- Development of Docker Content Trust: Addressing Docker Ecosystem Vulnerabilities
- Advantages of Docker Signing: Enhancing Security
- Understanding the Challenges and Limitations of Docker Content Trust
- Mitigating the Challenges of Docker Content Trust: EC's Approach
- Securing Docker Images using EC's CodeSign Secure
- Conclusion
Docker is an open-source platform that helps developers to automate application deployment, scaling, and management. Docker simplifies the process of managing applications by creating containers. These containers package code and dependencies so the software or application runs smoothly and reliably from one computing environment to another.
Docker containers are lightweight and standalone, meaning they can run anywhere: on your local machine, in a data center, in the cloud, or across a mixture of these environments. This portability and consistency make Docker a popular tool for developers and operations teams (DevOps) to collaborate, develop, ship, and run their applications.
On the other hand, Docker signing is a security feature that Docker provides known as Docker Content Trust (DCT). Docker Content Trust uses digital signatures to verify the integrity and publisher of all the data received from a registry over any channel
DCT is powered by Notary and The Update Framework (TUF), open-source projects designed to secure content distribution. When DCT is enabled, Docker signs images automatically during push operations and verifies images during pull operations. This ensures the authenticity, integrity, and freshness of your content.
In essence, Docker signing allows you to ensure the images you’re using in your containers are exactly what you expect them to be. This prevents tampering or corruption during transmission and ensures that third parties haven’t tampered with the images. This is critical in a security context, as it prevents unauthorized or malicious code from being added to your containers.
Development of Docker Content Trust: Addressing Docker Ecosystem Vulnerabilities
Docker Content Trust (DCT), which enables Docker signing, was created to respond to the necessity for enhanced security in the container ecosystem. The increasing use of containers and Docker images in development and deployment pipelines revealed potential vulnerabilities in the ecosystem that needed to be addressed.
Here are some of the main vulnerabilities that led to the development of Docker signing:
-
Image Authenticity
Before the Docker signing was introduced, it took much work to determine the authenticity of Docker images. Users could inadvertently download and use malicious or tampered images without realizing it.
-
Image Integrity
Without Docker signing, ensuring the Docker images hadn’t been tampered with during transmission or storage was hard. This meant that even if the original image was secure and legitimate, it could be modified and harmful.
-
Image Freshness
Without a system to ensure the freshness of Docker images, users could download and use outdated and potentially insecure images.
-
Supply Chain Security
As Docker and other container technologies became more popular, they began to be used in more complex and critical systems. This made the security of the supply chain – the series of processes involved in building, deploying and running Docker images – a critical concern. Without Docker signing, there was a lack of trust in the supply chain.
-
Trust On First Use (TOFU):
Before Docker signing, when you pulled an image you hadn’t pulled before, Docker would have no way of verifying its integrity or whether it had been tampered with.
These vulnerabilities can lead to serious security breaches. By introducing Docker signing and Docker Content Trust, Docker made a significant step towards enhancing the security of the Docker ecosystem and its supply chains. Now, users can be confident that the Docker images they download and use are authentic, unmodified, and up-to-date.
Advantages of Docker Signing: Enhancing Security
Docker Content Trust (DCT), which enables Docker signing, offers numerous benefits, particularly regarding the security and integrity of Docker images. Some of the key benefits of using Docker signing:
-
Image Authenticity
Docker signing ensures the images pulled from a registry are authentic. This means you can trust that the images you’re using were created by the entity they claim to be created by.
-
Image Integrity
Docker signing verifies that the images have not been tampered with during transmission or stored in the registry. This assures you that the Docker images you’re using are the exact images that were originally pushed to the registry.
-
Supply Chain Security
Docker signing enhances the security of your supply chain by ensuring that the images you’re using in your deployment pipelines are authentic and haven’t been tampered with. This is particularly crucial in enterprise environments where supply chain security is paramount.
-
Image Freshness
Docker signing ensures you’re using the most recent version of a Docker image. This prevents the use of outdated and potentially insecure images.
