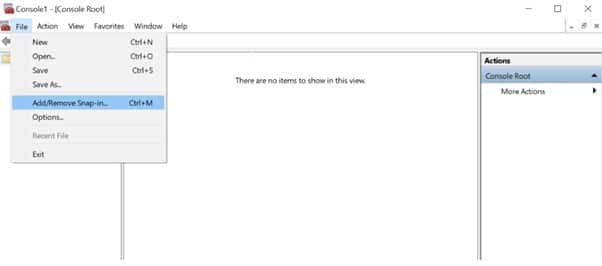
- Step 1: Open Microsoft Management console (mmc)
Run > type mcc > EnterOrOpen command prompt > type mcc > Enter
- Step 2: Click on File from the menu > select Add/Remove Snap-in
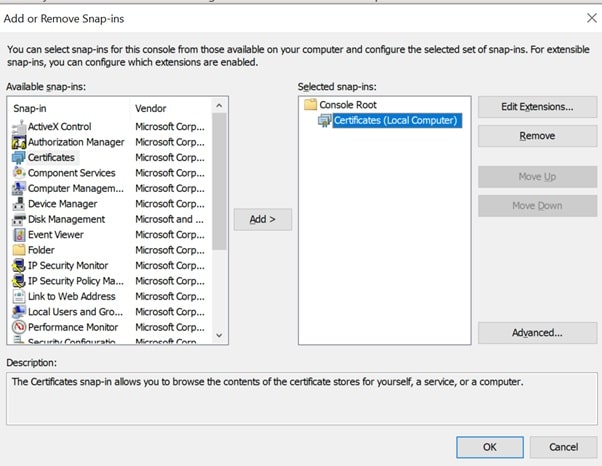
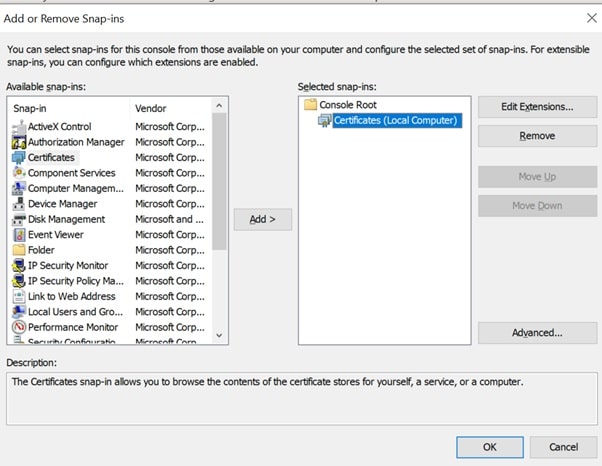
- Step 3: From the Available snap-ins list, choose Certificates, then select Add.
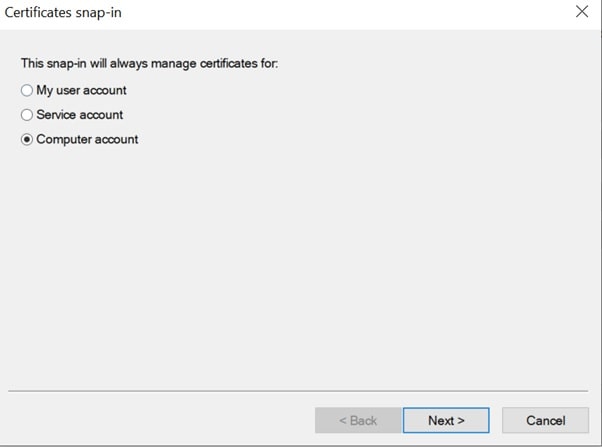
- Step 4: Select Computer account > click Next.
