The recent development of quantum computing signals an important shift in cybersecurity and presents a serious threat to established encryption techniques. As enterprises become more reliant on digital communications, the need to use post-quantum cryptography (PQC) methods has become essential. The National Institute of Standards and Technology (NIST) has indicated that algorithms such as RSA-2048 and ECC-256 are expected to be officially deprecated by 2030, with a complete phase-out of legacy cryptography anticipated by 2035. While large-scale quantum computers aren’t here yet, it’s only a matter of time. And when they do arrive, they could make today’s encryption methods useless. That’s why it’s so important for organizations to start preparing now. Building a solid post-quantum cryptography (PQC) readiness plan today can help ensure your digital assets stay protected in the quantum future.
While post-quantum computing promises accelerated computing power for scientific research and industry, it threatens the security of many cryptographic algorithms today. While you may not have all the time in the world to view white papers one after another, we have gathered a quick overview of the background, methods, and advice to help you understand where to start your journey to post-quantum readiness.
Understanding the Post-Quantum Threat
Quantum computers might not yet be powerful enough to break today’s cryptographic systems, but their fast-paced progress in recent years has sparked serious concern. Algorithms like RSA and Elliptic Curve Cryptography (ECC) are the foundation of internet security; they keep our online transactions safe, protect sensitive information, and ensure digital signatures are valid. As quantum technology continues to evolve, the security of these foundational systems is increasingly at risk. In fact, 63% of organizations believe that quantum advancements could eventually break the encryption methods we rely on today. On top of that, 61% see key distribution as one of the biggest challenges we’ll face in a world where quantum computers are a reality.
Post-quantum computing introduces newer quantum threats to the cryptographic systems that we currently rely on. Shor’s algorithm can efficiently factor large numbers, breaking the foundation of RSA and ECC. A key like RSA-2048, which is considered secure right now, could be cracked by a powerful enough quantum computer, exposing any data it protects. Grover’s algorithm, which speeds up brute-force attacks. It doesn’t completely break symmetric encryption like AES, but weakens it. For instance, AES-128 would only offer about 64 bits of security in the face of a quantum attack, cutting its strength in half.
In addition to these algorithmic risks, the “harvest now, decrypt later” approach is dangerous because attackers can gather encrypted data now in anticipation of future quantum decryption capabilities. Around 58% of organizations are concerned about the risk of “harvest now, decrypt later” attacks, where adversaries collect encrypted data today with the intention of decrypting it in the future when quantum capabilities become available. What’s more, post-quantum computing could make existing vulnerabilities even more dangerous. Attacks like side-channel and key recovery attacks might become more effective, giving attackers new ways to break into cryptographic systems. Side-channel attacks work by picking up on indirect clues, like how long a process takes or how much power it uses, to steal sensitive information. These techniques can even target post-quantum algorithms. Key recovery attacks take this a step further by using those signals to extract secret keys, posing a serious threat to the security of future cryptographic systems.
In light of these threats, organizations must recognize that any information transmitted via public channels today is vulnerable to eavesdropping without quantum-safe cryptography. Data that appears secure now could be preserved for future decryption, undermining the validity and integrity of transmitted information. The threat extends across the entire cybersecurity ecosystem, impacting communication protocols like TLS, IPSec, SSH, identity certificates, code signing, and key management protocols.
How to plan for PQC migration and its challenges?
As we get closer to quantum computers becoming a reality, we can’t afford to wait until they’re fully developed to start preparing. To establish the best defense, we must protect sensitive data and ensure compliance before current cryptographic systems become outdated. Crypto-agility, the ability to quickly swap out cryptographic algorithms without overhauling your entire infrastructure, can be one of the best key strategies. Here’s how organizations can start preparing for a smooth shift to post-quantum cryptography (PQC):
Key Steps for PQC Migration
To effectively prepare for the transition to post-quantum cryptography, consider the following steps:
- Assess Quantum Risks: Start by identifying cryptographic vulnerabilities and prioritizing high-risk applications for quantum-safe upgrades.
