Data security is one of the essential parts of an organization; it can be achieved using various methods. Encryption Key has a significant role in the overall process of data. Data encryption converts the plaintext into an Encoded form (non-readable), and only authorized persons/parties can access it.
Many algorithms are available in the market for encrypting such data. The encrypted data has been safe for some time, but we never think it is permanently secure. As time goes on, there is a chance that someone gets the data hacked.

In this article, we have considered various encryption algorithms and techniques for improving the security of the data, Information Security using encryption. Comparisons of encryption algorithms based on their performance, efficiency in hardware and software, key size, availability, implementation techniques, and speed.
Summary of the algorithms
We compare the measured speed of encryption algorithms with various other algorithms available as standard in Oracle JDK, using Eclipse IDE, and then summarize multiple other characteristics of those algorithms. The encryption algorithms consider here are AES (with 128 and 256-bit keys), DES, Triple DES, IDEA, and BlowFish (with a 256-bit key).
Performance of the algorithms
The figure below shows the time taken to encrypt various numbers of 16-byte blocks of data using the algorithms mentioned above.
It is essential to note right from the beginning that beyond some ridiculous point, it is not worth sacrificing speed for security. However, the measurements obtained will still help us make certain informed decisions.
Characteristics of algorithms

Table 1 summarizes the main features of each encryption algorithm, with what we believe is a fair overview of the current security status of the algorithm.
| Factors | RSA | DES | 3DES | AES |
|---|---|---|---|---|
| Created By | In 1978 by Ron Rivest, Adi Shamir, and Leonard Adleman | In 1975 by IBM | In 1978 by IBM | In 2001 by Vincent Rijmen and Joan Daemen |
| Key Length | It depends on the number of bits in modulus n, where n = p*q | 56 bits | 168 bits (k1, k2, and k3) 112 bits (k1 and k2) | 128, 192, or 256 bits |
| Rounds | 1 | 16 | 48 | 10-128 bit key, 12-192 bit key, 14-256 bit key |
| Block Size | Variable | 64 bits | 64 bits | 128 bits |
| Cipher Type | Asymmetric Block Cipher | Symmetric Block Cipher | Symmetric Block Cipher | Symmetric Block Cipher |
| Speed | Slowest | Slow | Very Slow | Fast |
| Security | Least Secure | Not Secure enough | Adequate Security | Excellent Security |
Table 1: Characteristics of commonly used encryption algorithms
Comparison
The techniques have been compared based on that how much:
- CPU processing speed for encrypting and decrypting data.
- Rate of key generation.
- Key size.
- Security consideration.
- Efficient on the hardware and software in case of implementation.
- The amount of memory required to hold the data in the encryption process.
- Number of users accommodated by the model.
- Time required by the model to recover the data in case of key failure.
- Time available to the hacker to produce various types of attacks.
- The complexity of algorithm technique.