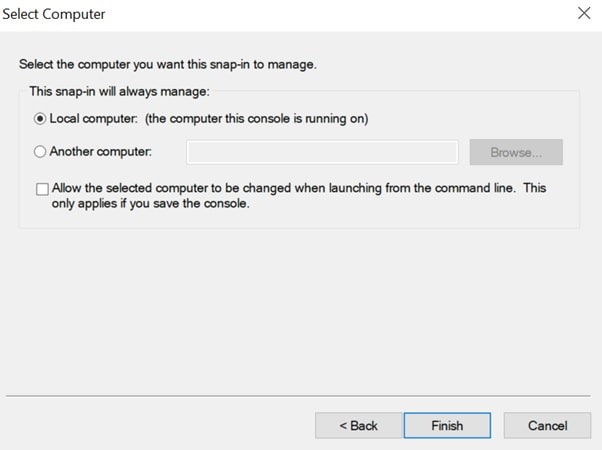
- Step 5: Select Local computer > click Finish.
- Step 6: At the “Add or Remove Snap-ins” window > click OK.
- Step 7: To view your certificates in the MMC snap-in > select a certificates store on the left pane. The available certificates are displayed on the middle pane.
- Step 8: Double click on a certificate, the Certificate window appears which displays the various attributes of the selected certificate.
Certificate Manager Tool
This is another method to view the installed certificates by launching windows Certificate Manager Tool.
- Step 1: On your local machine > open command console > type certlm.msc (Certificate Manager tool for the local device appears)
- Step 2: Under Certificates – Local Computer > expand the directory for the type of certificate you want to view


How to determine if the site you are visiting uses SSL certificates?
Along with checking your own certificate, it is important to be able to determine, if the site you are visiting uses SSL certificates. Below are a few points which you should keep in mind to check if the site uses certificates:
- Look for is the “https” in the URL of the site you are visiting. The “s” declares that this site is using an SSL Certificate.
- If you are Using Firefox > click on the padlock in the address bar > in the dropdown it should show secure connection, the secure connection indicates properly configured SSL is in use.
How to check if an SSL certificate is valid ?
SSL Certificates validity period is generally set to expire anywhere between one to three years. The validity period of the certificate completely depends on the company policy, cost considerations etc.There are multiple tools available to check the SSL certificates validity, in this article we will see how you can check the certificate validity by yourself.
-
Option 1: This process is time-consuming
Run > certlm.msc > open Certificates Local Computer
Go through the list of the certificates listed in the store to make sure only the legitimated ones are installed.
-
Option 2: Download the Windows sysinternals utility
Use Windows Sysinternals utility called sigcheck > Download
Once it is downloaded and installed > run command sigcheck -tv
Sigcheck downloads the trusted Microsoft root certificate list and provide outputs for only valid certificates.
How to set SSL certificates in Linux?
Install an SSL certificate on Linux (Apache) servers:
- Using S/FTP upload the certificate and the key files.
- Login to the server via SSH (as a root user).
- Enter Root password
- Move the certificate file and key file to /etc/httpd/conf/ssl.crt.
4.1. [It is important to keep the files secure by restricting permission. Using ‘chmod 0400’, you will securely restrict permission to the key]
- To edit Virtual Host Configuration setup for the domain, go to etc/httpd/conf.d/ssl.conf..
- Restart Apache
- Test the SSL Certificate using different browsers.
- Visit the site with the secure https URL to verify the SSL certificate is working correctly. Example: www.encryptionconsulting.com/
How to set SSL certificates in Windows?
Following are the steps to install an SSL certificate on Windows Server 2016:
- On the server (where the CSSR was created) save the SSL certificate .cer file (e.g. mydomain.cer)
- Windows start menu > type Internet Information Services (IIS) Manager > Open
- Click on the Connections menu tree > locate and Click on the server name
- Server name Home page > Action Menu > Click complete certificate Request
- In the Complete Certificate Request wizard > on the Specify Certificate Authority Response page > File name containing the certificate authority’s response > Click the box and select the .cer file
- Type a Friendly name for the certificate, (the friendly name is used to identify the certificate by adding the CA and expiration date.
- Select a certificate store for the new certificate: In the drop-down list, select Web Hosting.
- Certificate Installed successfully.
- Now, to assign the certificate to an appropriate site > go to Internet Information Services (IIS)
Manager > Connections Menu > expand the name of the server on which the certificate was installed
> expand Sites > select the sites to secure the SSL certificate
9.1.1 On the website Home page > Actions menu > Edit Site.. click bindings link
- Site Binding Window > click Add
- In the Add Site Bindings window, do the following:
Type: In the drop-down list > Select https
IP address: Select the IP address of the site or select All Unassigned.
