Securing Active Directory: Preventing Privilege Escalation via AD CS


The data security industry is one of the most rapidly advancing sectors in the world and with these constant advancements, the risks of vulnerabilities continue to rise. It is crucial for organizations to take a proactive approach to data protection by not just assessing but also effectively managing these vulnerabilities in order to enhance security against cyber threats.
One such serious vulnerability exists within Active Directory Certificate Services (AD CS) that attackers can exploit. This vulnerability provides a backdoor for attacks to elevate their privileges from a Child Domain Admin to an Enterprise Admin level across the entire forest.
Our blog gives you all the information you need about the vulnerability within AD Certificate Services (AD CS) that can be exploited to elevate Domain Admin privileges. We’ll explore methods to eliminate this risk by understanding the vulnerability to help you protect your AD environment.
The first step is to build a good understanding of the AD structure. This attack specifically targets Active Directory with a forest containing a parent domain (also called the root domain) and one or more child domains.
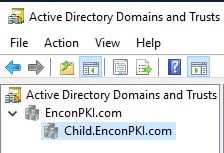
In this example scenario, the environment contains two domains:
Note: The Parent Domain (EnconPKI.com) is set up with a fully functional AD CS PKI Environment, while the Child Domain (Child.EnconPKI.com) contains only a writable Domain Controller.
The exploit begins with an attacker gaining initial access to a system within the network. If this compromised system belongs to a user with domain admin privileges for a child domain, the attacker could potentially elevate their access to Enterprise Admin privileges across the forest.
This compromise could grant them complete control over the entire Active Directory environment, including the ability to:
Here’s a detailed explanation of each step involved in this exploit:
First, the attacker tries to establish initial access to the network. This could be achieved through various means, such as phishing campaigns, exploiting software vulnerabilities on a user’s machine, or compromising a low-privileged account. For this attack to work, the compromised account must have ‘write’ access to a writable domain controller (DC) within a child domain.
Once the attacker has ‘write’ permission to a DC in the child domain, they can leverage the ‘System’ account’s excessive permissions within the Active Directory Configuration Naming Context. This vulnerability allows them to create a new rogue Certificate Authority (CA) within the child domain. This fraudulent CA appears legitimate to other machines within the domain, allowing the attacker to issue malicious certificates later.
Here’s a detailed breakdown of how the attacker deploys the rogue CA using PowerShell on the compromised DC:
Search for “PowerShell” in the Start Menu
Note: You might be prompted for your administrator credentials. Enter the username and password for the compromised account with administrative privileges.
Once PowerShell opens in a new window, you can verify if you have elevated privileges:
Alternatively, you can run the following command.
`Get-ExecutionPolicy`
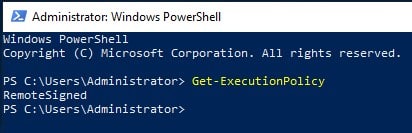
If the output displays “RemoteSigned” or “Bypass”, you have elevated privileges. If it shows “Restricted” or “AllSigned”, you won’t be able to execute the commands needed to deploy the fraudulent CA.
The following command installs a new Enterprise Root CA on the compromised DC:
Execute the following cmdlet command in the PowerShell window:
`Install-WindowsFeature AD-Certificate, ADCS-Cert-Authority -IncludeManagementTools`
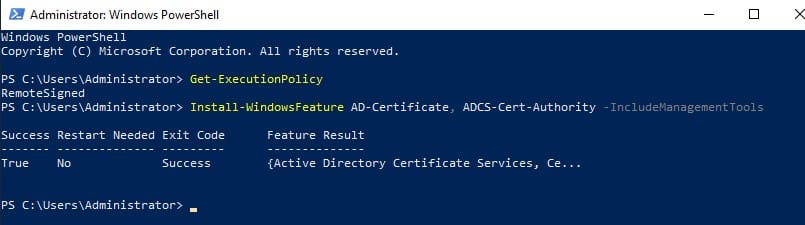
This command will install the required Active Directory Server roles and features on the System.
