Introduction
Encryption is the process of using an algorithm to transform plaintext information into a non-readable form called ciphertext. In simpler terms, encryption takes readable data and alters it so that it appears random. Encryption helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network such as the Internet. When the intended recipient accesses the message, the information is translated back to its original form, in a process called decryption. To unlock the message, both the sender and the recipient must use a secret encryption key — a collection of algorithms that scramble and unscramble data back to a readable format.
What is Tokenization?
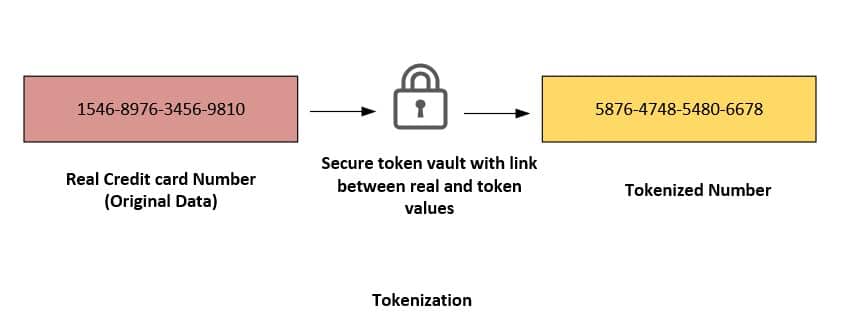
Tokenization is the process of replacing sensitive data elements (such as a bank account number/credit card number) with a non-sensitive substitute, known as a token. The token is a randomized data string which has no essential value or meaning. Unlike encrypted data, tokenized data is undecipherable and irreversible because there is no mathematical relationship between the token and its original number. There is no key or algorithm, that can be used to derive the original data for a token. Instead, tokenization uses a database, called a token vault, which stores the relationship between the sensitive value and the token. The real data in the vault is then secured, often via encryption.
Tokenization aims to safeguard sensitive information while maintaining its usefulness for business purposes. Although tokens are distinct values, they retain key characteristics of the original data, such as its length or format, allowing for seamless integration into ongoing business processes. Meanwhile, the original confidential data is securely stored in an external location, separate from the organization’s internal systems.
Furthermore, in machine learning, tokenization is crucial for feature extraction, transforming textual data into a numerical format suitable for model training. Beyond NLP, tokenization finds application in data security and blockchain, where it involves converting sensitive information into tokens to enhance privacy and reduce the risk of exposing confidential data during transactions or storage.
How data Tokenization works
Tokenization is one of the most popular security measures that merchants, payment processors, and banks use to protect sensitive financial and personal information from criminals.
For example, tokenization in banking protects cardholder data. While processing payment using the token stored in the systems, only the original credit card tokenization system can swap the token with the corresponding primary account number (PAN) and send it to the payment processor for authorization. The systems never record, transmit, or store the PAN—only the token. For tokenization to be effective, organizations must use a payment gateway to safely store sensitive data.
A payment gateway is a merchant service offered by an e-commerce application service provider that permits direct payments or credit card processing. This gateway stores credit card numbers securely and generates the random token.
Encryption vs Tokenization
While both tokenization and encryption enhance data security, their approaches differ. Tokenization focuses on replacing data with unrelated tokens, minimizing the exposure of sensitive information, and simplifying compliance with data protection regulations. Encryption, on the other hand, secures data by converting it into an unreadable format, necessitating a decryption key for access.
| Criteria | Encryption | Tokenization |
| Working process | Transforms plaintext into ciphertext using an encryption algorithm and key | Replaces sensitive data with a randomly generated token value |
| Kinds of Supported Data | Structured data such as payment cards, and unstructured data, such as entire files and emails | Structured data such as payment card, social security numbers, etc |
| Use Cases |
· In-person transactions · Payments over the phone · One of the main use cases is to ensure the confidentiality of data-at-rest (even if the storage media is compromised or lost, attackers are not able to see the actual data as they don’t have the keys) |
· Card-on-file payment · Recurring Payments · E-commerce transactions · Storing customer data across multiple locations · One of the main use cases is to reduce PCI scope by passing tokens to downstream applications. |
| Exchanging Data | Data can be exchanged with a third-party or recipient who has the encryption key | Exchanging data is difficult since it requires direct access to a token vault mapping token value |
| Security Strength | Original sensitive data leaves the organization, but in encrypted form | Original sensitive data never leaves the organization |
| Output | Output is not generally format or length preserving (e.g. AES, RSA); exception FPE- Format preserving Encryption | Output is format and length preserving |
| Mapping | May or may not use encryption as a mapping function, could use a hash function or static mapping table | Encryption does not have any use of tokenization internally |
What should your business use: Tokenization or Encryption?
The choice between encryption and tokenization is not always straightforward. Whether your organization should opt for tokenization or encryption will depend on your own unique requirements. If you want to stay compliant while reducing your obligations under PCI DSS, you can opt to use tokenization. If you want scalability, and must encrypt large volumes of data, then encryption is ideal since you only need an encryption key. But regardless of which one you choose for protecting private information, both tokenization and encryption can help satisfy regulatory requirements imposed by PCI DSS, HIPAA-HITECH, GLBA, ITAR and the upcoming EU Data Protection Regulation.
When to consider Encryption
Data encryption can efficiently apply a protective layer to large volumes of data without encumbering data transmission, or access by the recipient. In fact, for many general data protections use cases, data encryption offers the best mix of convenience, practicality, and security. Consider encryption for:
- Unstructured data, large volumes of data: Where your enterprise transmits large amounts of data such as images or video footage, data encryption can provide effective protection without incurring large costs. Likewise, where data lacks the type of structure (ID numbers, credit card details, etc.) that is required for token association, encryption is a suitable alternative.
- Lower compliance requirements. Some data requires Fort Knox-like protection, and regulation such as PCI compliance and HIPAA demands matching protective measures. Other data sets require merely adequate protection, with an associated reduced motive for data theft. In these cases, encryption is the most cost-effective protective measure.
Encryption Advisory Services
Encryption Consulting assist organizations to identify the key risks for their organization by conducting data encryption assessment. This also helps in understanding the capability maturity and any gaps that may exist in your organization. Based on this assessment, a data encryption strategy is developed, along with a roadmap that defines the components and capabilities of the data protection program and implementing an encryption plan end-to-end.
To learn more about Encryption Consulting’s advisory services, go to the following link: Encryption Advisory Services

