Encryption and Decryption are the two most essential steps for successful communication. To transmit sensitive or confidential information, secrecy and privacy should be assured by a system. Before diving into Encryption and Decryption, let’s first learn about Cryptography.
What is Cryptography?
Cryptography is used to secure and protect data units during communication. It is an efficient step to prevent an unauthorized person or a group of unknown users from accessing or using sensitive information or data. Encryption and decryption are the two most common and essential functionalities of cryptography. The idea here is simple, to convert a normal message/data (plaintext) into a encrypted message so that it cannot be attacked in middle (man-in-the-middle attack). This encrypted message then decoded to the original message/data through decryption.
What is meant by Encryption?
Encryption is the process of transforming the original information into an unrecognizable form. Although it is unrecognizable, yet does not lose it’s original data but rather encrypted in a logical way so that the owner can decrypt it back to it’s original form. Now, this new message is entirely different from the original message using various algorithms like:
Triple DES
Triple-DES algorithm was designed to replace the official and original Data Encryption Standard (DES) Algorithm. This algorithm uses three individual 56-bit keys, and their total key length adds up to 168 bits, but a more accurate key strength would be 112-bits. Obviously it outperforms the original Data Encryption Standard (DES) algorithm because imagine encrypting data 3 times which makes it more efficient and faster as compared to DES.
3 unique keys are generated at first. These keys are of 56-bit each known as a key bundle. It follows a pattern of Encrypt-Decrypt-Encrypt(EDE) i.e first key(K1) will encrypt message, second key(k2) will decrypt message, third key(K3) will again encrypt message for the last time. However there are 8 possible patterns or modes of triple DES which are DDD, DDE, DED, DEE, EDD, EDE, EED, EEE
AES
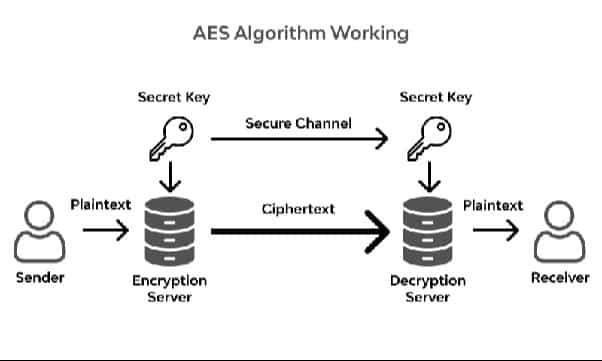
The Advanced Encryption Standard (AES) is the algorithm that many standard organizations most trust as it is much stronger than DES and triple DES. This encryption algorithm is developed by National Institute of Standards and Technology (NIST). It also uses keys of 192 and 256 bits for high-level encryption purposes. AES is a block cipher i.e in this encryption algorithm the input or message to be passed is already decided to be of a fixed size and thus it produces a ciphertext of same size.
For more understanding and how actually this AES algorithm works, please refer to our detailed article on AES here.
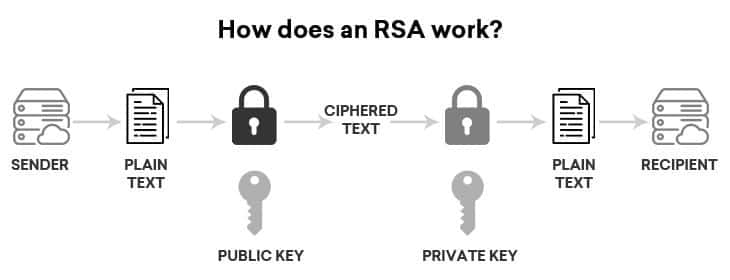
RSA
Rivest-Shamir-Adleman (RSA) is a public-key encryption algorithm and is the standard for sending encrypted data over the internet. It is considered an asymmetric algorithm because it uses a pair of keys – a public key to encrypt a message and a private key to decrypt it.
If the public key is used for encryption, the private key must be used to decrypt the data. This is perfect for sending sensitive information across a network or Internet connection, where the recipient of the data sends the data sender their public key. The sender of the data then encrypts the sensitive information with the public key and sends it to the recipient. Since the public key encrypted the data, only the owner of the private key can decrypt the sensitive data. Thus, only the intended recipient of the data can decrypt it, even if the data were taken in transit.
