Certificate discovery is your frontline defense against outages, security breaches, and compliance risks. By uncovering every digital certificate, including third-party certificates (like those issued by public Certificate Authorities (CAs) or external vendors), it ensures nothing slips through the cracks. This proactive process isn’t just about tracking what you manage internally; it’s about mapping your entire certificate ecosystem to safeguard operations, secure communications, and maintain trust. Without visibility into what certificates exist, where they are deployed, and when they expire, organizations face serious risks like service outages, compliance failures, or security breaches. You can go through our education centre’s article on Certificate Discovery for a detailed explanation.
In large-scale environments with thousands of certificates spread across teams and systems, a centralized certificate inventory is essential for maintaining control and visibility. It enables organizations to:
- Identify unknown or unmanaged certificates before they become a threat.
- Group and organize certificates by business unit, environment, or usage.
- Enforce access control and define lifecycle policies such as setting renewal schedules, replacement intervals, and expiration alerts, to ensure certificates are managed proactively and securely.
- Monitor certificate status and receive alerts for upcoming expirations.
- Map certificates to their devices, applications, or endpoints for accountability.
What is the Actual Importance?
Many organizations still rely on outdated methods to track their certificate landscape, often using spreadsheets to record the number of certificates or their expiration dates. Despite the availability of modern solutions, manual tracking remains common. This approach not only consumes time and resources but also introduces a high risk of human error, ultimately compromising the accuracy and reliability of the certificate inventory.
In contrast, real-time visibility tools offer automated discovery, continuous monitoring, and instant alerts for certificate changes or upcoming expirations. Unlike static spreadsheets, these tools provide a dynamic, always-updated view of the certificate environment, ensuring that security teams are immediately aware of expired, weak, or misconfigured certificates before they cause issues like application outages, compliance violations, or security breaches.
Ok, now what if organizations are already managing certificates dynamically, so the problem’s being solved for them, right? Not exactly. While automation helps, it doesn’t solve the entire problem, especially as certificate volumes grow rapidly.
As organizations scale, it becomes nearly impossible to manually track every certificate in use, leading to serious risks such as service outages, non-compliance, and security vulnerabilities. Expired or misconfigured certificates can cause critical applications or websites to go down, resulting in financial loss and reputational damage. Worse, attackers can exploit unknown or weak certificates for Man-in-the-Middle (MitM) attacks or unauthorized access. Without a clear, real-time inventory of all certificates, who owns them, where they are deployed, and when they expire, organizations lack the visibility needed to protect their digital infrastructure.
This is where certificate discovery becomes essential. Certificate discovery solves this by continuously scanning and identifying all certificates, regardless of where they reside, ensuring that no asset goes unmanaged or unnoticed. It empowers security teams to detect and mitigate risks, enforce cryptographic policies, and automate renewals, which ultimately strengthens operational resilience and regulatory compliance.
Let’s consider some other factors to show the importance of Certificate Discovery:
Visibility & Inventory
Studies show that the average enterprise manages over 10,000 digital certificates, spread across various environments – from public clouds and on-premise servers to containers and end-user devices. These certificates may come from different CAs, including public ones like DigiCert, Let’s Encrypt, GlobalSign, and private CAs such as Microsoft CA or HashiCorp Vault, be provisioned using different tools, and serve various purposes.
When organizations rely on fragmented CA usage without centralized management, it becomes difficult to enforce consistent security policies. This fragmentation can lead to gaps in certificate renewal, inconsistent configurations, and increased risk of expired or weak certificates slipping through the cracks.
Without centralized visibility, managing these certificates becomes an impossible task. Certificate discovery provides a complete inventory of certificates, making it possible to monitor their status, usage, and compliance posture.
Certificate discovery solutions support hybrid and multi-cloud scenarios by continuously scanning across on-premise infrastructure, multiple public cloud providers, and containerized environments. This enables organizations to maintain a comprehensive, real-time inventory that spans all deployment platforms.
Preventing Expirations
A single expired certificate can bring down critical services—websites become inaccessible, APIs stop functioning, and customer trust takes a hit. For example, in 2021, Microsoft Teams experienced a widespread outage caused by an expired TLS certificate, leaving millions of users unable to connect for hours. Expirations are often caused not by negligence, but by lack of visibility.
Discovery tools continuously monitor certificate validity and provide timely alerts, helping teams renew or replace certificates before they expire. They often integrate seamlessly with ticketing and alert platforms like ServiceNow and PagerDuty, enabling automated workflows that create renewal tickets or notify the right teams proactively. This ensures certificates are renewed or replaced well before expiration, preventing costly service disruptions.
