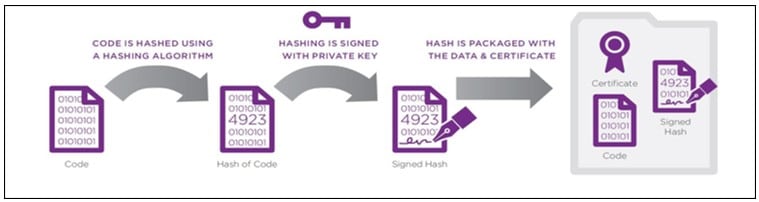
Code-signing is crucial as it guards against the risks posed by the huge number of software downloads from the Internet, particularly the threat of Man-in-the-Middle attacks. This process verifies and authenticates software, ensuring users download only safe, developer-or-distributor-certified applications.
This resolves the issue of an attacker easily impersonating legitimate sources and distributing malware. Prioritizing code signing protects software integrity and user trust in today’s digital landscape.

Code Signing Solution – CodeSign Secure
The main idea for developing CodeSign Secure was to meet our customer’s unique demands and needs. Each organization faces its challenges; we aim to provide a personalized and adaptable solution that addresses and anticipates the various security requirements of different industries.
Our mission is clear: to offer a code-signing solution that puts the customer’s needs at the forefront, ensuring a customized approach that maximizes security without compromising usability.
Our CodeSign Secure provides a secure and flexible solution for seamless code-signing integration across on-premises or cloud environments. With the capability to create or import cryptographic keys into HSMs like Thales, Utimaco, Securosys, or nCipher, our product prioritizes the utmost security for your security keys. This eliminates the potential risks of key theft, corruption, or misuse.
Our product, CodeSign Secure, is designed for compatibility and seamless integration across various environments, ensuring the security and authenticity of your software or application:
-
Compatible Operating Systems
Windows
Linux
Macintosh
-
Supported File Types
Windows: .exe, .dll, .msi, .cab, .ocx
Linux: RPM files
macOS Softwares
Mobile: Android apps, iOS apps
Documents: PDF files, Word documents, PowerShell Scripts, Batch Scripts, etc.
Containers: Docker images
Our platform enhances your software distribution process with advanced features, providing continuous insights and control over the code-signing processes:
-
Automated Workflows
Fully automated and customizable approval workflows.
Automated malware and virus scans with preferred scanners.
-
Integration and Reporting
Integration with Corporate Active Directory.
Comprehensive audit trails, reports, and extensive logging.
-
Enhanced security measures
Multi-factor authentication (MFA) for added security.
Detailed and extensive Role-Based Access Control (RBAC) system with customizable workflows to prevent the risk of unauthorized access and ensure the integrity of certificates.
Enhanced Security Features
This section will explain more about the security features provided by our platform, which make it a good solution for your code-signing process and ensure the integrity and authenticity of your software.
Advanced Key Protection
CodeSign Secure integrates with various Hardware Security Modules (HSMs), such as Thales Luna, Utimaco, nCipher, and Securosys. Using HSMs, our platform ensures that the cryptographic keys are always stored in a tamper-resistant, secure hardware device. This provides an extra layer of protection against key corruption, theft, or misuse, which is very important for maintaining the authenticity of your software.
Multi-Factor Authentication
The signing process in CodeSign Secure supports multi-factor authentication (MFA), which adds another security layer beyond passwords to allow for codesigning operations. This ensures that only authorized personnel can sign code or access sensitive security keys. This is crucial for preventing the risk of insider threats or external breaches.
Powerful Role-Based Access Control System
CodeSign Secure’s access control system is integrated with Corporate Active Directory (like Microsoft AD) to register users and allow centralized management of their credentials and permissions. This makes managing access rights easier and smoothens the authentication process.
Our platform offers customizable workflows to provide granular control over the code signing processes. This feature prevents the risk of granting inappropriate access to unauthorized users and minimizes the potential for security breaches or misuse of the code-signing system.
Flexible Deployment Models
CodeSign Secure’s flexible deployment model is created to satisfy the diverse needs of organizations, ensuring that they can implement code signing with their specific security, operational, and infrastructural requirements. Below is an overview of the deployment options available:
Cloud-Based Service (SaaS)
A cloud-based deployment of CodeSign Secure offers unparalleled scalability and accessibility. Organizations or entities can easily scale their code-signing capabilities up or down based on demand without investing in hardware.
This model is ideal for companies looking for flexibility and those operating in a dynamic development environment. We provide high security and reliability even in cloud-based solutions; security keys can be managed through cloud HSMs. This protects against unauthorized access while benefiting the cloud’s redundancy and availability.
