- What is FIPS Compliance?
- Why is FIPS Compliance Crucial?
- Understanding FIPS 140-2 vs. FIPS 140-3
- The Key Components of FIPS Compliance
- Key Differentiating Factors Between FIPS Compliance and FIPS Validation
- How to Achieve FIPS Compliance: A Step-by-Step Process
- Challenges and Considerations in FIPS Compliance
- Transitioning from FIPS 140-2 to FIPS 140-3
- Challenges in Transitioning to FIPS 140-3
- How to Prepare for the Transition?
- Who Needs FIPS Compliance?
- How Encryption Consulting Can Help?
- Conclusion
The world of cryptography and information security is constantly advancing, and at the core of this evolution are standards and regulations designed to safeguard sensitive information from unauthorized access and cyber threats. Federal Information Processing Standards (FIPS), particularly those related to cryptography, play a crucial role in ensuring that systems used to protect government data are both secure and resilient.
For organizations dealing with government contracts, financial data, healthcare records, or any form of classified or sensitive information, achieving FIPS compliance is not optional, it’s a necessity. In this blog, we will explore FIPS compliance in-depth, focusing on key aspects such as the difference between FIPS 140-2 and FIPS 140-3, how to achieve compliance, the challenges involved, and how organizations can manage the complexities of becoming fully FIPS-compliant.
What is FIPS Compliance?
At its core, FIPS compliance refers to adherence to specific guidelines and standards set by the National Institute of Standards and Technology (NIST) for the security of cryptographic modules used in the processing of sensitive federal data. These standards are part of a broader suite of regulations designed to ensure data confidentiality, integrity, and authenticity. FIPS 140-2 and the more recent FIPS 140-3 are the most well-known and widely used standards for cryptographic systems.
When organizations are FIPS-compliant, it means that their cryptographic modules, whether hardware-based or software-based, have passed strict security testing and meet the required criteria set out by NIST. These modules are crucial in protecting data from unauthorized access and ensuring that the data being transmitted or stored is secure.
While FIPS compliance might seem like a buzzword, it is a deeply technical process that involves designing and certifying systems to be resistant to both physical and logical attacks, using approved cryptographic algorithms, and following strict protocols for key management, authentication, and access control.
Why is FIPS Compliance Crucial?
For industries such as government contracting, finance, healthcare, and telecommunications, FIPS compliance is not just a technical requirement, it’s a legal obligation. For businesses serving federal clients or dealing with regulated data, non-compliance can result in the loss of contracts, fines, and damage to reputation.
Moreover, as organizations adopt more complex systems like cloud services, mobile applications, and IoT devices, the need for FIPS-compliant cryptographic solutions becomes more critical. Here’s why:
- Regulatory Compliance: Many industries are required to comply with various regulatory frameworks such as HIPAA (for healthcare), PCI DSS (for payment processing), and FISMA (for federal information security). Many of these regulations mandate the use of FIPS-approved cryptographic modules for securing sensitive data.
- Data Integrity: FIPS-certified modules help ensure that data hasn’t been tampered with. They ensure that data remains intact during storage and transmission, which is critical for industries where trust and confidentiality are paramount.
- Government Contracts: Any business working with the U.S. federal government must ensure that their cryptographic systems are FIPS-compliant. The government mandates the use of FIPS-certified solutions in its operations, and this requirement extends to contractors.
- Public Trust and Security Assurance: Achieving FIPS compliance demonstrates a commitment to the highest standards of security. It instills confidence in stakeholders and clients that their data is being handled securely.
Understanding FIPS 140-2 vs. FIPS 140-3
Before we dive deeper into how to achieve FIPS compliance, it’s essential to understand the differences between FIPS 140-2 and FIPS 140-3, as these two versions govern cryptographic modules in different ways.
FIPS 140-2: The Current Standard
FIPS 140-2 has been in effect since 2001 and is the current cryptographic standard used in federal and regulated industries. This standard specifies the security requirements for cryptographic modules, which are essential components for protecting sensitive data. The standard is divided into four security levels:
- Level 1: Requires basic cryptographic requirements, including standard algorithms like AES, RSA, and SHA, without additional physical security.
- Level 2: Adds additional physical security requirements, such as tamper-evident seals and role-based authentication, to prevent unauthorized access.