Next, execute the following command in the PowerShell window:
`Install-AdcsCertificationAuthority -CAType EnterpriseRootCA -CACommonName “Fraudulent CA”`
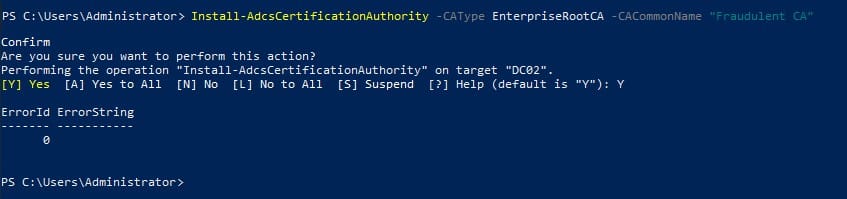
Verify the CA using pkihealth.msc tool and AD Containers.
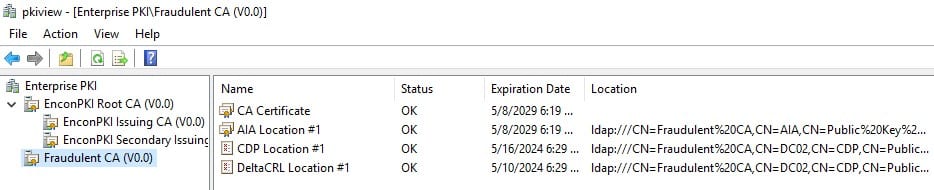
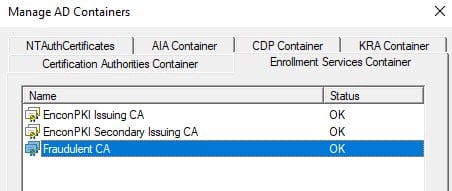
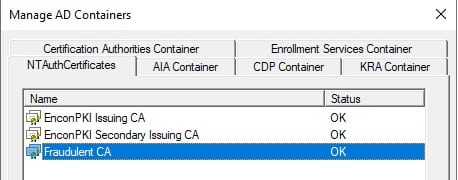
The CA has been successfully registered as an Enrollment Service in the AD Container. The rogue CA has established trust within the Active Directory forest, allowing any member – users, computers, and even other domain controllers – to request certificates from it.
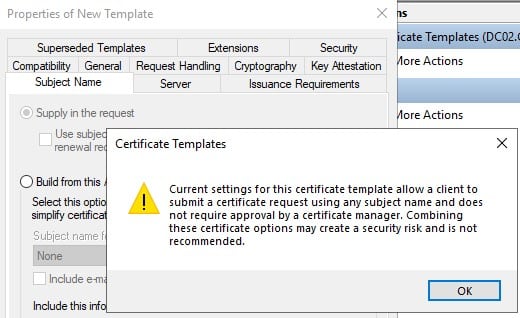
Once the fake CA is established, the attacker can design a malicious certificate template and manipulate it to grant themselves elevated privileges, such as mimicking an Enterprise Admin account.
Here’s how the attacker can create a Malicious Certificate Template:
From an elevated PowerShell prompt, type `certtmpl.msc` and press Enter.
Select “Duplicate Template”.
This creates a copy of the default user template that the attacker can modify for malicious purposes.
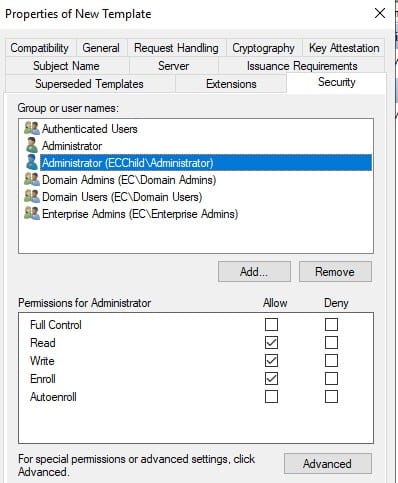
The attacker will now focus on configuring two specific tabs within the newly created template properties:
Add the account if required and provide all permissions – ‘Read’, ‘Write’ and ‘Enroll’.
A Warning Alert appears specifying the risk associated with these settings. Since we are simulating the attacker’s steps, we can continue. Click ‘OK’.
Expand the current CA and right-click on Certificate Templates.
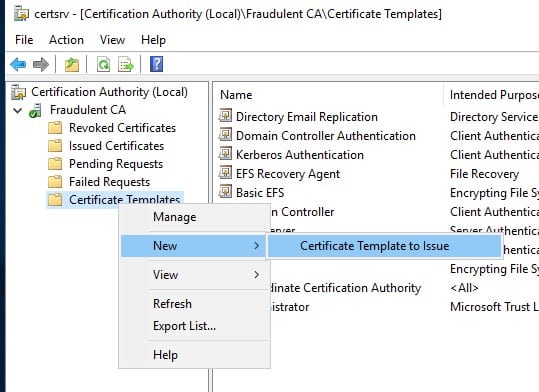
Select the malicious certificate template and click on OK.