Formulation and Case Study
Case Study
Symmetric ciphers use the same key for encrypting and decrypting, so the sender and the receiver must both know — and use — the same secret key. All key lengths are deemed sufficient to protect classified information up to the “Secret” level, with “Top Secret” information requiring either 192- or 256-bit key lengths. There are 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys — a round consists of several processing steps that include substitution, transposition, and mixing of the input plaintext and transform it into the final output of ciphertext.
AES Design
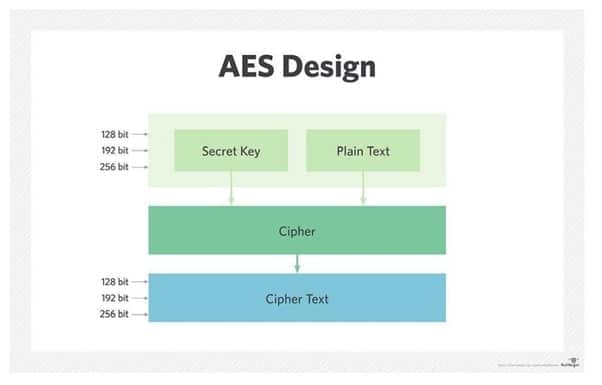
Rounds
Padding is the method of adding additional Dummy data. During the encryption process of a message, if the message is not divisible by the block length, then the padding is used. E.g., if the message consists of 426 bytes, we need seven additional bytes of padding to make the message 432 bytes long because 432 is divisible by 16. Three key sizes can be used in AES, and depending on key sizes, the number of rounds in AES changes. The standard key size in AES is 128 bits, and the rounds are 10. for AES encryption, two sub keys are generated and in 1st round a round key is added in the first round.
| No. | Key Size | No of Rounds |
|---|---|---|
| 1 | 128 bits | 10 |
| 2 | 192 bits | 12 |
| 3 | 256 bits | 14 |
For 128 bits, plain text and 128 bits key are used, and 10 rounds are performed to find the ciphertext. In the first step, 10 round keys are generated for each round, and there is a separate round key. But in the first round, an extra round key, the initial round, is added to the round, and then transformation is started. The transformation consists of four steps.
- Substitute Bytes
- Shift Rows
- Mix Columns
- Add Round Key
The Following figure explains all the encryption stages from plain text to ciphertext.
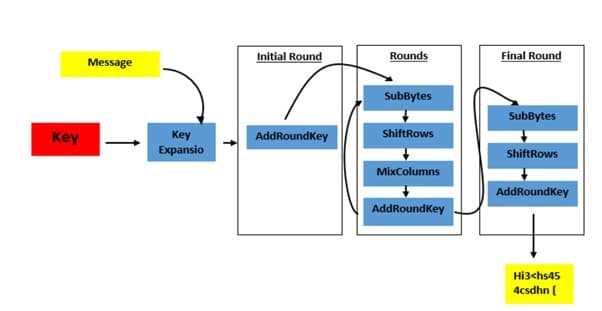
Encryption with AES
The encryption phase of AES can be broken into three steps: the initial round, the main rounds, and the final round. All of the stages use the same sub-operations in different combinations as follows:
- Initial RoundAdd Round Key
- Main Round
- Sub Bytes
- Shift Rows
- Mix Columns
- Add Round Key
- Final Round:
- Sub Bytes
- Shift Rows
- Add Round Key
- Add Round Key
This is the only phase of AES encryption that directly operates on the AES round key. In this operation, the input to the round is exclusive-or with the round key.
- Sub Bytes
Involves splitting the input into bytes and passing each through a Substitution Box or S-Box. Unlike DES, AES uses the same S-Box for all bytes. The AES S-Box implements inverse multiplication in Galois Field 2.
- Shift Rows
Each row of the 128-bit internal state of the cipher is shifted. The rows in this stage refer to the standard representation of the internal state in AES, which is a 4×4 matrix where each cell contains a byte. Bytes of the internal state is placed in the matrix across rows from left to right and down columns.
- Mix Columns
Provides diffusion by mixing the input around. Unlike Shift Rows, Mix Columns performs operations splitting the matrix by columns instead of rows. Unlike standard matrix multiplication, Mix Columns performs matrix multiplication per Galois Field 2.
Decryption with AES
To decrypt an AES-encrypted ciphertext, it is necessary to undo each stage of the encryption operation in the reverse order in which they were applied. The three-stage of decryption is as follows:
- Inverse Final Round
- Add Round Key
- Shift Rows
- Sub Bytes
- Inverse Main Round
- Add Round Key
- Mix Columns
- Shift Rows
- Sub Bytes
- Inverse Initial Round
- Add Round Key
Conclusion
The study of various algorithms shows that the model’s strength depends upon the key management , type of cryptography, number of keys, number of bits used in a key. All the keys are based on mathematical properties. The keys having more number of bits requires more computation time, indicating that the system takes more time to encrypt the data. AES data encryption is a more mathematically efficient and elegant cryptographic algorithm, but its main strength is the option for various key lengths. AES allows you to choose a 128-bit, 192-bit, or 256-bit key, making it exponentially strong. AES uses permutation-substitution, which involves a series of substitution and permutation steps to create the encrypted block