On-Premises Solution
The on-premises option suits organizations prioritizing complete control over their infrastructure and data. This model allows all platform components to be installed within the organization’s data centers and who want to leverage their existing Hardware Security Modules (HSMs).
This ensures the cryptographic keys are securely managed and stored within the organization’s controlled environment. This direct integration supports a secure and efficient code-signing process without requiring any external dependencies.
Comprehensive Platform Support
CodeSign Secure’s comprehensive platform support is designed to address the needs of modern software development and distribution by ensuring that a wide variety of software and digital assets across different operating systems can be signed. Here’s a closer look at the platform support:
Supported Operating Systems
CodeSign Secure is designed to operate seamlessly across the most widely used Operating Systems: Windows, Linux, and Macintosh. Our platform ensures that users don’t need to switch between code-signing tools to sign their code or applications across various Operating Systems. This cross-platform support simplifies the development process for teams working in diverse environments.
Wide Range of Signable Assets
CodeSign Secure supports software and executable files for signing, including .exe, .dll, .msi, .cab, .ova, .hlkx, and .ocx files on Windows and executable formats on Linux and macOS. This ensures that the software distributed in these operating systems maintains integrity and authenticity. With the rise of mobile computing, our platform supports the signing of Android APKs and iOS app packages for mobile application developers.
Our platform also supports signing Docker and Container images to acknowledge the shift towards cloud and containerized environments. Beyond software, CodeSign Secure also provides signing of digital documents, such as PDF files, word documents, and XML files. Our platform also supports OVA, NuGet, and HLK Signing.
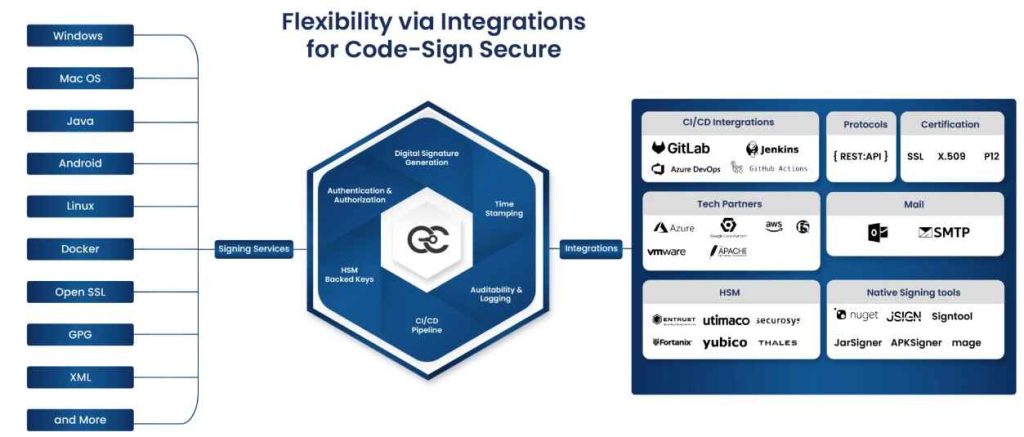
Seamless Integration with Development Processes
Seamless integration with development processes is a pivotal feature of CodeSign Secure, designed to integrate with existing software development workflows without causing any disruptions. Here’s how this seamless integration is achieved:
Integration and Compatibility
Our platform integrates with popular industry development tools and environments, ensuring the code-signing processes can easily be implemented into your existing workflows. CodeSign Secure is developed to support rapid development cycles and continuous integration/continuous deployment (CI/CD) processes like Azure DevOps, Jenkins, GitLab, and so on.
This helps address the needs of modern software development teams to achieve efficiency and security. This automation ensures that all the releases are signed consistently and securely without manual intervention, enhancing efficiency and reducing the risk of human errors.
Simplifying the Development Workflow
Our platform is designed to integrate code-signing into the development process as straightforwardly and non-disruptively as possible. With CodeSign Secure, the complexities of your code-signing processes decrease, helping developers and teams maintain their focus on creating and delivering high-quality software. Our platform automates the complexities of key management, certificate provisioning, and compliance, simplifying the overall development workflow.
Automated Workflow and Compliance
Automated Workflow and compliance are some of CodeSign Secure’s most critical components. It is designed to streamline the code-signing process while ensuring security standards and regulatory requirements. Here’s a more detailed explanation of how our platform addresses these issues:
Automated Approval Workflows
Our platform automates the approval workflows for code-signing requests, ensuring that each software is signed according to predefined policies and procedures. Organizations can customize these workflows based on their required policies and team structures.
This automation and flexibility help eliminate bottlenecks and reduce the time and effort required for manual approvals, also enforcing granular control over who can sign what based on compliance requirements.