- Level 3: Requires tamper-resistant modules, along with more robust authentication mechanisms such as biometric and PIN-based access control.
- Level 4: The highest level of security, requiring a complete tamper-resistant design, continuous monitoring for attacks, and robust physical security to prevent any form of tampering.
FIPS 140-2 sets the baseline for cryptographic security and is often seen as a necessary prerequisite for government contracts or regulated industries.
FIPS 140-3: The Next Generation of Cryptographic Standards
While FIPS 140-2 has been widely adopted for many years, FIPS 140-3 was introduced in 2019 to address the increasing complexity of cybersecurity challenges. FIPS 140-3 introduces new security features and stronger testing requirements for cryptographic systems. This new version is designed to ensure that cryptographic modules can withstand increasingly sophisticated threats, particularly in the face of emerging technologies like quantum computing. FIPS 140-3 also includes four security levels, each providing increasing levels of protection to address different security needs.
Key differences between FIPS 140-2 and FIPS 140-3 include:
- Increased Testing Requirements: FIPS 140-3 emphasizes more comprehensive testing for cryptographic modules, including side-channel attack resistance, fault tolerance, and tamper detection.
- Post-Quantum Cryptography (PQC): FIPS 140-3 introduces guidelines for integrating post-quantum cryptographic algorithms into cryptographic modules, ensuring that systems are ready for future quantum computing threats.
- Broader Scope: FIPS 140-3 extends its coverage to include modern IT environments, such as cloud infrastructure, mobile devices, and IoT systems, which weren’t sufficiently addressed in FIPS 140-2.
- Improved Documentation: FIPS 140-3 provides more stringent documentation requirements, ensuring that cryptographic modules are properly vetted and validated.
Core Differentiation Factors Between Both Compliances
| Category | FIPS 140-2 | FIPS 140-3 |
|---|---|---|
| Standard Reference | Based on ISO/IEC 19790:2006 | Based on ISO/IEC 19790:2012 |
| Security Levels | Four security levels (1-4) | The same four security levels with refined criteria |
| Entropy Requirements | Not explicitly defined | Stronger entropy requirements for key generation |
| Physical Security | Emphasis on tamper-evidence and tamper-resistance | Improved physical security mechanisms and modernized testing |
| Module Authentication | Limited to passwords and simple authentication | Multi-factor authentication for high-security levels |
| Software Security | Basic software integrity checks | More stringent requirements for software integrity and self-tests |
| Operational Environment | Defined in broad terms | Stricter requirements for virtualized environments and firmware updates |
| Non-Invasive Attacks | Addressed only at high-security levels | More comprehensive testing for side-channel attacks (SPA, DPA, etc.) |
| Approved Algorithms | Supports older algorithms | Supports post-quantum cryptographic readiness and modern cryptographic algorithms |
| Testing & Certification | Separate testing and documentation process | Aligned with ISO/IEC 24759, reducing redundancy in testing |
| Maintenance & Updates | More rigid process for updates and changes | Improved module revalidation and change management |
| Applicability | Focus on hardware modules | Broader coverage, including hybrid and cloud environments |
| Transition Deadline | Still valid for existing deployments | Required for all new cryptographic modules post-transition deadline |
For organizations already compliant with FIPS 140-2, transitioning to FIPS 140-3 will involve updating systems, processes, and documentation to meet the new security requirements.
The Key Components of FIPS Compliance
Achieving FIPS compliance is not just about passing a test, it requires a well-planned approach to secure design, implementation, and management. Let’s break down the essential components of FIPS compliance:
1. Cryptographic Module Design and Security
FIPS compliance begins with the design of your cryptographic module. FIPS requires cryptographic modules, whether hardware or software, to adhere to specific security principles, including:
- Access Control: Ensuring that only authorized personnel can interact with the cryptographic module.
- Authentication: Secure authentication mechanisms to verify the identity of users accessing the cryptographic system.
- Audit Trails: Monitoring access and usage of the cryptographic module to detect any unauthorized activity.
- Key Management: Safely generating, storing, and destroying cryptographic keys to ensure their confidentiality and integrity.
2. Approved Cryptographic Algorithms
FIPS sets stringent requirements for the use of cryptographic algorithms. These algorithms must have been validated by NIST to meet the Security Requirements for Cryptographic Modules.
Some of the most widely used approved algorithms include:
- AES (Advanced Encryption Standard): A symmetric encryption algorithm used for securing sensitive data.