- Identify Critical Data: Pinpoint the sensitive data and systems that must be protected first. Prioritize anything that must remain secure for years to come.
- Track PQC Standards: Follow updates from NIST and other standardization bodies to stay aligned with the latest recommendations for post-quantum algorithms.
- Enable Crypto-Agility: Ensure your systems are flexible enough to support new cryptographic algorithms. This will make the transition to quantum-safe cryptography much easier down the line.
- Implement in Phases: Don’t try to do everything at once. Migrate in stages to reduce risk and ensure that each step is thoroughly tested and implemented.
Challenges Ahead
Quantum computers capable of breaking current cryptography do not exist publicly yet, but experts estimate their arrival within the next decade.
- Long-term Data Security: Data with long confidentiality requirements (e.g., government secrets, healthcare records) is at risk of “harvest now, decrypt later” attacks.
- Complex Migration: Cryptography is deeply embedded in software, hardware, protocols, and infrastructure. Migration to PQC is a massive engineering effort.
- TLS protocol transition: TLS protocols must be updated to NIST-approved, quantum-resistant algorithms to prevent unauthorized individuals from reading, modifying, or intercepting your data.
- Compliance and Regulation: Businesses must comply with new regulations to implement more quantum-safe methods.
- Standardization Progress: The National Institute of Standards and Technology (NIST) has been evaluating and standardizing post-quantum algorithms since 2016, has already published the initial set of PQC algorithms in FIPS 203, 204, and 205 in July 2024, and continues to evaluate additional candidates for future standardization.
While the shift to PQC is critical, alternative technologies such as Quantum Key Distribution (QKD) provide an alternative route to secure communication. QKD uses the principles of quantum mechanics to distribute cryptographic keys. One of the major advantages is its ability to detect eavesdropping. Any attempt to intercept the key disturbs the quantum states and alerts the communicating parties about a potential breach. However, because QKD focuses on key distribution, it cannot fully replace all cryptographic requirements. Therefore, an extensive security strategy may involve a combination of PQC for general encryption and QKD for specific high-security key exchange scenarios.
NIST-Selected Post-Quantum Algorithms
In July 2024, NIST announced the first set of standardized post-quantum cryptographic algorithms. These algorithms are designed to resist attacks from both classical and quantum computers.
| Algorithms | CRYSTALS-Kyber (ML-KEM) | CRYSTALS-Dilithium (ML-DSA) | FALCON (FN-DSA) | SPHINCS+ (SLH-DSA) | HQC (Hamming Quasi-Cyclic) |
|---|---|---|---|---|---|
| Overview | CRYSTALS-Kyber is a Module-Lattice-based Key-Encapsulation Mechanism (ML-KEM). It’s based on the hardness of solving the Module Learning With Errors (MLWE) problem over structured lattices. | CRYSTALS-Dilithium is a Module-Lattice-based Digital Signature (ML-DSA) scheme. It’s based on the hardness of solving the Module Learning With Errors (MLWE) and Module Short Integer Solution (MSIS) problems over structured lattices. | FALCON is a lattice-based signature scheme based on the Fast Fourier Orthogonal Lattice Construction. It leverages the algebraic structure of lattices to achieve very compact signatures. | SPHINCS+ is a stateless hash-based signature scheme. This means it doesn’t require maintaining any internal state between signature operations, making it more resilient to certain attacks and easier to deploy in some situations. | HQC is a code-based public key encryption scheme that relies on the hardness of decoding random linear codes, specifically using quasi-cyclic codes to enhance efficiency. |
