Encryption serves as a method to conceal information by transforming it in a manner that gives the appearance of random data. Its significance lies in being a fundamental tool for ensuring security across the vast Internet landscape.
What is Encryption Algorithm?
To simplify, an encryption algorithm is like a secret code that makes information unreadable to people who shouldn’t see it. It uses special math rules and keys to jumble up data; only those with the right key can unscramble and understand the information. This is important for keeping our messages, passwords, and other sensitive data safe when we send them online or store them on our devices. It’s like locking our digital information to keep it private and secure.
There are two main types of encryption algorithms (Read more about them in the Encryption Basics Section):
-
Symmetric Encryption Algorithms
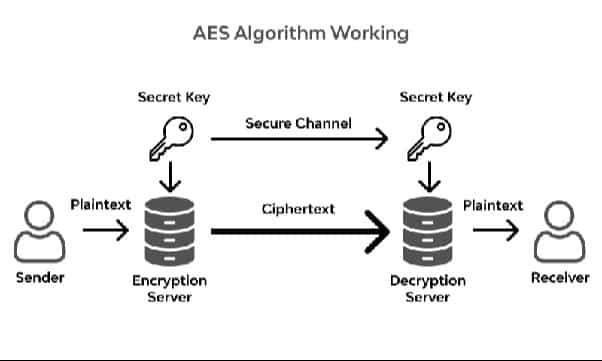
In symmetric encryption, a single key is used for encryption and decryption. The same key is shared between the communicating parties. While symmetric encryption is efficient, it requires a secure method for key exchange.
-
Asymmetric Encryption Algorithms
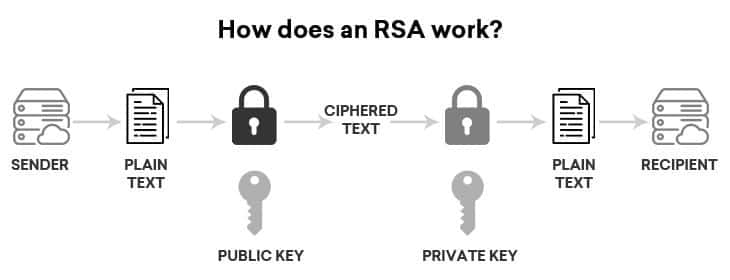
Asymmetric encryption, also known as public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, allowing anyone to encrypt data, but only the private key holder can decrypt and access the original information.
How does the Encryption Algorithm work?
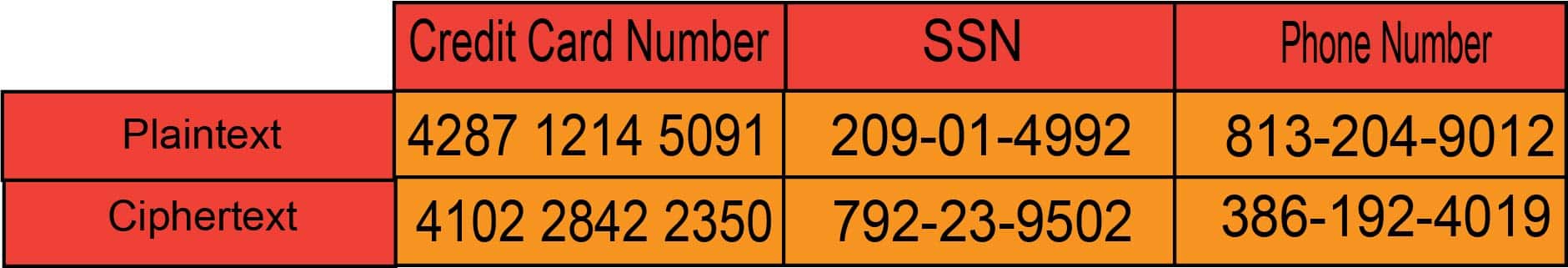
Encryption transforms readable “plaintext” into encoded “ciphertext” through cryptographic algorithms and mathematical models for secure data manipulation. Reverting this encoded data to its original form (plaintext) requires a decryption key—a series of numbers or a password, also generated through an algorithm.
Strong encryption practices involve using a vast array of cryptographic keys, making it practically impossible for unauthorized individuals to guess the correct key or employ brute force attacks to try every potential combination systematically. This complexity enhances the security of encrypted data.
An example of a basic encryption method is the “Caesar cipher,” attributed to Julius Caesar. In this substitution cipher, each letter is replaced by another letter positioned a fixed number of spaces down the alphabet. To decipher the message, the recipient needs the key—knowing, for instance, the specific shift applied (e.g., a “left shift four”). This means every “E” in the message would correspond to a “Y”.
How can encryption be used to protect data throughout its lifecycle?
The following refers to different states of data based on its activity or location within a computing environment:
-
Data-at-Rest
Stored or archived information that is not actively being used or transmitted. This data is typically saved on storage devices such as hard drives, solid-state drives, or other long-term storage solutions. Examples include files stored on your computer’s hard drive, data on a USB flash drive, and information saved in a database when not actively accessed.
-
Data-in-Transit
Information actively moving from one location to another over a network or between devices. This could involve communication over the internet, between servers, or data being transmitted between devices. Example include Sending an email, accessing a website, or transferring files between devices using a network connection.
-
Data-in-Use
Information actively processed, accessed, or utilized by a computer system or application. This occurs when the data is being used by applications or undergoing computational operations. Example: When you open and work on a document using a word processor or when a database server is actively processing queries and providing results.
Conclusion
In conclusion, encryption emerges as a critical tool in fortifying the security and confidentiality of information within the expansive landscape of the Internet. As a fundamental technique, encryption transforms readable data into encoded ciphertext, ensuring that sensitive information remains indecipherable without the corresponding decryption key.
The Encryption Algorithm, akin to a secret code, employs mathematical rules and keys, with Symmetric Encryption utilizing a shared key and Asymmetric Encryption employing a public-private key pair. Throughout the data lifecycle, encryption is vital in protecting information at rest, in transit, and in use. Robust encryption practices, exemplified by historical methods like the Caesar cipher, make unauthorized access practically impossible. As a cornerstone of cybersecurity, encryption is a crucial safeguard, upholding the integrity and privacy of digital information in an interconnected and data-driven era.