- RSA: A widely used asymmetric encryption algorithm for secure communications.
- SHA (Secure Hash Algorithm): A family of cryptographic hash functions used for data integrity.
- HMAC (Hash-based Message Authentication Code): Used to ensure data integrity and authenticity.
FIPS-compliant systems must ensure that these algorithms are implemented correctly and used appropriately.
3. Key Management Procedures
Key management is a critical component of FIPS compliance. The way cryptographic keys are generated, stored, used, and destroyed directly impacts the security of the cryptographic module. FIPS requires that cryptographic modules:
- Use secure key generation methods to ensure that keys are strong and resistant to cryptanalysis.
- Provide key storage mechanisms that prevent unauthorized access, typically using hardware-based solutions such as Hardware Security Modules (HSMs).
- Ensure that keys are properly destroyed when they are no longer needed to prevent leakage of sensitive data.
4. Physical Security Requirements
Physical security is another key consideration under FIPS compliance. FIPS 140-2 and FIPS 140-3 require that cryptographic modules be designed with tamper-evident or tamper-resistant features, which means that they must be able to detect and respond to physical attacks.
Common features include:
- Tamper seals: To indicate if the module has been physically tampered with.
- Tamper detection circuits: To monitor the physical state of the module and respond accordingly if tampering is detected.
5. Certification and Documentation
FIPS compliance requires that cryptographic modules be tested and certified by an accredited laboratory. This certification process involves validating the cryptographic module’s design, algorithms, key management, and physical security features against the criteria set forth in the standard.
In addition to certification, FIPS-compliant systems must have detailed documentation covering:
- The design and architecture of the cryptographic system.
- The security testing process, including test results and validation procedures.
- Key management and access control procedures.
This documentation serves as proof of compliance and must be made available for inspection during audits.
Key Differentiating Factors Between FIPS Compliance and FIPS Validation
| Category | FIPS Validation | FIPS Compliance |
|---|---|---|
| Definition | A formal certification process conducted by NIST to verify that a cryptographic module meets FIPS 140 standards. | A broader concept where an organization ensures its cryptographic systems adhere to FIPS 140 security standards without necessarily going through certification. |
| Scope | Specific to cryptographic modules (hardware/software) | Applies to entire systems, architectures, and operations that use FIPS-validated cryptographic modules. |
| Approval Authority | Requires CMVP (Cryptographic Module Validation Program) testing by NIST and CSE in Canada. | No direct approval by NIST; organizations self-assess or get external advisory to maintain compliance. |
| Testing Process | Involves rigorous testing at NIST-accredited labs (CSTL) | Focuses on aligning cryptographic policies, configurations, and operational security with FIPS requirements. |
| Certification Requirement | Yes, issued after passing lab tests and NIST review. | No formal certification, but adherence ensures security best practices. |
| Time & Cost | Expensive and time-consuming (6-24 months). | Faster and cost-effective; organizations can achieve compliance without waiting for certification. |
| Flexibility | Strict and limited to certified module versions only. | More flexible, allowing organizations to adapt FIPS-approved algorithms and configurations without undergoing validation. |
| Focus Areas | HSMs, encryption software, and cryptographic libraries. | System-wide implementation, ensuring proper use of FIPS-approved cryptography. |
| Updates & Changes | Requires re-certification for any significant modifications to a module. | Allows ongoing improvements and updates while maintaining compliance. |
| Who Needs It? | Vendors and manufacturers of cryptographic modules. | Organizations in regulated industries (government, finance, healthcare, etc.) must use FIPS-validated cryptographic tools. |
| Real World Example | A vendor submits their HSM or encryption software for FIPS 140-3 validation by an accredited lab. | A financial institution ensures all encryption services use FIPS-validated modules and follow best practices for implementation. |
How to Achieve FIPS Compliance: A Step-by-Step Process
Achieving FIPS compliance is a complex process that requires careful planning, testing, and certification. Below is a step-by-step guide for organizations seeking to achieve compliance with FIPS 140-2 or FIPS 140-3.
1. Conduct a Preliminary Assessment
The first step in achieving FIPS compliance is to assess your current cryptographic systems and identify any gaps in compliance. This step should include reviewing your cryptographic algorithms, key management procedures, and security controls to ensure that they align with the FIPS requirements.