The other method of asymmetric encryption with RSA is encrypting a message with a private key. In this example, the sender of the data encrypts the data with their private key and sends encrypted data and their public key along to the recipient of the data. The recipient of the data can then decrypt the data with the sender’s public key, thus verifying the sender is who they say they are. With this method, the data could be stolen and read in transit, but the true purpose of this type of encryption is to prove the identity of the sender.
What is meant by Decryption?
Decryption converts an encrypted or encoded message into a readable form and can be understood by the user or system. This process is performed manually by using keys to unencrypted text to the original data. The same algorithm with the same key (in the case of symmetric only) can be used for both encryption-decryption operations.
Why use Encryption and Decryption?
There are various reasons for using these processes, but a few important reasons are:
-
Protects Data
It helps to protect confidential and sensitive data like passwords or other credentials. Let’s assume the worst scenario where the system got breached, now in that case the encrypted data will be unreadable for the attacker as it will need a corresponding decryption key to decode data, hence reducing the risk of exposing confidential data.
-
Maintains Data Integrity
It helps maintain the integrity of users’ data, as data won’t constantly change and can be frequently verified. By using techniques like digital signatures or hash functions, organizations can verify that data has not been altered during transmission or storage.
-
Prevents Data Alteration
Sometimes attacker can alter your data in middle, however Decryption tools ensure that the original data being sent over does not alter. Among different methods, one is where a hash function can compare the original data with the received data, identifying any tampering.
-
Prevents Plagiarism and IP address
Whether it’s software code, research, or creative content, encryption can ensure that only authorized individuals or systems have access to these assets, making it more difficult for competitors or malicious actors to steal and misuse the content.
-
Facilitates Secure Network Communication
When data is encrypted, an attacker intercepting the network cannot easily access the information without the decryption key. This is particularly important for secure communication between servers, devices, or applications (e.g., HTTPS, VPNs). It prevents man-in-the-middle attacks, where attackers try to capture and manipulate data during transmission.
-
Protects Personally Identifiable Information (PII) and Protected Health Information (PHI)
Helps protecting sensitive personal information such as PII and PHI. These include names, addresses, social security numbers, medical records, and more. When PII/PHI data is encrypted, it remains secure even if unauthorized users gain access to it, safeguarding against data breaches and ensuring compliance with data protection regulations like HIPAA, GDPR, and CCPA.
Types of Keys used in Encryption and Decryption
- Symmetric key encryption algorithms use duplicate cryptographic keys for both plaintext encryption and ciphertext decryption.
- Asymmetric key encryption uses two different pairs of keys for encryption. A public key is available to the public, while a secret key is only made available to the receiver of the message, which in turn boosts security.
- Public key encryption is based on two pairs of keys. These keys are used to encrypt messages for a receiver.
- Private key may or may not be a part of the public/private asymmetric key pair. It can also be used in asymmetric encryption, as users can use the same key to encrypt and decrypt data.
- Pre-Shared Key (PSK) is a shared secret that was previously shared between the two parties by using some secure channel before officially using it.
Difference between Encryption and Decryption
| Encryption | Decryption |
|---|---|
| It is a process of converting standard readable data into an unreadable form to prevent unauthorised access to data. | It is a method of converting unreadable or coded data into its original form. |
| When data is supposed to be sent between two different machines, it is encrypted using a secret key automatically. | The data receiver automatically converts the data from code to its original form. |
| The sender sends the data to the destination. | The receiver receives the data and then converts the following. |
| An employee sends essential information to their superiors. | The superior or manager receives crucial confidential information from employees. |
| The same algorithm having the same key is used for encryption-decryption processes. | A single algorithm is used for encryption and decryption using a pair of keys. |
| To transform humanly readable and understandable messages into obscure and incomprehensible forms to prevent interpretation by an attacker. | It converts a hidden message into an understandable form for the user and the system. |
Conclusion
Cryptography is used to secure and protect data, and encryption-decryption is two critical processes. Encryption methods help users protect their confidential information like passwords and so on. But decrypting these coded messages to be readable is also an important step. Decryption is a process of conversion of encrypted data back to it’s original form, indicating that the data has been successfully sent to it’s targeted receiver. However methods like hash function checks the originality of data if somehow any data breach occurs in middle.




