You use a certificate authority each time you access a website that begins with HTTPS. But the question is, what is a Certificate Authority and how it makes our lives easier by securing the internet? Let’s dive deep into what CA is.
Certificate Authority is one of the most crucial components of preserving security in the modern digital world. A Certificate Authority, or CA, is a highly trusted entity given the responsibility of signing and generating digital certificates. CAs are one of the most important pillars of a PKI. A certificate authority specifically issues digital certificates that are subsequently used to confirm the legitimacy of websites, devices, individuals, and more.

What does Certification Authority do?
A public certificate authority is essentially a publicly dependable body that issues digital certificates to people, companies, and other entities. These issued certificates are short data files with verified organization identification information. So, by having a trustworthy third party vouch for you, CAs are a technique to establish your credibility with those who don’t directly know you (or your organization).
But the question is, what about website security amidst all these?
So, a certificate authority undergoes a set of rules to ensure the integrity of certificates. The certifying authority investigates the petitioning entity before issuing a certificate. They examine records and documentation from official sources to ensure that the business is authentic. After that, the CA issues a digital certificate that the company can use to encrypt and digitally sign its software, websites, and email correspondence.
Consequently, a certification authority assists you in achieving the following if you are someone who demands a certificate for your company:
- Substantiate your organization’s identity
- Verify the legitimacy of your organization.
Verifying the Authenticity
How can you tell if you’re linked to a legitimate website? Exactly that depicts the real job of the Certification Authority; it ensures you are aware of whom you are talking with online. CAs verify websites and organizations, which prevents you from sending your data or sensitive numbers to the hacker.
If you would look at the image below shows what a secured website will look like. When you visit a secure website, there should always be a lock in the URL bar of a modern browser. The lock will reveal more information when you click on it, including a statement confirming the site’s current certificate.
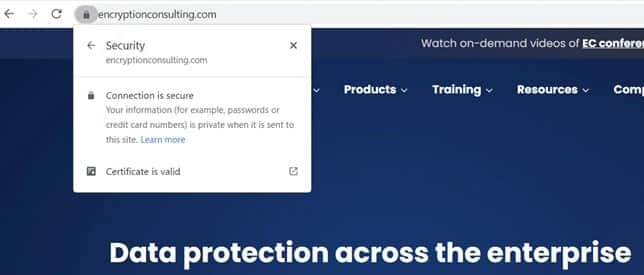
You can even see the certificate details, which include all the parameters such as whom it is issued to, who issued it, validity period and fingerprints, etc.
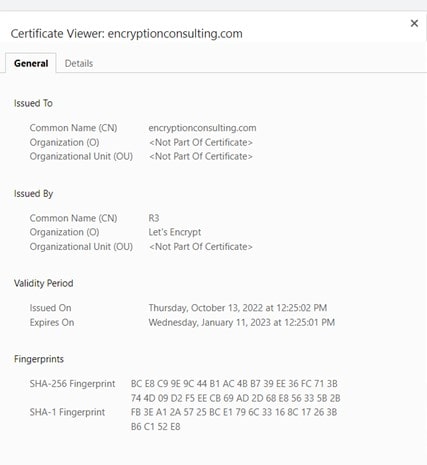
If a site displays a warning that the connection is not private and a note that the certificate is untrusted and does not have a valid certificate, it is a kind of fake website and unsafe to open.
All certificates must be issued by a reputable entity, be tamper-resistant, and include information proving their legitimacy for this system to function.
Deep Dive: How CAs Work?
A certificate authority uses asymmetric encryption for issuing certificates. One public key and one private key are used in asymmetric encryption to encrypt and decrypt a communication and safeguard it against misuse or unwanted access. The private key is used to decrypt messages that have been encrypted using the associated public key, and the certificate holder should only know it. Additionally, the certificate holder may use it to verify their identity when using a digital signature or in place of a password.
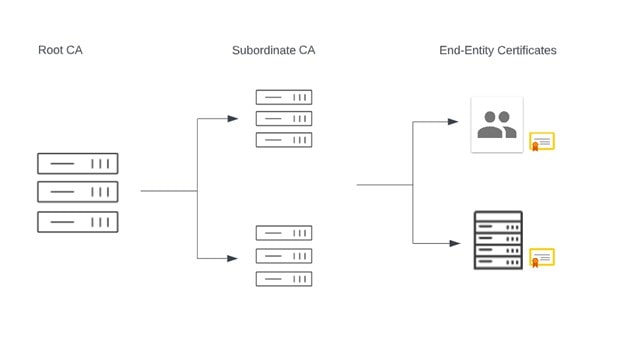
The CA hierarchy is one crucial component that supports the overall idea of the certificate authority. In essence, this indicates that CAs exist to confirm the legitimacy of and issue certificates to another certificate authority. The two most common Hierarchies include Two Tier and Three Tier CA Hierarchies, as more tiers can cause more complexity.
A Two-Tier CA Hierarchy includes Root CA and Issuing CAs, whereas a three-tier CA hierarchy includes Root CA, Policy CAs, and Issuing CAs. The Root CA will issue the intermediate CA certificate. The intermediate CA will afterward issue or sign end-entity certificates or another CA one step lower.
Public and Private CAs
Now we have two types of CAs, namely Public CA and Private CA. Despite having essentially the same functions, they are distinct, and most organizations must use both.
-
Private CAs
An internal CA governed by the company for whom it provides certificates is known as a private CA (or private certifying authority). To Demonstrate more clearly, it’s the same as signing your child’s report card. Self-signed documents may be acceptable within your company, but strangers who don’t know you will not accept them.
-
Public CAs
On the other hand, public certificate authorities are independent organizations not under the jurisdiction of the organizations to which they issue certificates. Public CAs are completely unrelated to the individuals who receive their certificates, and the certificates they issue are widely regarded as reliable on the internet.
How can Encryption Consulting help?
Encryption Consulting provides a specialized Certificate Lifecycle management solution CertSecure Manager. From discovery and inventory to issuance, deployment, renewal, revocation, and reporting. CertSecure provides an all-encompassing solution. Intelligent report generation, alerting, automation, automatic deployment onto servers, and certificate enrollment add layers of sophistication, making it a versatile and intelligent asset.
Conclusion
A Certificate Authority, or CA, is an extremely reliable entity tasked with creating and signing digital certificates. After a CA signs and issues a certificate, that certificate can be used for establishing communication or other tasks. CAs verify whether the certificates are valid; it is not a good practice to open a website with expired certificates.