2. Perform a Gap Analysis
Once the initial assessment is completed, perform a gap analysis to identify specific areas that need to be addressed to meet FIPS compliance. This might involve:
- Upgrading to approved cryptographic algorithms.
- Implementing additional security features for physical protection.
- Enhancing key management processes.
3. Develop a Compliance Roadmap
With the gap analysis complete, create a compliance roadmap that outlines the steps required to achieve FIPS certification. This roadmap should include:
- A detailed timeline for implementing necessary changes.
- Required testing and documentation.
- A clear plan for achieving certification.
4. Design and Implement FIPS-Compliant Systems
Based on the roadmap, update or design your cryptographic system to meet the specific security requirements outlined in FIPS. This may include:
- Implementing tamper-evident features and enhancing physical security.
- Updating or replacing cryptographic algorithms with FIPS-approved algorithms.
- Introducing a more secure key management infrastructure.
5. Certification and Testing
Once the system has been updated, it’s time to submit it for testing and certification. This involves submitting your cryptographic module to an accredited lab for evaluation.
Challenges and Considerations in FIPS Compliance
While FIPS compliance is a cornerstone of cryptographic security, it’s not without its challenges. Organizations often face significant hurdles when implementing and maintaining FIPS-compliant systems. Here’s a closer look at the limitations and constraints of FIPS standards:
1. Complexity and Time-Consuming Processes
One of the primary drawbacks of FIPS compliance is its prescriptive and complex nature. Achieving and maintaining certification requires:
- Rigorous testing and validation by accredited labs.
- Detailed documentation of cryptographic modules, algorithms, and key management processes.
- Ongoing audits and updates to ensure continued compliance.
This process can be time-consuming and resource-intensive, particularly for smaller organizations with limited cybersecurity expertise.
2. Narrow Focus on Encryption
FIPS standards are narrowly focused on cryptographic modules and encryption. While this ensures robust data protection, it doesn’t address other critical aspects of cybersecurity, such as:
- Network security.
- Endpoint protection.
- Threat detection and response.
Organizations must integrate FIPS-compliant solutions with broader cybersecurity measures to create a comprehensive defense strategy.
3. Performance and Compatibility Issues
FIPS compliance can introduce performance bottlenecks and compatibility challenges, especially in systems that handle both sensitive and non-sensitive data. For example:
- Applications may require multiple encryption modules but only calls involving sensitive data need to use FIPS-compliant modules.
- Routing all data through FIPS-compliant modules can slow down performance and increase complexity.
This adds to the development burden, as organizations must carefully document and manage which calls require FIPS compliance and which do not.
4. Legacy Systems and Non-Compliant Protocols
Many organizations rely on legacy systems or non-compliant protocols that don’t support FIPS-approved algorithms. This creates significant challenges, such as:
- Lack of Algorithm Support: Non-compliant protocols may not support FIPS-approved algorithms like AES or SHA-2.
- Integration Issues: Legacy systems may not be compatible with FIPS-compliant cryptographic modules.
To overcome these challenges, organizations can:
- Use cryptographic gateways or proxies to bridge the gap between non-compliant protocols and FIPS-compliant encryption.
- Implement key management solutions that adhere to FIPS requirements, even in non-compliant environments.
5. Ongoing Maintenance and Documentation
FIPS compliance isn’t a one-time effort, it requires continuous monitoring and updates. Organizations must:
- Regularly test cryptographic modules for vulnerabilities.
- Update systems to meet evolving FIPS standards (e.g., transitioning from FIPS 140-2 to FIPS 140-3).
- Maintain detailed documentation of compliance efforts for audits and reviews.
This ongoing commitment can strain resources, particularly for organizations with limited cybersecurity budgets.
6. Misconceptions About FIPS Compliance
A common misconception is that FIPS compliance can only be achieved by using FIPS-compliant protocols. However, this isn’t always the case. Organizations can achieve compliance by:
- Implementing FIPS-compliant cryptographic modules within non-compliant systems.
- Using cryptographic gateways to enforce FIPS-approved algorithms for sensitive data.
This approach allows organizations to maintain compliance while working with legacy systems or non-compliant protocols.
FIPS compliance is a critical component of data security, but it’s not without its limitations. By understanding these challenges and adopting strategic solutions, organizations can achieve compliance without compromising performance or compatibility.