Security Risk Mitigation
Unmanaged certificates can be exploited by attackers. Self-signed, weak, or misconfigured certificates open doors to MITM attacks, impersonation, and unauthorized access. For instance, the 2011 DigiNotar breach, where attackers compromised a trusted certificate authority, led to fraudulent certificates that were used to intercept and spy on internet traffic.
Regularly scanning for certificates that use deprecated or weak cryptographic algorithms, such as SHA-1 or RSA keys below recommended lengths, is also critical. These outdated algorithms weaken security and increase the risk of compromise over time. Certificate discovery helps identify risky or non-compliant certificates and cryptographic weaknesses, enabling security teams to take corrective action before attackers can exploit them.
Regulatory Compliance
Expired or misconfigured certificates can lead to encryption failures or untrusted connections, resulting in violations of these regulations. Compliance mandates like PCI-DSS, HIPAA, GDPR, and others often require proper encryption and certificate management. For example, during PCI-DSS audits, the presence of expired SSL/TLS certificates on payment systems can trigger compliance failures, potentially leading to fines and increased scrutiny. Discovery ensures that organizations can prove they are using valid, trusted certificates and not exposing sensitive data to unnecessary risk.
Certificate discovery solutions also provide detailed audit trails and exportable compliance reports, enabling organizations to demonstrate continuous adherence to regulatory requirements easily. These features streamline the audit process by supplying auditors with clear, verifiable documentation of certificate status, usage, and lifecycle management.
Organizations can use our solution, CertSecure Manager, to manage their certificates, from discovery and inventory to issuance, deployment, renewal, revocation, and reporting. We’ve got you covered for everything.
How Certificate Discovery Works?
Because certificates are spread across diverse systems, networks, and cloud environments, a multi-layered discovery approach is essential to ensure no certificate goes unnoticed. Effective certificate discovery combines various scanning methods and analysis techniques tailored to different IT assets to provide a comprehensive, real-time inventory. Here’s how it typically works:
Network Scanning
Network scanning is the most common method for discovering certificates exposed over standard communication protocols. Discovery tools use techniques such as TCP port scanning, TLS/SSL handshakes, and banner grabbing to detect services running on common ports like 443 (HTTPS), 990 (FTPS), 465/587 (SMTPS), and others. When these services respond, the tool collects certificate metadata such as the subject name, issuer, expiration date, and cryptographic strength.
Popular open-source tools such as Nmap (with the ssl-cert and ssl-enum-ciphers scripts) and SSLyze are often used for performing deep TLS/SSL handshake analysis, detecting insecure ciphers, deprecated protocols, and certificate misconfigurations.
This approach is particularly effective for mapping certificates on both internet-facing and internal services, such as web servers, load balancers, and mail servers. However, it’s not without challenges. Firewalls and network segmentation can block scanning attempts, especially in sensitive environments. Additionally, tools may return false positives or miss certificates if services are configured to respond only under certain conditions. Overcoming these hurdles often requires coordination with IT and security teams, as well as fine-tuning the scan parameters.
Agent-Based Scanning
In environments where network scanning is restricted due to segmentation, firewalls, or policy constraints, agent-based scanning provides deeper visibility. Lightweight agents installed on servers, desktops, or other endpoints inspect local certificate repositories such as the Windows Certificate Store, Java keystores, and certificate files in formats like PEM, PKCS#12 (PFX/P12), and DER. On Linux, agents typically inspect file paths, application config directories, and system trust stores.
These agents can scan both system-level and application-specific stores, including certificates used by internal tools, web apps, or middleware. Once collected, the data is securely sent to a central console for analysis. This method is ideal for discovering certificates not exposed to the network, such as those used in code signing, email encryption, or authentication.
Integration-Based Discovery
Discovery tools can directly integrate with trusted certificate sources to fetch and reconcile certificate information. These integrations offer a real-time, authoritative source of certificate data, ensuring organizations stay informed about certificates issued across the environment.
Certificate Authority & Cloud Integration
Discovery tools can connect directly to public and private CAs as well as cloud-native certificate management platforms to fetch and reconcile certificate inventories. This integration provides a top-down view of certificate issuance, helping teams monitor expiry, ownership, and compliance across hybrid or multi-cloud environments. Supported integrations often include AWS Certificate Manager (ACM), Azure Key Vault, and Google Cloud Secret Manager.
DevOps & Secrets Management Integration
Modern DevOps workflows increasingly rely on automated certificate issuance. These integrations help identify short-lived, programmatically issued, or ephemeral certificates that may not appear in traditional inventories. This ensures full visibility into certificates embedded in containerized workloads, microservices, and automated deployments. Discovery tools integrate with Kubernetes clusters, Secrets managers like HashiCorp Vault, CyberArk Conjur, and CI/CD pipelines (e.g., GitHub Actions, Jenkins, GitLab).
