Insight Into TLS Handshake For Building Secure Communications Over The Internet

A TLS protocol is an encryption protocol that is designed to secure communications over the internet. During a TLS handshake, the two communicating parties exchange messages to recognize each other, verify each other’s identities, agree on encryption algorithms, and establish session keys. TLS handshakes are a critical component of how HTTPS works.
TLS-secured connections will display HTTPS (Hypertext Transfer Protocol Secure) in the address bar of web browsers, rather than plain HTTP. It is most often associated with safe online browsing, namely the padlock icon that shows in web browsers when a secure session is formed.
TLS’s fundamental function is to offer end-to-end encryption for all data transported from one point to another, and it leverages cryptography to ensure that only the two transacting parties can read this information. Every service in the world today requires TLS-secured connections — popular browsers do not permit users to view websites without a verified TLS connection.
TLS stands for Transport Layer Security which is the most used security protocol developed to facilitate the privacy and security of data for communications over the internet. TLS is primarily used for encrypting the communication between web applications and servers. TLS can also be used to encrypt emails, messaging, and voice over IP(VoIP).
TLS stands for Transport Layer Security which is the most used security protocol developed to facilitate the privacy and security of data for communications over the internet. TLS is primarily used for encrypting the communication between web applications and servers. TLS can also be used to encrypt emails, messaging, and voice over IP(VoIP).
TLS has evolved from Secure Socket Layer (SSL) itself, developed by Netscape. TLS version 1.0 originated as SSL version 3.1, but the protocol’s name was changed before release to signify that it was no longer affiliated with Netscape.
Message Authentication Code Protocol is used in SSL, while TLS uses Hashed Message Authentication Code Protocol.
TLS provides more security compared to SSL. SSL uses a message digest to create a master secret, while TLS uses a Pseudo-random function to create a master secret.
TLS encryption can safeguard web applications from data infractions and other attacks. HTTPS is a secure HTTP extension. Websites that install and set up an SSL/TLS certificate can leverage the HTTPS protocol to connect to the server securely. SSL/TLS’s objective is to ensure safety and security to sending sensitive information such as personal data, payment, or login information.
To establish a secure connection with a server, the client and server must first exchange a “handshake” using asymmetric cryptography. When the server receives a connection request, it delivers its digital certificate to the client at the start of the handshake. The client inspects the certificate for flaws and, if none are found, encrypts a “session key” with the public key of the server (found on the certificate).
The server decodes this session key using its private key (which is only known to it). The session key is now known by both the server and the client, and it is used to encode and decode any communications sent during that session. When the session ends, the session key is deleted.
TLS/SSL certificates are a sort of X.509 certificate that is used in browser-server communication to validate the authenticity of a server-side endpoint. A typical TLS/SSL certificate that meets with the X.509 standard comprises the owner’s public key, the subject or owner name, serial number, the name of the CA, the period in which the certificate is valid, and a digital signature with the CA’s private key.
TLS/SSL certificates are the key concepts of a Public Key Infrastructure (PKI). PKI refers to everything necessary to set up and administer public-key encryption, which is one of the most used types of internet encryption. It is built into every web browser used nowadays to encrypt public internet traffic, but enterprises may also utilize it to secure internal conversations and access to linked equipment. TLS/SSL certificates serve as security checkpoints in network communication.
These certificates connect the public key to the relevant owner, which might be a server, domain, or host. Before binding, the key must be confirmed to belong to the claimed owner, which is the responsibility of the Certificate Authority (CA) that provides these certificates. Once the validity of the entity (for example, a website) being requested has been validated, the browser uses that website’s public key to establish a secure connection with it.
A TLS certificate must be deployed on the server for a website or application to use TLS. A CA issues a TLS certificate to the person or organization that owns a domain. The certificate holds crucial information such as who owns the domain, as well as the server’s public key, both of which are required to confirm the server’s identity.