Whether you’re working with legacy systems, non-compliant protocols, or complex applications, a thoughtful approach to FIPS compliance can help you protect sensitive data and meet regulatory requirements effectively.
Transitioning from FIPS 140-2 to FIPS 140-3
The transition from FIPS 140-2 to FIPS 140-3 marks a significant evolution in cryptographic standards. While FIPS 140-2 has been the benchmark for cryptographic module security since 2001, FIPS 140-3 introduces updated requirements to address modern cybersecurity challenges, including emerging threats like quantum computing.
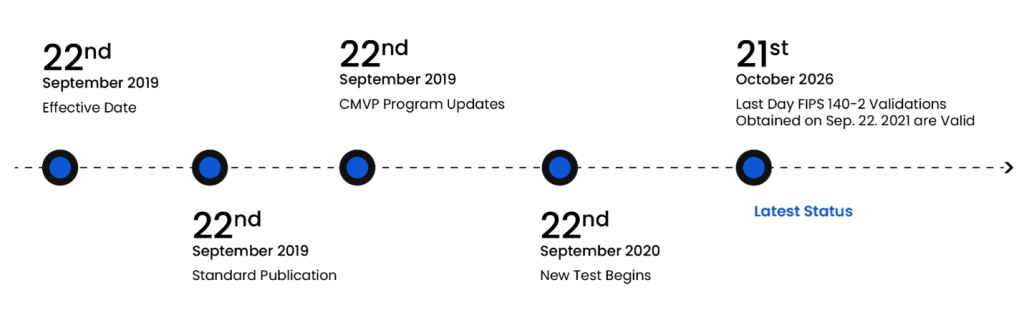
Transition Timeline
The transition from FIPS 140-2 to FIPS 140-3 has been a phased process. Below is a summary of the key milestones:
Challenges in Transitioning to FIPS 140-3
The transition from FIPS 140-2 to FIPS 140-3 presents several challenges for organizations:
1. Increased Complexity
FIPS 140-3 introduces stricter security requirements and more detailed documentation, which can be resource intensive.
2. Compatibility Issues
Legacy systems and non-compliant protocols may not support FIPS 140-3 requirements, requiring significant updates or replacements.
3. Ongoing Maintenance
FIPS 140-3 requires continuous monitoring, testing, and updates to maintain compliance.
4. Quantum Readiness Integrating post-quantum cryptographic algorithms can be complex and time-consuming
How to Prepare for the Transition?
To ensure a smooth transition to FIPS 140-3, organizations should:
- Conduct a Gap Analysis: Assess current systems to identify gaps in compliance.
- Update Cryptographic Modules: Replace outdated algorithms and modules with FIPS 140-3-compliant solutions.
- Enhance Documentation: Maintain detailed records of compliance efforts, including testing and validation.
- Invest in Training: Educate your team on FIPS requirements and best practices to streamline compliance efforts.
- Leverage Expert Guidance: Partner with cybersecurity experts to navigate the complexities of FIPS compliance.
- Adopt Hybrid Solutions: Use cryptographic gateways or proxies to integrate FIPS-compliant modules with non-compliant systems.
- Prioritize Key Management: Implement FIPS-compliant key management practices to ensure cryptographic keys are securely generated, stored, and destroyed.
The transition from FIPS 140-2 to FIPS 140-3 is a critical step in strengthening cryptographic security. While the process can be challenging, it’s essential for organizations to stay ahead of new and advancing threats like PQC and meet changing regulatory requirements.
By understanding the key changes, addressing challenges proactively, and leveraging expert guidance, organizations can successfully transition to FIPS 140-3 and ensure their systems are secure, resilient, and ready for the future.
Who Needs FIPS Compliance?
FIPS standards are often associated with federal agencies, but their scope extends far beyond government use. These standards are designed to ensure the security and integrity of sensitive data, making them relevant to a wide range of organizations and applications. Whether you’re a federal contractor, a state government, or a private sector company, FIPS compliance can play a critical role in your cybersecurity strategy. Here’s a look at the industries and sectors where FIPS compliance plays a vital role:
1. Government and Defense
- Federal Agencies: Government organizations are required to use FIPS-validated cryptographic modules to protect classified and sensitive information.
- Defense Contractors: Companies working on national security projects must comply with FIPS standards to ensure the integrity and confidentiality of defense-related data.