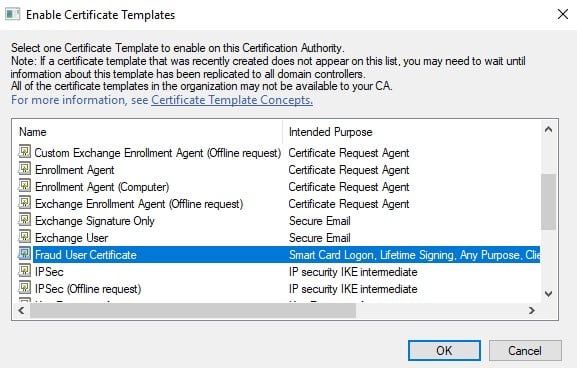
Note: Attackers often use the built-in “Domain Controller” template for enabling smart card logon functionality across an entire forest. Here’s why:
By creating a malicious certificate template, the attacker lays the groundwork for issuing a certificate that grants them unauthorized access. They can potentially use this certificate to impersonate a privileged user and gain control over critical domain resources.
Using the compromised DC, the attacker can issue a certificate signed by the fake CA. This certificate is intended to look like it was issued for a legitimate Enterprise Admin account. The attacker can manipulate different certificate fields like the “Subject” (which identifies the certificate holder) to mimic a real Enterprise Admin account.
The following steps are used by the attacker to issue the malicious certificate:
In the “Available snap-ins” list, select “Certificates” and click “Add”.
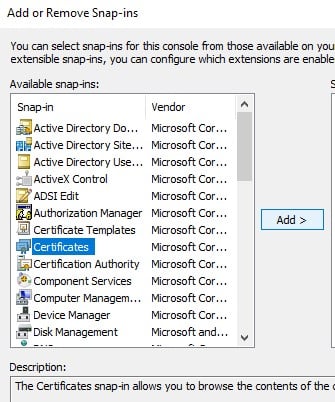
Now you should see the “Certificates” snap-in listed in the MMC console tree.
Go to All Tasks, Select “Request New Certificate…”
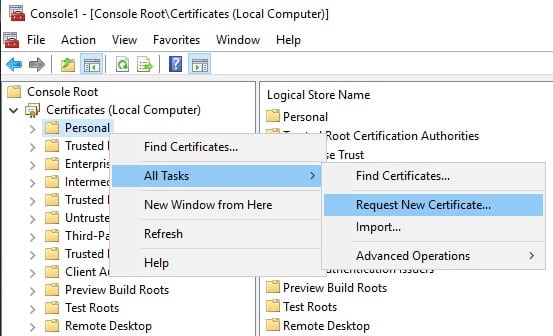
Navigate through the wizard, “Request Certificates” action is encountered.
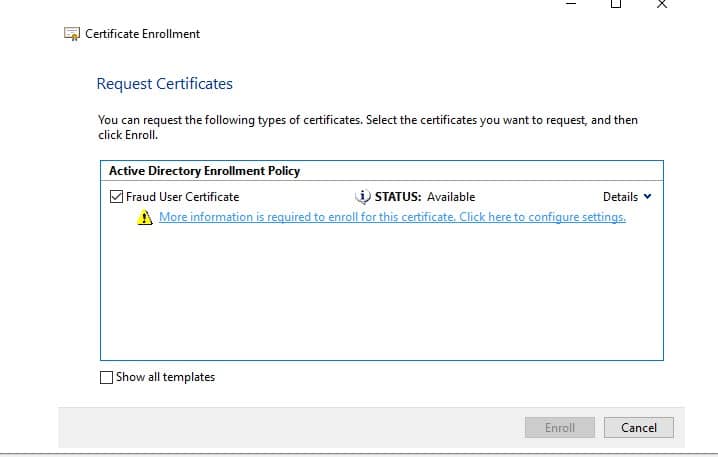
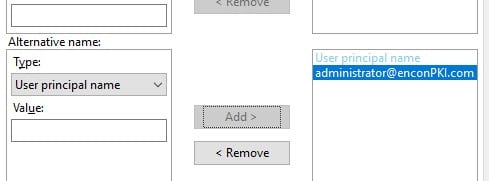
Under Subject tab, in Alternative Name box add “User Principal Name” and set the value to be target account’s UPN.