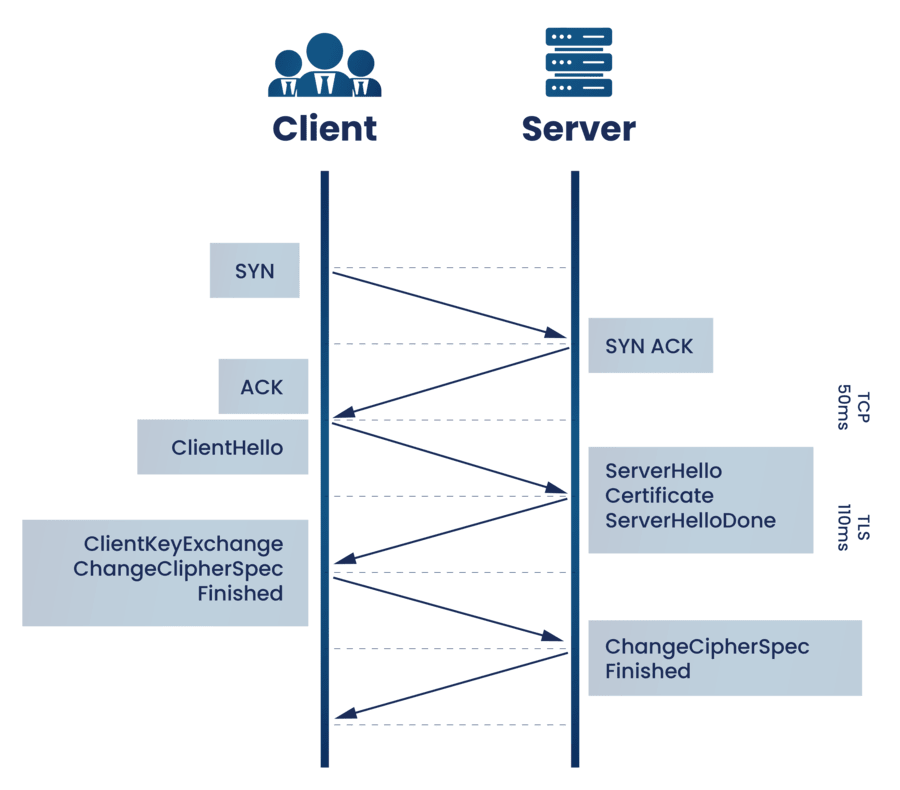
The TLS handshake sequence is used to establish a TLS connection. When a user browses a TLS-enabled website, the TLS handshake between the user’s device and the web browser begins.
The user’s device and the web server exchange the following information during the TLS handshake:
For each communication session, the TLS handshake establishes a cipher suite. The cipher suite is a collection of algorithms that provide information like which encryption keys, or session keys, will be utilized for that specific session. TLS uses public-key cryptography to set the matching session keys across an unencrypted channel.
The handshake is also responsible for authentication, which typically consists of the server verifying its identity to the client. This is accomplished through the use of public keys. Public keys are one-way encryption keys, which means that anybody who has the public key may decrypt data encrypted with the server’s private key to guarantee its validity, but the data can only be encrypted by the original sender with the private key. The public key of the server is included in its TLS certificate.
After the data has been encrypted and validated, it is signed with a message authentication code (MAC). The receiver can then validate the MAC to guarantee the data’s integrity. This is similar to the tamper-proof foil seen on medicine bottles; the buyer knows no one has tampered with their medicine since the foil is still intact when they buy it.
The user must acquire an SSL certificate from the CA, often by paying some charges or fees and then installing the certificate on the servers.
One can also get a free SSL certificate since there are some websites or platforms that offer free SSL certificates.
The primary goal of the TLS handshake is to protect data privacy and integrity by securing communication between the browser and the server. It is a message process that the client and the server exchange before building a secure encrypted connection.
As previously stated, there are several reasons to use SSL/TLS. Traditionally, one of the primary reasons for purchasing an SSL certificate is to help safeguard your website. With the arrival of let’s Encrypt and HTTP/2, now, there are additional advantages to adopting SSL/TLS encryption.