-
Compliance and Auditing
In industries where software must comply with specific standards or be auditable (for example, finance, healthcare, etc.), Docker signing provides a method for ensuring and demonstrating that the deployed software hasn’t been tampered with and is exactly what it’s supposed to be.
-
Prevent Man-in-the-Middle (MITM) attacks
Docker signing prevents MITM attacks. A MITM attack involves the attacker surreptitiously relaying and perhaps changing the message between two parties who think they are speaking directly to one another.
By ensuring the integrity, authenticity, and freshness of Docker images, Docker signing makes the Docker ecosystem much more secure, which is crucial as Docker and container technologies continue to play an increasingly important role in modern development and deployment pipelines.
Understanding the Challenges and Limitations of Docker Content Trust
While Docker signing or Docker Content Trust (DCT) provides many benefits, it also has some limitations and potential drawbacks that should be considered:
-
Complexity
Docker signing involves managing cryptographic keys, which can add complexity to your usage. This includes securely generating, storing, and using these keys. For large organizations with many developers, this could add substantial overhead.
-
Operational overhead
Using Docker signing requires changes to your existing workflows, including how you push and pull images. This can lead to extra operational overhead, particularly during the initial adoption phase.
-
Compatibility issues
Docker Content Trust is only sometimes compatible with all Docker commands and options, which can limit its usability in certain contexts.
-
Lost or compromised keys
If your private keys are lost, any images signed with them will also lose their trust. If your keys are compromised, attackers could sign malicious images as if they were you. Key management is, therefore, a crucial aspect of Docker signing.
-
Dependency on Notary Server
Docker Content Trust relies on a Notary server to manage the trust. This dependency creates a potential point of failure in your Docker workflow.
-
Increased build time
Docker signing can increase build times slightly, as it adds a step of signing the image during the build process.
-
Lack of granular control
Docker Content Trust operates at the level of the Docker image, but it doesn’t provide control or trust at the level of individual files or layers within an image. This means you can’t verify the integrity or authenticity of individual components of an image, only the image as a whole.
Despite these drawbacks, Docker signing remains a crucial security feature for many Docker users, particularly those in enterprise or other high-security contexts. As with any security tool, balancing the need for security against the operational overhead and complexity it introduces.
Mitigating the Challenges of Docker Content Trust: EC’s Approach
To overcome the drawbacks of Docker signing, we take several measures:
-
Simplifying Key Management
We leverage secure and automated key management solutions to reduce the complexity and risk of managing cryptographic keys. This can include hardware security modules (HSMs) or cloud-based key management solutions.
-
Training and Documentation
We provide thorough training and clear, concise documentation to our developers. This helps to mitigate the operational overhead associated with adopting Docker signing and ensures that everyone understands the process and its importance.
-
Regular Audits
We regularly audit our processes to ensure compatibility issues are resolved quickly. This ensures that Docker signing can be fully integrated into our workflows with minimal disruption.
-
Robust Key Recovery Process
We implement a robust key recovery process in case of lost keys. In addition, we limit the potential impact of compromised keys by using different keys for different images or groups of images, where feasible.
-
Failover Mechanisms
We establish failover mechanisms to ensure that our Docker workflows can continue functioning even if the Notary server is unavailable. This could involve setting up a secondary Notary server or leveraging Docker’s offline signing capabilities.
-
Optimizing Build Times
We continuously optimize our build process to offset any increase in build time due to Docker signing. This can include parallelizing builds or optimizing other parts of the build process.
-
Using Additional Security Measures
To supplement the image-level trust provided by Docker Content Trust, we use other security measures like scanning for vulnerabilities in Docker images, verifying the integrity and authenticity of base images, and adhering to best practices for Dockerfile and image creation.
By taking these measures, we can significantly mitigate the drawbacks of Docker signing and take full advantage of its security benefits.