Complete Audit Trails and Reporting
Our platform maintains comprehensive audit trails of all code-signing activities, including details about who signed what and when. This level of transparency helps track the software’s integrity throughout its lifecycle and investigate any possible security incidents. CodeSign Secure generates detailed reports and logs that can be used to demonstrate compliance with internal policies and external regulations.
Compliance with Industry Standards and Regulations
CodeSign Secure is designed to comply with industry standards and best practices for code-signing, such as those outlined by the CA/Browser Forum or specific software security regulations in various sectors. Organizations can meet the requirements of many relevant regulations and standards for software development and distribution by automating and enforcing a secure code-signing process or platform.
Ensuring Software Integrity and Trust
Ensuring integrity and trust is a cornerstone of secure software development and distribution. In CodeSign Secure, we have incorporated advanced features like origin verification, reproducible builds, and build verification to offer a comprehensive solution for maintaining the integrity and trustworthiness of software throughout its lifecycle.
Origin Verification
This is crucial for establishing software authenticity by ensuring it comes from a trusted source. Our platform leverages digital signatures to validate the software publisher’s identity, providing a way to verify that the software has not been tampered with after it has been signed.
This helps protect against malicious software and builds user trust by associating the software with a verified developer or organization.
Reproducible Builds
These refer to ensuring that a given source code consistently produces an identical output (like a hash in our case) every time it is compiled, regardless of the environment. This practice enhances the transparency and security of the software development process, as it allows for the verification of the build output against known good outputs to detect any unauthorized changes or potential security vulnerabilities.
Our platform supports this process by providing tools and integration that facilitate the creation and verification of reproducible builds, ensuring that the software distributed is exactly what was intended by the developers.
Build Verification
Build verification extends the concept of integrity checks to the compiled software, ensuring that the software has not been tampered with between compilation and signing. This process involves a series of automated checks and balances, including malware scanning and integrity checks, to validate the safety and integrity of the software before it is signed.
By integrating build verification features, CodeSign Secure ensures that only secure, unaltered software is distributed to end-users, thereby maintaining trust in the supply chain.
Types of Signing offered by CodeSign Secure
| Types of Signing | Brief Description | Key Features | File Extensions |
| Windows Signing | You can digitally sign documents with keys secured in your HSM. Our platform supports EV and OV public code-signing, as well as private code-signing. | Authenticode Files signing with SignTool, Mage, NuGet, ClickOnce, HLK, HCK | .exe, .dll, .cab, .msi, .js, .vbs, .ps1, .ocx, .sys, .wsf, .cat, .msp, .cpl, .efi, .arx, .dbx, .crx, .xsn, .deploy, .xap, and more. |
| Docker and Container Image Signing | You can add digital fingerprints to docker images while keys are stored in the HSM. | Supports Docker Notary for enhanced security | Docker images |
| Firmware Code-Signing | You can sign firmware binaries to authenticate the manufacturer and avoid tampering. | Ensures the integrity of firmware code | .bin, .img, .hex, .fw, .dfu |
| OVA/OVF Code-Signing | Our platform ensures authenticity, prevents unauthorized modifications, and protects against malware. | Provides a verifiable trail of trust for virtual appliance formats | .ova, .ovf |
| Apple Signing | You can sign MacOS software, tools, updates, utilities, and applications. | Uses ProduSign for installer packages and archives | .dmg, .ipa, .app, .pkg, .mpkg |
| Linux Signing | Our platform ensures the authenticity and integrity of RPM packages. | Maintains security throughout the software supply chain | GPG, XML, and more for RPM packages |
| Java Signing | You can securely sign all your Java code using our platform. | Supports signing of Android apps with JarSigner | .jar, .war, .sar, .ear, .apk |

Conclusion
In conclusion, CodeSign Secure offers a comprehensive and secure solution for code-signing across various platforms and file types. Its integration with HSMs ensures the highest level of security for cryptographic keys, supporting both cloud and on-premises environments.
With support for Windows, Docker, firmware, OVA/OVF, Apple, Linux, and Java Signing, our platform addresses many development needs, including EV and OV certificates. Automated workflows, compliance features, and seamless integration with development processes streamline the signing procedure, making it more efficient without compromising security. With CodeSign Secure, elevate your organization’s supply chain to new heights of trust and integrity.
- Code Signing Solution – CodeSign Secure
- Enhanced Security Features
- Advanced Key Protection
- Multi-Factor Authentication
- Powerful Role-Based Access Control System
- Flexible Deployment Models
- Comprehensive Platform Support
- Seamless Integration with Development Processes
- Automated Workflow and Compliance
- Ensuring Software Integrity and Trust
- Types of Signing offered by CodeSign Secure
- Conclusion