2. Healthcare
- Hospitals and Clinics: Protecting patient data is a top priority in healthcare. FIPS-compliant encryption helps organizations meet HIPAA requirements and keep sensitive health information secure.
- Health Tech Companies: Developers of electronic health records (EHR) systems, telemedicine platforms, and other health-related software rely on FIPS compliance to ensure their solutions are trustworthy and secure.
3. Finance and Banking
- Banks and Credit Unions: Financial institutions must secure customer data and transactions. FIPS-compliant encryption is often required to meet regulations like GLBA and PCI DSS.
- Fintech Companies: From mobile payment apps to cryptocurrency platforms, fintech companies use FIPS-compliant solutions to protect financial data and build user trust.
4. Technology and Cloud Services
- Cloud Service Providers: Companies offering cloud storage, SaaS, or IaaS solutions need FIPS-compliant encryption to meet customer expectations and regulatory requirements.
- IoT Device Manufacturers: With the rise of connected devices, FIPS compliance ensures that data transmitted by IoT devices remains secure and protected from cyber threats.
5. Retail and E-Commerce
- Online Retailers: Securing payment systems and customer data is essential for compliance with PCI DSS. FIPS-compliant encryption helps retailers protect sensitive information and prevent data breaches.
- Point-of-Sale (POS) Systems: Providers of POS systems rely on FIPS validation to ensure secure transactions and protect customer payment data.
6. Energy and Utilities
- Smart Grid Operators: Protecting critical infrastructure and customer data is a top priority for energy providers. FIPS-compliant solutions help secure smart grids and other utility systems.
- Oil and Gas Companies: From drilling operations to supply chain logistics, FIPS compliance ensures that sensitive data in the energy sector is protected from cyber threats.
7. Manufacturing and Industrial Systems
- Industrial IoT (IIoT): Manufacturers using connected devices in their operations need FIPS-compliant encryption to protect data and ensure the integrity of their systems.
- Supply Chain Security: Companies must safeguard sensitive supply chain data, and FIPS-validated cryptographic modules provide a reliable way to do so.
8. Education and Research
- Universities and Research Institutions: Handling sensitive research data or student information requires robust security measures. FIPS compliance helps educational organizations protect their data and maintain trust.
- EdTech Providers: Developers of online learning platforms and educational software use FIPS-compliant solutions to ensure user data is secure and protected.
9. Telecommunications
- Telecom Providers: Securing communication networks and customer data is critical for telecom companies. FIPS-compliant encryption helps meet regulatory requirements and protect sensitive information.
VoIP and Messaging Platforms: Providers of communication tools rely on FIPS compliance to ensure end-to-end encryption and protect user privacy.
How Encryption Consulting Can Help?
Navigating FIPS compliance can feel overwhelming, but you don’t have to do it alone. At Encryption Consulting, we make the process simpler and more efficient, helping you understand where your cryptographic systems stand, identifying gaps, and creating a clear plan to achieve compliance with FIPS 140-2 and transition to FIPS 140-3. Whether you’re upgrading cryptographic modules, ensuring proper documentation, or maintaining ongoing compliance, our experts guide you every step of the way, reducing risks, avoiding delays, and minimizing disruption to your operations. Our goal is to take the stress out of compliance so you can focus on what matters most: keeping your data secure and your business moving forward.
Conclusion
Achieving FIPS compliance is a critical requirement for any organization handling sensitive information in industries like finance, healthcare, government contracting, and telecommunications. By following the steps outlined in this guide, organizations can ensure that their cryptographic systems meet the highest standards of security and integrity and are prepared to tackle the challenges.
If you are looking to achieve FIPS compliance, partner with a trusted encryption consulting firm that can provide the expertise and support you need to navigate this complex process successfully. With the right approach, FIPS compliance can become a seamless part of your organization’s operations, ensuring that your data remains secure and your organization stays compliant with changes.
- What is FIPS Compliance?
- Why is FIPS Compliance Crucial?
- Understanding FIPS 140-2 vs. FIPS 140-3
- The Key Components of FIPS Compliance
- Key Differentiating Factors Between FIPS Compliance and FIPS Validation
- How to Achieve FIPS Compliance: A Step-by-Step Process
- Challenges and Considerations in FIPS Compliance
- Transitioning from FIPS 140-2 to FIPS 140-3