Passive Discovery
Passive discovery involves monitoring network traffic to detect TLS/SSL handshakes and extract certificate data without initiating connections or requiring endpoint access. Tools operating in this mode are usually deployed at network chokepoints(places where all or most data traffic passes through), such as proxies, firewalls, or network taps. By analyzing handshake traffic, they can identify certificates used by devices or applications, whether managed or not. This is especially useful for discovering certificates on legacy systems, IoT devices, or unauthorized assets where no agents are installed and scanning is not possible. It also helps detect ephemeral or misused certificates in environments that change frequently.
Directory Scanning
Directory scanning significantly aids in auditing user and machine certificate usage by providing comprehensive visibility into how certificates are issued, deployed, and utilized across an organization. Many organizations distribute certificates through directory services like LDAP or Active Directory, or by using configuration management tools such as Ansible, Chef, or Puppet. Certificate discovery tools can scan these directories and configuration files to locate certificates embedded in user profiles, machine objects, or deployment scripts. This method is particularly useful for identifying certificates used in internal authentication mechanisms (e.g., smart cards, RADIUS, or 802.1x), SSO configurations, and application deployments.
How Can EC Help with Certificate Discovery?
Encryption Consulting provides a specialized Certificate Lifecycle management solution , CertSecure Manager, which scans your entire network, identifies every certificate in use, and gives you a centralized inventory with key details like issuer, expiration, and other details. By leveraging CertSecure Manager, enterprises can proactively discover and monitor their certificate infrastructure, preventing unauthorized access and vulnerabilities.
With real-time alerts, ownership tagging, and seamless integrations with your existing tools, we make it easy to prevent outages, enforce encryption policies, and stay compliant. Whether it’s rogue certificates or unknown assets, we ensure no certificate goes unnoticed. We provide:
- Real-time scanning of certificates for any of the CAs.
- Perform actions like renew, revoke, download, and many more.
- Expiration, Active, and others count of overall certificates are shown in the dashboard for easy certificate handling.
- A report and analysis are provided for the certificates.
- Multi-tenant environment support, including On-premises, Cloud, Saas, and Hybrid.
- Robust RBAC to ensure secure and granular access management within your organization. We also provide the feature of category-wise filtering out certificates so that organizations can have the freedom to easily segregate the certificates based on the category without any manual work. Here’s a reference, if one has to find out the upcoming expiring certificates in 7-30 days belonging to the SSL/TLS category.
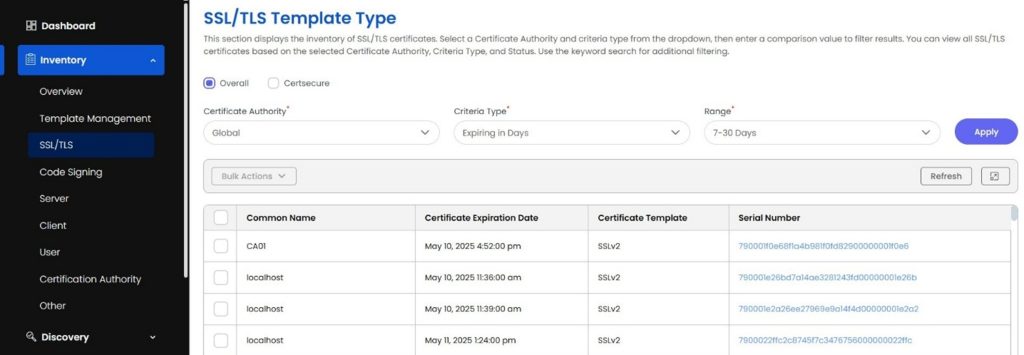
Improve security posture and compliance by identifying and removing unused or expired certificates, ensuring critical certificates are not missed or allowed to expire, and enhancing overall PKI infrastructure management.
Conclusion
Digital certificates are essential for securing modern infrastructure, but managing them without visibility is risky. As organizations adopt cloud, DevOps, and distributed systems, relying on manual tracking like spreadsheets leads to expired certificates, outages, and security gaps.
Certificate discovery solves this by providing real-time visibility into all certificates, regardless of where they’re deployed. It helps identify risks, prevent downtime, and ensure compliance through centralized, automated management.
In short, certificate discovery is not optional—it’s a critical first step in protecting your digital environment. With the right solution in place, organizations can eliminate blind spots, reduce operational risk, and maintain trust across every system.