| Use Cases | General-purpose key exchange, similar to RSA or Diffie-Hellman, is suitable for protecting the confidentiality of data in transit. | Digital signatures for authentication and non-repudiation ensure data integrity and authenticity. | Digital signatures where small signature sizes are critical, such as in bandwidth-constrained environments or when storing signatures is expensive. | Digital signatures are particularly useful in environments where resistance to side-channel attacks is paramount or where simplicity of implementation is desired. | General-purpose encryption is suitable for secure data transmission and storage, providing confidentiality and integrity for sensitive information. |
| Replaces | RSA, Diffie-Hellman, ECC (ECDH and X25519/448) for key exchange. | RSA, ECDSA, EdDSA (specifically, ECDSA with NIST curves and Ed25519/448) for digital signatures. | RSA, ECDSA, EdDSA (for digital signatures) in scenarios where signature size is a primary concern. | RSA, ECDSA, EdDSA (for digital signatures) in scenarios where side-channel resistance is a major concern. | RSA and ECC (specifically, schemes like ECDSA and ECDH) for public key encryption and digital signatures. |
| Technical Details | Kyber operates in a key encapsulation mechanism (KEM) framework, where the sender generates a random key, encapsulates it using the recipient’s public key, and sends the ciphertext to the recipient. The recipient then uses their private key to decapsulate the key. | Dilithium uses a “commit-and-open” approach, where the signer commits to a value, then reveals part of it based on a challenge derived from the signed message. | FALCON uses a trapdoor function based on the Shortest Integer Solution (SIS) problem on lattices. | SPHINCS+ is based on a Merkle tree structure and uses hash functions as its primary building blocks. | HQC works by producing a public-private key pair, with the public key extracted from a random linear code. By encoding the plaintext message with a random error vector, encryption creates a ciphertext that may be transmitted to the destination. To ensure safe communication, the recipient decrypts the ciphertext and recovers the original message using their private key. |
Each algorithm provides a distinct set of parameters to reach different levels of security. You can focus on selecting a set of parameters that satisfies your application’s unique security needs. Depending on the platform and implementation, these algorithms’ performance can change. Benchmarking is essential to determine the best algorithm for your needs. While some algorithms are relatively easy to implement, others may require specialized expertise.
This information is based on the current understanding of these algorithms. As research progresses, new findings that could affect their security or performance may emerge.
Establish a quantum readiness roadmap.
Industry professionals acknowledge that we are at a crucial turning point in the shift towards post-quantum cryptography (PQC). With NIST’s announcement of the PQC algorithm finalists and the recent finalization of key algorithms, many businesses and vendors are starting to strategize their migrations. As organizations assess the potential impacts of these changes, it is essential to take proactive measures to stay ahead in this evolving landscape. Regulatory bodies worldwide also emphasize the importance of immediate preparation to ensure compliance and security in an evolving digital landscape.
Developing an effective PQC readiness plan requires a blend of strategic foresight, technical assessment, and operational discipline.
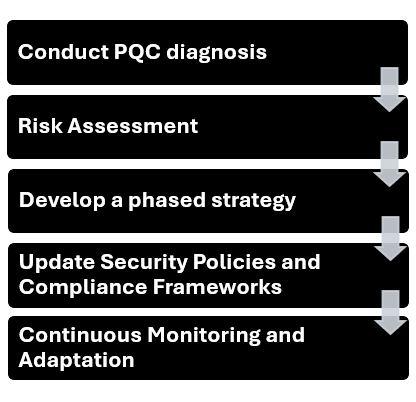
1. Prepare a Cryptographic Inventory
It is crucial to understand where and how cryptography is utilized within your organization. This involves creating a detailed cryptographic inventory to identify quantum-vulnerable technology and associated data criticality. This inventory will:
- Enable planning for risk assessment processes to prioritize migration to PQC.
- Help prepare for a transition to a zero-trust architecture.
- Help identify or correlate outside access to datasets, as those are more exposed and at higher risk.
- Inform future analysis by identifying what data may be targeted now and decrypted when a CRQC is available.
Specifically, this diagnosis should include:
- Discovery of algorithms currently in use (RSA, ECC, AES, etc.) across all IT and OT systems, along with documentation of all applications, devices, systems, and processes that rely on cryptography.