Securing Docker Images using EC’s CodeSign Secure
There are certain prerequisites for Docker Image signing, those are:
-
Installing Cosign
# binary wget "https://github.com/sigstore/cosign/releases/download/v2.0.0/cosign-linux-amd64" mv cosign-linux-amd64 /usr/local/bin/cosign chmod +x /usr/local/bin/cosign # rpm Wget "https://github.com/sigstore/cosign/releases/download/v2.0.0/cosign-2.0.0.x86_64.rpm" rpm -ivh cosign-2.0.0.x86_64.rpm # dkpg Wget "https://github.com/sigstore/cosign/releases/download/v2.0.0/cosign_2.0.0_amd64.deb" dpkg -i cosign_2.0.0_amd64.deb -
Installing and Setting up Python and Docker
- sudo apt-get install docker.io
- sudo apt-get install python-is-python3
- sudo apt install python3-pip
- pip install docker
- sudo apt-get install -y docker-ce-rootless-extras
- sudo apt-get install -y dbus-user-session
- docker login
The next step is to check out the code from GitHub:
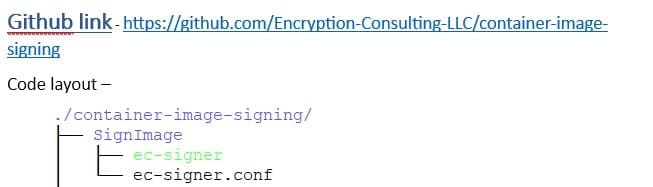
After that, perform the following steps:
- Open terminal.
-
Execute –
./ec-signer –project_name=<certificate name> --image_name=<target container> --docker_username=<your docker username> --docker_passwd=<your docker password>
Kubernetes has to be deployed to verify the Container Image, which can be done from here.
Now, deploy the following two services:
-
Image-validation-webhook
- Checkout the code from GitHub and then go to folder – ../VerifyImage/validating-webhook
- Open terminal
-
Execute –
sudo kubectl apply -f webhook-secret.yaml -
Execute –
sudo kubectl apply -f webhook-deploy.yaml -
Execute –
sudo kubectl apply -f webhook-config.yaml
-
verifyImage
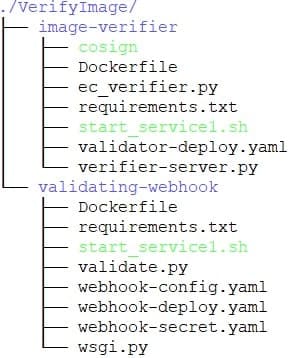
- Checkout the code from GitHub and then go to folder – ../VerifyImage/image-verifier
- Open terminal
-
Execute –
sudo kubectl apply -f validator-deploy.yaml
After the images are deployed successfully, execute the command:
sudo kubectl get pods –all-namespaces
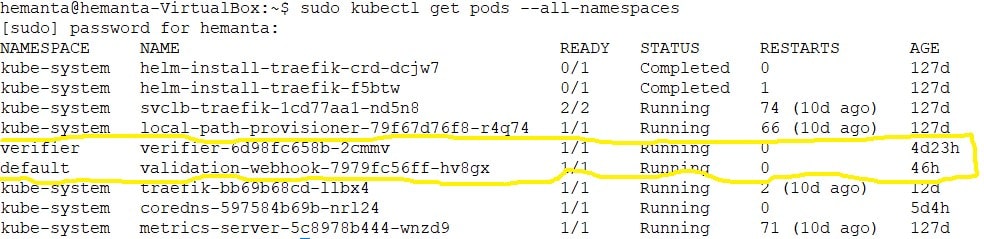
Note: For updating the codesigning server URL, docker username, docker password, edit validator-deploy.yaml located at ../VerifyImage/image-verifier.
Also, check out the demo of Docker Signing using our EC’s CodeSign Secure here.
Conclusion
In conclusion, Docker signing is a powerful tool for enhancing the security of Docker workflows. It’s a crucial aspect of Docker, particularly in high-security or enterprise contexts. Like any tool, it’s important to understand and manage its limitations, but the benefits it provides in terms of increased trust and security are substantial.
- Development of Docker Content Trust: Addressing Docker Ecosystem Vulnerabilities
- Advantages of Docker Signing: Enhancing Security
- Understanding the Challenges and Limitations of Docker Content Trust
- Mitigating the Challenges of Docker Content Trust: EC's Approach
- Securing Docker Images using EC's CodeSign Secure
- Conclusion