Port: Type port 443. The port over which traffic is secure by SSL is port 443.
SSL certificate: In the drop-down list, select your new SSL certificate (e.g. mydomain.com).
- SSL Certificate is now installed successfully.
- Using different browsers, visit the site with the secure https URL to verify the SSL certificate is working correctly.
How do you renew an SSL certificate?
Renewing a certificate is, technically, purchasing a new certificate for
the domain and company. As per the industry standards, certificates comes with
an expiration date. When the certificate expires, it is no longer valid. So,
when you “renew” a certificate, the certificate authority must issue a new one
to replace the expiring one, and the new certificate must be installed on the
server.
There are two procedures to renew the certificate:
- Renew a self-signed certificate
- Renew a certificate from a CA
Renew a self-signed certificate
- On your windows Server, click on the Start menu > go to Administrative Tools > click on Internet Information Services (IIS) Manager.
- Click on the name of the server in the Connections column > Double-click on Server Certificates.
- In the Actions column on the right > click on Create Self-Signed Certificate
- Enter any friendly name and then click OK.
- The self-signed certificate has been created, and it is valid for 1 year and listed under Server Certificates.
- Now, bind the self-signed certificate to the site. Go to Connections (left column)> expand the sites folder > click on the website that you want to bind the certificate to > Click on Bindings in the right column under Actions.
- Click on Bindings > On the Site Bindings window > click on the Add
- Change the Type to https > select the SSL certificate that you just installed > Click OK.
- Binding for port 443 is now listed.
- Now, to add your self-signed certificate in the Trusted Root Certificate Authorities. Open Microsoft Management Console (MMC), create a Certificate snap-in for the Local Computer account (see the steps in the How Do you Find your SSL Certificate? section above)
- Under Certificates > expand Personal > Click on the Certificates folder > Right click on the self-signed Certificate > Copy
- Underneath Trusted Root Certification Authorities folder > click the Certificates folder > Right-click in the white area below the certificates and click Paste.
Renew a certificate from a CA
In this example we will show you how to renew the Root certificate from your CA.
- Navigate to the Microsoft Management Console (MMC) of your windows server > start the Certification Authority snap-in > Right click the name of the Certificate Authority > All Tasks > Renew CA Certificate.
- The Install CA Certificate warning pops up, which informs us that Active Directory Certificate Services must be stopped. Select Yes.
- On the Renew CA Certificate window, either choose to use the existing CA key pair or generate a new key pair for certificate renewal. The default option is to reuse the current public and private key pair.
- To check if the certificate is Renewed, Right click the name of the Certificate Authority > Properties > General
Conclusion
A website needs an SSL/TLS certificate to keep user data secure, verify ownership of the website, prevent attackers from creating a fake version of the site, and gain user trust. SSL/TLS certificates verify that a client is talking to the correct server that owns the domain. This helps prevent domain spoofing and other kinds of attacks.
How can Encryption Consulting help?
Encryption Consulting provides a specialized Certificate Lifecycle management solution CertSecure Manager. From discovery and inventory to issuance, deployment, renewal, revocation, and reporting. CertSecure provides an all-encompassing solution. Intelligent report generation, alerting, automation, automatic deployment onto servers, and certificate enrollment add layers of sophistication, making it a versatile and intelligent asset.
- What is a TLS Certificate?
- How does TLS work?
- Standard SSL handshake
- What are the types of SSL certificates?
- How will visitors know my site has an SSL certificate?
- How does SSL/TLS use both asymmetric and symmetric encryption?
- Difference between SSL and TLS Certificates
- How to check an SSL certificate in Chrome and Firefox?
- How to find your SSL certificate?
- Certificate Manager Tool
- How to determine if the site you are visiting uses SSL certificates?
- How to check if an SSL certificate is valid ?
- How to set SSL certificates in Linux?
- How to set SSL certificates in Windows?
- How do you renew an SSL certificate?
- Conclusion
- How can Encryption Consulting help?