- Identifying all machine identities, including TLS certificates, SSH keys, and code signing credentials, along with the protocols they use and the applications that depend on them.
2. Risk Assessment
Once you have done your crypto discovery, the next step is to evaluate the state of your current environment to identify risks and gaps. A risk assessment helps identify the list of applications, algorithms that can be affected by quantum computing. It is important to note that not all data and systems face equal risk. Prioritize risk to your assets by data sensitivity and lifespan, exposure, compliance, and legal requirements.
3. Develop a phased strategy
PQC readiness is not a one-time fix, but a phased process.
- Hybrid Cryptography: Begin by implementing PQC algorithms alongside classical ones to maintain compatibility and test effectiveness without disrupting existing services.
- Algorithm Selection: Based on finalized NIST standards and organizational requirements, select suitable algorithms (e.g., CRYSTALS-Kyber for encryption, CRYSTALS-Dilithium for signatures).
- Pilot Deployments: Start with less critical applications or test environments to validate functionality, performance impact, and interoperability.
- Vendor and Partner Engagement: Collaborate with vendors and service providers to understand their PQC support timelines and coordinate upgrades.
4. Update Security Policies and Compliance Frameworks
Your organization’s governance should evolve alongside technical changes to adapt to PQC.
- Revise encryption and key management policies to incorporate quantum-safe algorithms.
- Define criteria and timelines for deprecating vulnerable crypto algorithms and applications.
- Ensure all contracts and service-level agreements require PQC readiness.
- Monitor and adapt to emerging quantum-related regulatory mandates.
5. Continuous Monitoring and Adaptation
The initial transition might be done, but it is important to look out for updates and progress in the field of PQC. Look out for any advancements, track updates in PQC regulations and standards, regularly train your staff to maintain expertise and awareness, and reassess and update strategies periodically to incorporate new advancements.
Challenges to anticipate
The path to PQC readiness might not be a smooth one, and it can present several complex challenges:
1. Technical Challenges
-
Performance Considerations
- PQC algorithms typically require more computational resources, memory, storage, and communication capabilities because they usually have larger key sizes and more complex algorithms. Research is required to understand and measure the performance implications in different deployment scenarios.
- A larger key size can impact packetization and latency patterns in secure communication protocols such as TLS, thus affecting the network devices optimized for the current cryptography protocols (such as routers, switches, firewalls).
- More research will have to be conducted to optimize the performance of particular PQC algorithms, including the investigation of parallelism, better memory access performance, and new data structures.
-
Implementation Considerations
- PQC algorithm implementations can be made difficult by the complexities of converting mathematical algorithms into platform-specific designs.
- Many devices, mainly IoT devices, have limitations on power availability, memory, and computing power. More research is needed to understand how PQC algorithms may be efficiently carried out under such restrictions while retaining side-channel resistance.
2. Operational Challenges
-
Limited Visibility into Cryptographic Assets
- Organizations rarely have full visibility into their cryptographic landscape, which makes it harder to find and fix vulnerabilities. It is crucial to know where and how cryptography is employed to plan the migration towards PQC, which can only be achieved by creating a cryptographic inventory./li>
- Without a clear inventory, it will be hard for organizations to prioritize risk assessments and identify the systems and processes most vulnerable to quantum threats.
-
Transition to Zero Trust Architecture
- As organizations migrate to PQC, they may also need to transition to a zero-trust architecture. This would therefore require a reevaluation of how access controls and security protocols are defined, which can itself pose very real operational challenges.
3. Security Considerations
-
New Security issue
- PQC introduces new security challenges due to their new properties and requirements. Compared to other algorithms such as RSA and ECC, PQC counterparts are provided with different trade-offs, primarily key size and computational time. This increases the difficulty of evaluating their security effectively.
- To comprehend the security trade-offs of different PQC algorithms across diverse usage domains, more research is required. This involves looking at threat models, possible weaknesses in certain algorithms, and the consequences of side-channel vulnerabilities that might result from new communication and memory consumption patterns.