The format must be [email protected]
Once the certificate request is processed, it will appear under the Personal Certificates.
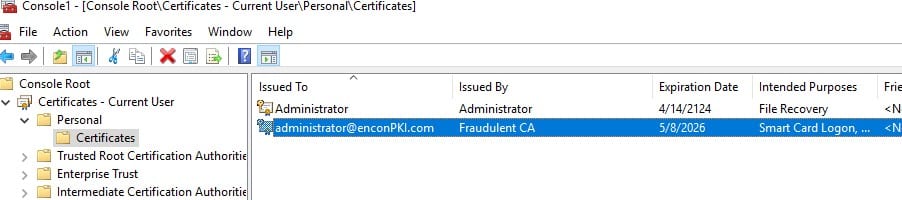
Right-click on the newly issued certificate and select “All Tasks” -> “Export”.
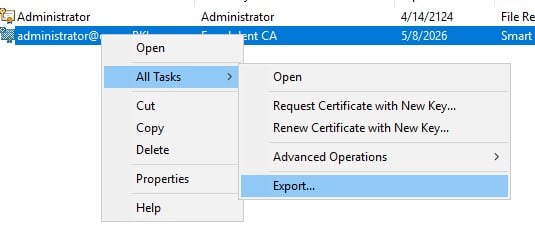
Choose the PKCS#12 (.PFX) format for exporting the certificate and private key together. You’ll need to provide a strong password to protect the exported file.
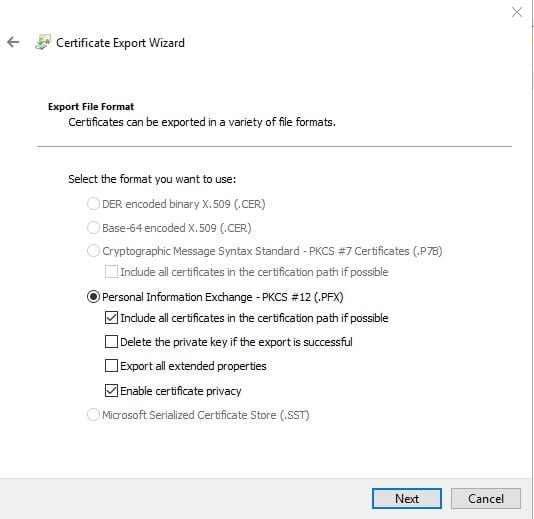
Now, the attacker has a certificate file that appears legitimate and impersonates a privileged Enterprise Admin account.
Now the attacker can leverage this forged certificate to gain unauthorized access to domain resources. Since the certificate appears legitimate and signed by a seemingly trusted CA (the Fraudulent CA), the attacker can potentially bypass security measures and access resources typically restricted to Enterprise Admins. This allows them to move laterally within the network, steal sensitive data, or disrupt critical operations.
This attack exploits the default configuration of AD CS, where the “System” account has full control permissions within the Active Directory Configuration NC. This excessive permission allows attackers with “write” access to a DC to manipulate critical AD objects with elevated privileges.
There are so many preventative actions that one can take to protect their AD defenses and prevent these exploits. Here are the most common and effective steps you can take to protect your AD environment today:
It is important for us to remember that these continuous advancements in technology will also leave room for vulnerabilities within the environment and the most effective long-term strategy is one where organizations like yours adopt a proactive approach by continuously monitoring your infrastructure, assessing the vulnerabilities, and minimizing risks factors.
So, always remember to continuously monitor your architecture and include strong authentication, permission control, network segmentation, and user education in your security strategy to render such external attacks ineffective.
At Encryption Consulting, we specialize in helping organizations like yours identify and mitigate security risks through tailored PKI Assessments. Our team of experts can provide a customized strategy to protect your PKI architecture from emerging threats, ensuring your data and infrastructure remain secure.
Our full range of Public Key Infrastructure (PKI) services helps you safeguard your digital assets and enhance your organization’s overall security posture,
For those seeking a hands-off solution, our PKI as a Service (PKIaaS) delivers all the benefits of PKI without the burden of in-house management. We ensure to provide four parameters:
With Encryption Consulting’s PKIaaS, you can focus on your core business while we handle the complexities of PKI management. Let us provide the peace of mind that comes from knowing your digital trust and security needs are in expert hands. Reach out today at [email protected] to explore how we can help your organization stay secure against cyber threats.