-
Adversarial Threat
- PQC algorithms have the potential to introduce new attack vectors, such as memory-based attacks, timing attacks, and differential fault analysis.
Crypto Agility
As you prepare to build a PQC readiness plan for your organization, crypto agility should be an important concept. Crypto agility refers to the ability of an organization to quickly adapt its cryptographic algorithms and protocols in response to emerging threats, vulnerabilities, or technological changes. Crypto agility allows organizations to respond to quantum threats, as organizations with crypto agility can swiftly transition to stronger, quantum-resistant algorithms without extensive fallbacks, mitigate risks by maintaining flexibility in cryptographic choices, and enhance security posture by regularly updating cryptographic practices.
To achieve crypto agility, organizations should design systems with architectures that allow for easy swapping of cryptographic algorithms. Organizations can also implement automated key management systems to accommodate new algorithms and key sizes as they are adopted.
How can Encryption Consulting Help?
Using NIST-aligned planning, focused risk reduction, and deep crypto discovery, our PQC Advisory Services can transform your environment into an audit-ready, quantum-resilient infrastructure.
-
Comprehensive PQC Risk Assessment
We evaluate governance frameworks and optimize cryptographic processes, identifying vulnerabilities in encryption protocols and key management. Through discovery and inventory, we assess all cryptographic assets and their usage. We classify data and crypto assets by sensitivity, and apply protection measures customized to you. We work on analyzing the cryptographic risk exposure to deliver a report. The report will contain detailed gap analysis with mitigation strategies and recommendations to address each identified gap, all aligned with NIST’s post-quantum cryptography (PQC) standards.
-
Personalized PQC Strategy & Roadmap
To ensure strategic alignment, we assess organizational goals, risk tolerance, and the cryptographic environment. Our approach includes developing a phased PQC migration strategy aligned with business operations, defining governance frameworks, and planning hybrid deployment models for gradual adoption.
Deliverables consist of an extensive PQC strategy document, a cryptographic agility framework, and a phased migration roadmap with business-aligned timelines to address emerging quantum threats effectively.
-
Seamless PQC Implementation
We conduct real-world performance testing to evaluate the effectiveness of cryptographic solutions against quantum attack vectors. We create Proof of Concepts to validate quantum-resistant cryptographic methods. We do comprehensive data scanning and inventorying of cryptographic assets, followed by careful planning to ensure smooth, low-disruption transitions. This makes it easier to integrate quantum-safe cryptography, including hybrid cryptographic models seamlessly. Additionally, we resolve issues identified during pilot testing and integrate lessons learned into the overall implementation strategy.
You can greatly benefit from our service as we categorize data by lifespan and implement customized quantum-resistant protection for long-term confidentiality. We also provide enterprise-wide crypto strategies and remediation plans to mitigate risks from outdated or weak cryptographic algorithms. We facilitate seamless migration to post-quantum algorithms for lasting resilience.
We focus on developing a robust governance structure that specifies roles, responsibilities, ownership, and rules for cryptographic standards and processes in the post-quantum age. We emphasize developing crypto-agile PKI architectures that readily swap out cryptographic algorithms as new threats or standards arise.
Conclusion
The timeline for quantum computing is dynamic and evolving. If you have started to work on a plan to be prepared for the outcomes of this, you are on track; if you haven’t, it is high time to start working on it, as preparing for this isn’t optional. Building your PQC readiness plan enables a controlled, well-informed transition to quantum-safe cryptography, protecting your most valuable digital assets. This exhaustive journey requires continuous education, complete inventory and risk analysis, phased migration, rigorous testing, policy evolution, and persistent vigilance. Start early, collaborate broadly, and build your cryptographic resilience step-by-step.
If you are wondering where and how to start, Encryption Consulting is here to help you. You can count on us as your trusted partner in the PQC readiness process. The future of secure communication and data protection depends on today’s actions. Reach out to us at info@encryptionconsulting.com to build a plan that is fitted to your needs.




